The Crown Prince, Nezha: A New Tool Favored by China-Nexus Threat Actors
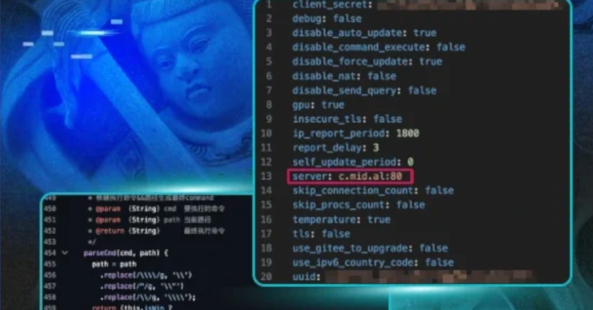
Analysis of an intrusion involving a new tool known as Nezha, which up until publishing this hasn’t been publicly reported on. This was used in tandem with other families of malware and web shell management tools such as Ghost RAT and AntSword by a PRC-Nexus threat actor.