MITRE ATT&CK™ Analysis - T1546.010 AppInit DLLs
AppInit DLLs
By modifying the AppInit_DLLs registry key in either of these locations:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows
- HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows
We’re able to effectively tell Windows to load an arbitrary dll into a process every time the user32.dll is loaded, which is essentially whenever any process runs. Because of this we’re able to establish persistence or go from Admin to SYSTEM privileges.
AppInit DLLs Analysis
Lab Example
RED TEAM: ATTACK
In the below example we have created a dll which will popup a message every time it is loaded into a process. This is supported by 3 values within the AppInit_DLLs registry key, 1 to specify our DLL, 1 to specify it will be loaded, and 1 to ensure it doesn’t need to be signed.This is revealed using Autoruns, and these specific registry keys should be closely monitored as they don’t often change.
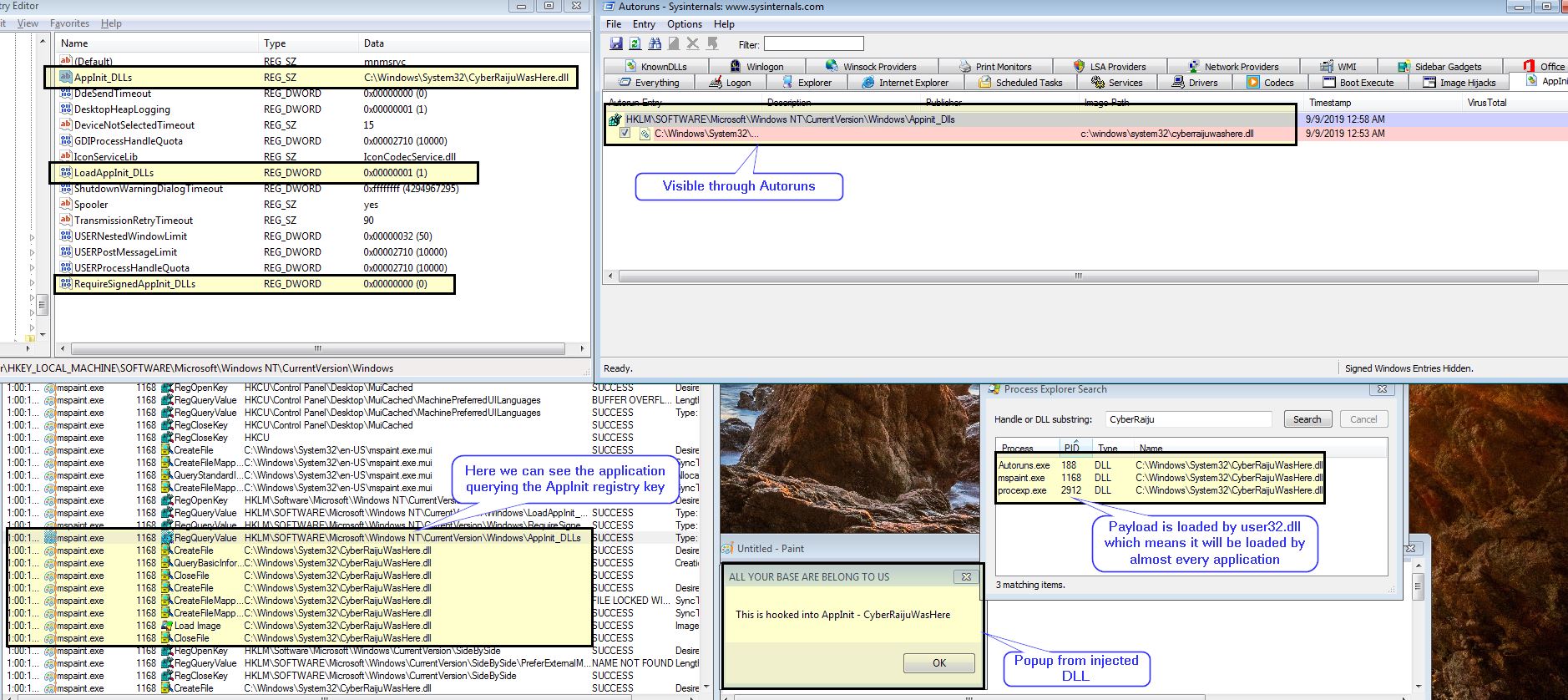
With this example there are still some flaws, if the key isn’t removed before the machine restarts it will cause the operating system to freak out on boot and we see a friendly Blue Screen of Death (BSOD).
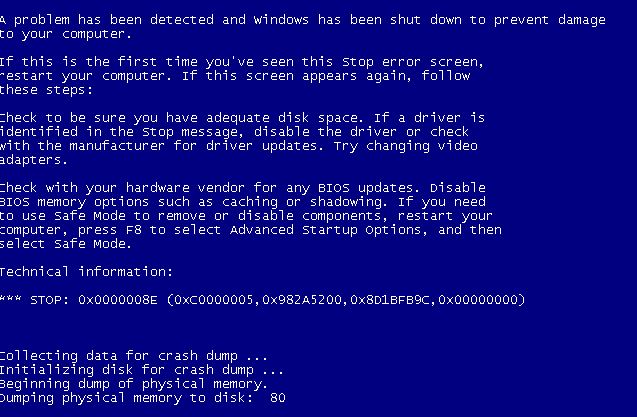
This is something to keep in mind when attempting to run persistence using this method. Of note if someone who has become a victim of this attempts to automatically resolve the BSOD issue using Windows Repair, Windows will fail to fix the issue in this example and they may need to perform a system restore if they were unaware that this particular DLL or reg key was causing the issue.
The end result is that this machine suddenly loads your DLL into multiple processes quite quickly and must be approached very carefully if this is to succeed.
BLUE TEAM: DEFEND
As mentioned this can be seen using Autoruns, but we can also see these entries during live triage by using the below.
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\Appinit_DLLs" /s
reg query "HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Windows\Appint_DLLs" /s
Looking through our SIEM it is worth monitoring these 2 entries for registry changes using the below Sysmon events.
- Sysmon: 12 (Registry object added or deleted)
- Sysmon: 13 (Registry value set)




