MITRE ATT&CK™ Analysis - T1074.001 Local Data Staging
Data Staged
An adversary will likely stage any data ready for exfiltration into a centralised location. By doing this it allows them to keep files out of view of an unsuspecting victim while ensuring that only relevant information will be ready to ship when they want to finally decide to exfiltrate the information.
Data Staged Analysis
Lab Example
RED TEAM: ATTACK
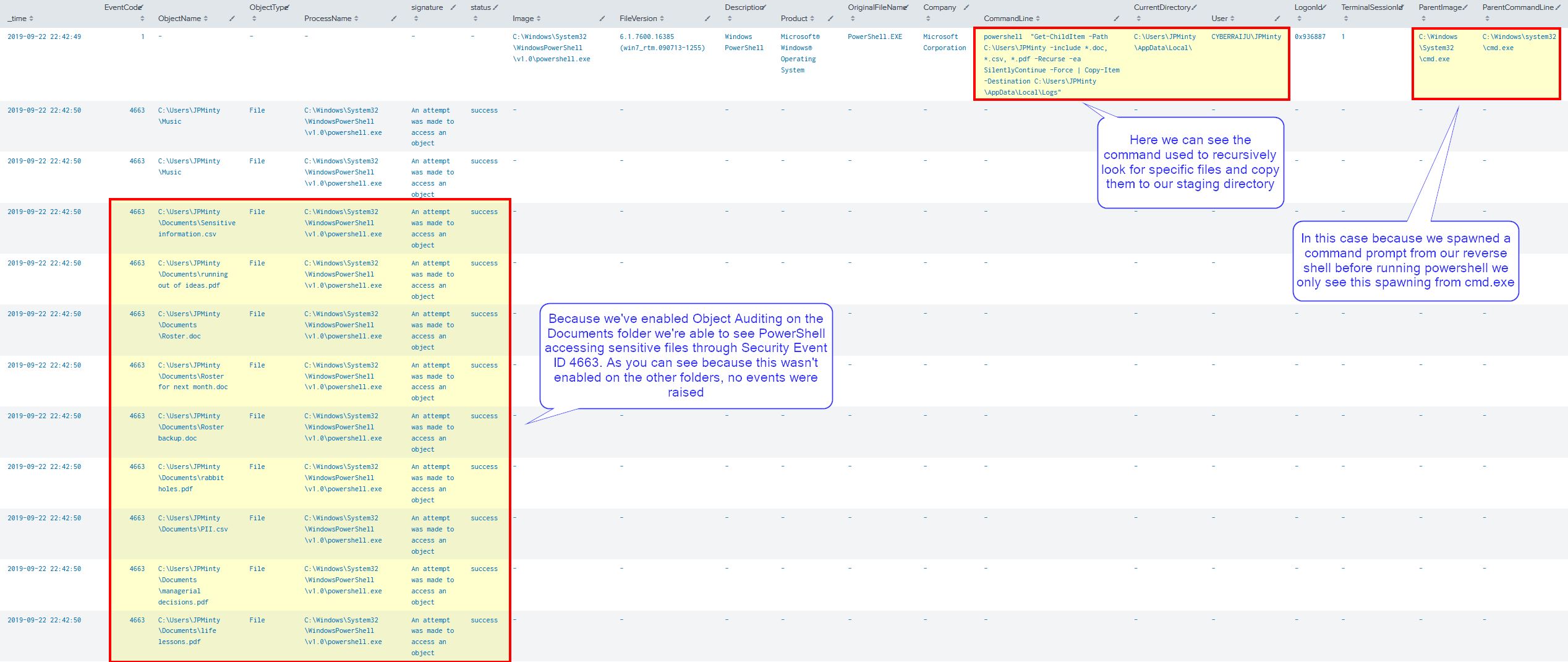
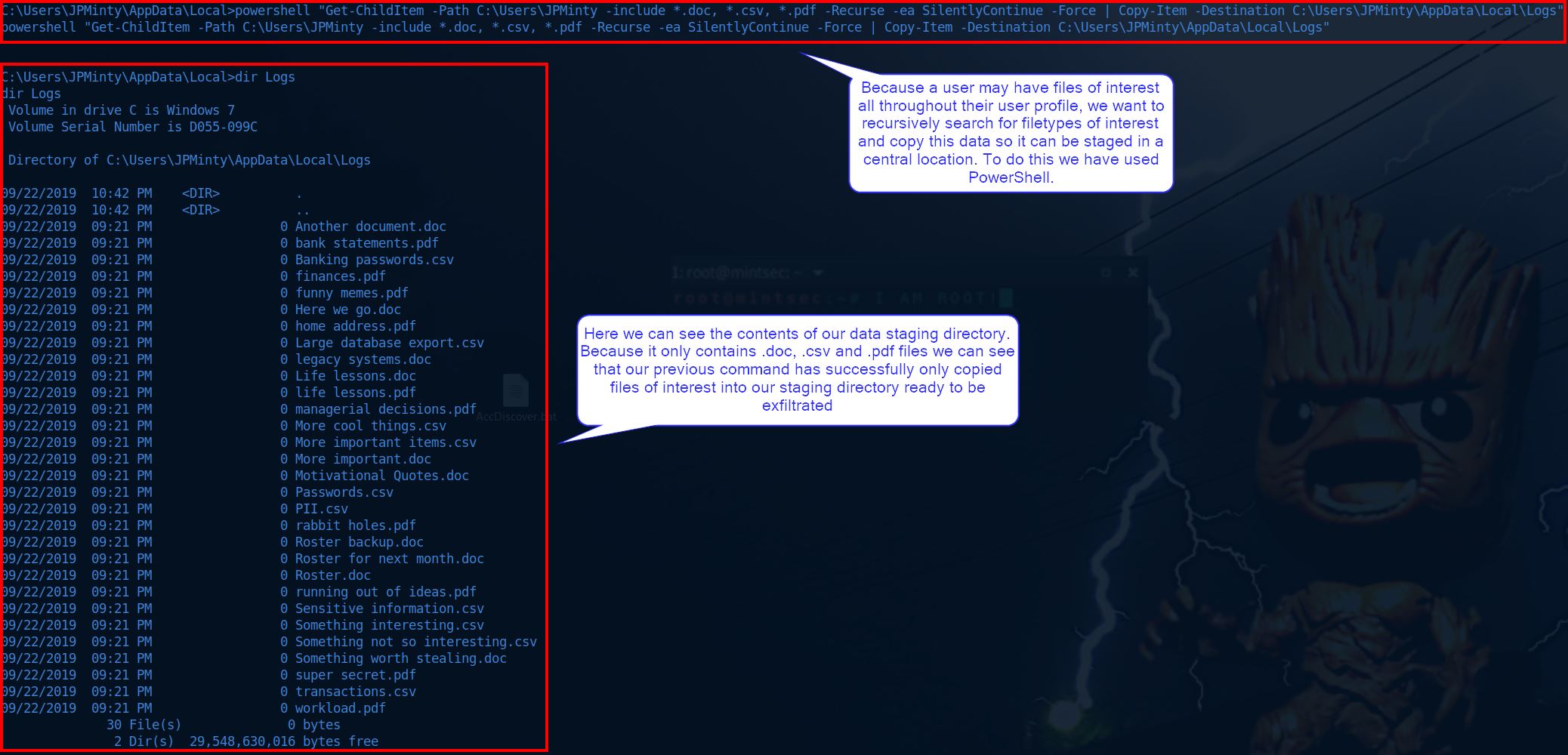
In this example we have used our existing shell to selectively look for filetypes of interest. By using PowerShell we can copy the files of interest to a directory we create ready for exfiltration.
cd %LocalAppData%
mkdir Logs
powershell "Get-ChildItem -Path C:\Users\JPMinty -include *.doc, *.csv, *.pdf -Recurse -ea SilentlyContinue -Force | Copy-Item -Destination C:\Users\JPMinty\AppData\Local\Logs"
BLUE TEAM: DEFEND
From a defenders point of view we knew that files in this users Documents directory were of high value so we enabled object access auditing to see whenever they were accessed.
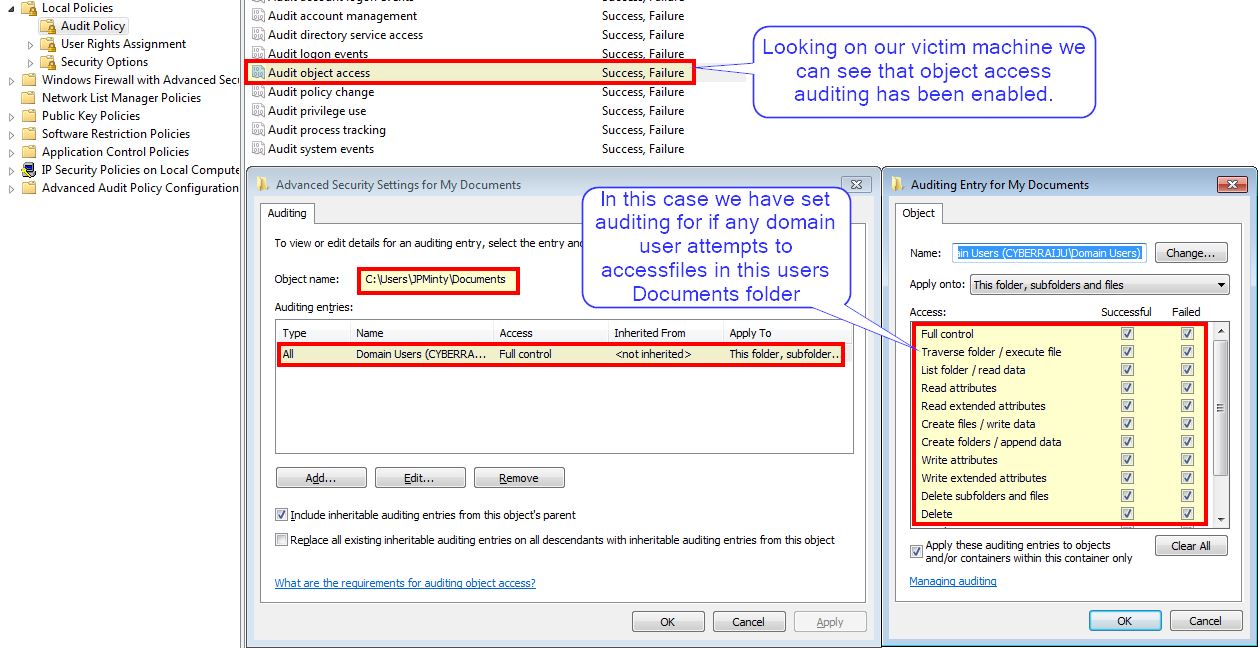
Because of this we can see Security Event ID 4663 has logged access attempts to these files, but not the files which were present in other directories.
In addition we can see the command used to search for these files through our Sysmon logs; however, because the attacker spawned a command prompt prior to executing we weren’t able to see the malicious process which created the reverse shell as it didn’t fall within our search timeframe.