MITRE ATT&CK™ Analysis - T1021.006 Windows Remote Management
Windows Remote Management
Windows Remote Management is a service and its own protocol within the Windows Operating System. Originally created for remote management of a system, if the WinRM service is enabled on a machine it becomes a useful way of moving laterally within an environment.
Windows Remote Management Analysis
Lab Example
RED TEAM: ATTACK
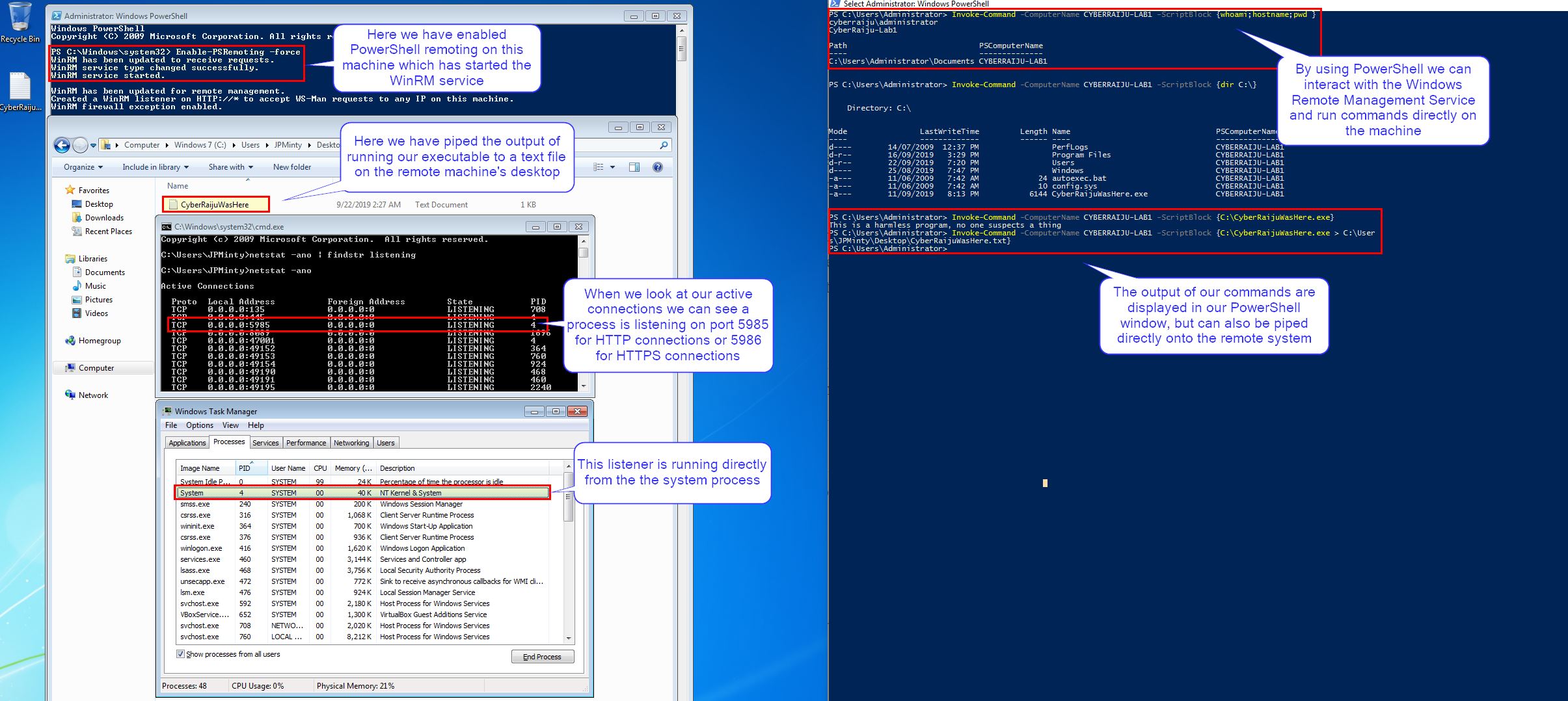
In this example we’ve enabled WinRM by using the below on our victim machine within a PowerShell window.
Enable-PSRemoting -force
At this point the machine begins listening on HTTP://* port 5985 (or 5986 if you’ve specified HTTPS), awaiting commands from an authorized user from a remote machine.
From our attacking machine we have run a few commands including executing a binary on our victim machine.
Invoke-Command -ComputerName CYBERRAIJU-LAB1 -ScriptBlock {whoami;hostname;pwd}
Invoke-Command -ComputerName CYBERRAIJU-LAB1 -ScriptBlock {dir C:\}
Invoke-Command -ComputerName CYBERRAIJU-LAB1 -ScriptBlock {C:\CyberRaijuWasHere.exe}
Invoke-Command -ComputerName CYBERRAIJU-LAB1 -ScriptBlock {C:\CyberRaijuWasHere.exe > C:\Users\JPMinty\Desktop\CyberRaijuWasHere.txt}
BLUE TEAM: DEFEND
From a defenders point of view we’re able to see these events spawning from wsmprovhost.exe (Although if we first established a remote PSSession with the machine and then spawn the process using WMI it would appear differently).
In addition to this System and Security logs help us identify when WinRM was enabled on this host.
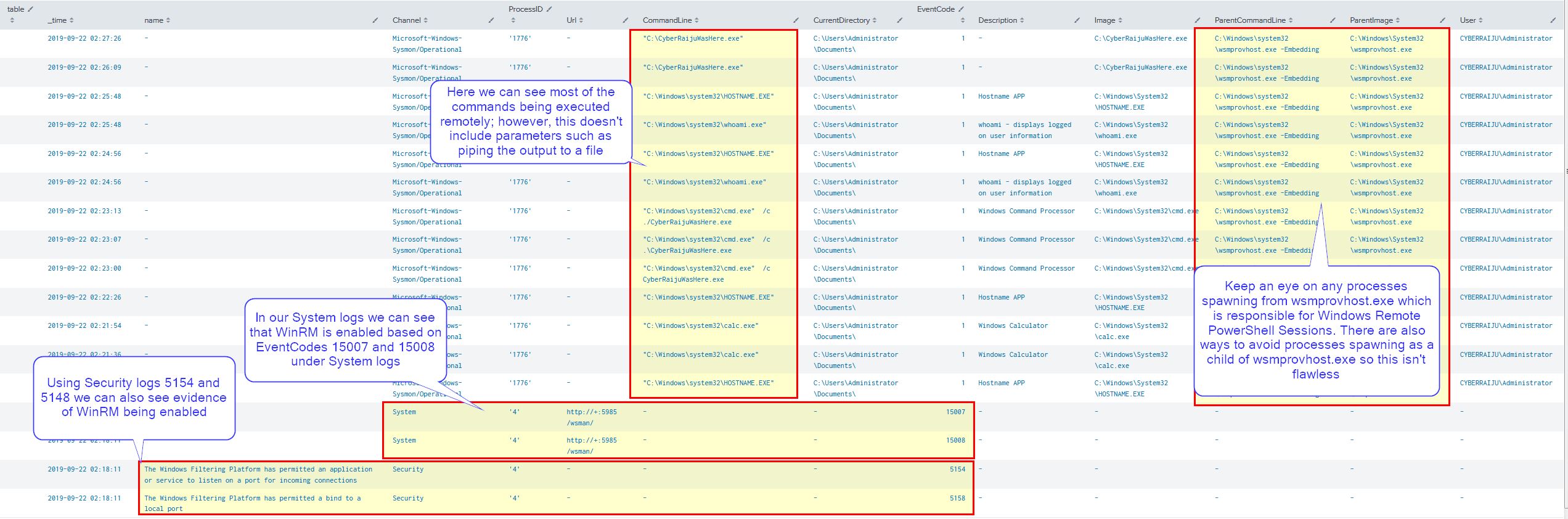
System:
- 15007
- 15008
Security:
- 5154
- 5148




