MITRE ATT&CK™ Analysis - T1546.015 Component Object Model Hijacking
Component Object Model Hijacking Overview
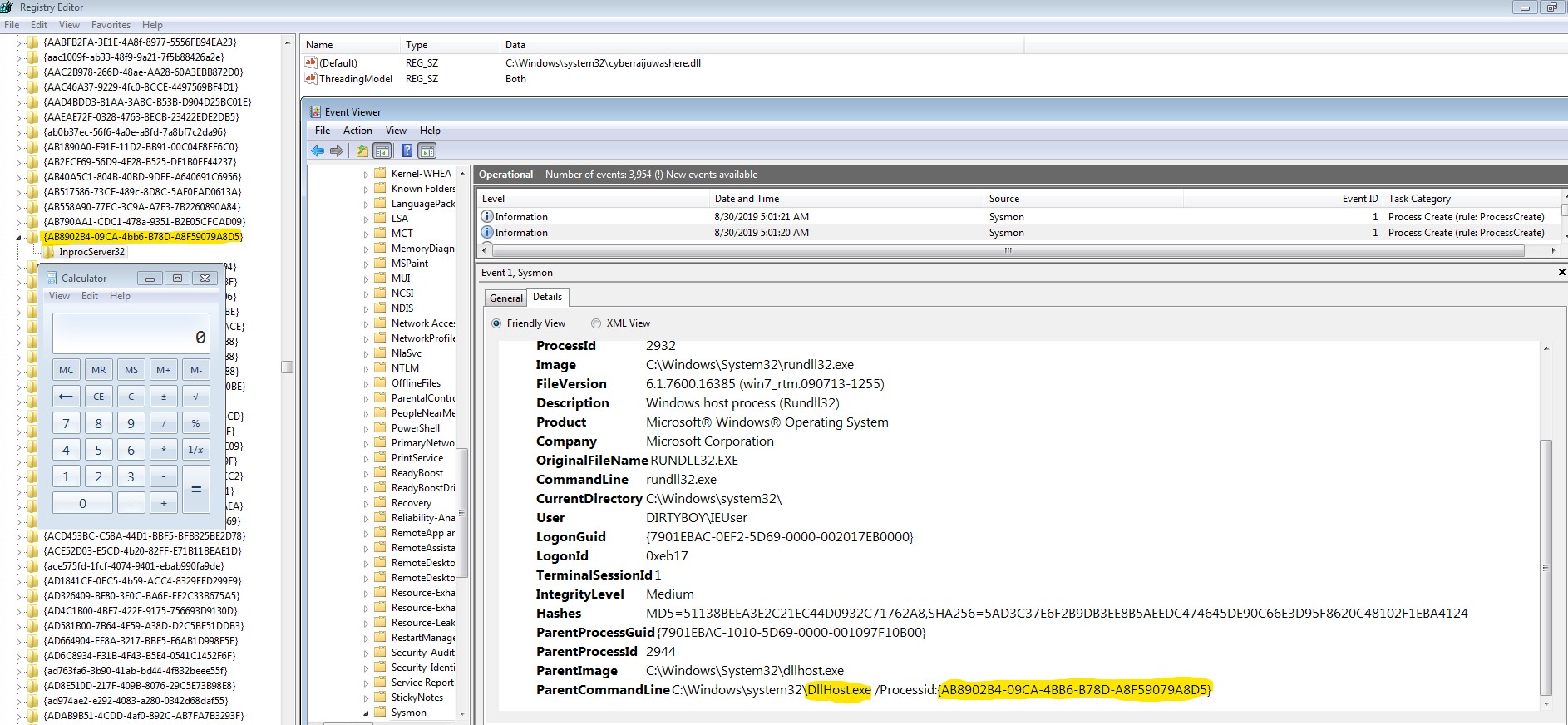
An adversary is able to hijack COM references and relationships as a means for persistence by modifying specific registry keys.
Component Object Model Hijacking Analysis
Lab Example
RED TEAM: ATTACK
Rundll32.exe executing an arbitrary executable through a malicious dll replacement.
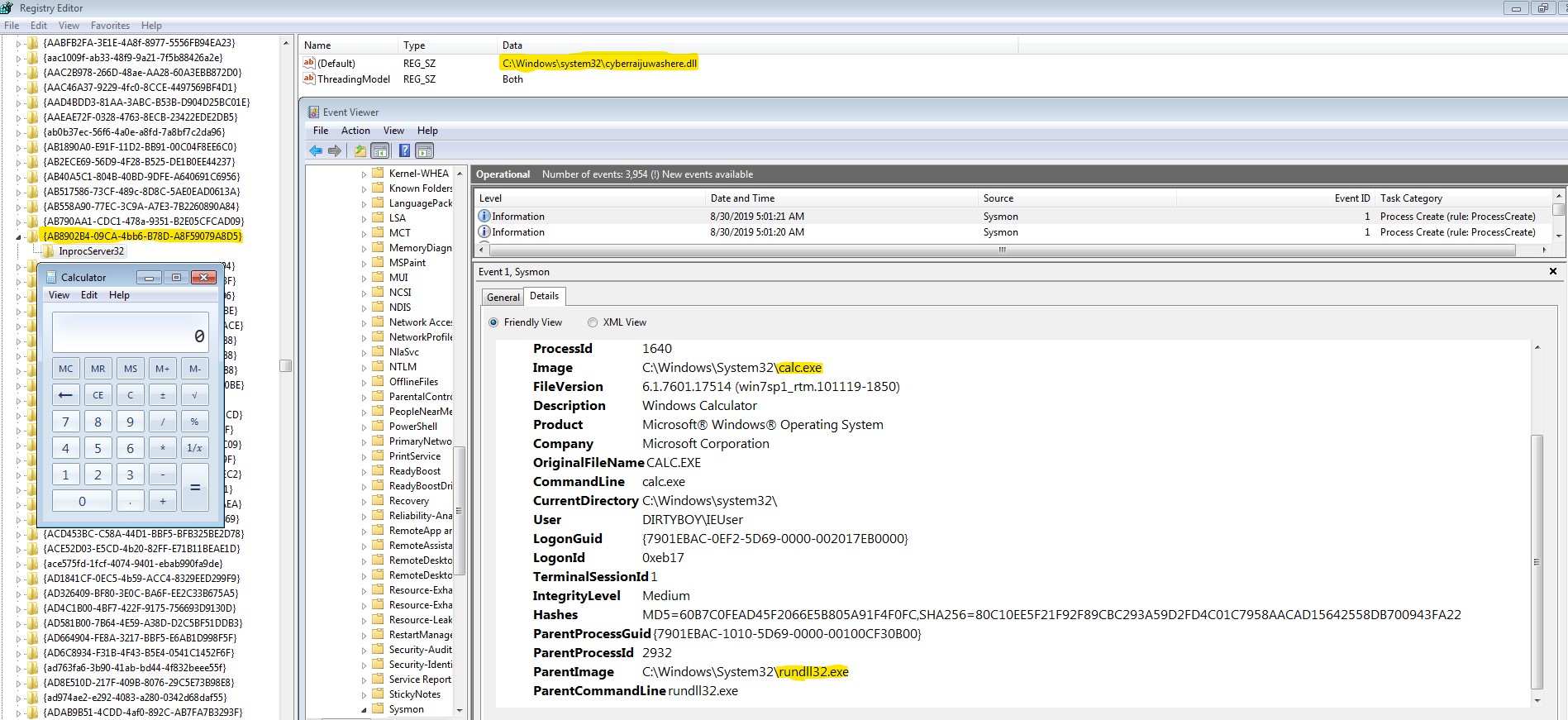
The end result is whenever a thumbnail is viewed, the calculator is executed on this host.
BLUE TEAM: DEFEND
The DLLHost parent executable gives away the impacted CLSID (Com Object) registry key and we can use this to remediate the system.