MITRE ATT&CK™ Analysis - T1087 Account Discovery
Account Discovery
Adversaries will often seek to gather information on local or domain accounts. This information is useful for situational awareness and knowing who is a high privileged user in an organisation who may be useful to try and pivot to in order to move laterally or escalate privileges.
Account Discovery Analysis
Lab Example
RED TEAM: ATTACK
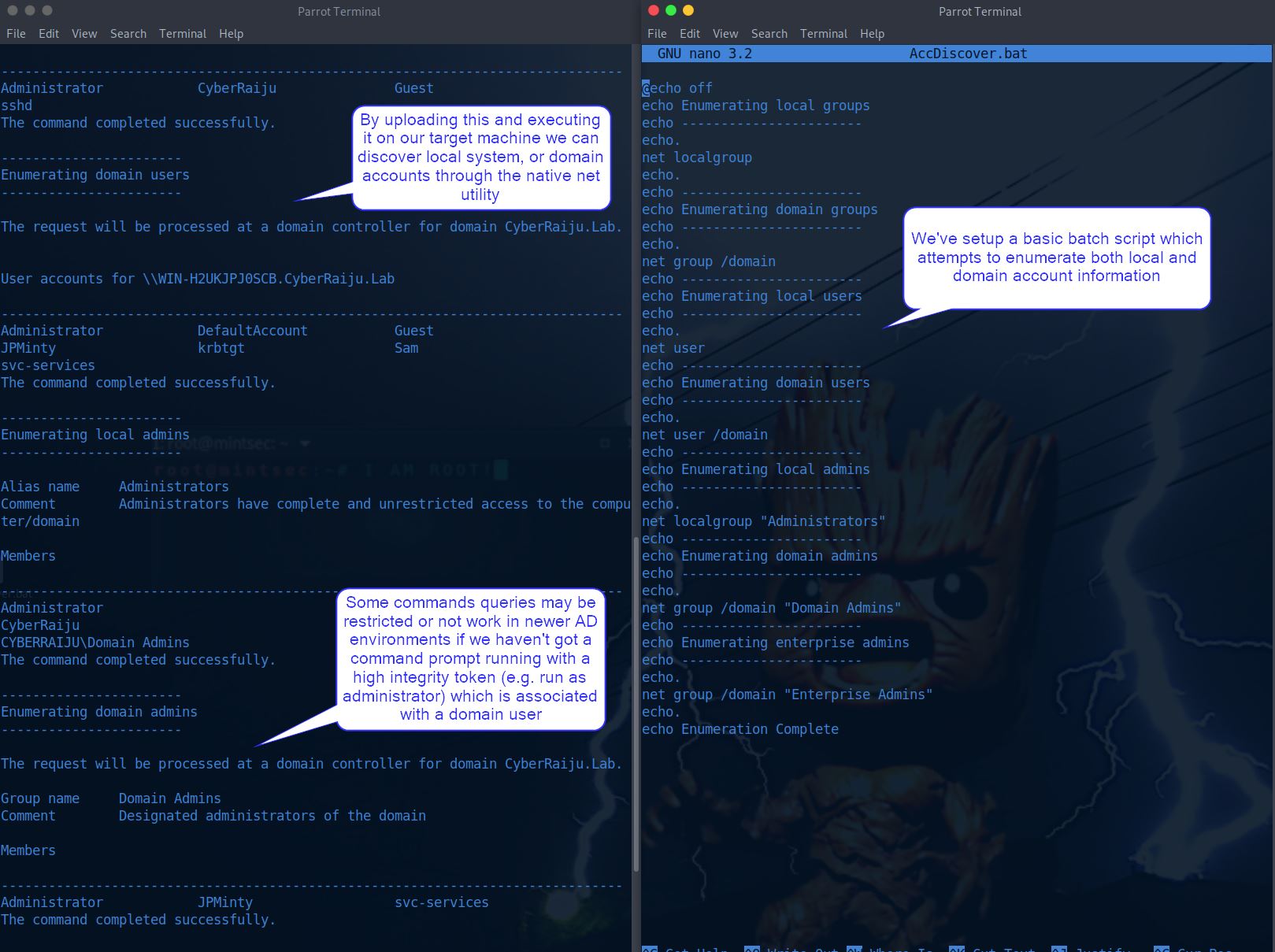
In this example we have an existing shell on a remote system and want to gather user information.
To do this we could run some net commands through our terminal; however, to speed up the process and ensure we don’t mistype (which may be an indication of our presence to the defenders), we upload a batch script to our machine and run it.
BLUE TEAM: DEFEND
From a defenders point of view we’re able to see a number of commands being executed at the same time, this is a giveaway that it was through an automated fashion such as a script.
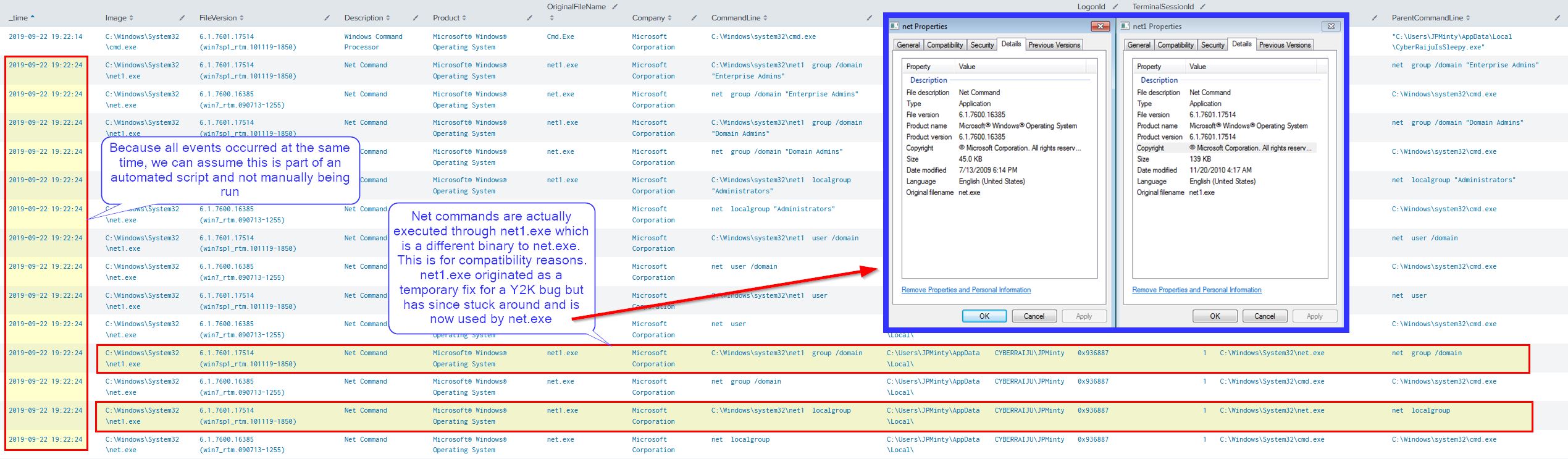
Through our event logs we can see a net1.exe binary which at first glance seems suspicious; however, this is actually a legitimate binary which was created to address issues caused by the year 2000, or for those who are old enough to remember, Y2K.




