2019 Defcon DFIR CTF Write-up
Summary
On August 9th David Cowen (HECFBlog) announced the 2019 Unofficial Defcon DFIR CTF was going live which had been provided by the Champlain College’s Digital Forensic Association. The Unofficial Defcon DFIR CTF comprised of 5 different challenge categories with a total of 82 DFIR related challenges including a Crypto Challenge, Deadbox Forensics, Linux Forensics, Memory Forensics, and a Live VM to Triage.
After the challenge was over, Evandrix and I teamed up to tackle the rest of the challenges and became the second and third person to successfully complete all the CTF challenges. At the time of writing only 3 people had successfully completed all challenges including the champion Adam Harrison, Evandrix, and myself.
Below details how I went about solving each challenge.
Pre-requirements
For this challenge I had the following at my disposal:
- Windows host OS
- Kali Linux VM
- Autopsy
- FTK Imager
- CTF Files
Write-up
Pre-warning, the answers to the questions are below. If you do not want to spoil this challenge for yourself or others, use this as a guide to help you get over the line for a particular flag rather than a way of cheating your way up the scoreboard. Or don’t, it’s entirely up to you how you choose to learn, and I’m not in charge of your life :).
Category: DFA Crypto Challenge
Are you ready for this? - 30 Points
“On the homepage you will notice the Champlain College Digital Forensics Association’s Logo. Can you decipher the hidden message?”*
This particular challenge involved a little bit of experimentation, a little bit of OSINT, and a little bit of luck. Looking at the DFA Logo, we can see the following characters from left to right.
70 6F 71 64 63 6B 68 6E
This looks a lot like Hex, so by decoding this from Hex we get.
Poqdckhn
Still appearing like gibberish, we know this is supposed to be a “Crypto Challenge”. Before going down the path of modern cryptography, we can start experimenting with some different implementations of the common caesar cipher. One algorithm is Rot13 which rotates alphabetical characters by 13, and considering these are all alphabetical it’s a good start.
Cbdqpxua
This is still quite gibberish. Now by taking the context of a “Crypto Challenge”, it is possible this string requires an algorithm which needs a key, one common algorithm which implements this is the Vigenere cipher. At this point we need a key. As this was created by the Champlain college, Champlain may be a possible key.
audeamus
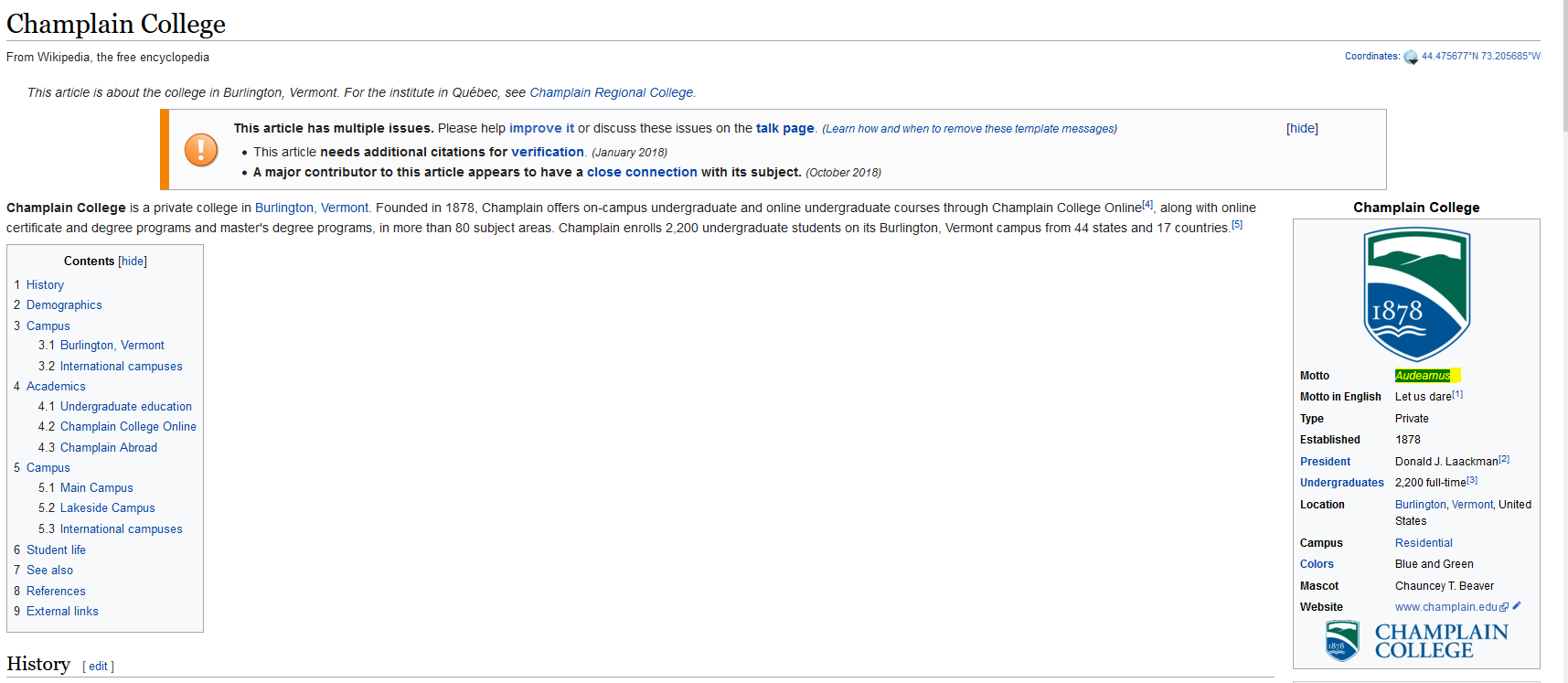
This at first glance still looks incomprehensible; however, this is actually Latin, and a quick Wikipedia search of Champlain reveals this is their motto.
All of this can be automated and the output can be viewed using the tool CyberChef
With that output, we have found the flag.
flag<audeamus>
Category: Deadbox Forensics
01. Hello, my name is… - 1 Point
“What is the name of the examiner who created the E01?”*
As this was created using AccessData® FTK® Imager we can simply read Horcrux.E01.txt and find this information.
Created By AccessData® FTK® Imager 4.1.1.1
Case Information:
Acquired using: ADI4.1.1.1
Case Number: 9.75
Evidence Number: 394
Unique description: Lbh'er n jvmneq Uneel!
Examiner: Minerva
Notes: Why does Voldemort only use Twitter and not Facebook? --Because he has followers not friends...
flag<Minerva>
02. Who owns it? - 1 Point
“What is the username of the primary user of the machine?”*
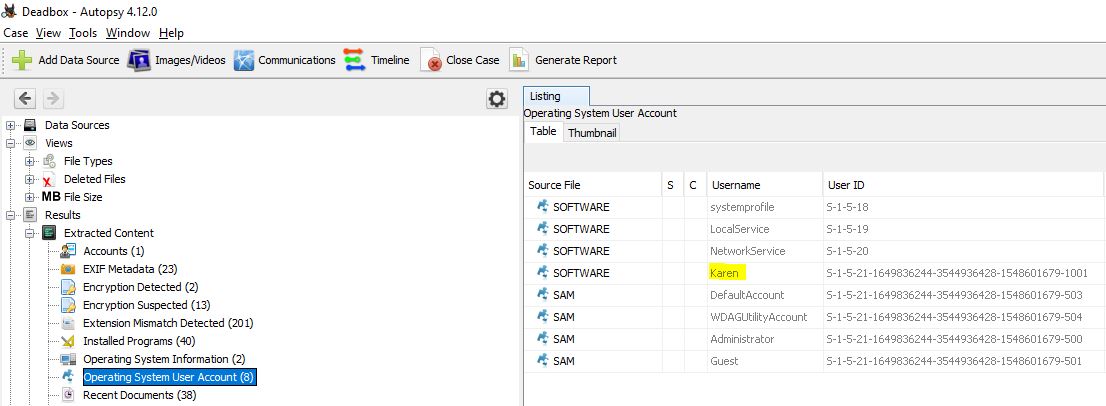
Although this was created with FTK Imager, I started my analysis using Autopsy to see how it would fare with open source tools. After opening and parsing the E01 file we can find this information under the ‘Operating System User Account’ section.
flag<Karen>
03. Does it match? - 1 Point
“What is the SHA1 hash of the evidence?”
Looking back within the Horcrux.E01.txt file we can find this information computed and verified by AccessData® FTK® Imager.
Image Verification Results:
Verification started: Fri Mar 22 20:25:53 2019
Verification finished: Fri Mar 22 20:42:12 2019
MD5 checksum: 3422bde521801901155f73f7de5cd8fe : verified
SHA1 checksum: 0fa6ab4bd9a707d49ded70e8b9198fe18114b369 : verified
flag<0fa6ab4bd9a707d49ded70e8b9198fe18114b369>
04. The Big Bang - 1 Point
“What time was the image created? Submit in UTC as MM/DD/YYYY HH:MM:SS in 24 format”
Using a Kali instance, we can use the inbuilt ewfinfo tool to view metadata associated with the Horcrux file which was created with the Expert Witness Compression Format (EWF). Because of how the information was obtained, we can make the assumption this is already in UTC.
ewfinfo Horcrux.E01
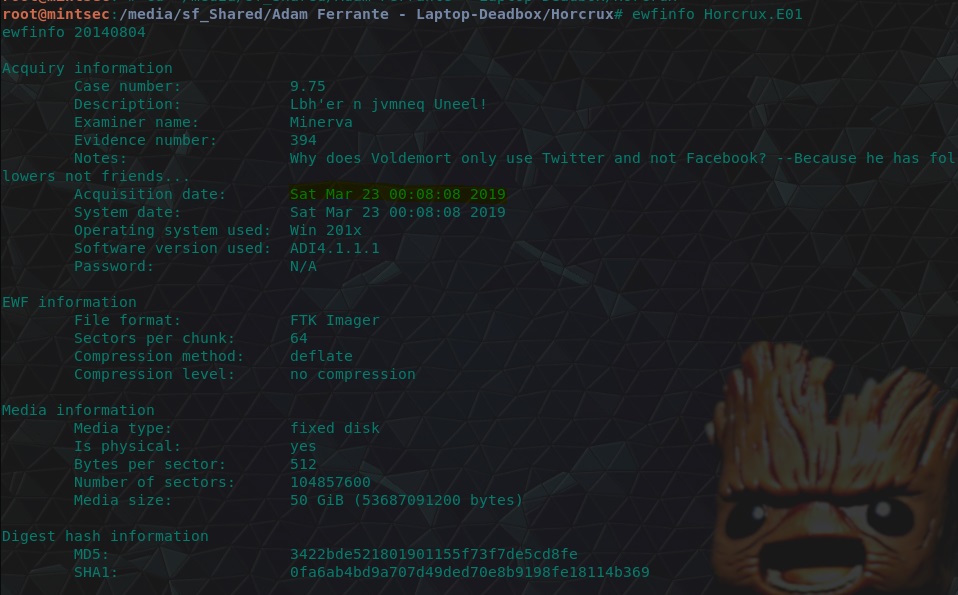
flag<03/23/2019 00:08:08>
05. Which window is it? - 5 Points
“What OS is installed on this computer? Windows __”
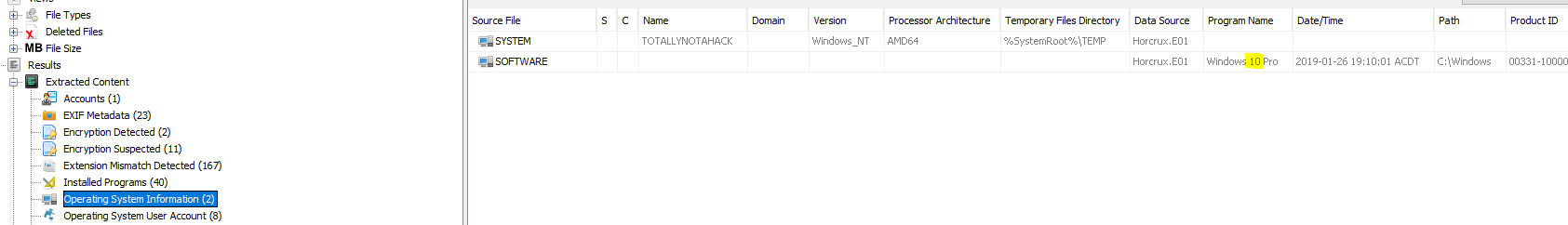
Back within Autopsy, we can find this information under “Operating System Information”.
flag<10>
06. The worst thing about prison were the dementors! - 5 Points
“There appears to be a theme used when creating the E01. What is the theme? (Case Sensitive, two words)”
This was pretty self explanatory, but if you’ve been living under a rock and don’t know what a ‘dementor’ is, a simple search will give you your answer. Here’s some themes we’ve seen so far for anyone who may be a Muggle, or as the US calls it, No-Maj.
- Minerva (Minerva McGonagall)
- Voldemort (Lord Voldemort AKA He who shall not be named)
- Horcrux (An object with a fragment of a Wizard or Witch soul)
- Dementor (Basically a flying Grim Reaper ‘Death’ who has lost their scythe)
flag<Harry Potter>
07. Brooms aren’t just for sweeping - 5 Points
“What is the decoded name of the Evidence File?”
The unique description within the Horcrux.E01.txt currently looks like gibberish.
Lbh'er n jvmneq Uneel!
Once again we can simply run the Rot13 cipher over this to get our answer…but I personally prefer this answer.

flag<You're a wizard Harry!>
08. Russia - 10 Points
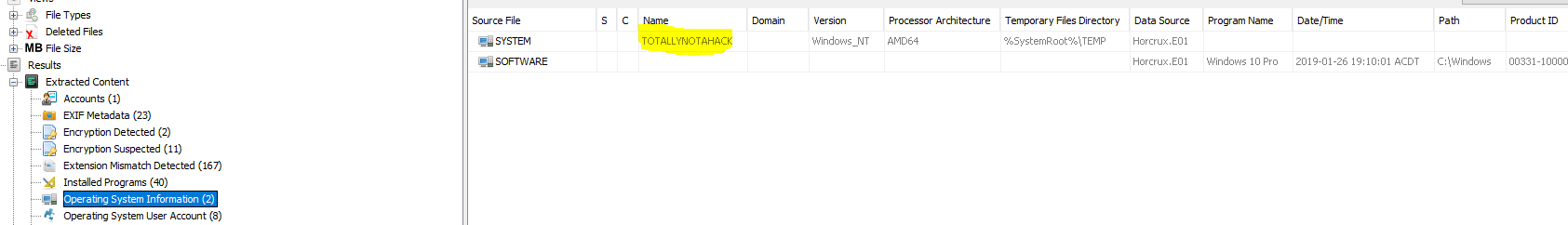
“What is the hostname of the Windows partition?”
Once again using Autopsy this information is shown under “Operating System Information”.
flag<TOTALLYNOTAHACK>
09. Let’s chat - 10 Points
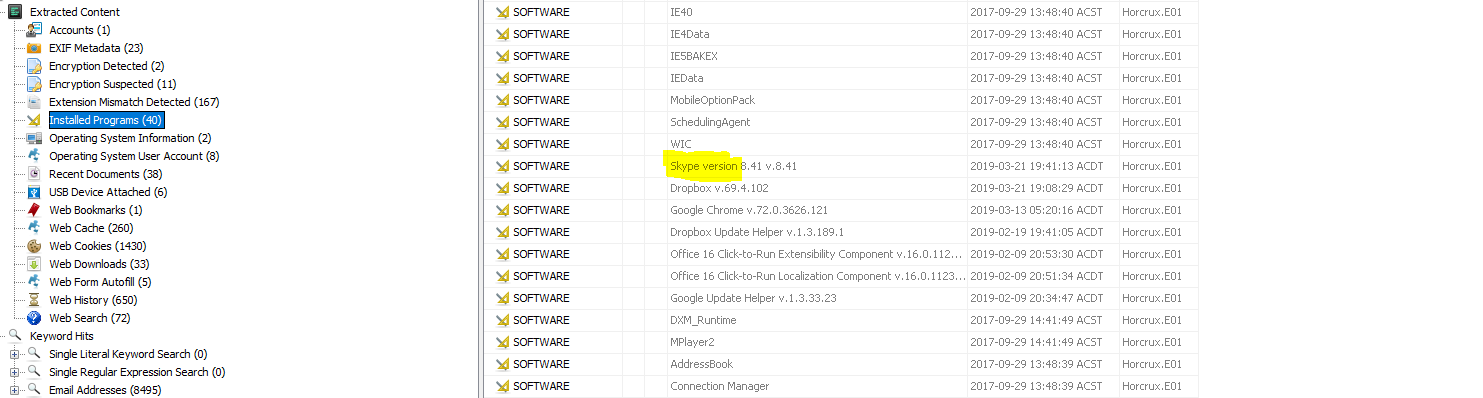
“A messaging platform was used to communicate with a fellow Alpaca enthusiest, what is the name of the software?”
Autopsy also extracts a list of “Installed Programs”. A quick look into this revealed Skype was the only popular messaging platform installed to the machine. Assuming this wouldn’t have been a different standalone binary, we now have our answer.
flag<Skype>
10. Zippy Zip - 15 Points
“What is the zipcode of Karen’s craigslist post?”
Autopsy has a ‘Web History’ section, and by looking within this we can see Karens zipcode on her Craiglist Post.
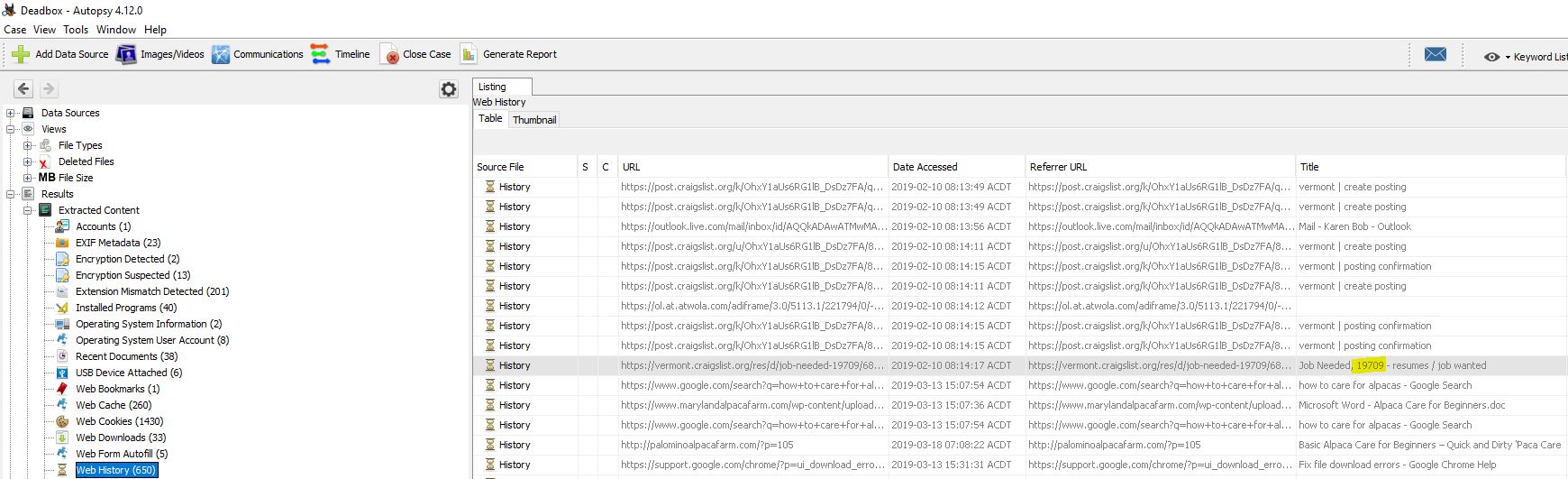
flag<19709>
11. New email, who dis? - 15 Points
“What are the initials of the person who contacted Karen”
To find this information, we need to find out how they contacted Karen. Given she was placing a job wanted advertisement on Craigslist, it was highly likely the contact method would be email. Looking at the Web Form Autofill section we can see a reference to Karen’s email address, [email protected].
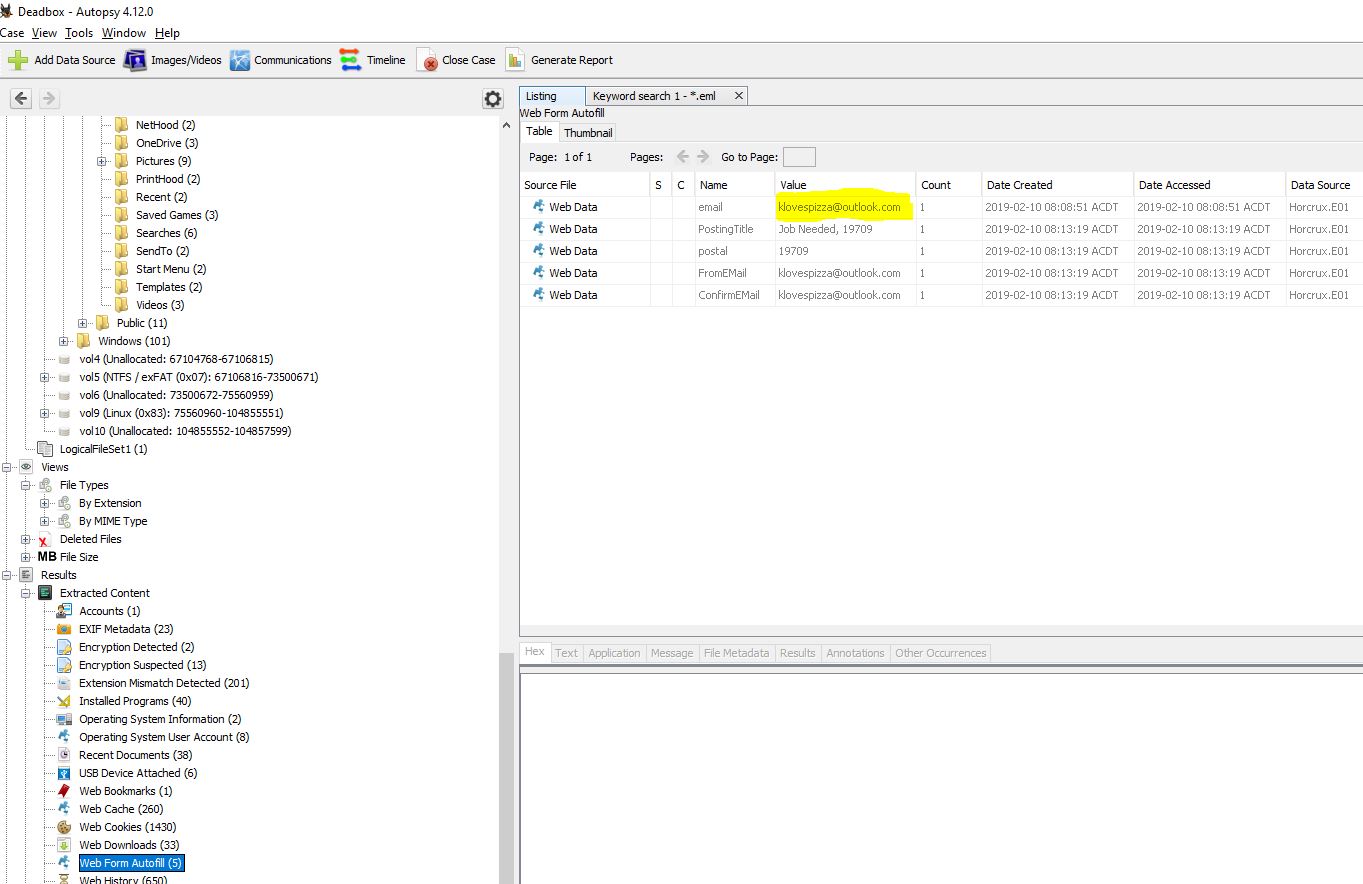
Running a keyword search for this we can find an OST (Offline Outlook Data) file of interest and where it is located.
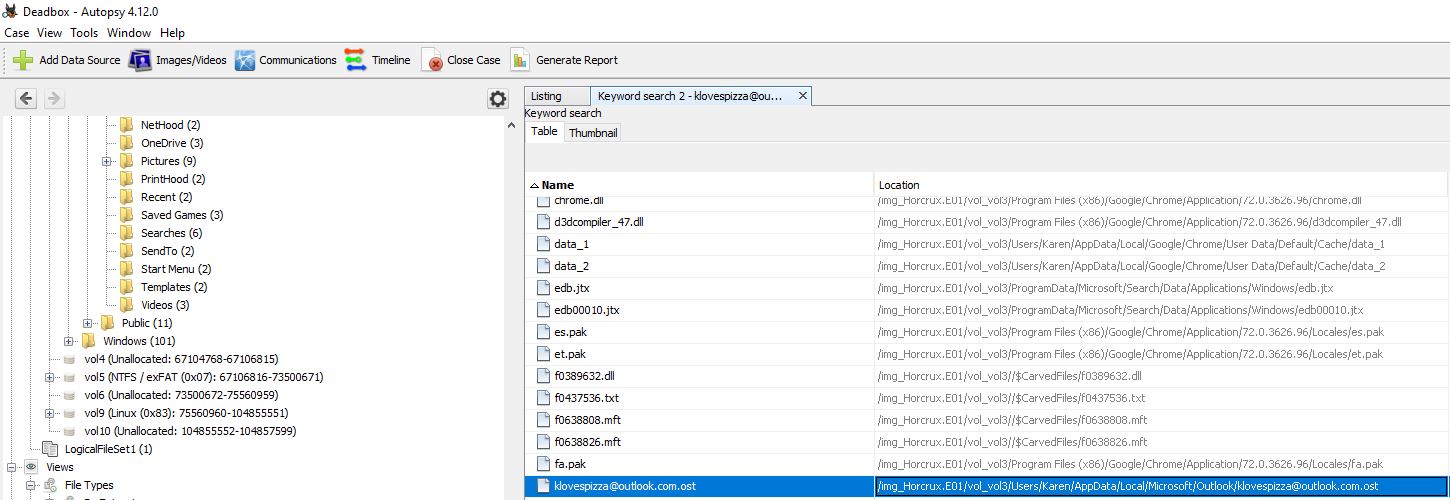
Within Autopsy we can simply extract this file from within the interface. After this we can move this to our Kali instance into its own folder and use the readpst tool within to parse the information into a manageable ‘mbox’ format with the below.
readpst [email protected]
Finally we can use the linux mail command to read these emails.
mail -f Inbox.mbox
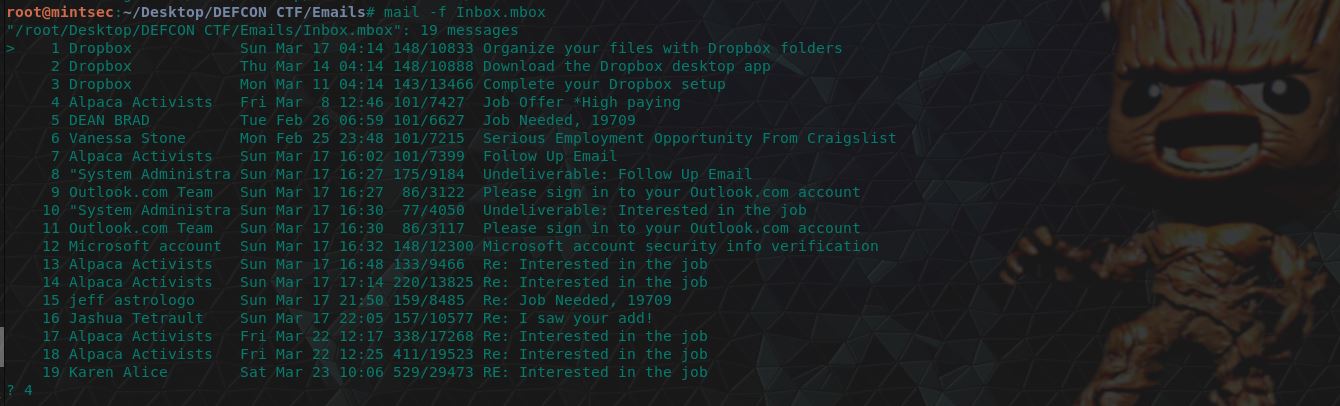
Searching through the “Alpaca Activists” email (number 4), we can find reference to a Michael Scotch which gives us the intitials required.
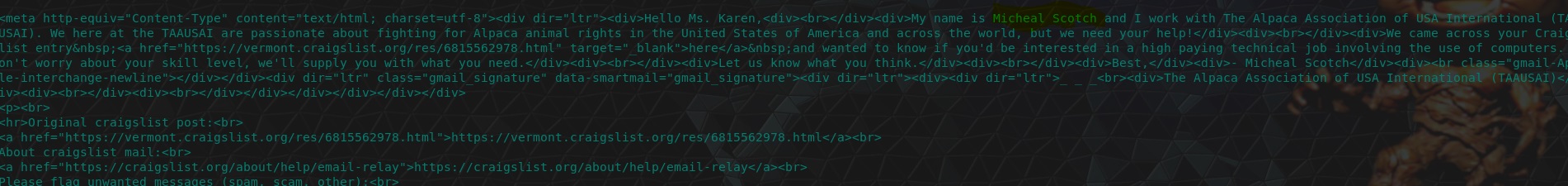
A bit of trivia, Michael Scotch is the name of a drink invented by Michael Scott from ‘The Office’. Michael Scott has also been known to play the part of Prison Mike, so in the true spirit of this CTF, I give you a classic Prison Mike quote.

flag<MS>
12. Make it rain! - 15 Points
“How much money was TAAUSAI willing to pay Karen upfront? Answer without commas or dollar signs.”
Looking through their follow up email (number 7) we can find the answer to this question.
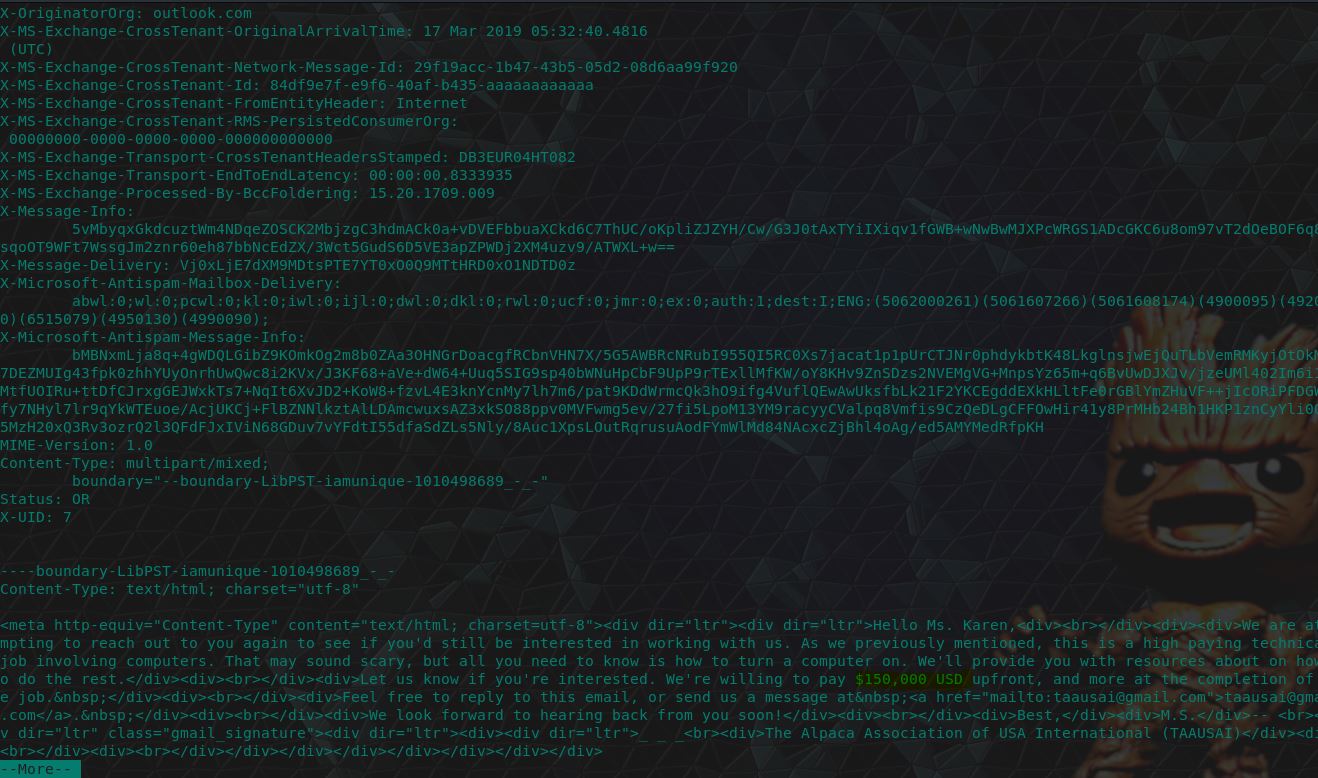
flag<150000>
13. You have no idea how high I can fly - 15 Points
“What country is Karen meeting the hacker group in?”
For this flag we actually need to go further into the email trail and look within the 17th email to find some coordinates. ‘27°22’50.10″N, 33°37’54.62’
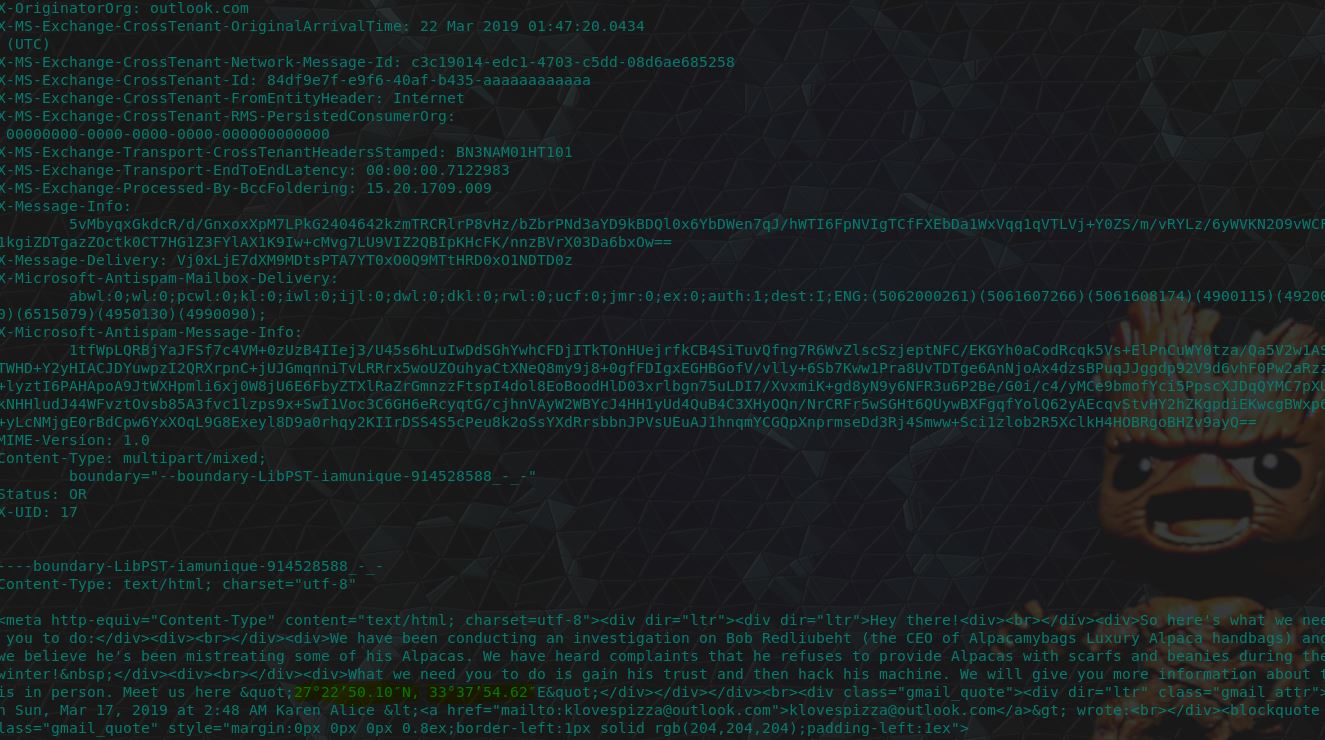
Looking these up within Google Maps reveals that it is coordinates to the Desert Breath which was created in 1997 in the Egyptian Desert.

flag<Egypt>
14. Where in the world is Carmen Sandiego? - 15 Points
“What is the timezone?”
This question was a little bit confusing, but if we take it to mean the timezone noted within the email headers, then we can see this is UTC time, which happens to bhe the correct answer.
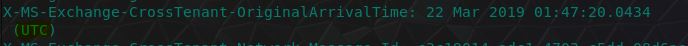
flag<UTC>
15. Someone actually read that? - 15 Points
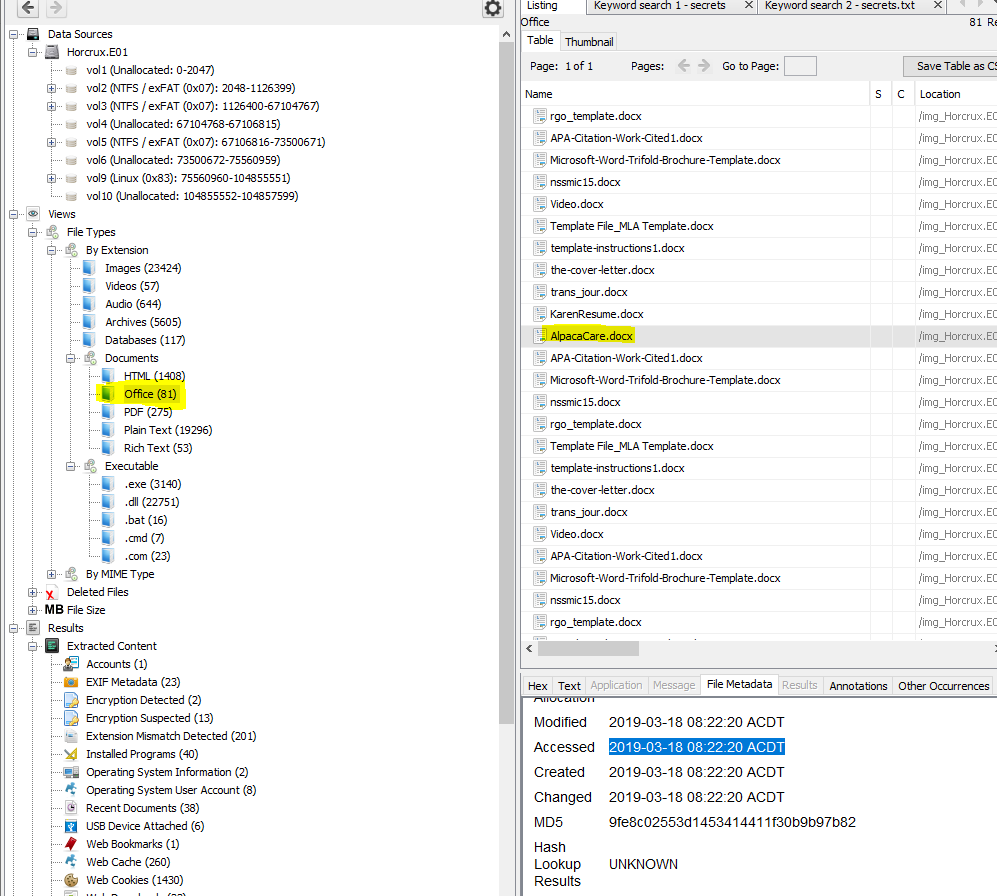
“What is the Last Accessed time for AlpacaCare.docx? Submit in UTC as MM/DD/YYYY HH:MM:SS in 24 format”
Within Autopsy we can find this file by looking at Office file extensions, the file metadata displays when it was last accessed.
After converting it to the appropriate UTC timezone we get the flag.
flag<03/17/2019 21:52:20>
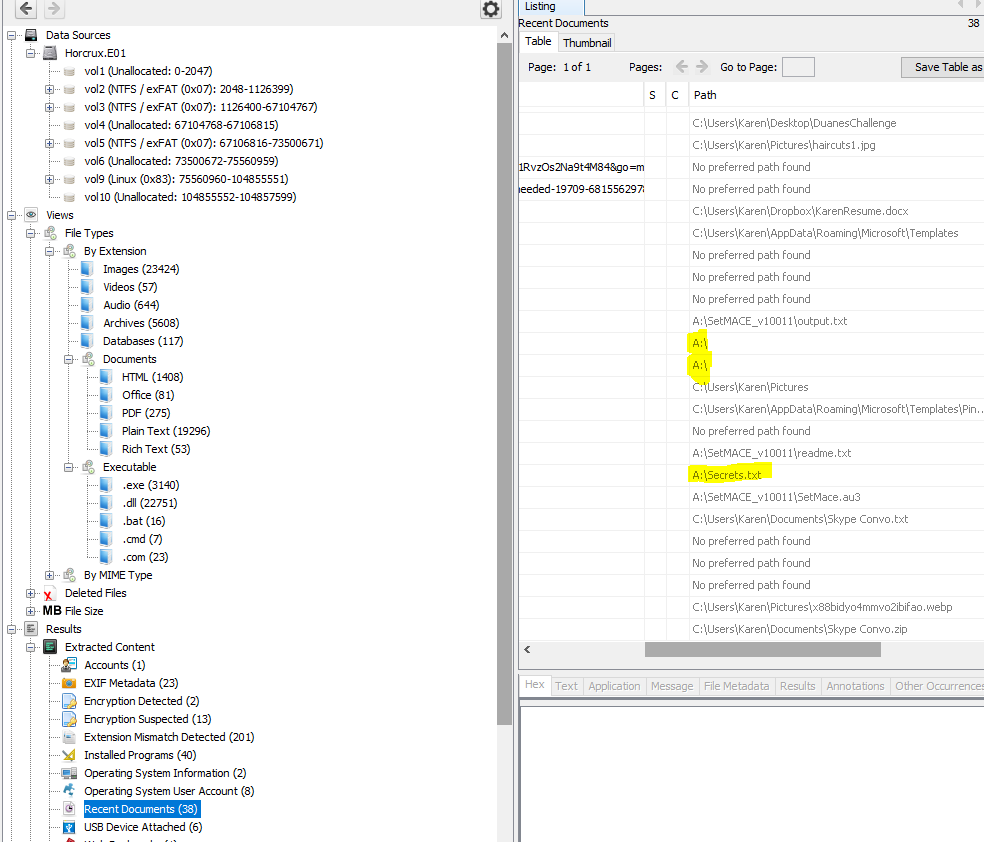
16. Partition Suspicion - 20 Points
“Karen had a second partition on the drive, what drive letter was it assigned?”
Looking at the Recent Docs section within Autopsy we can see many references to a second drive which was assigned the letter ‘A’
flag<A>
17. You’ve got questions? I’ve got answers - 20 Points
“What is the answer to the question Michael’s manager asks Karen?”
Jumping back into our Kali instance, we can find the following question within email 13 after cleaning out the div and break tags.
"So I may have lied, my manager is saying that before we can offer you a job, we need to give you a quick test. Can you tell me what the answer to the thing at the bottom is?
VGhlQ2FyZENyaWVzTm9Nb3Jl
Good Luck!"
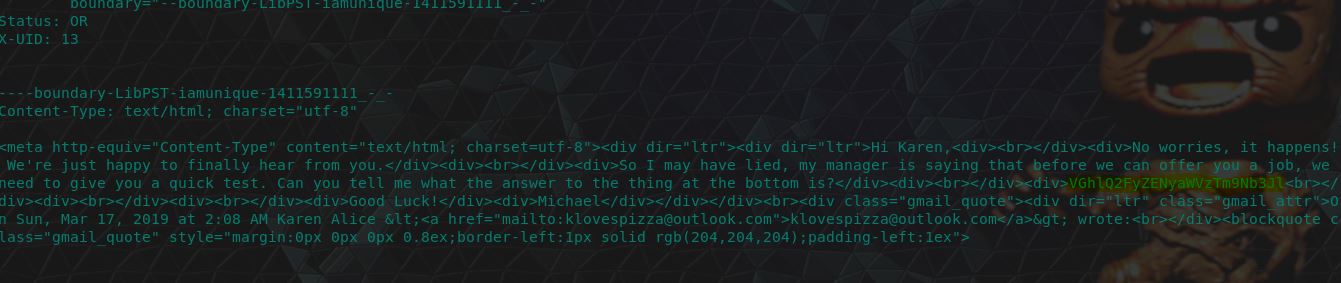
There’s 2 ways to go about this, we can easily base64 decode this using CyberChef, or we can find the answer in Karen’s sent items using:
mail -f 'Sent Items.mbox'
And then searching in sent email number 7. Although there’s a lot of noise due to the email trail we can find the answer in plaintext here.
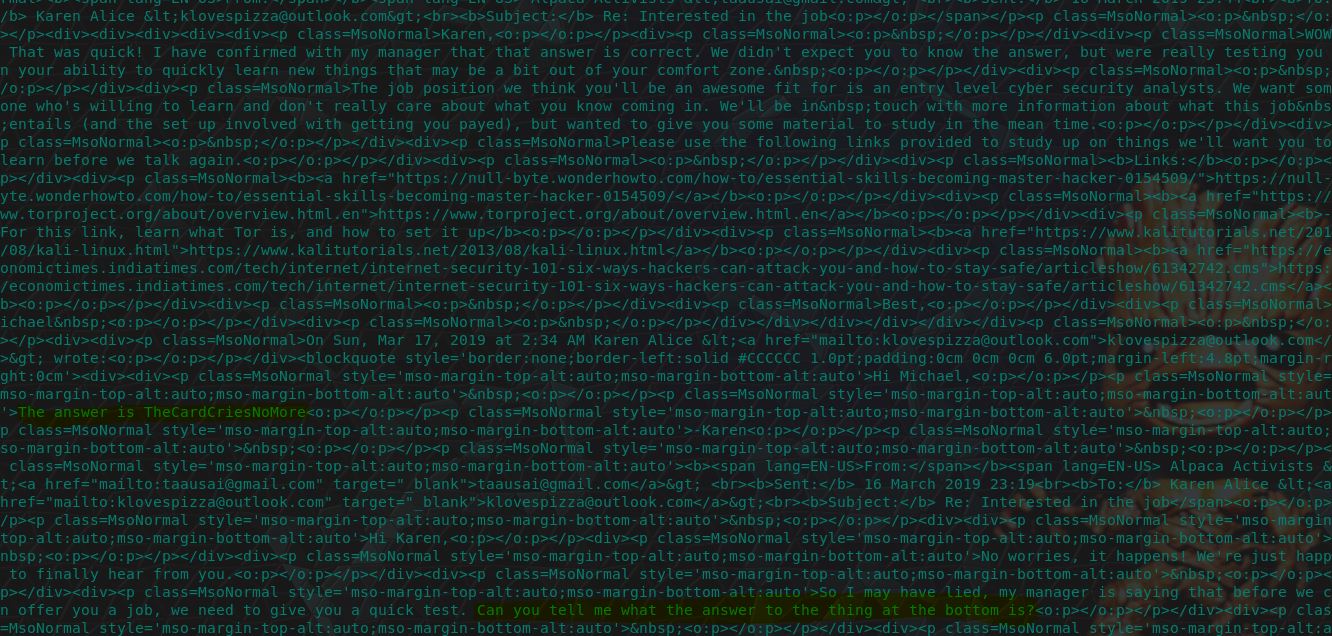
flag<TheCardCriesNoMore>
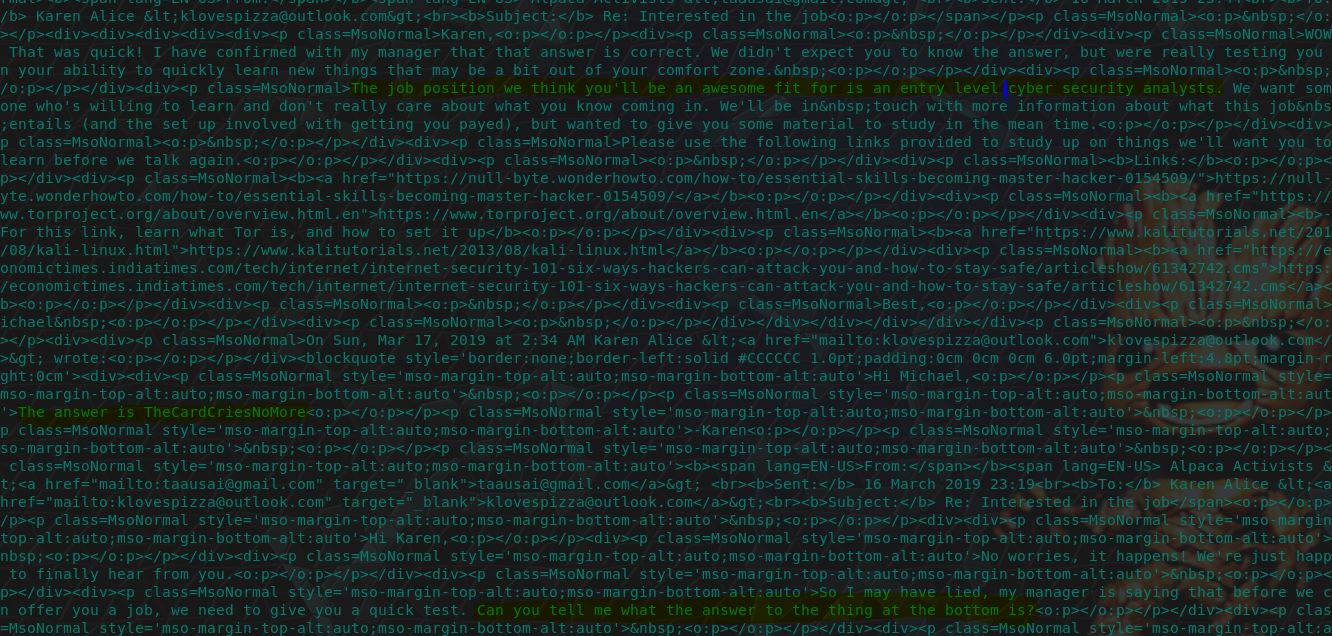
18. Recruit Pursuit - 20 Points
“What job is Karen told she is being considered for? Answer should be submitted with no spaces and all lowercase.”
Using the same sent email number 7, or ones within Karen’s inbox we can clearly see this answer as a (albeit misspelled) ‘cyber security analysts’.
flag<cybersecurityanalysts>
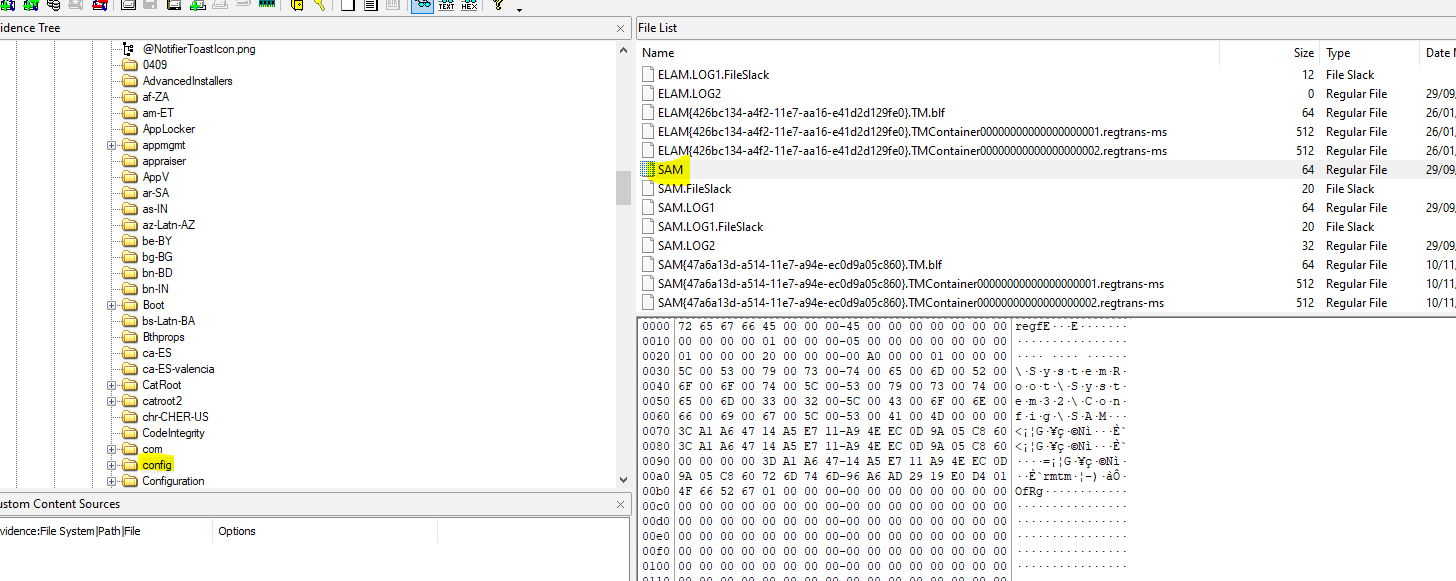
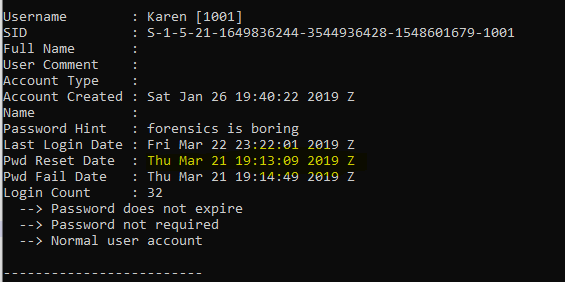
19. Oh, you’re not supposed to use the same password for everything…? - 20 Points
“When was Karens password last changed? Submit in UTC as MM:DD:YYYY HH:MM:YYYY in 24 format”
This leads us back into Autopsy for a bit of fun. We’re able to extract the SAM (Security Account Manager) Hive from this machine which is located at C:\Windows\System32\config\SAM.
From here we can use RegRipper by H. Carvey to extract the necessary information.
rip.exe -r "<SAMFile>" -f sam
Translating this to the necessary format we can find our flag.
flag<03/21/2019 19:13:09>
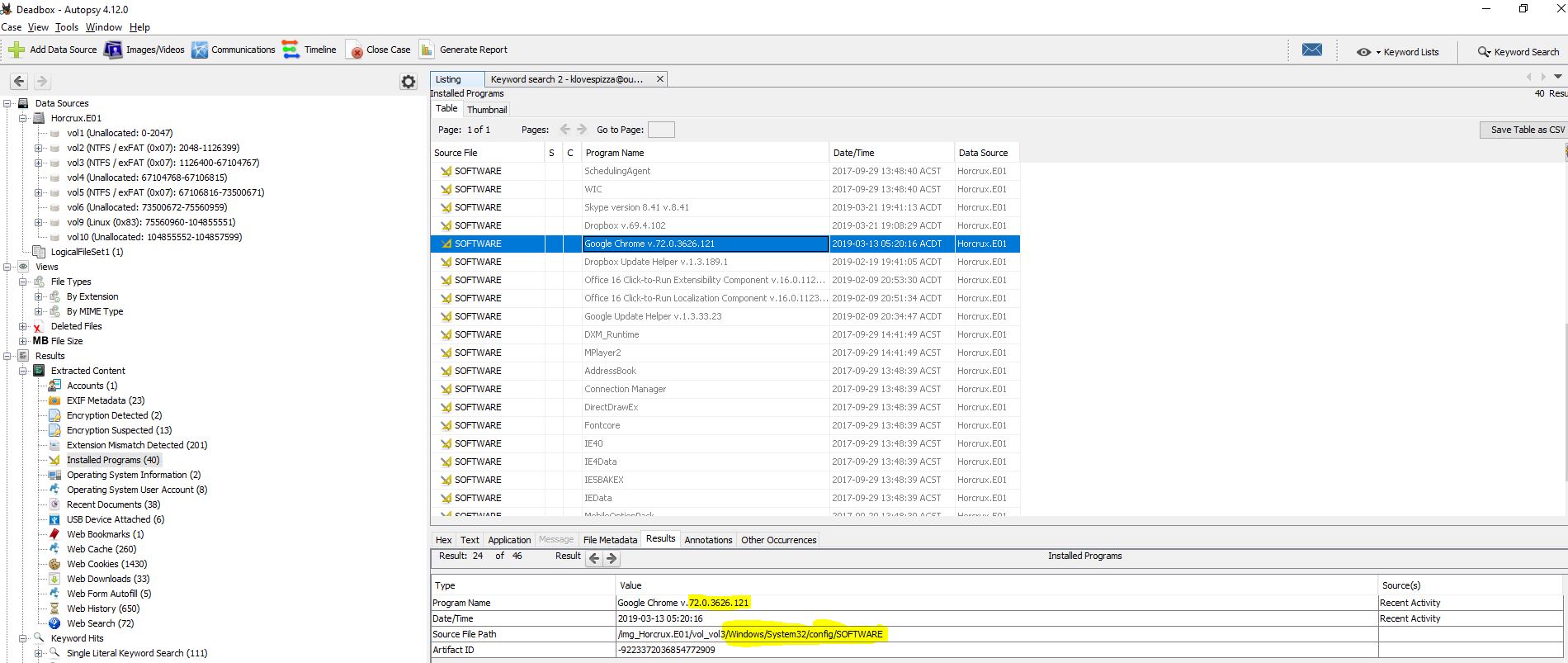
20. Are you sure you want to change your default browser? - 20 Points
“What Version of Chrome is installed on the machine?”
Once again an easy one for Autopsy. This information can be found under ‘Installed Programs’ and has automatically been dumped from the SOFTWARE hive, which saves us some time.
flag<72.0.3626.121>
21. iS tHiS sP@M? - 22 Points
“Karen received a reply to her craigslist ad from a fellow Alpaca enthusiast, what is the email address associated with this reply?”
Back into Kali once more, we can see that the first email received from ‘Alpaca Activists’ (email 4 again) has the below reply email.
From: "Alpaca Activists" <[email protected]>
This email was not accepted as the answer during submission, and as strange as this was I couldn’t figure out why. After collaborating with Evandrix here, he had been informed that there was a typo when placing the answer into the submission form, so although this is the correct answer there is actually a typo requiring a 3 to be changed to a 2.
flag<7066d7539fdf305[3][email protected]>
After changing this the flag was successfully submitted. Now’s probably a good time to throw this one out there…
flag<[email protected]>
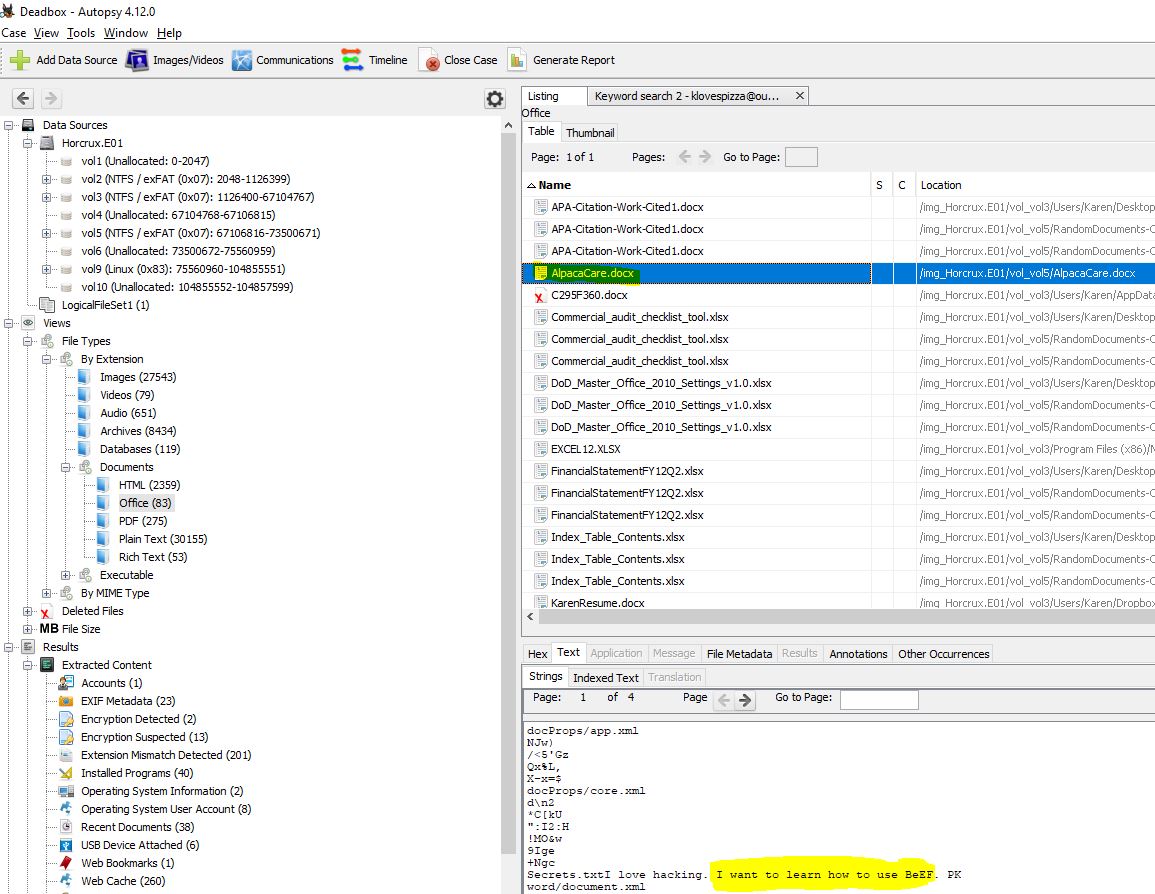
22. Moooooooooo - 30 Points
“What is the tool Karen hopes to learn to use? This question is case sensitive.”
Shuffle back to Autopsy (Alt+Tab sure is getting a workout by this point), and we can find a file called ‘AlpacaCare.docx’. Within this file we can see that there’s some strings which have been extracted which indicates Karen wants to learn how to use BeEF (Get it? The question is Mooooo, badum tskkkkk). Extracting this file for later will come in handy…
flag<BeEF>
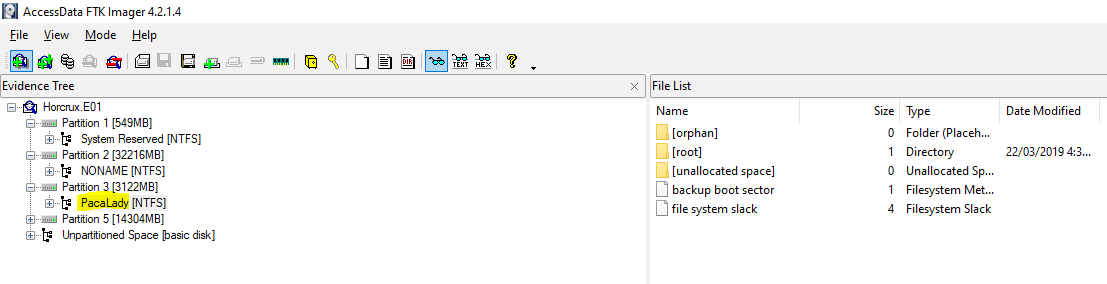
23. She’s a ladies man - 30 Points
“What was the volume name of the second partition on the laptop?”
At this point I started to hit a wall, so I had to bring out FTK Imager. Opening this up in FTK Imager mentioned that the second partition didn’t actually have a name; however, the third partition did.
Reading between the lines here, I went out on a limb and assumed the answer they’re expecting is actually that of the third partition in this case. This was the correct flag.
flag<PacaLady>
24. now with 99% more ads - 30 Points
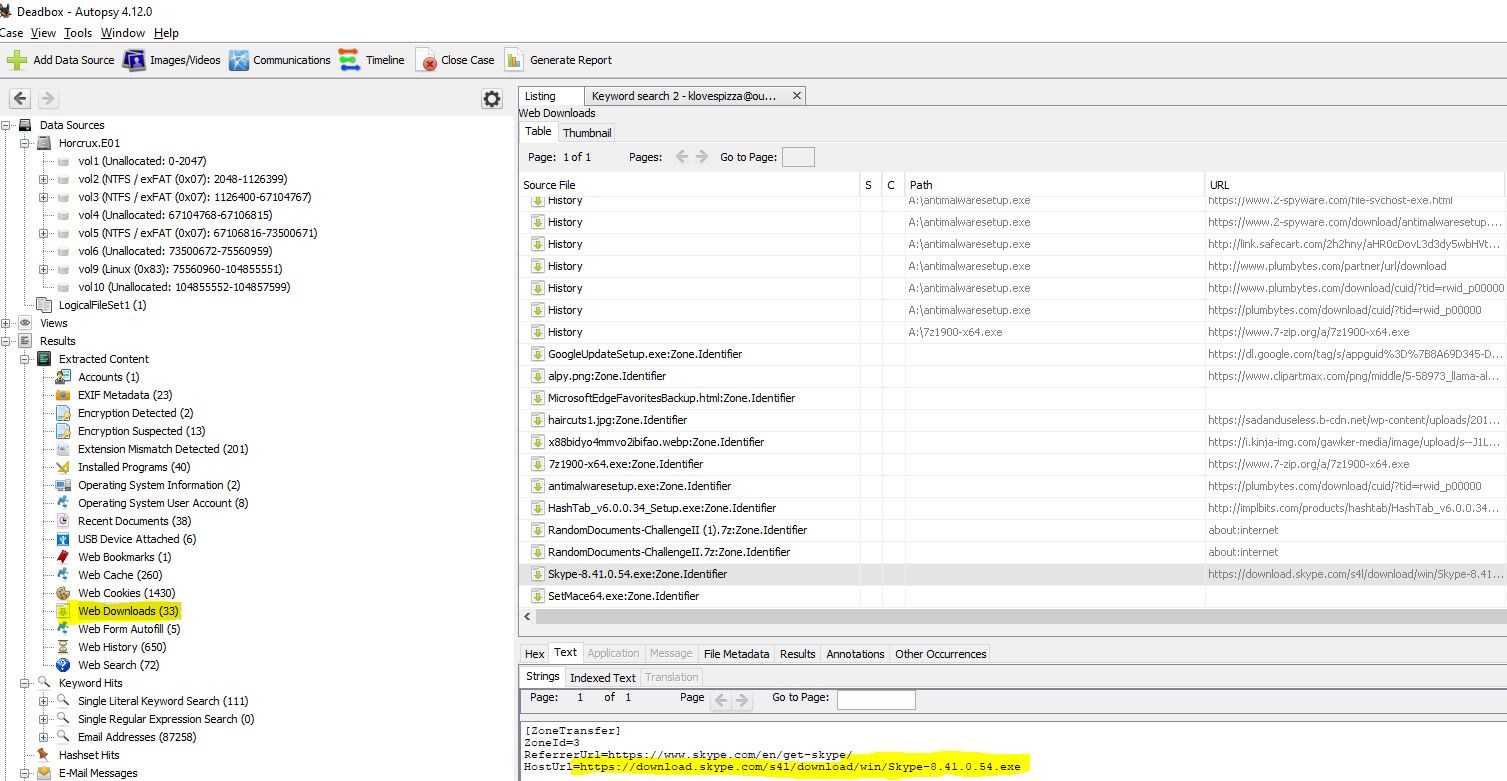
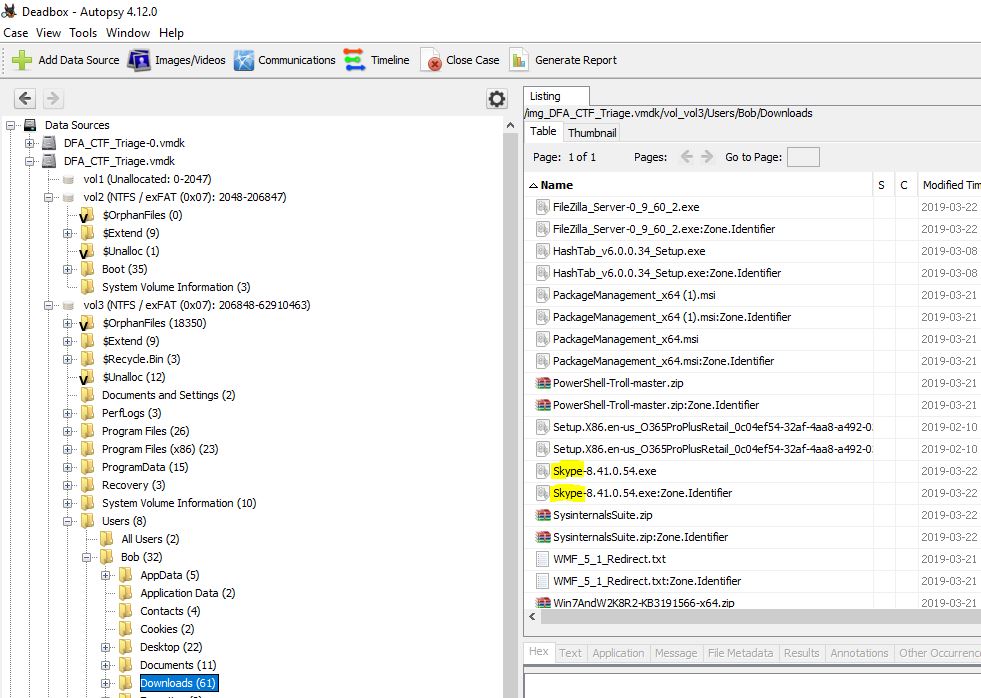
“What is the HostUrl of Skype?”
Shifting back to Autopsy for simplicity, we can find that the extracted Web Downloads contains the zone identifier for Skype.
After trying the host URL here with no luck, Evandrix mentioned that he’d found out it had to include the preceding ‘=’. Once again a bit of a strange way of submitting this flag but after this modification it went through a charm.
flag<=https://download.skype.com/s4l/download/win/Skype-8.41.0.54.exe>
25. her name is snow - 35 Points
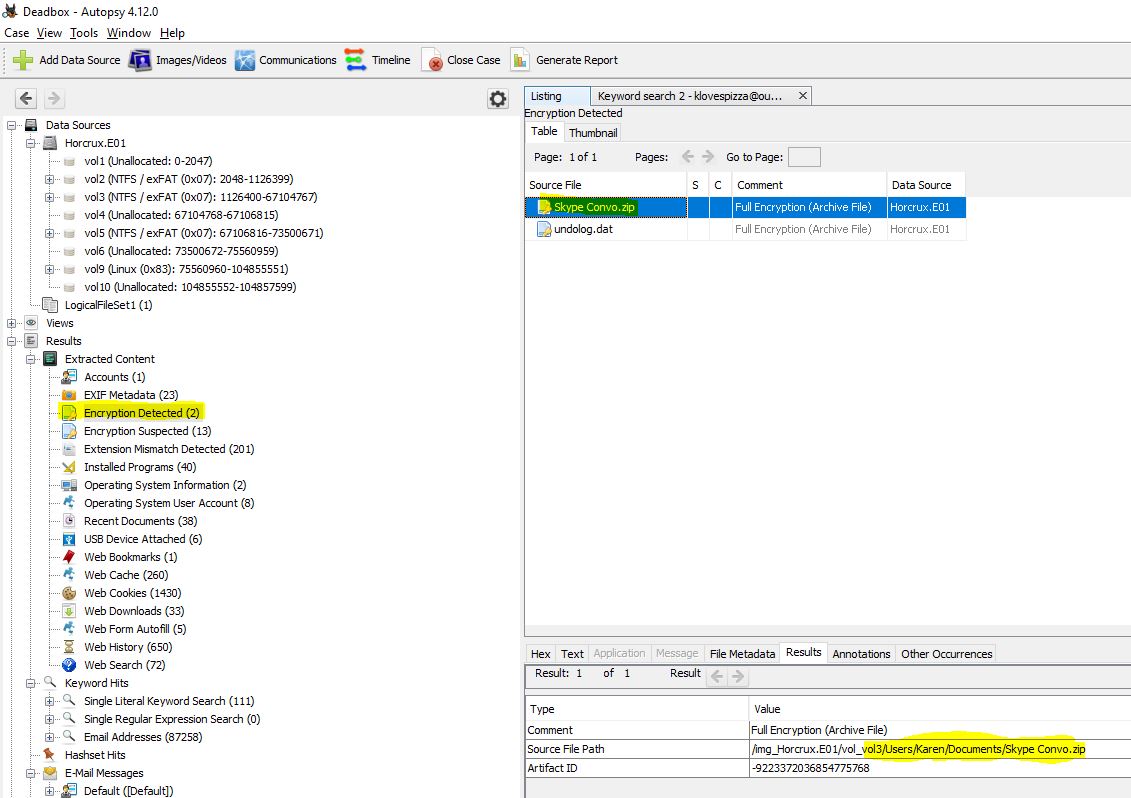
“Bob told Karen the name of his favorite Alpaca. What is the name?”
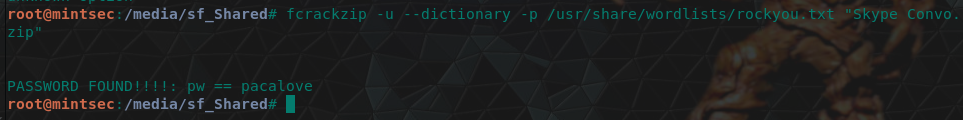
Alrighty, so for this we know Karen is using Skype to communicate with Bob. Luckily the Skype conversation has been encrypted and we can find this under the ‘Encryption Detected’ section of Autopsy.
Did I say lucky? I meant unlucky…I mean, lucky we can find it, unlucky it is encrypted. There’s a couple of ways of proceeding here, we can put on our red hat and crack it using fcrackzip and the rockyou.txt wordlist which come stock standard like so.
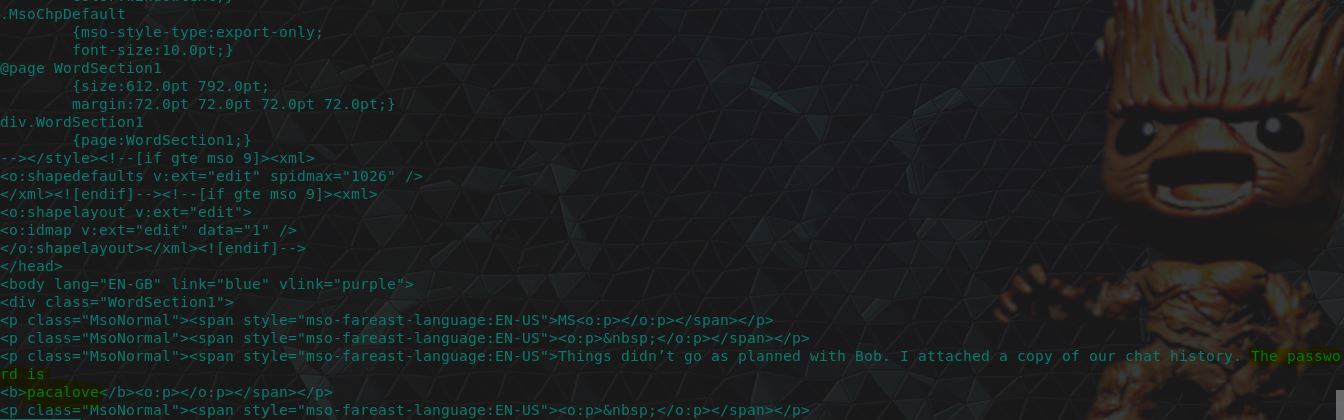
Or, we can find this in the email Karen sent to herself (email 19), or the corresponding sent items.
Either way we’re in! The skype conversation is as follows.
Karen, 19:45 (wave)
Bob, 19:46
Howdy
Karen, 19:46
OMG I'm so happy you answered!
Bob, 19:46
Why?
Karen, 19:46
I love people that love Alpacas!
Bob, 19:46
Oh wow. Me too!
Karen, 19:47
Although, I must inform you, your profile pic is a llama not a paca baby
Bob, 19:47
Yeah, I know. Its a test. I have to weed out the fakers.
Karen, 19:47
Oh I feel that.
Karen, 19:48
I hear you have a small business...
Bob, 19:48
Yup! Alpacamybags luxury alpaca handbags!
Karen, 19:48
So you don't think its wrong to turn a profit at your alpaca's expense...
Bob, 19:57
Not at all my favorite Alpaca, who's name is "MFDfMiTfMyHfMyHfMyj=" LOVES to be sheared!
Karen, 20:00
Interesting...
Karen, 04:22
Frick you bob.
Karen, 04:22
I heard you don't let your alpacas wear scarfs
Karen, 04:22
#pacasgetcoldtoo
Karen, 23:24
I'm sorry for yelling. Can we still be friends
…This deserves another meme!
So although that was the worst spy attempt in history, we did get the string ‘MFDfMiTfMyHfMyHfMyj=’. Time to head back to CyberChef. At first it looks like this string would just need a simple Base64 decoding, but this yields an unusual output.
0Pß2$ß3!ß3!ß3(
If we go back to what we know, it’s that ROT13 seems to be a common theme. This also yields an unusual result.
e$,fñ¬fU,fU,f\
Perhaps now it’s been changed up and isn’t ROT13, but rather a different rotation, performing ROT1 and then base64 decoding this provides us with a promising output which resembles Hex.
4a 65 72 72 79
Now if we change this back to a readable format we get the output ‘Jerry’. Once again this can be done using CyberChef.
flag<Jerry>
26. rev2md5 - 45 points
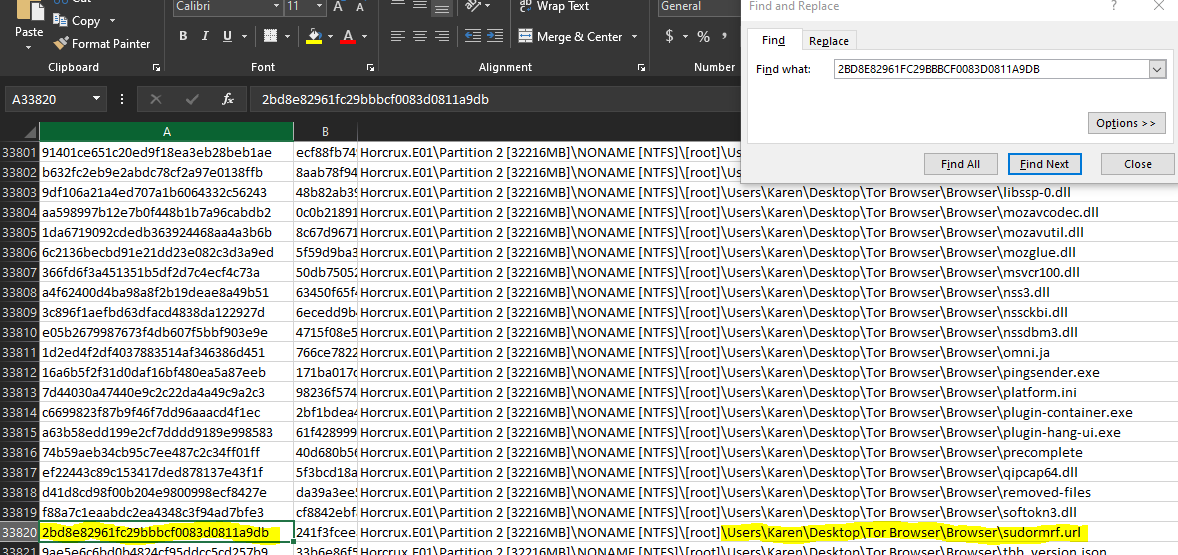
“Find the file with MD5 2BD8E82961FC29BBBCF0083D0811A9DB. It will lead you to victory.”
This is where FTK Imager begins to shine. For any partition we can dump out all of the file hashes to a spreadsheet using the GUI, and then search them for this specific file.
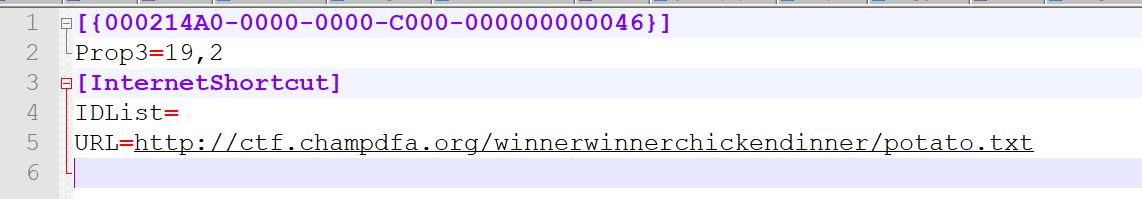
This leads us to a sudormrf link file (little bit of Linux admin humor for you there). Extracting this file and looking at where it is pointing leads us to a file http://ctf.champdfa.org/winnerwinnerchickendinner/potato.txt.
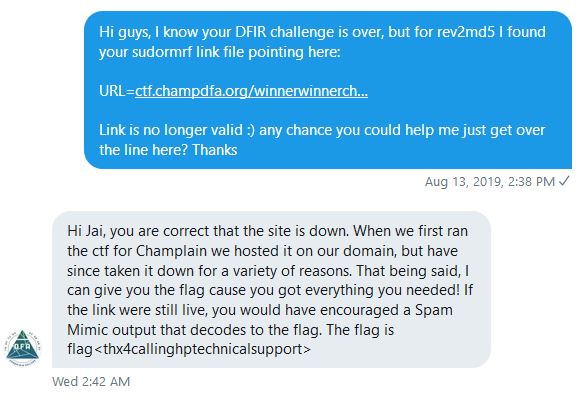
Unfortunately the domain is no longer active, and there are no historical records in the Wayback Machine or otherwise. Originally you had to contact @ChampDFA on Twitter with the relevant information and they would assist you in getting the flag, like so…
Since completing this though the challenge has been updated.
“Update: The link found from this file is no longer active. The flag has been updated to accept the full URL which the link points to. If you are having issues, please contact @ChampDFA on twitter.”
flag<thx4callinghptechnicalsupport>
flag<http://ctf.champdfa.org/winnerwinnerchickendinner/potato.txt>
27. AlpacaCare2020 - 75 Points
“What is the domain name of the website Karen browsed on Alpaca care that the file AlpacaCare.docx is based on?”
Although this could be found in the web browsing history, we can actually get this information from the AlpacaCare document we extracted earlier (you did extract it right?). Opening up the file in Word, we can see it has a copyright logo with a link to the website it is from.
Once again, this question hoodwinked me, it wasn’t the full domain of palominoalpacafarm.com which was required, we have to drop the suffix of ‘.com’
flag<palominoalpacafarm>
28. You have secrets? - 75 Points
“What is the Created Timestamp for the secret file? Submit in UTC as MM/DD/YYYY HH:MM:SS in 24 format. Hint: Secrets are best kept hidden in plain sight.”
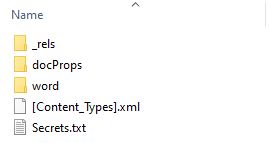
If we think back to our previous challenge where we found the answer BeEF, this was actually in a secrets.txt document inside of this word document. Word documents are actually archives, and an easy way to get this file is to just unzip the word document as if it was a zipped file (rename if you like, use 7-Zip, it’s up to you).
After converting your timestamp to UTC you get the required answer.
flag<03/25/2019 08:23:45>
29. DrDD - 150 Points
“Duanes Challenge: Duane Dunston had his passwords hijacked. Karen hid them C:\Users\Karen\Desktop\DuanesChallenge somewhere, what is the password to Duane’s LinkedIn?”
This directory has a lot of junk in it. After extracting them all and browsing through the files we find that one of the PDF’s has a base64 encoded appended after the end of the file.
South_Carolina_Academic_Standards_and_Performance_Indicators_for_Science_2014.pdf
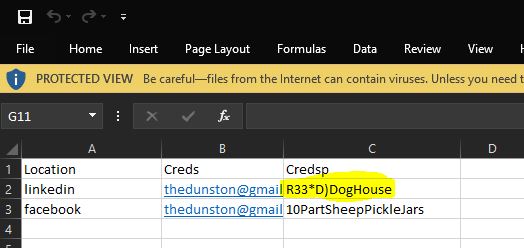
Throwing this into CyberChef we can see it neatly decodes to what appears to be a spreadsheet.
By downloading the file and opening it in excel, we can see the credentials, and at this point have our flag.
flag<R33*D)DogHouse>
Category: Linux Forensics
01. red star - 10 Points
“What distribution of Linux is being used on this machine?”
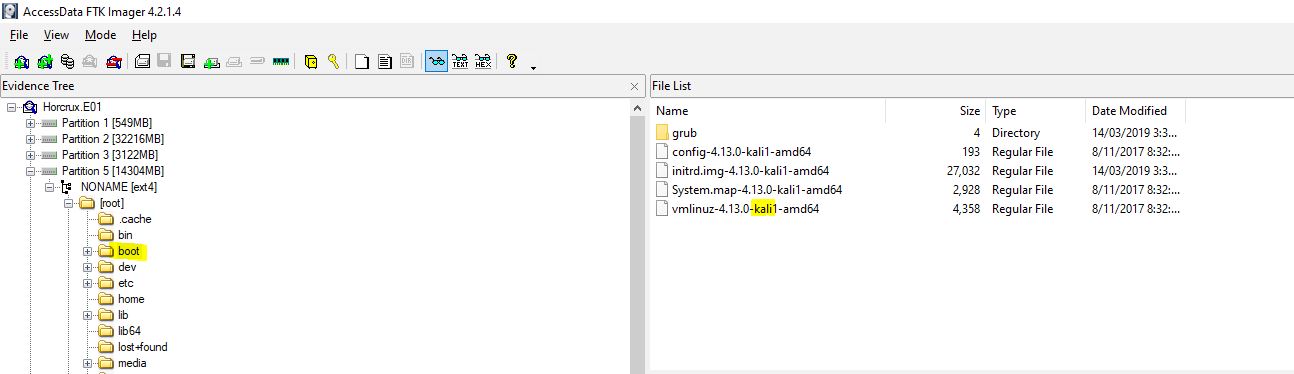
Using FTK Imager we can see Partition 5 is a linux partition with the boot section indicating it is Kali.
flag<Kali>
02. abc123 - 10 Points
“What is the MD5 hash of the apache access.log?”
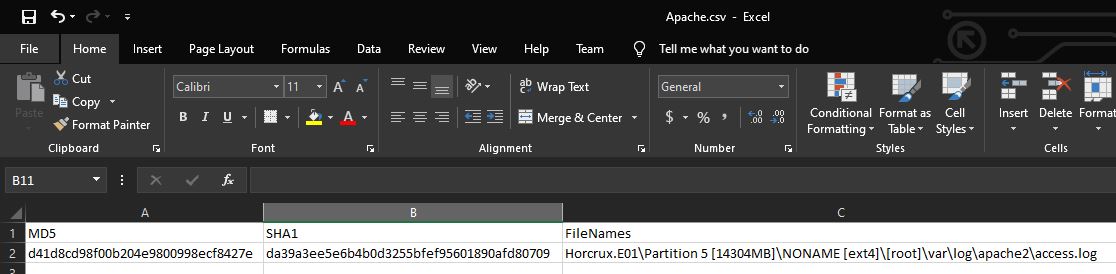
Using FTK Imager we can get this by right clicking the file, selecting Export File Hash List, and then viewing the spreadsheet output. The apache access.log is found at ‘/var/log/apache2/access.log’
flag<d41d8cd98f00b204e9800998ecf8427e>
03. Radiohead - No Surprises - 10 Points
“It is believed that a credential dumping tool was downloaded? What is the file name of the download?”
Looking at the root downloads section we can see that Mimikatz was downloaded. If you don’t know about Mimikatz, go check out GentilKiwi AKA Benjamin Delpy. Fun fact at the time of writing Windows Defender has a signature which means if the text ‘Invoke-Mimikatz’ comes up anywhere in a command line it will flag it as a Trojan. This includes naming a picture ‘Invoke-Mimikatz’ and then trying to edit it with paint. This will even include Windows Defender itself
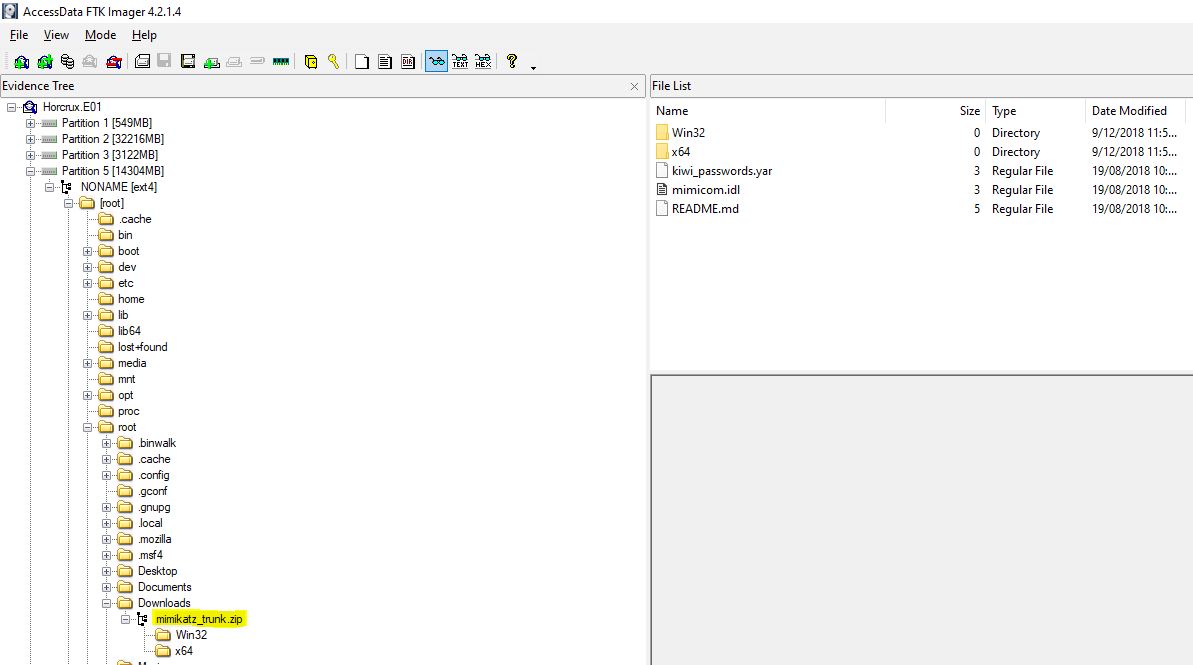
flag<mimikatz_trunk.zip>
04. super duper secret - 15 Points
“There was a super secret file created, what is the absolute path?”
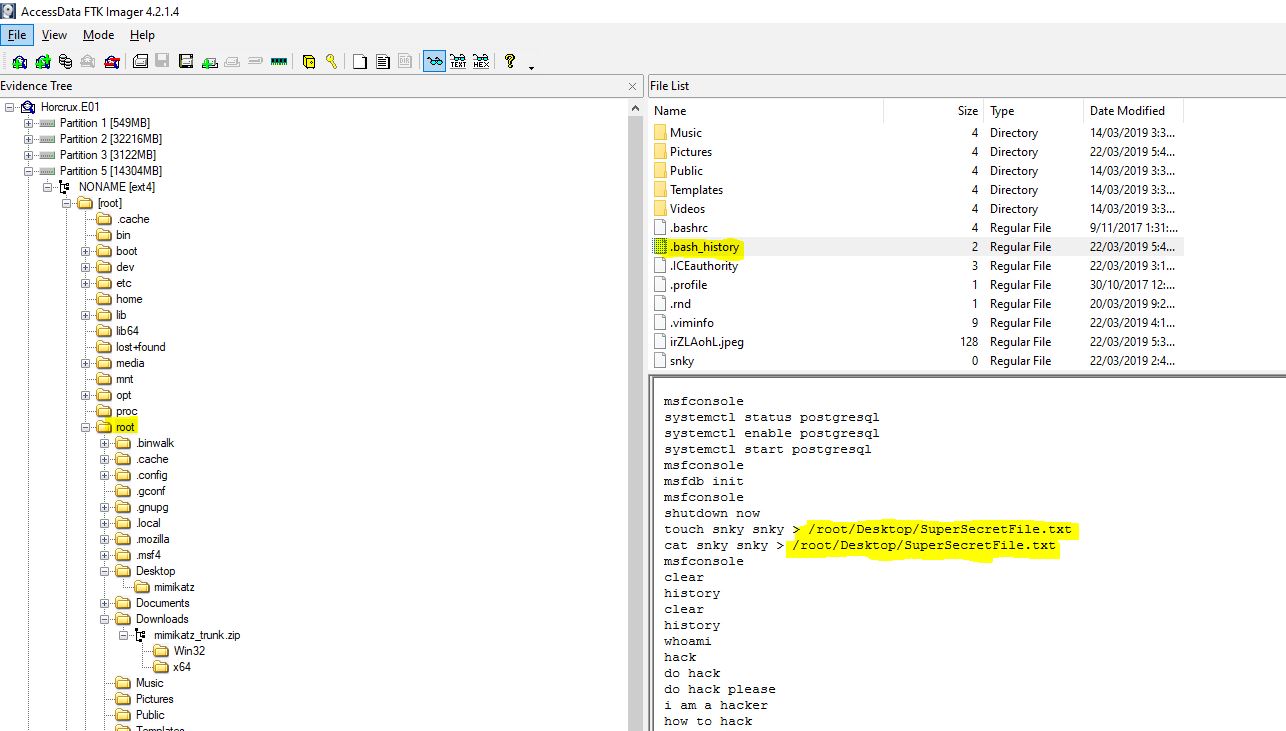
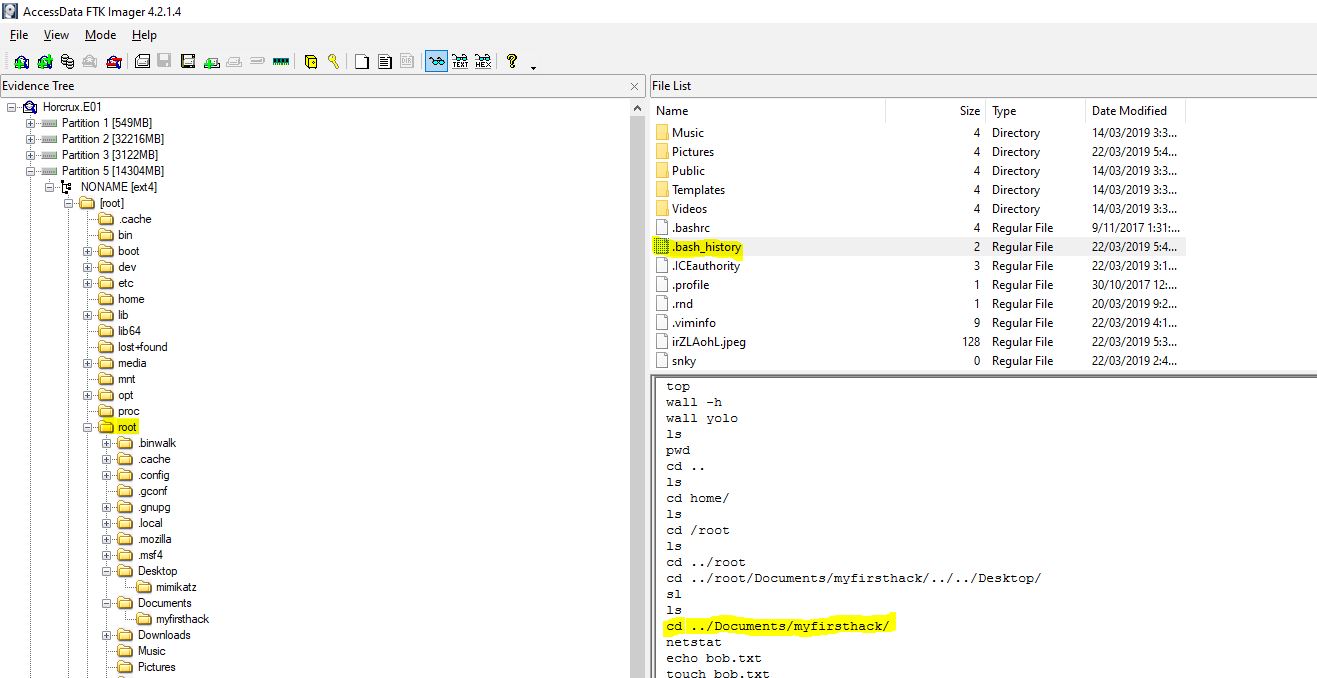
Looking into the bash history for the root user, we can see that a super secret file was created previously on the desktop.
flag</root/Desktop/SuperSecretFile.txt>
05. this is a hard one - 15 Points
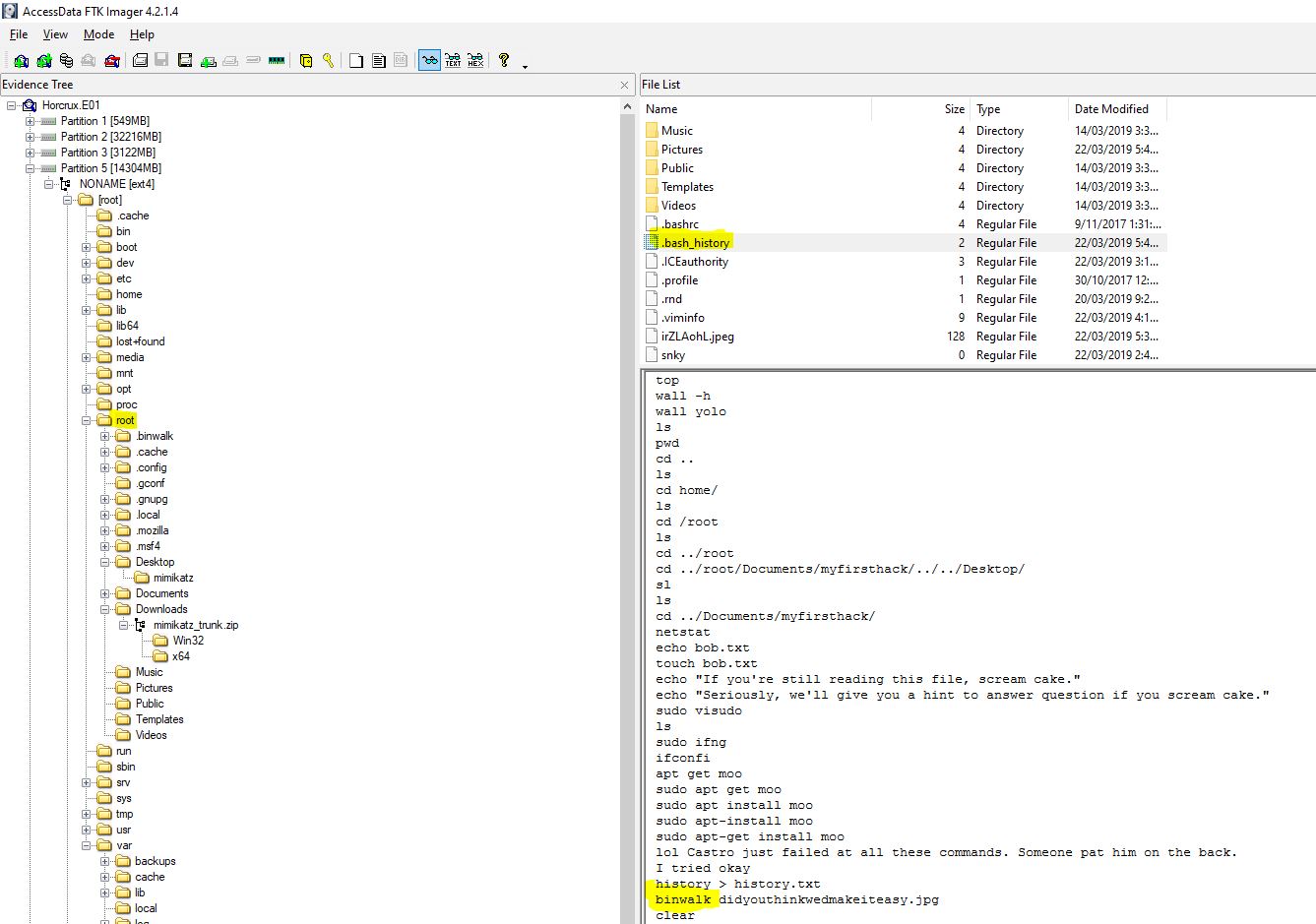
“What program used didyouthinkwedmakeiteasy.jpg during execution?”
Keep scrolling, no really just keep scrolling down the bash history.
flag<binwalk>
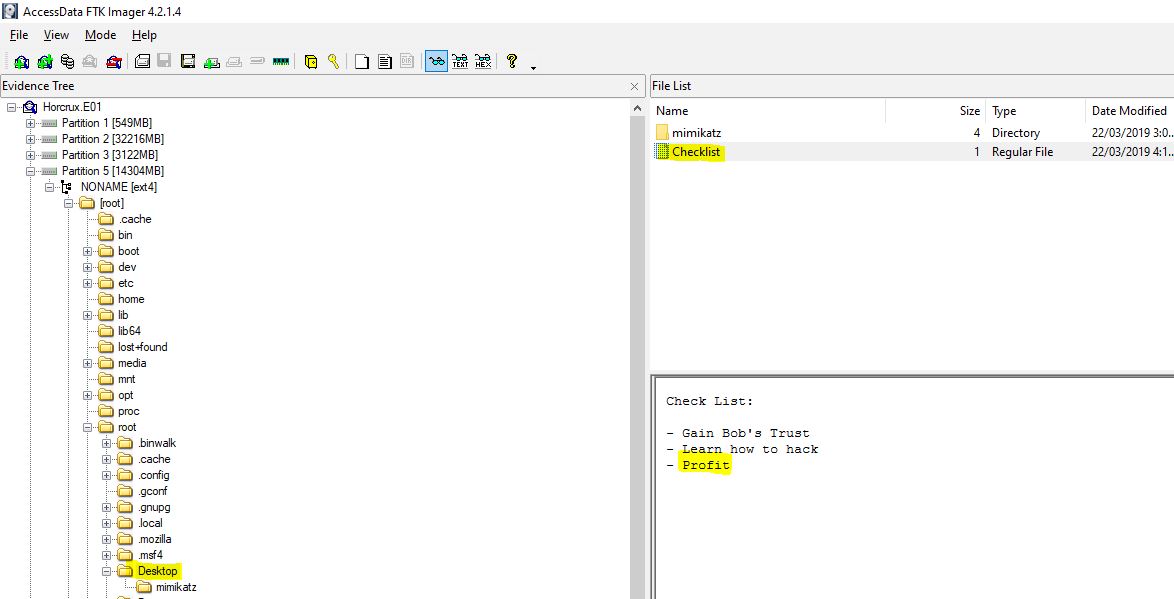
06. overachiever - 15 Points
“What is the third goal from the checklist Karen created?”
On the desktop where we also find Mimikatz, we can can see a checklist.
flag<Profit>
07. attack helicopter - 20 Points
“How many times was apache run?”
This is a bit of a trick question, looking at /var/log/apache2/access.log which we previously got the hash for, we can see that this is 0 bytes, which seems to indicate Apache was never run.
flag<0>
08. oh no some1 call ic3 - 25 Points
“It is believed this machine was used to attack another, what file proves this?”
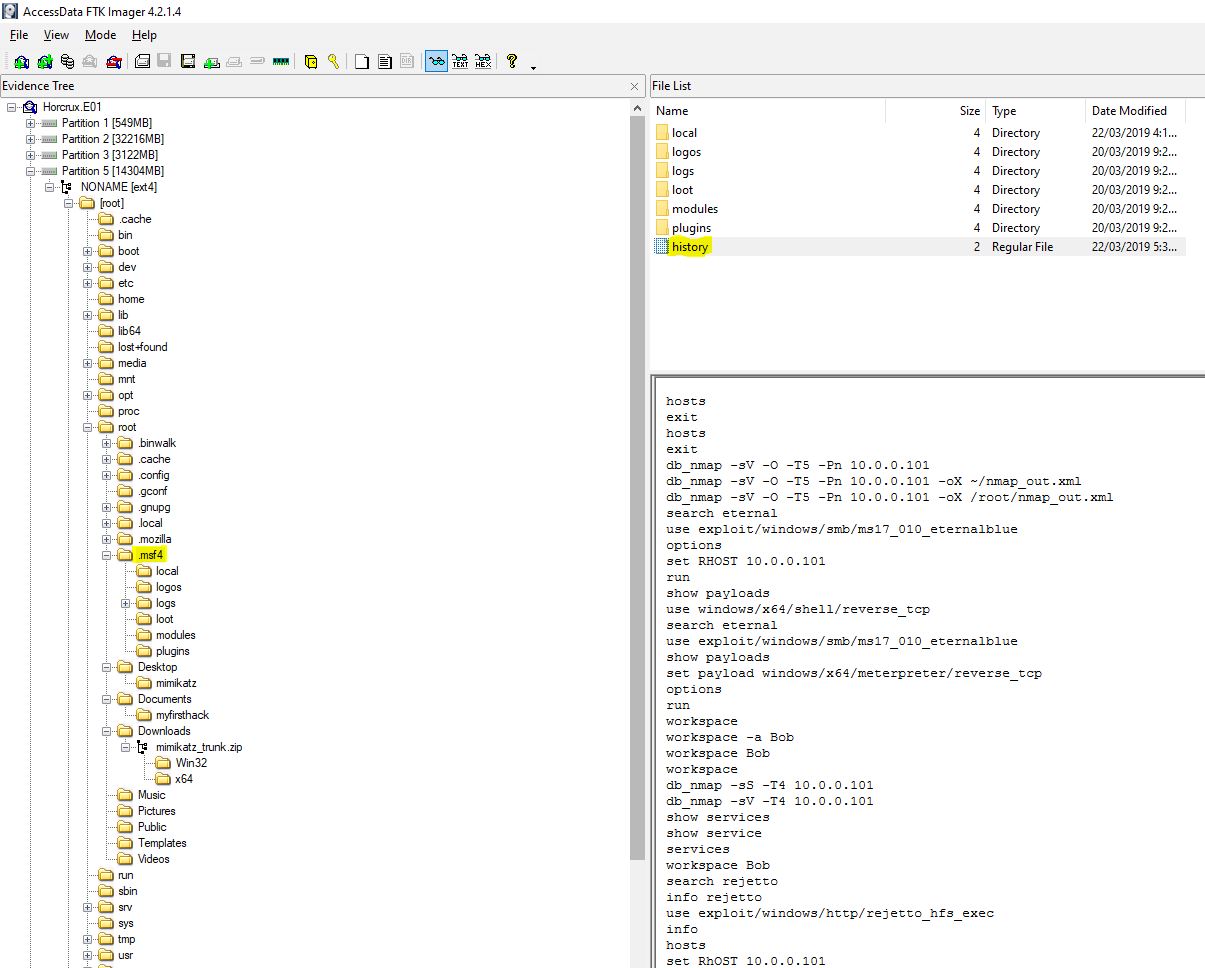
An ambiguous question, if you decided to go with the metasploit framework history file which clearly shows an attack, you would be wrong.
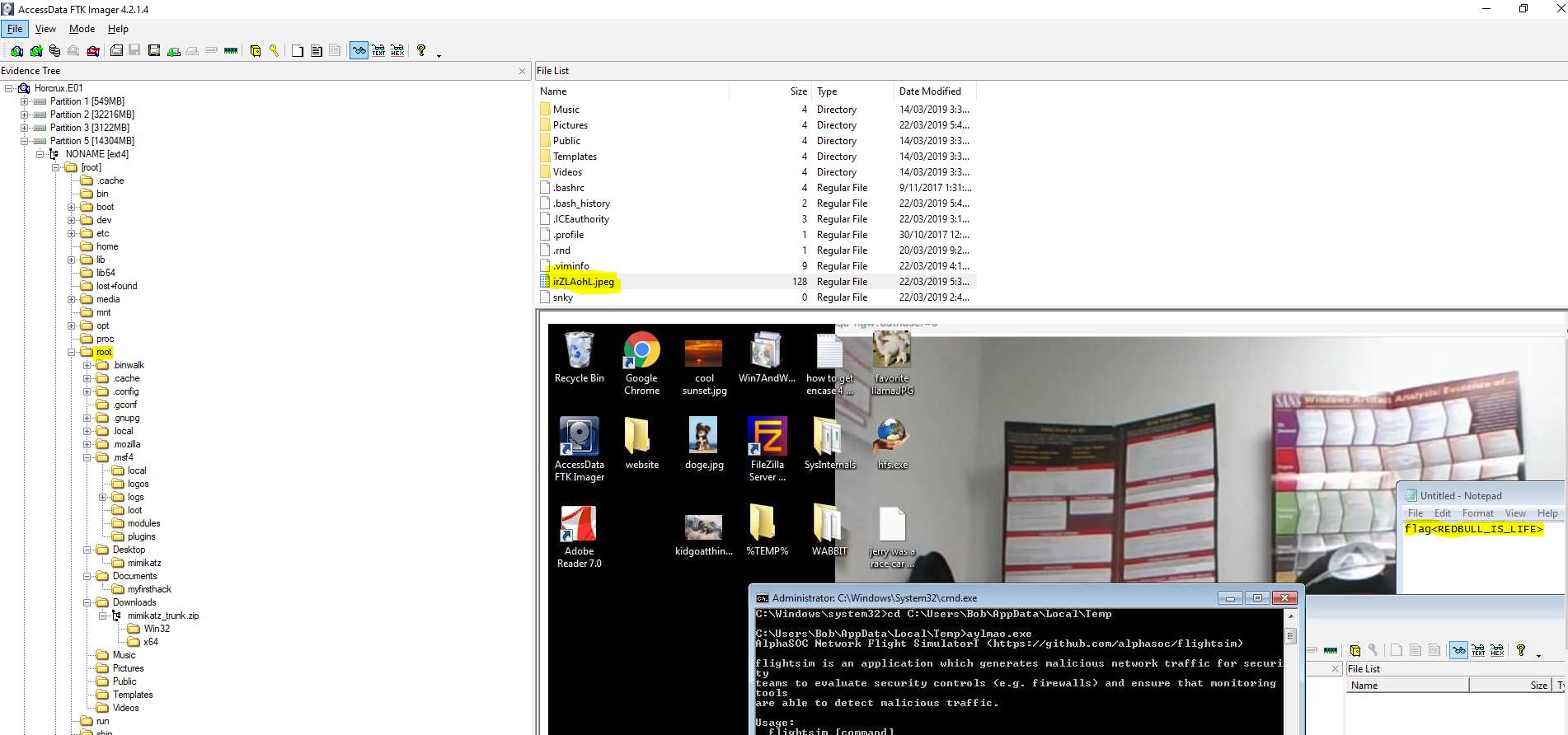
This could have been tampered with, after all it is just text. So the answer we’re actually looking for is a screenshot taken of the hacked machine’s desktop located in the root directory.
It may also be important to note the flag mentioned in the notepad file, so we’ll keep this in our back pocket…
flag<irZLAohL.jpeg>
09. scripters prevail - 25 Points
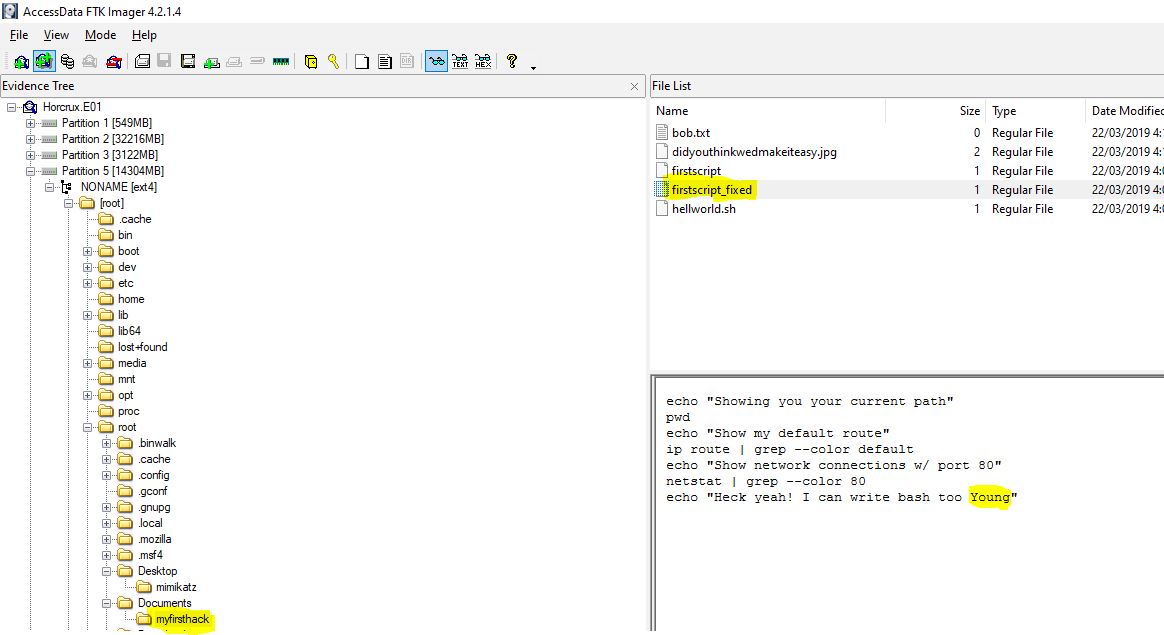
“Within the Documents file path, it is believed that Karen was taunting a fellow computer expert through a bash script. Who was Karen taunting?”
Looking in documents, we find a directory named ‘myfirsthack’, worst criminal ever… moving right along, this contains a script which echos the output “Heck yeah! I can write bash too Young”, and with this we have our answer.
flag<Young>
10. the who - 30 Points
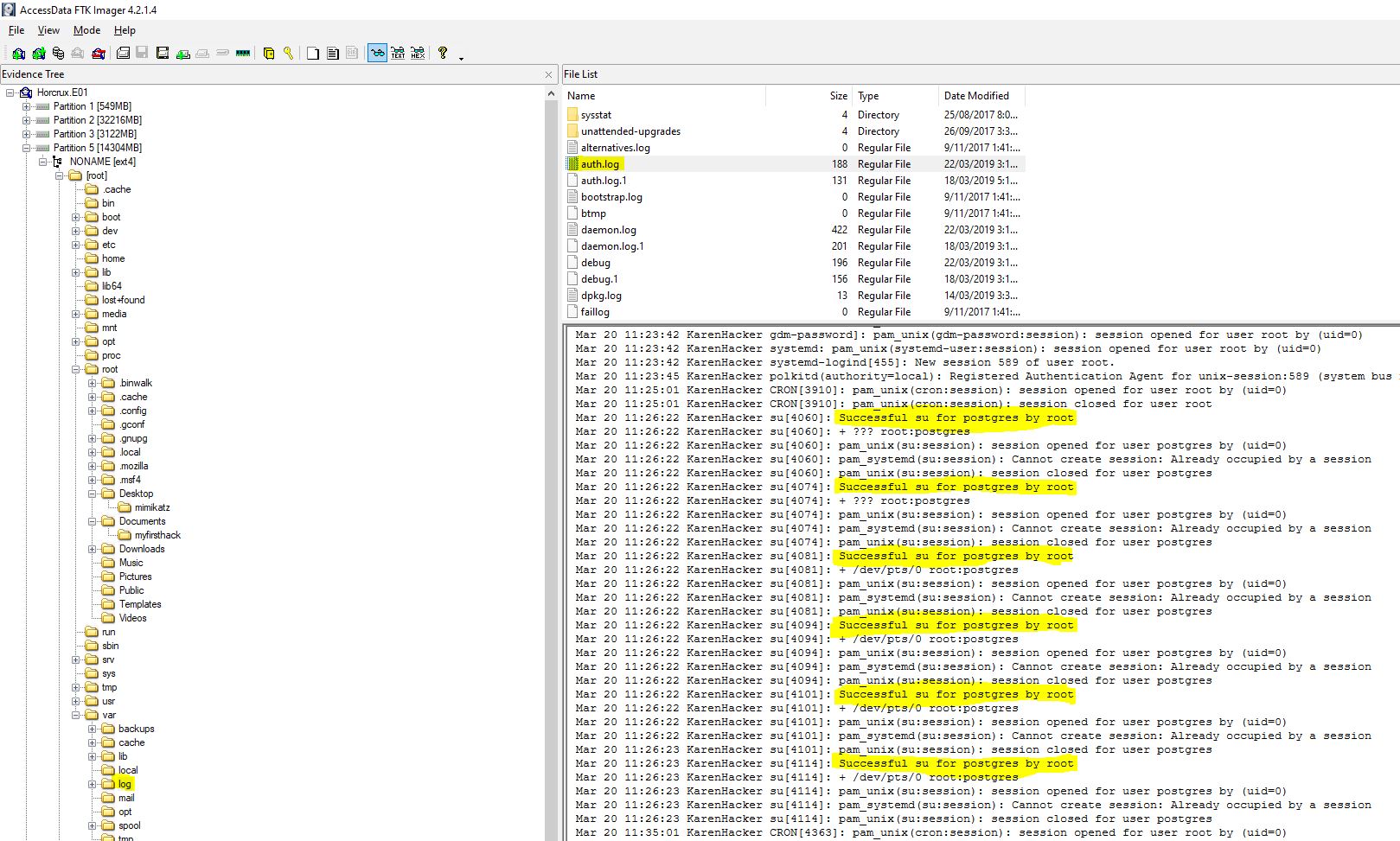
“A user su’d to root at 11:26 multiple times. Who was it?”
Looking through the auth log located at: /var/log/auth.log we can see that postgres su’d to root multiple times.
flag<postgres>
11. / - 30 Points
“Based on the bash history, what is the current working directory?”
Revisiting the bash history all we need to do is locate the last directory changed to in the log.
flag</root/Documents/myfirsthack>
Category: Memory Forensics
01. get your volatility on - 5 Points
“What is the SHA1 hash of triage.mem?”
We can safely assume that triage.mem is in reference to the memory file we downloaded called Triage-Memory, so I renamed it and went ahead getting the filehash with powershell.
gi *.mem|filehash -Algorithm SHA1

flag<C95E8CC8C946F95A109EA8E47A6800DE10A27ABD>
02. pr0file - 10 Points
“What profile is the most appropriate for this machine? (ex: Win10x86_14393)”
Using Volatility we can get this information from our Kali VM in a couple of ways.
volatility -f triage.mem imageinfo
volatility -f triage.mem kdbgscan
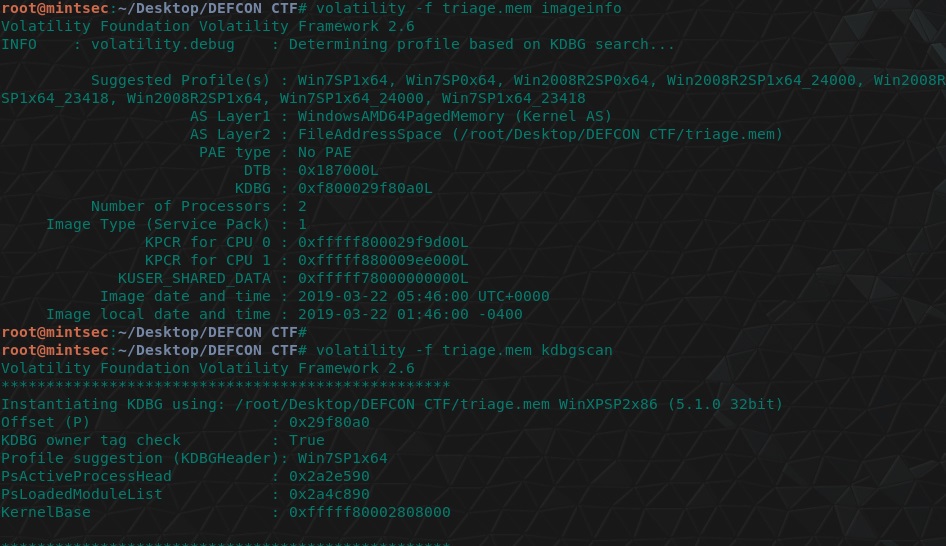
flag<Win7SP1x64>
03. hey, write this down - 12 Points
“What was the process ID of notepad.exe?”
Volatility has a psscan module we can use for this.
volatility -f triage.mem --profile=Win7SP1x64 psscan
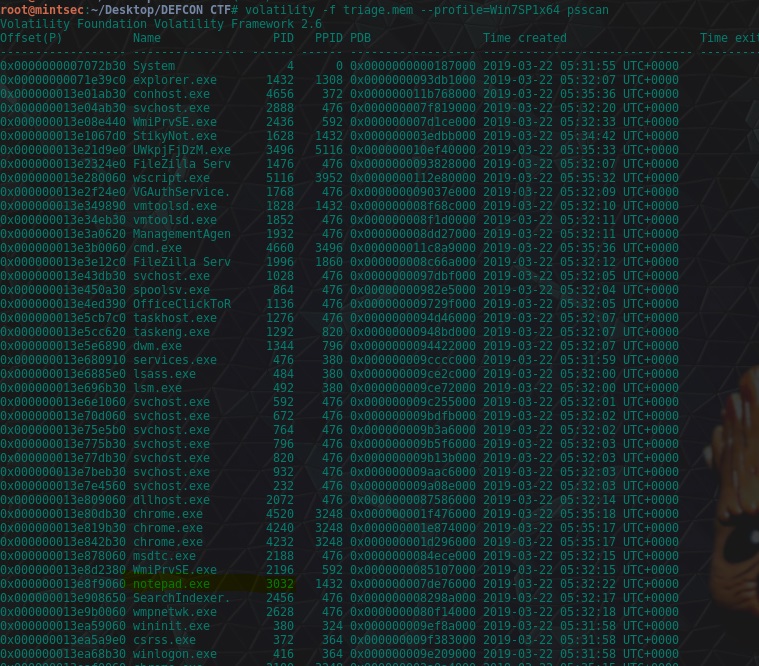
flag<3032>
04. wscript can haz children - 14 Points
“Name the child processes of wscript.exe.”
This is revealed in the previous question.
volatility -f triage.mem --profile=Win7SP1x64 psscan
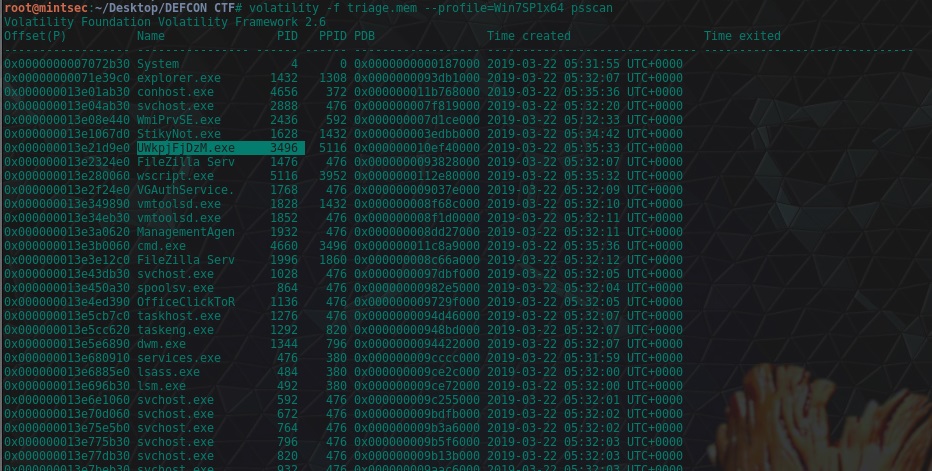
flag<UWkpjFjDzM.exe>
05. tcpip settings - 18 Points
“What was the IP address of the machine at the time the RAM dump was created?”
Using the netscan module of Volatility, we can see references to a local IP which isn’t 127.0.0.1, and given this has come from the owner “SYSTEM” it is a good indication this is was the IP at the time of the RAM dump.
volatility -f triage.mem --profile=Win7SP1x64 netscan
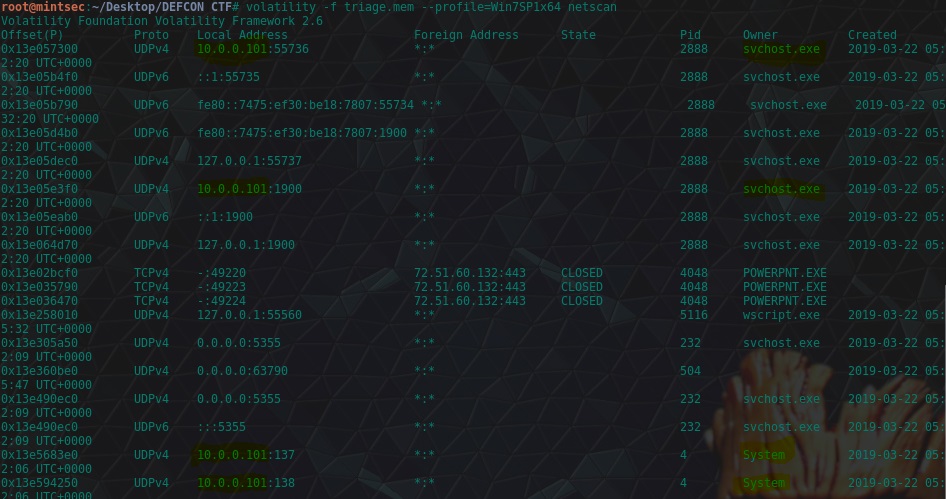
flag<10.0.0.101>
06. intel - 18 Points
“Based on the answer regarding to the infected PID, can you determine what the IP of the attacker was?”
Scroll down, once again just keep scrolling scrolling and we have our answer.
volatility -f triage.mem --profile=Win7SP1x64 netscan
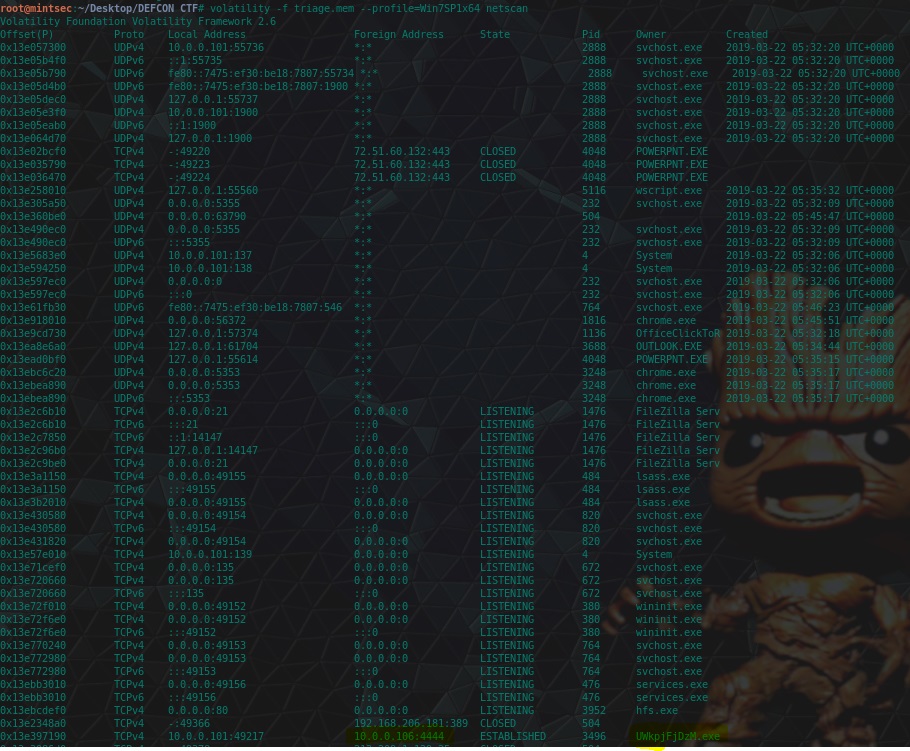
flag<10.0.0.106>
07. i <3 windows dependencies - 20 Points
“What process name is VCRUNTIME140.dll associated with?”
This question we can use the dllist plugin of Volatility and some grep kungfu to find out the process.
volatility -f triage.mem --profile=Win7SP1x64 dlllist | grep "VCRUNTIME140.dll" -B 40
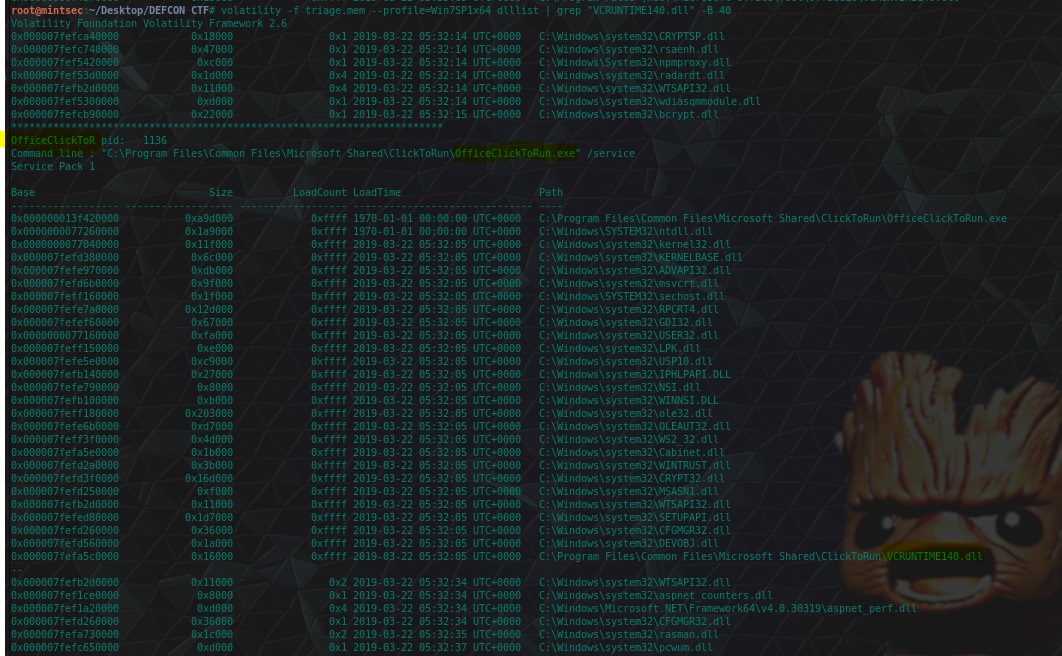
flag<OfficeClickToR>
08. mal-ware-are-you - 20 Points
“What is the md5 hash value the potential malware on the system?”
One useful plugin of Volatility is the procdump plugin which allows us to obtain process dumps (executables as they exist in memory) and examine them. In this case we know the ‘infected PID’ which would be ‘potential malware’ so we can dump this from memory and check its md5 hash.
volatility -f triage.mem --profile=Win7SP1x64 procdump -p 3496 --dump-dir=./
md5sum executable.3496.exe
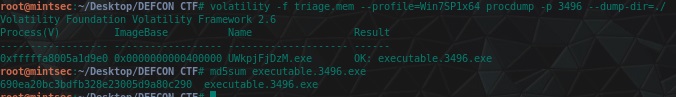
flag<690ea20bc3bdfb328e23005d9a80c290>
09. lm-get bobs hash - 24 Points
“What is the LM hash of bobs account?”
Now we’re putting the red hat back on. Using Volatility if we have a full memory dump we can actually extract password hashes using the hivelist and hashdump modules. This requires us to first locate the virtual address space of the SYSTEM Hive, and SAM, and then dump the user hashes.
volatility -f triage.mem --profile=Win7SP1x64 hivelist
volatility -f triage.mem --profile=Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a000e66010 `> hash.txt
cat hash.txt
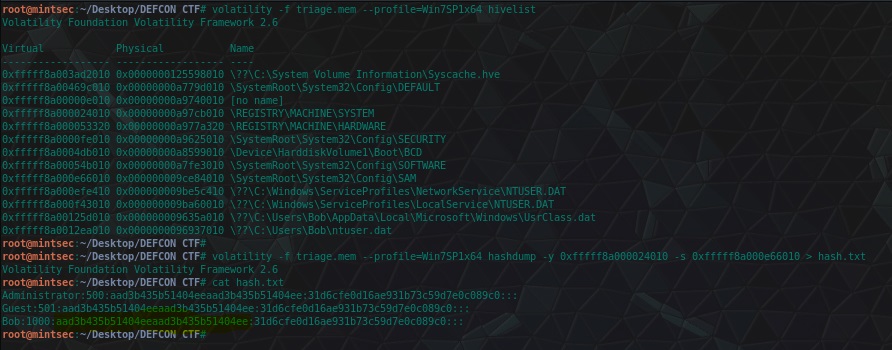
In this case the LM hash is the Prefix to the entire hash, with the rest being the NTLM hash. Those with a keen eye will notice that the LM hash is in fact the LM hash assigned when there is ‘No Password’ which in this case means that LM hashes weren’t enabled on this box (which isn’t a bad thing).
flag<aad3b435b51404eeaad3b435b51404ee>
10. vad the impaler - 25 Points
“What protections does the VAD node at 0xfffffa800577ba10 have?”
Using the vadinfo plugin and a little bit of grep-foo we’re able to find these protections.
volatility -f triage.mem --profile=Win7SP1x64 vadinfo | grep "0xfffffa800577ba10" -A 3
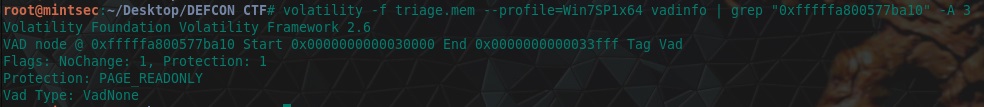
flag<PAGE_READONLY>
11. more vads?! - 25 Points
“What protections did the VAD starting at 0x00000000033c0000 and ending at 0x00000000033dffff have?”
Same deal with this question, we just need to modify our grep-foo a little bit given we know the output format.
volatility -f triage.mem --profile=Win7SP1x64 vadinfo | grep "Start 0x00000000033c0000 End 0x00000000033dffff" -A 3
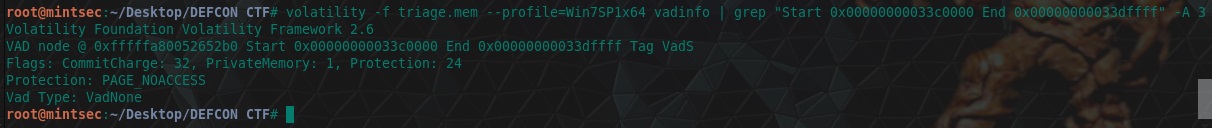
flag<PAGE_NOACCESS>
12. vacation bible school - 25 Points
“There was a VBS script run on the machine. What is the name of the script? (submit without file extension)”
One way of finding this is taking a memory dump of a process using the memdump module of Volatility, and then using strings and some grep foo to find the file in question. Using the below we find our answer.
volatility -f triage.mem --profile=Win7SP1x64 memdump -p 5116 --dump-dir=./
strings 5116.dmp | grep .vbs
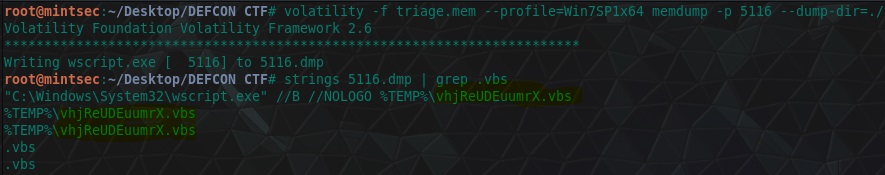
flag<vhjReUDEuumrX>
13. thx microsoft - 25 Points
“An application was run at 2019-03-07 23:06:58 UTC, what is the name of the program? (Include extension)”
More plugins, more grep-foo, except this time we can use the shimcache module to gather information about what applications were run and when.
volatility -f triage.mem --profile=Win7SP1x64 shimcache | grep "2019-03-07"
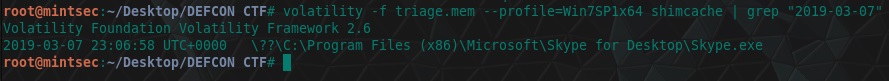
flag<Skype.exe>
14. lightbulb moment - 35 Points
“What was written in notepad.exe in the time of the memory dump?”
Hold on, let’s now stop for a moment and let that ‘lightbulb moment hit us’… you got it? For those who are still not sure, remember the picture we found on Karen’s machine during the deadbox challenges? This had the flag typed into an open notepad document. For those who haven’t done this challenge, we can still locate this using…You guessed it a little grep-foo! First we’ll need to dump the memory of the notepad process.
volatility -f triage.mem --profile=Win7SP1x64 memdump -p 3032 --dump-dir=./
Next, we need to understand that notepad stores text as a 16-bit little-endian format, so we’ll need to use the ‘-e l’ switch with strings. Tie this in with a grep searching for the flag and we have our answer.
strings -e l 3032.dmp | grep "flag"
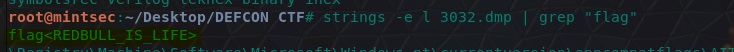
flag<REDBULL_IS_LIFE>
15. 8675309 - 35 Points
“What is the shortname of the file at file record 59045?”
Why stop now right, using yet another Volatility module known as the MFT (Master File Table) Parser we can use some grep-foo to once again find what we’re looking for.
volatility -f triage.mem --profile=Win7SP1x64 mftparser | grep "59045" -A 20
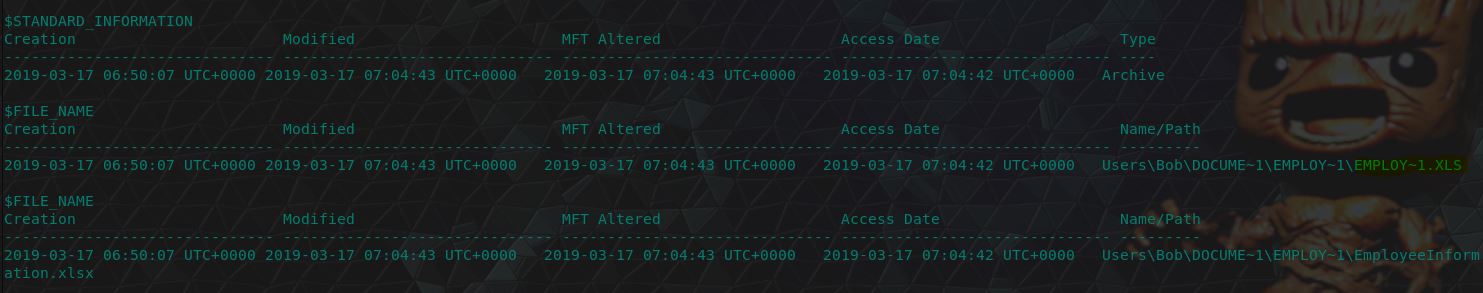
flag<EMPLOY~1.XLS>
16. whats-a-metasploit? - 50 Points
“This box was exploited and is running meterpreter. What PID was infected?”
This question could have been a trick question given a Meterpreter shell could have been migrated into another process; however, based on question 4 we already know the process ID of the malicious executable which is likely to be Meterpreter. Using this assumption we can dump the executable and submit it to VirusTotal to confirm our hypothesis.
volatility -f triage.mem --profile=Win7SP1x64 procdump -p 3496 --dump-dir=./
and as we can see from the VirusTotal Report, this is most definitely a malicious Meterpreter Trojan.
flag<3496>
Category: Triage VM Questions
01. Who’s That User? - 1 Point
“What is the name of the user?”
Firing up the VM we have a lot going on, and want to make sure we have minimal impact on the box during triage in case it impacts later questions. This first question can be solved by opening the start menu.
flag<bob>
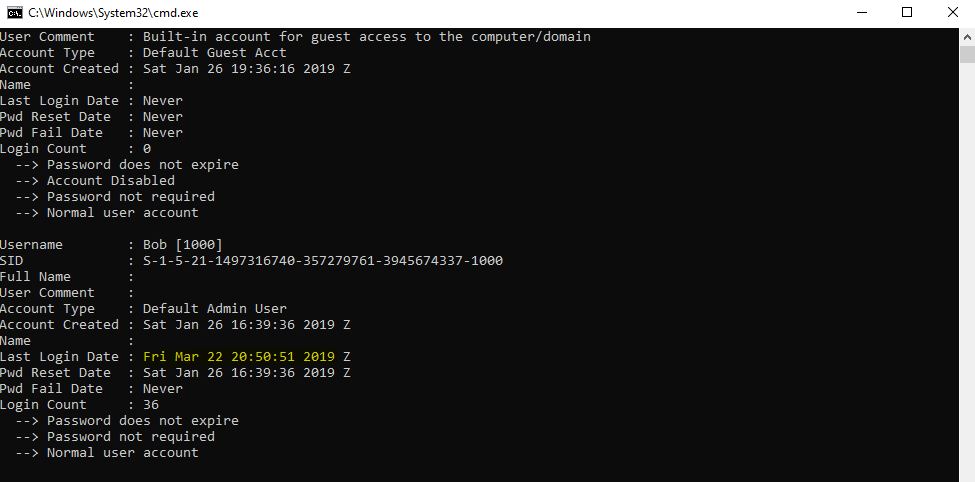
02. Thee who logged in last - 5 Points
“Which time was the most recent logon? Submit in UTC as MM:DD:YYYY HH:MM:YYYY in 24 format.”
Although you’d think that looking this up using logonsessions as part of the supplied sysinternals toolkit would suffice, this will actually give you slightly incorrect information causing the flag to be incorrect.
To get the answer you’ve actually got to take this information directly from the SAM, which you cannot interact with while it’s in use… this could still be done using Erik Zimmerman’s RegExplorer tool; however, there’s some errors either based on dependencies or this machine trolling us. So, no one said we had to fight fairly here, let’s treat this as a deadbox.
Repeating the same process as before we can dump the SAM and use RegRipper to give us the necessary information.
rip.exe -r "SAM" -f sam
flag<03/22/2019 20:50:51>
03. Down Time? More like Frown Time - 5 Points
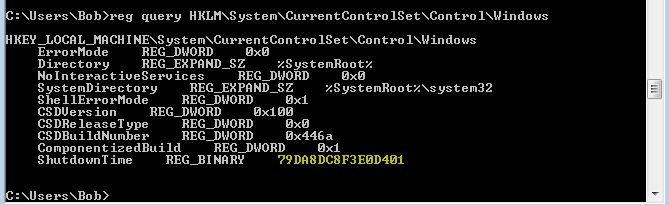
“When was the machine last turned off? Submit in UTC as MM:DD:YYYY HH:MM:YYYY in 24 format”
This information would need to be gathered from the registry to be accurate, so we can query this by opening a command prompt and running:
reg query HKLM\System\CurrentControlSet\Control\Windows
As you can see this is stored in a format which is illegible; however a quick google-foo reveals a nice solution to this problem on Stack Overflow
#! /usr/bin/python3
from __future__ import division
import struct
import sys
from binascii import unhexlify
from datetime import datetime, timedelta
nt_timestamp = struct.unpack("<Q", unhexlify(sys.argv[1]))[0]
epoch = datetime(1601, 1, 1, 0, 0, 0)
nt_datetime = epoch + timedelta(microseconds=nt_timestamp / 10)
print(nt_datetime.strftime("%c"))
Back in our Kali instance we can use this same python script to get our answer.
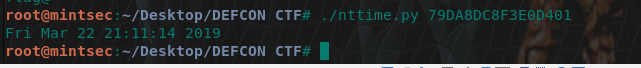
./nttime.py 79DA8DC8F3E0D401
flag<03/22/2019 21:11:14>
04. No one’s ever really gone… Palpatine Laugh - 5 Points
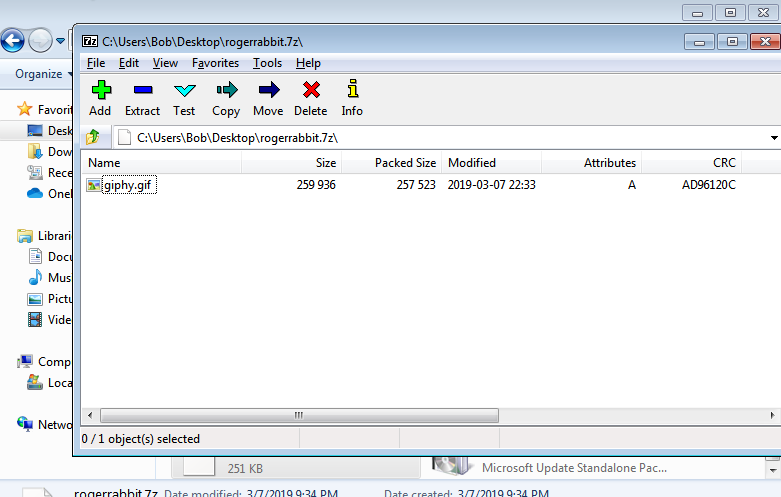
“A 7z archive was deleted, what is the CRC32 hash of the file inside?”
This is as easy as restoring the deleted file from the recycle bin, installing 7-Zip which has been downloaded, and checking the CRC32 value, with this you have your answer.
flag<AD96120C>
05. Now, is no time at all - 7 Points
“What is the current timezone on the machine? (Submit in UTC format)”
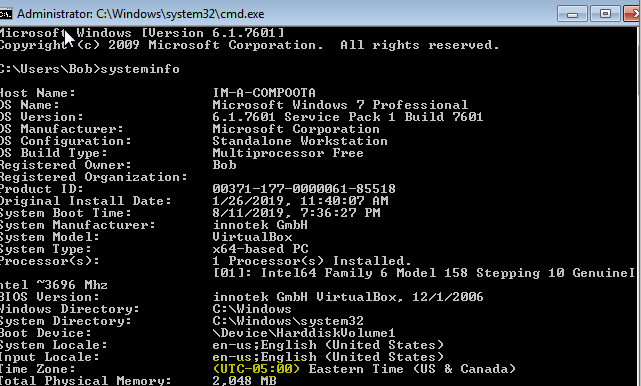
There’s a lot of information we can gather through the command line. Using the ‘systeminfo’ command we can find our answer.
systeminfo
flag<UTC-5>
06. IT’S OVER 1000 - 7 Points
“How many users have an RID of 1000 or above on the machine?”
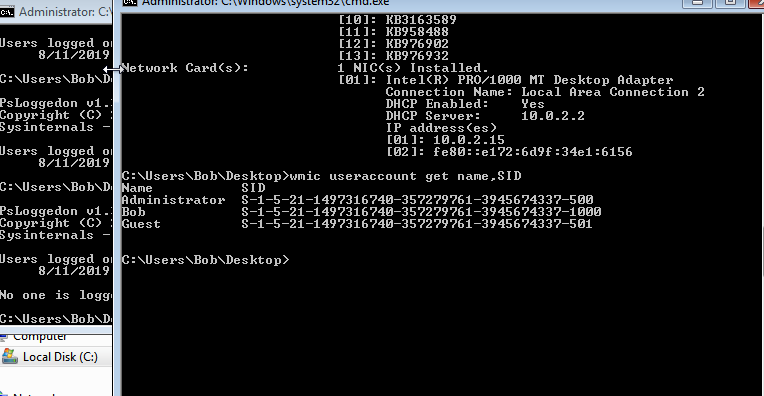
Using WMI we can get this information quite easily.
wmic useraccount get name,SID
flag<1>
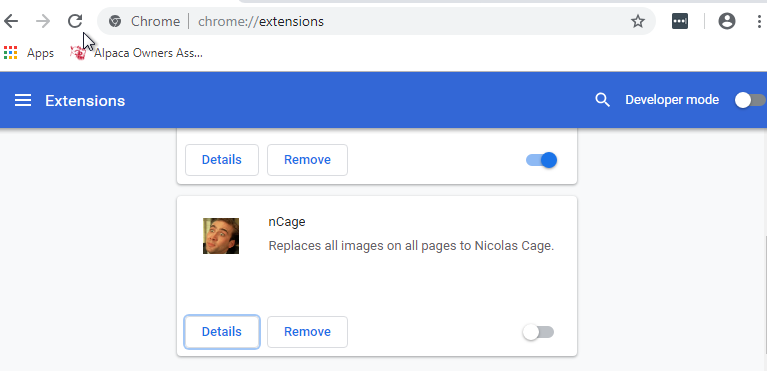
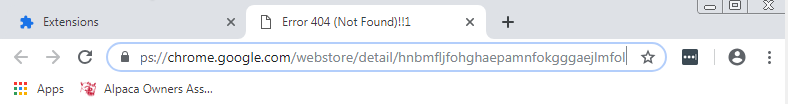
07. Go Go Gadget Google Extension - 7 Points
“What is the ID of the chrome extension installed?”
There’s a few ways we can go about viewing this, but one of the easiest is to just run chrome and viee the extension.
Then from here checking the ‘details’ takes us to a URL which has the extension ID.
flag<hnbmfljfohghaepamnfokgggaejlmfol>
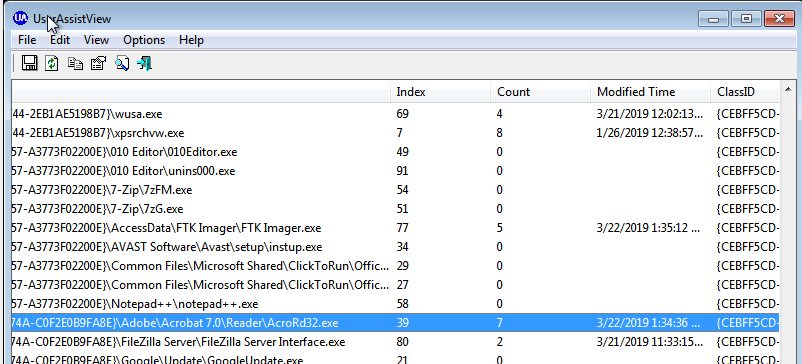
08. Run, Adobe, Run! - 7 Points
“How many times was adobe reader run?”
Luckily we haven’t opened up any Adobe Reader sessions….right? So by now you we realise that there’s some troll scripts running on this machine which may hinder our future analysis, so we may just need to keep that in mind as we have swapped our left and right clicks.
Downloading the nirsoft toolset we can use UserAssistView to find out this information.
flag<7>
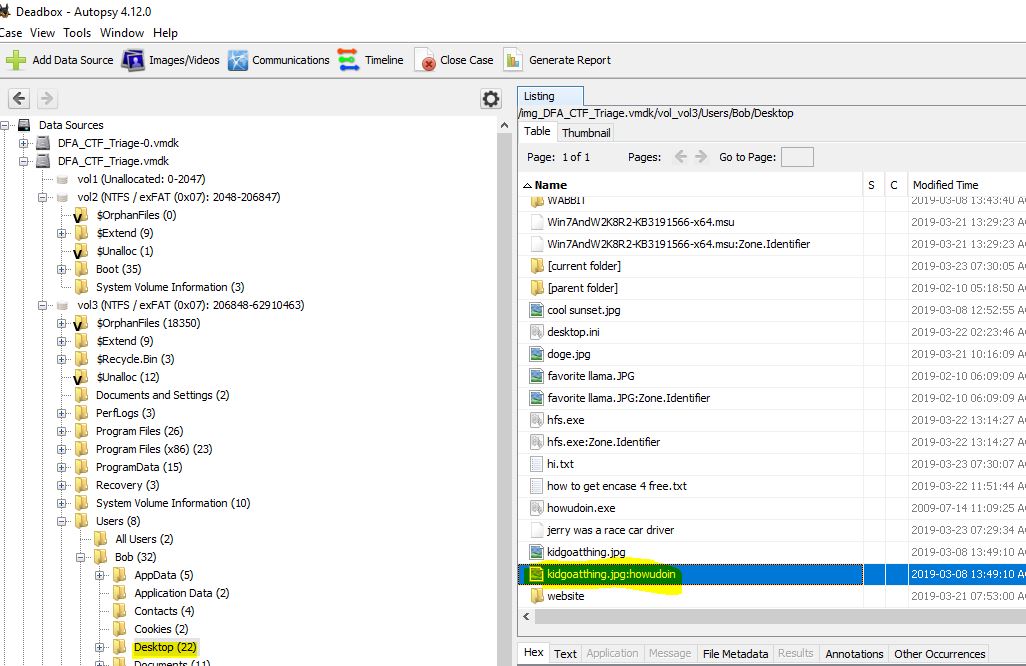
09. Should I use my invisibility to fight crime or for evil? - 10 Points
“A hidden executable is on the desktop. What is the name of the file (extension included)?”
This can be easily located by running a directory command on the Desktop.
dir /a
flag<howudoin.exe>
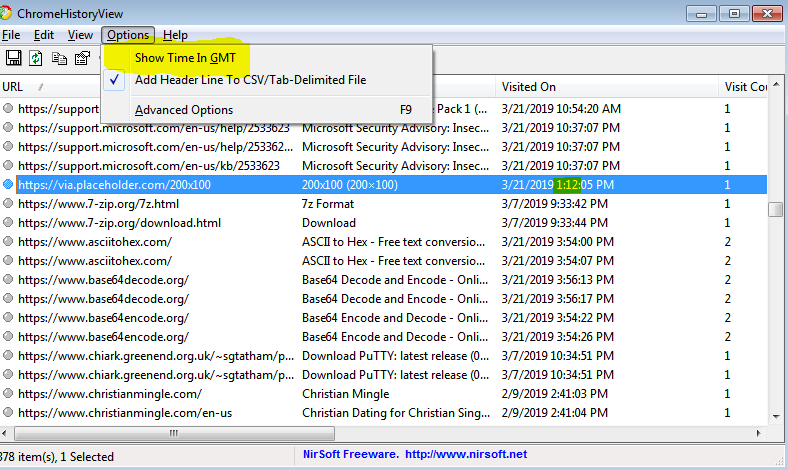
10. It’s all in the timing - 10 Points
“What time did the user access content on placeholder.com? Submit answer in HH:MM format.”
Using ChromeHistoryView we can find this information; however, we also need to remember to turn off the setting ‘Show Time in GMT’ as this isn’t specified in this question, and the answer needs to be submitted without taking into consideration 24hr time.
flag<01:12>
11. The Hostess with the Mostest - 10 Points
“What is the hostname of the Triage machine?”
We have already gathered this information through the systeminfo command; however, we can also get this information by using ‘hostname’.
hostname
flag<im-a-compoota>
12. These messages aren’t gonna message themselves! - 10 Points
“What messaging application was downloaded onto this machine?”
We can see this within downloads, whether we view this in Autopsy or the VM itself is entirely preferential.
flag<skype>
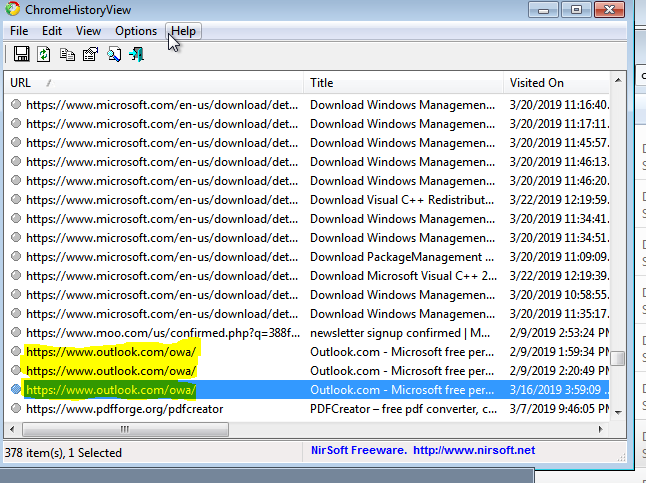
13. Dang it Bobby - 15 Points
“How many times did Bob visit Outlook.com?”
Once again, Bob only seems to have used Chrome. By using ChromeHistoryView we can see there were only 3 visits.
flag<3>
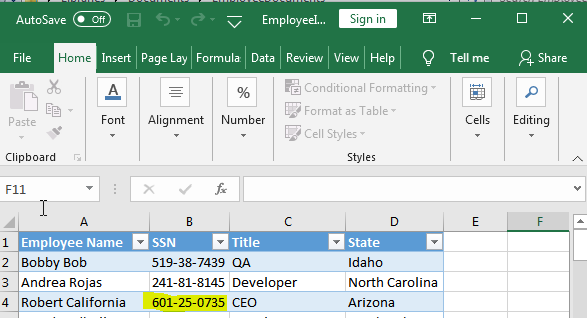
14. Damnit Bobby! - 15 Points
“It appears that Bob may have been playing the role of HR. Can you find the Social Security Number for someone with the initials R.C.?”
Looking within My Documents we find a folder called EmployeeDocuments which contains a file called EmployeeInformation. Opening this up using excel gives us our answer.
flag<601-25-0735>
15. Get back to work Sponge Bob me boy - 18 Points
“Bob was watching youtube videos at work. The network capture showed the video ID to be N9NCyGaxoDY. What is the name of the video?”
This doesn’t even require the VM and we can find it by the below:
- Check video ID on YouTube…
- https://www.youtube.com/watch?v=N9NCyGaxoDY
flag<Rowan Atkinson Toby the Devil - Welcome to Hell>
16. Laughs in Hidden - 25 Points
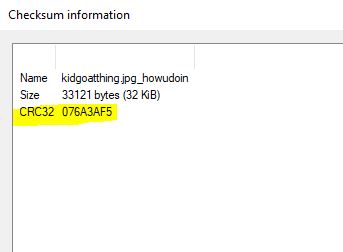
“Bob has a hidden powerpoint presentation. What is the file’s CRC32 hash?”
Well, as much as we’d surely love to run dir /A to find this file hidden in an alternate data stream on the desktop and then tinker with extracting it and finding the CRC32 hash while Powershell continues to troll us, we can get this information directly by dumping the Alternate Data Stream from Autopsy.
and then checking it’s CRC32 hash using 7-Zip.
flag<076A3AF5>
17. Desktop Flag 1: Just the start of the fun - 25 Points
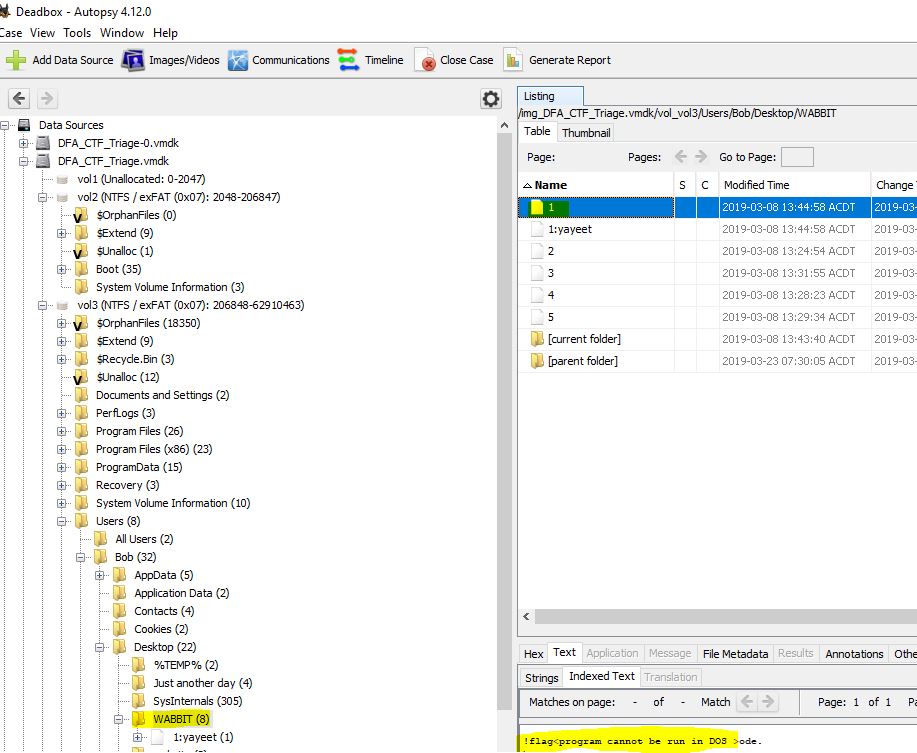
“What is the flag in C:\Users\Bob\Desktop\WABBIT\1?”
Checking this in Notepad++ reveals our answer without having to identify or repair the executable. Alternatively, Autopsy gives us the same goods.
flag<program cannot be run in DOS>
18. Desktop Flag 2: Electric Boogaloo - 25 Points
“What is the flag in C:\Users\Bob\Desktop\WABBIT\2?”
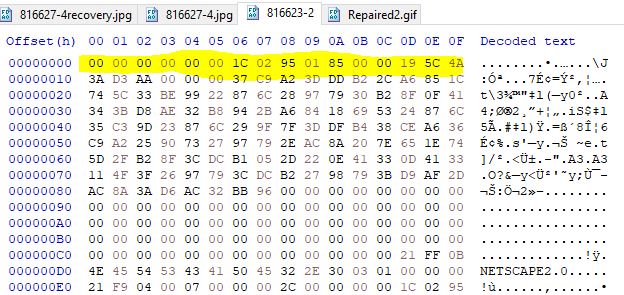
Looking at the file we can quickly identify that this file is a Netscape Looping Application Extension.
This was used back when Netscape was a widely used browser to determine how many loops a Gif would perform. If we look at the file closely we can see it is missing the magic bytes necessary to be identified as a gif. By modifying this we can get a valid gif file.
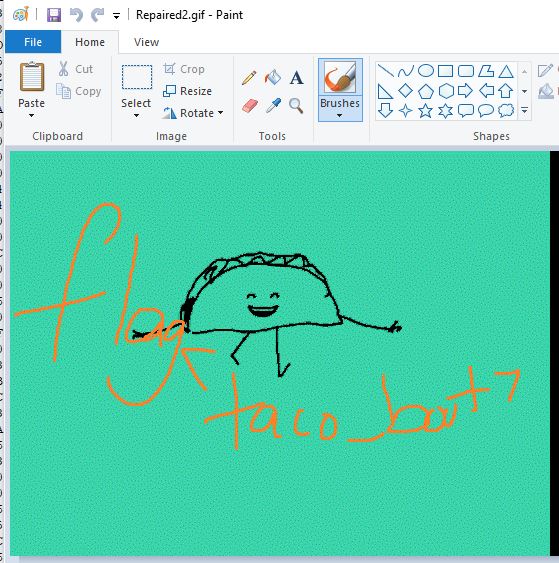
Editing this with paint reveals our flag.
flag<taco_bout>
19. Desktop Flag 3: Need for Speed - 25 Points
“What is the flag in C:\Users\Bob\Desktop\WABBIT\3?”
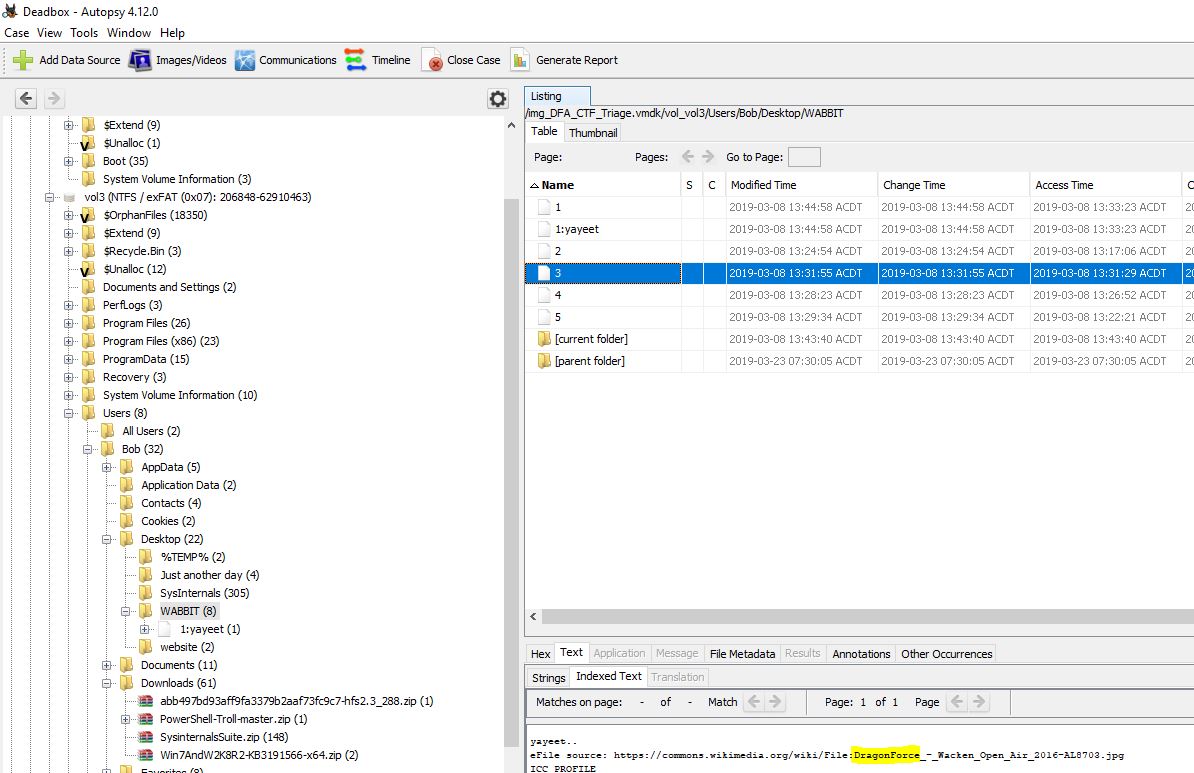
Without going too deep we can already find reference to DragonForce in the form of an ‘eFile source’ through Autopsy and its extracted strings. This happens to be the correct flag.
flag<dragonforce>
20. Desktop Flag 4: Want some more? - 25 Points
“What is the flag in C:\Users\Bob\Desktop\WABBIT\4?”
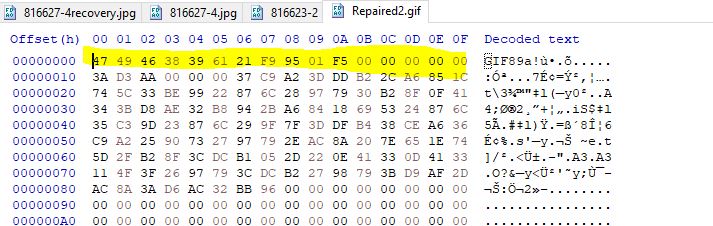
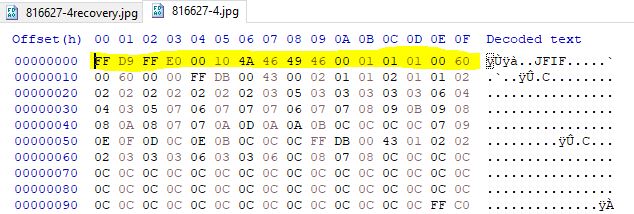
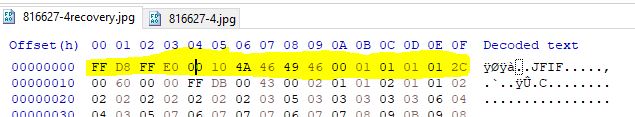
Viewing this in HxD we can see that the first 16 bytes indicate it is a JPEG file through the fingerprint ‘JFIF’.
Comparing this to a valid JPEG we can see that some of the first 16 bytes are malformed, by replacing these with valid values the picture is repaired and we get our flag.
Professor Lupin would be pleased!

flag<wof_on_champ>
21. Now watch me youuuuuuuu - 25 Points
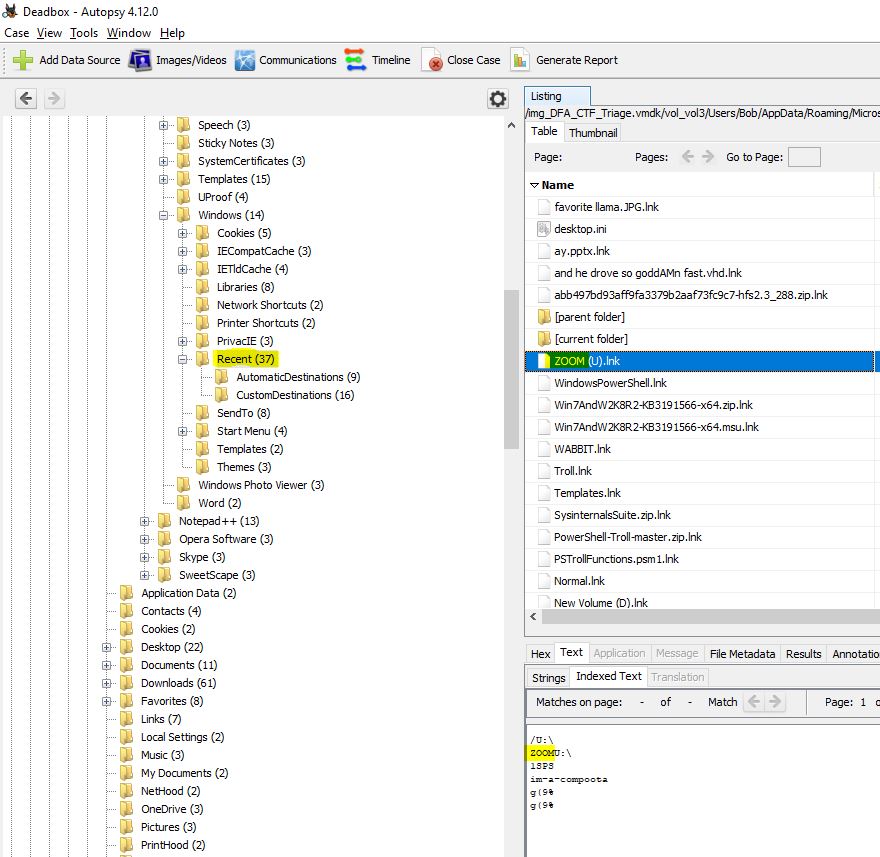
“A device with the drive letter “U” was connected. What was the label of the volume?”
Without going into registry forensics, we can still see the name of this drive through the RecentDocs section. This is easily seen with Autopsy.
flag<ZOOM>
22. Desktop Flag 5: No, you can’t have more time - 30 Points
“What is the flag in C:\Users\Bob\Desktop\WABBIT\5?”
There’s a few ways you can go about this, but the easiest is to identify based on the first few bytes that this looks like a PDF.
We can actually open this as a PDF, and by selecting all the hidden text we can find our flag.
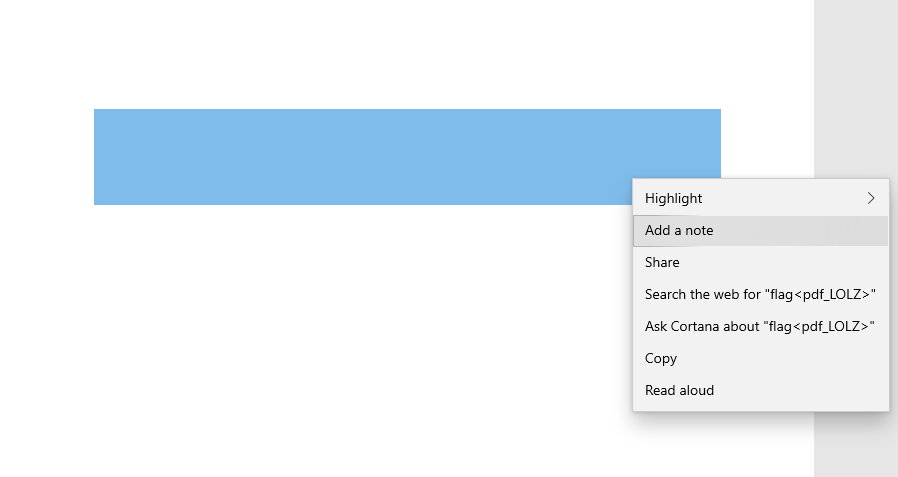
flag<pdf_LOLZ>
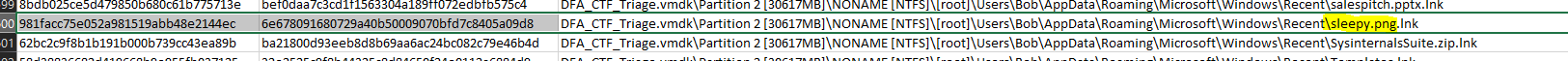
23. I will look for you, I will find you… and I will hash you - 30 Points
“A file with MD5 981FACC75E052A981519ABB48E2144EC is on the box… somewhere. What is the name of the file? (with ext)”
Once again, we could go through the trouble of trying a recursive loop to locate and hash every single file on this box, but an easier way is to once again just open it up in FTK Imager, get all the file hashes, export to csv and locate the hash.
flag<sleepy.png>
24. Easy Peasy Lemon Squeezy - 40 Points
“So DFA leadership got tired…what’s the flag ON the desktop?”
Locating the picture which was mentioned in the previous flag (sleepy.png), we can view this and find a message on a sticky note which becomes our flag.
flag<holla>
25. Can you like… not? - 50 Points
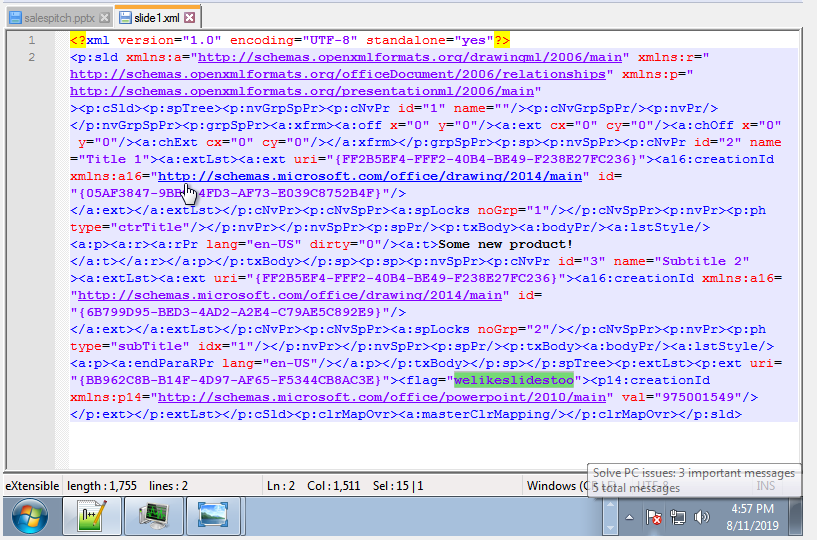
“It looks like Bob was going a little crazy with hiding files within different files. Can you find a flag within a powerpoint about sales pitches? Copy flag exactly how its found (i.e. not in normal flag format).”
Locating the Powerpoint file in my Documents we can check the elements which make it up by extracting them. Inside the Slide1.xml file (ppt/slides/slide1.xml) we find the hidden flag.
<flag="welikeslidestoo">
26. KA-CHOW - 100 Points
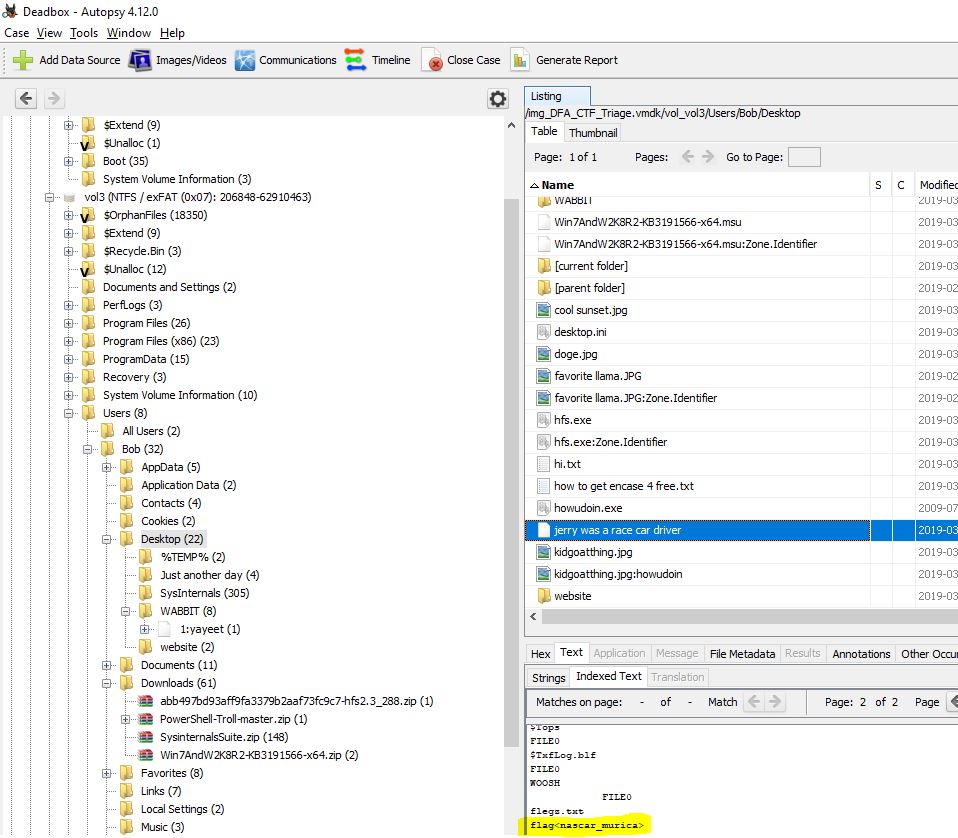
“jerry was a racecar driver”
The only context we have is the filename on the desktop. A look into this reveals that it is quite large and likely a MBR, or a boot sector based on some strings.
Invalid partition table
Error loading operating system
Missing operating system
Rather than trying to reverse this, we can just look at the indexed text by Autopsy to give us our flag.
flag<nascar_murica>
And that sums up the Unofficial DEFCON DFIR CTF for 2019.
Final Notes and bonuses
I wholeheartedly thank David Cowen (HECFBlog) for the Unofficial Defcon DFIR CTF, and the Champlain College Digital Forensic Association for putting these challenges together. As a side-bonus, Autopsy also appears to have carved out some emails which weren’t related to this CTF. Although there is nothing sensitive here in the nature of PII protection emails and names have been redacted in the below example.