MITRE ATT&CK™ Analysis - T1556.002 Password Filter DLL
Password Filter DLL
A Password Filter DLL is used by the operating system to validate that passwords conform to password policies. These can be on both local machines, and domain controllers and come in the form of a DLL file located within Windows\System32.
Before a new password is set within the Security Accounts Manager (SAM), the operating system Local Security Authority (LSA) attempts to validate that the password set is approved by notifying password filter DLLs.
By creating a malicious password filter DLL and registering this with the LSA, we are able to ensure that whenever a password is changed, it is first sent through our DLL in cleartext which we can then output to a file or send to a remote server.
Password Filter DLL Analysis
Lab Example
RED AND BLUE TEAM: ATTACK AND DEFEND
In this example we use @spotheplanet’s evilpwfilter based on @mubix’s original evilpassfilter to log the new plaintext passwords whenever a user changes their password.
This has been tested on Windows 10 Enterprise Build 17134. It should be noted that in testing different scenarios, it was found if you do not have a machine with a valid Windows License then it won’t check against the Password Filter DLL, and in turn will not work.
By modifying the lsa registry key and ensuring the value of “notification packages” includes the name of our malicious Password Filter DLL, we are able to ensure that passwords are sent to it whenever they are changed.
reg add "HKLM\SYSTEM\currentcontrolset\control\lsa" /v "notification packages" /d scecli\0raijufilter /t reg_multi_sz
In this scenario any password changes it will be logged to a file called CyberRaijuWasHere.txt in the C: drive.
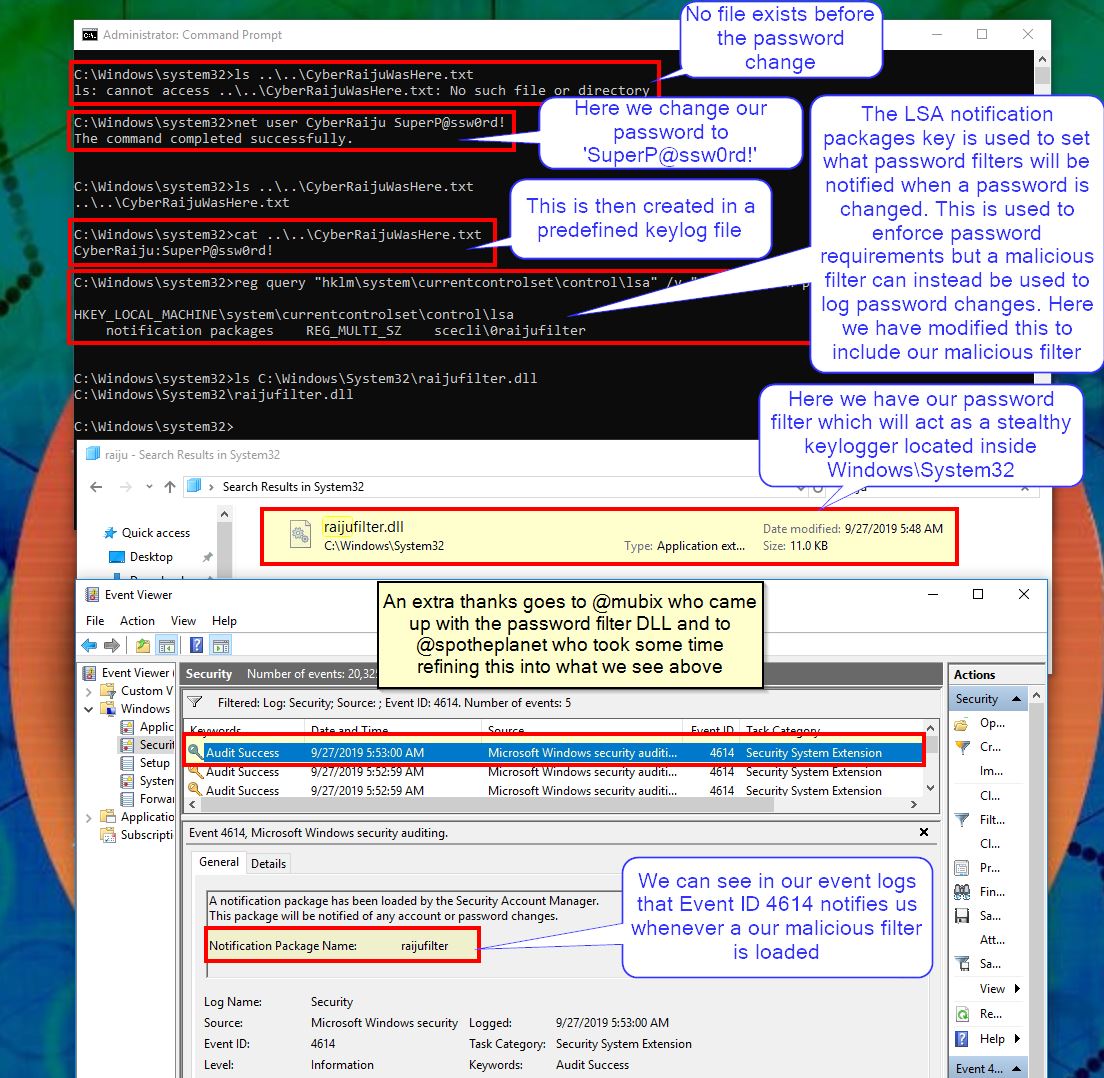
One thing to note is that from a defenders point of view this generates a Security Event ID of 4614 which tells us that a notification package was loaded by the SAM.




