MITRE ATT&CK™ Analysis - T1055 Process Injection
Process Injection
Process injection is a way of executing code under the context of another process. To quote the MITRE ATT&CK entry:
“Process injection is a method of executing arbitrary code in the address space of a separate live process. Running code in the context of another process may allow access to the process’s memory, system/network resources, and possibly elevated privileges. Execution via process injection may also evade detection from security products since the execution is masked under a legitimate process.
Process Injection Analysis
Lab Example
RED TEAM: ATTACK
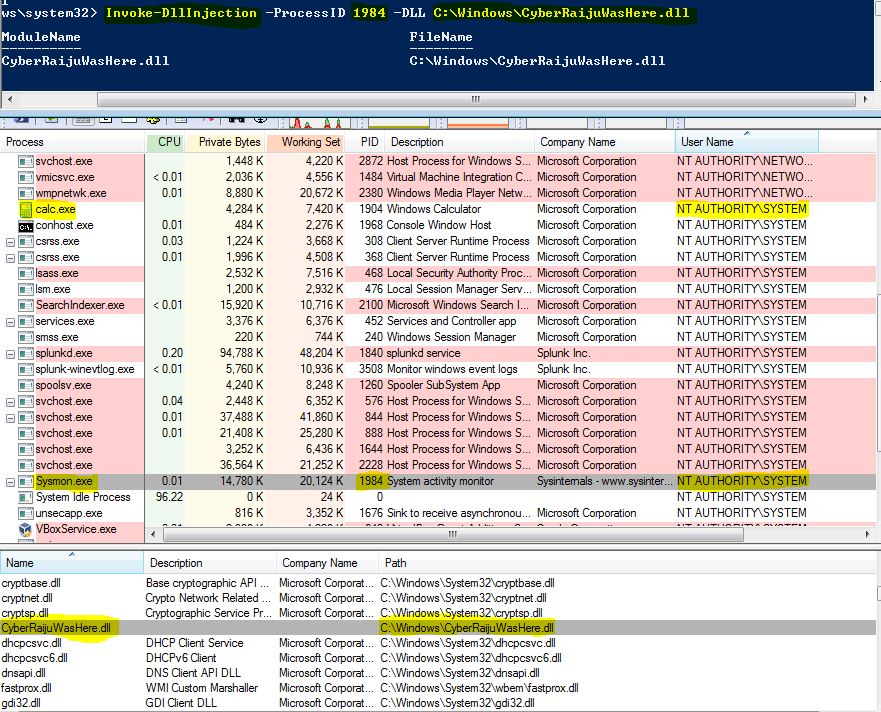
In the below example we have leveraged the Invoke-DLLInjection PowerShell module created as part of the PowerSploit framework.
Using the below we are easily able to take our malicious dll and inject it into the memory of a running process (in this case the running Sysmon service just for the irony). This works by the following:
- VirtualAllocEx is used to allocate virtual memory which will be executable from the Sysmon process
- WriteProcessMemory is used to write the location/name of our malicious DLL into this memory space
- RtlCreateUserThread is used to create a remote thread and run LoadLibraryA which loads our malicious dll into the address space of Sysmon.
Commands:
Import-Module .\CodeExecution.psd1
Invoke-DllInjection -ProcessID [PID] -DLL [DLL]
The end result is that Microsoft Sysmon has been leveraged to run our malicious DLL with System level privileges which in this scenario runs Calc.
BLUE TEAM: DEFEND
Successful execution of this attack left minimal traces through the most common sysmon configuration. To detect this you should have powershell logging enabled and be on the lookout for any legitimate processes making illegitimate requests. You can always monitor the below sysmon events which may provide valuable information.
- Sysmon: 11 (File created)
- Sysmon: 17 (Named pipe created)
- Sysmon: 18 (Named pipe connected)
We can also enable script block logging and powershell transcription by creating the below registry keys.
- HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging /v EnableScriptBlockLogging 1
- HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableTranscripting 1
- HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableInvocationHeader 1
- HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\Transcription /v OutputDirectory [outputpath]
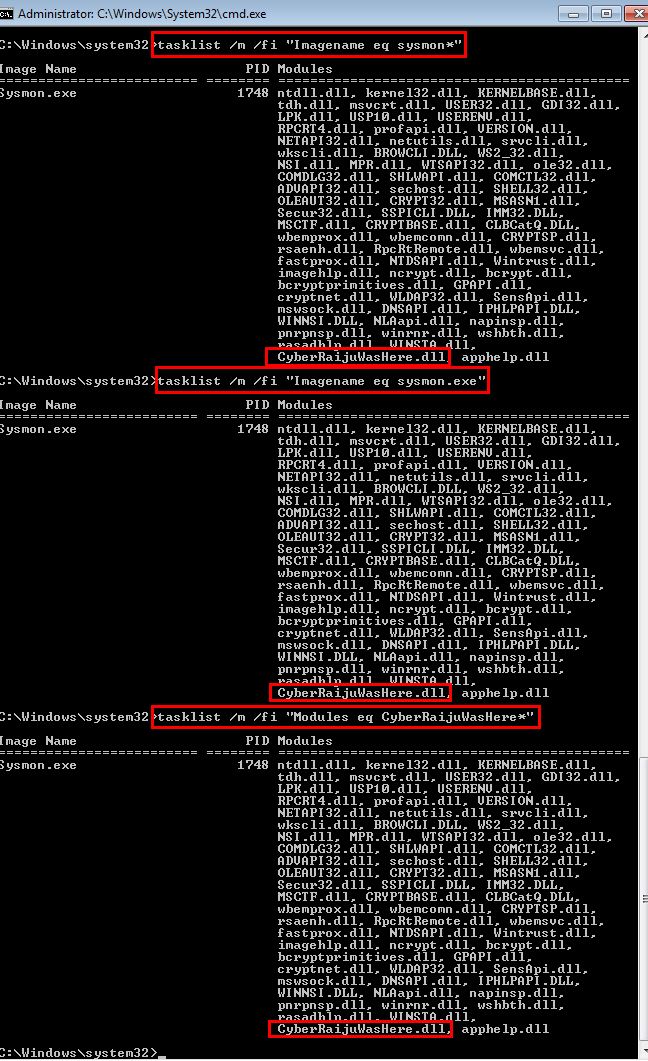
During live triage we can always see what modules including DLLs have been loaded by a process by using the tasklist command with or without filters.
tasklist /m /fi "PID eq [PID]"
tasklist /m /fi "IMAGENAME eq Sysmon.exe"
tasklist /m /fi "MODULES eq CyberRaijuWasHere*"
If this isn’t of value we can also get the hash of DLLs being injected, simply visit my DFIR cheatsheet.