MITRE ATT&CK™ Analysis - T1078 Valid Accounts
Valid Accounts
Having access to valid accounts is sometimes the only thing separating an adversary from impersonating someone else, or even a service on a system. By using Valid Accounts an adversary can often go undetected within an environment or on a website, and generally the system or website are none the wiser, as this was the correct verification method from human to system.
Valid Accounts Analysis
Lab Example
RED TEAM: ATTACK
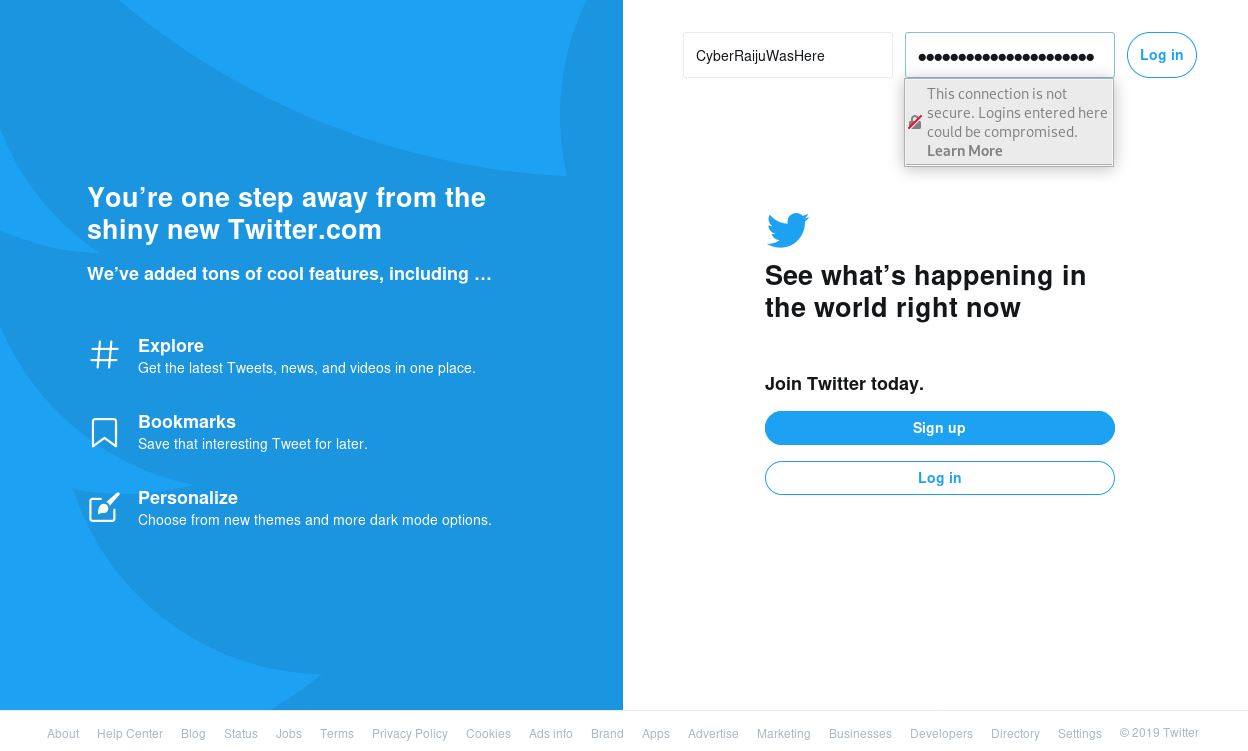
In the below example we have leveraged the Social Engineer Toolkit to clone the Twitter login page and serve it up as a phishing website to an unsuspecting user.
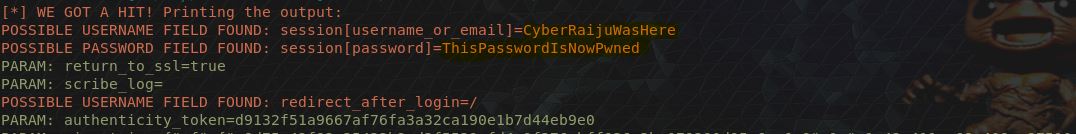
Once the unsuspecting user logs into the website and uses their credentials, these are sent to the adversaries machine.
The end result is that these accounts are fed into the global economy which thrives on compromised credentials and joins over 555million other known passwords. We are also now able to impersonate this user if they haven’t used Multi-Factor Authentication (which can also be Phished) and logon to their Twitter account, now imagine all the systems you could logon to if only you had the valid account credentials.
BLUE TEAM: DEFEND
Knowing about poor password practices, previously compromised credentials, phishinbg, and detecting suspicious logons are just a few ways blue teams can defend against valid credential abuse. You may want to look at logon times and source IP addresses to determine if someone is logging on outside of normal working hours, or onto systems they usually don’t.
When you do find your account has been compromised a password reset and invalidation of any current sessions is the quickest way to regain control. We can do this via command line without entering our new credentials on the screen by using the below.
net user [UserName] *
or if it is a domain joined account.
net user [UserName] * /domain
If this is a web application which uses its own username and password feature then you’ll need to do it through the appropriate web application’s password reset page.