MITRE ATT&CK™ Analysis - T1090 Proxy
Connection Proxy
A proxy is essentially a tunnel between 2 systems, this allows data to come through one system and be redirected to or through another. This can be used for a variety of methods such as obfuscation, to deal with multiple connections, or to provide a level of resiliency in an attack should 1 connection go down.
One benefit of using a Connection Proxy is that you can bypass firewalls by using a compromised host.
Connection Proxy Analysis
Lab Example
RED TEAM: ATTACK
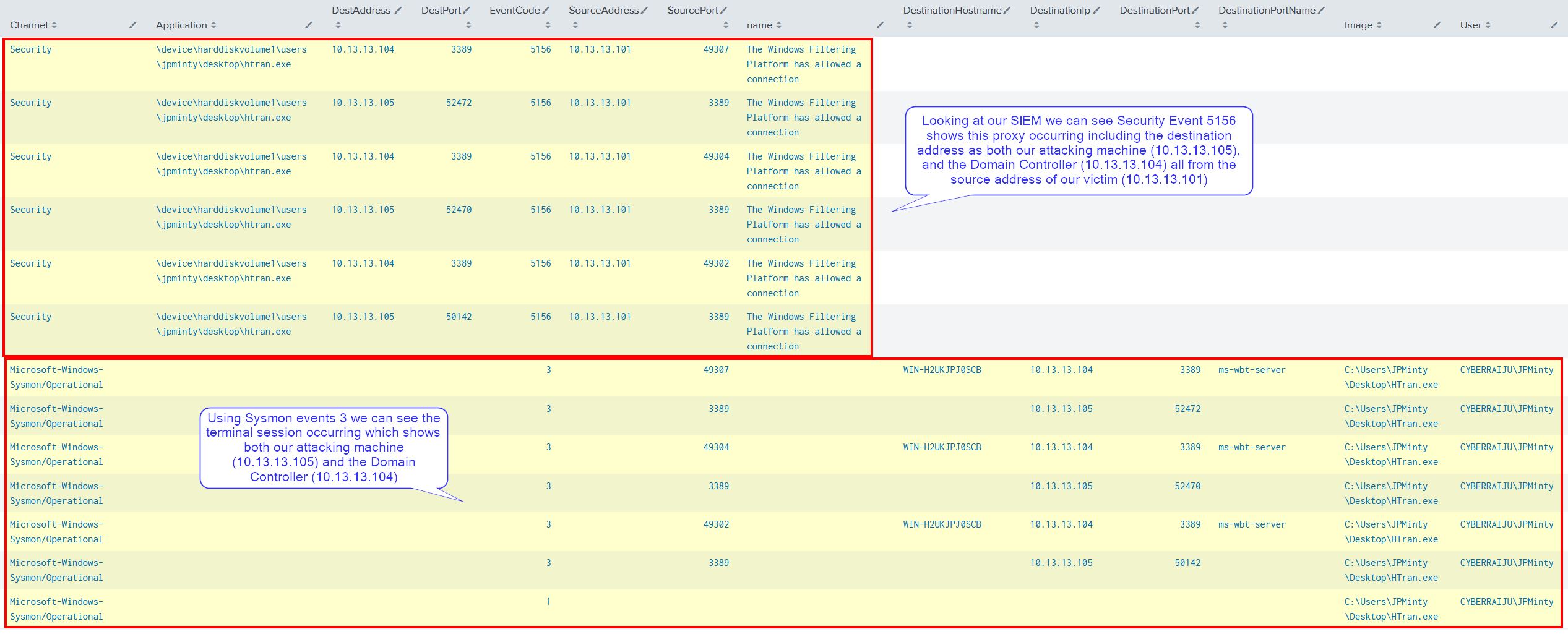
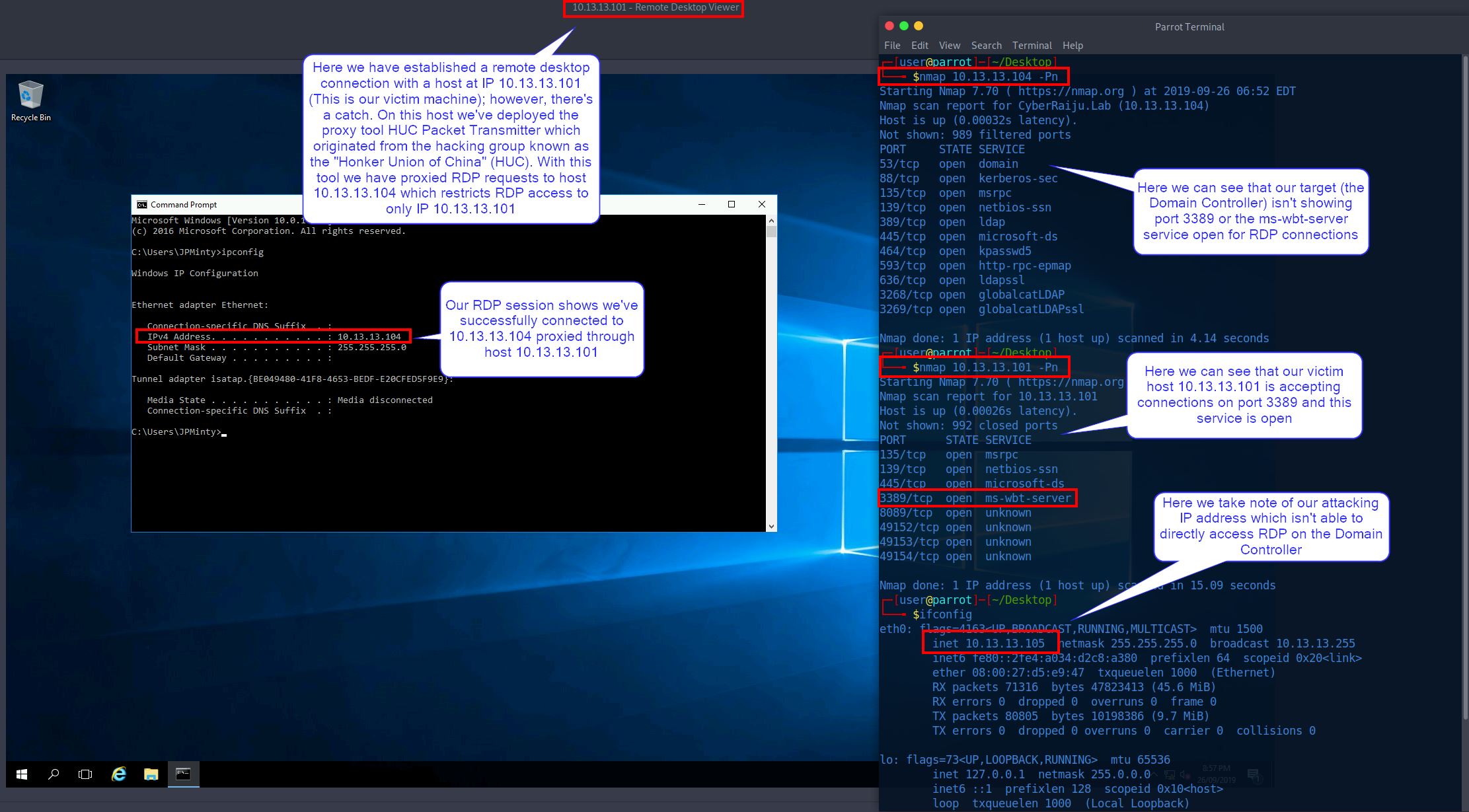
In this example we have valid credentials to a Domain Controller (our target), and a jump (victim) host; however, we’re unable to connect to the Domain Controller because it only allows RDP traffic from our jump host which we only have a shell on.
Using a Connection Proxy known as the HUC Packet Transmitter (HTran) which originated from the hacking group known as the “Honker Union of China” (HUC), we are able to proxy connections from our compromised jump host to allow us to RDP directly from our attacking machine to the Domain Controller
In practice we have dropped HTran onto our victim machine through our remote shell and initiated a proxy connection to the Domain Controller, our target.
At this point we cansee that our victim machine is listening on port 3389, and upon connecting we have access to the Domain Controller.
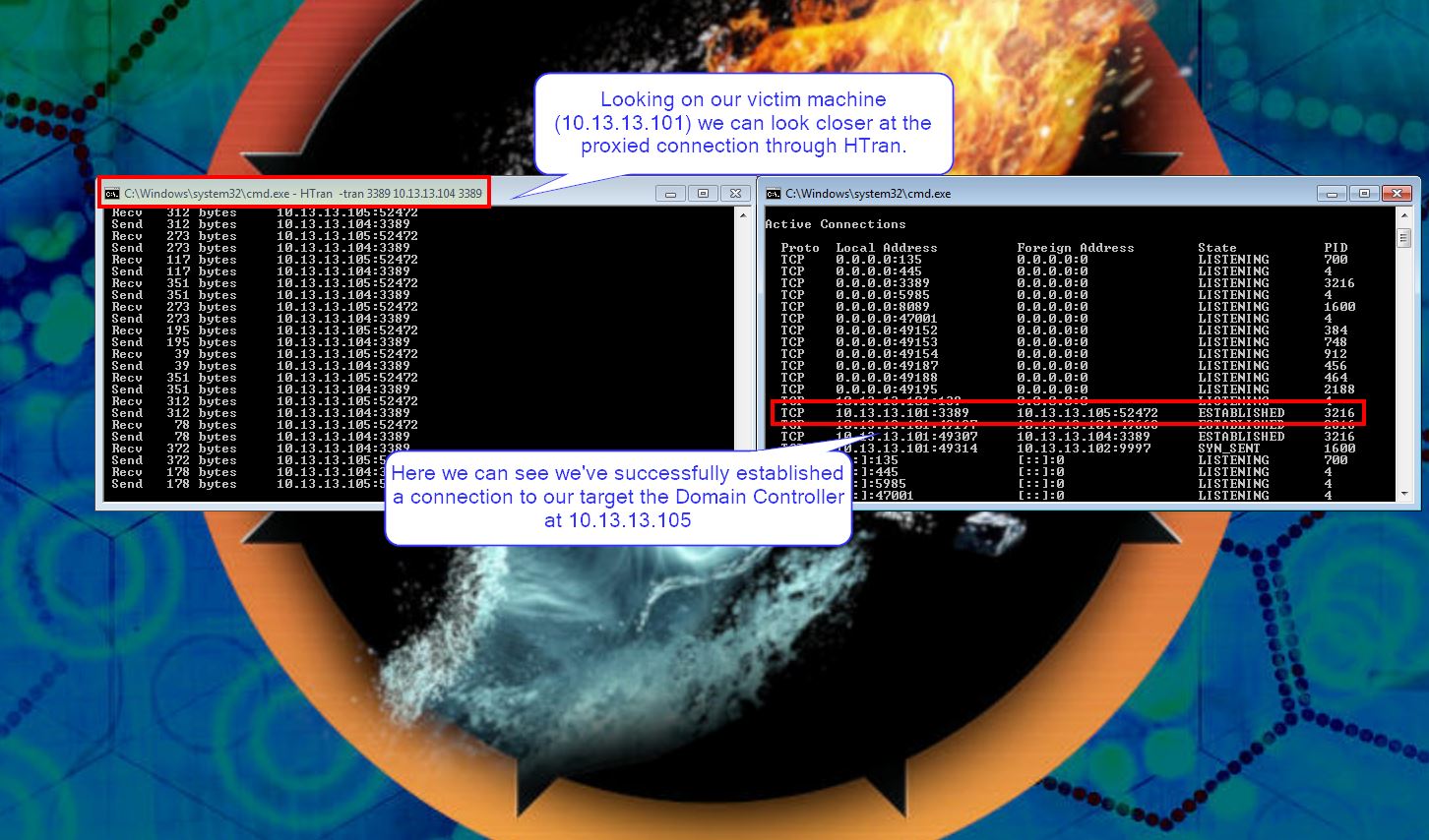
Looking closer into the tool in action we can see it is relaying our packets directly to the Domain Controller as if our victim machine was initiating the connection itself.
BLUE TEAM: DEFEND
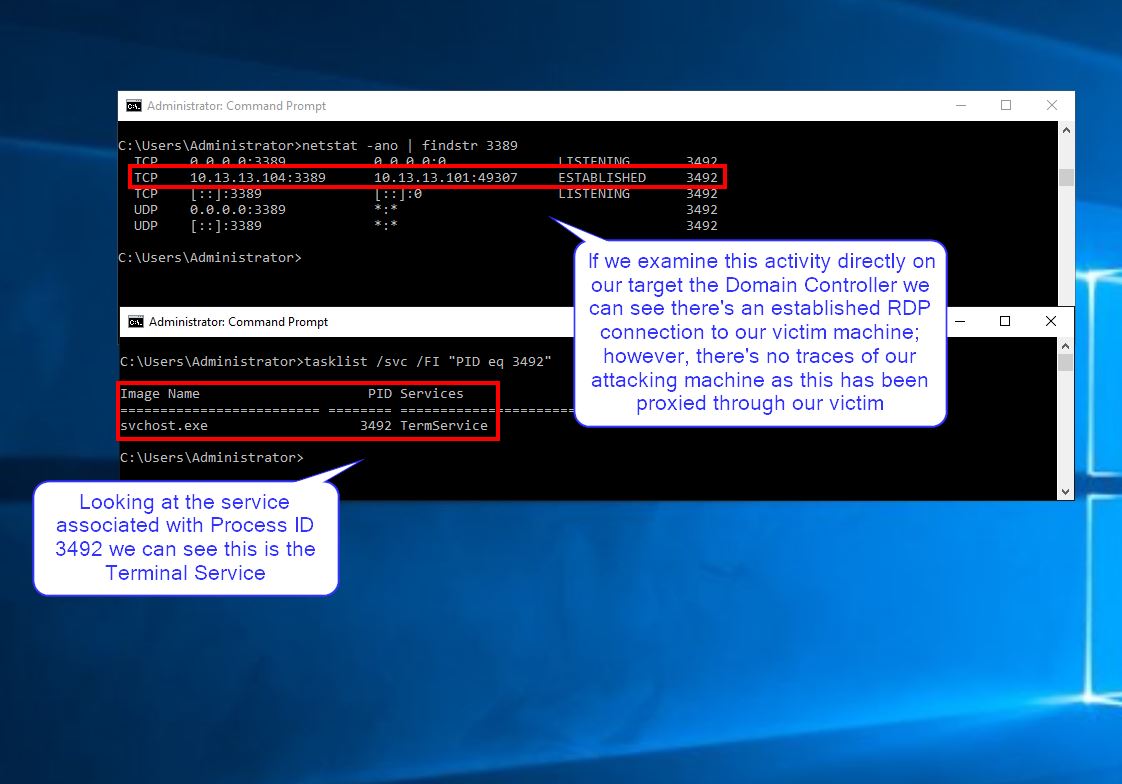
From a defenders point of view when we look at the established connections on the Domain Controller we cannot see the attacking IP as it has all been relayed through our victim.
When we look at the logs on our victim machine through our SIEM we can clearly see this connection being established in addition to the attacking IP, and the target Domain Controllers IP.