Practical Malware Analysis - Chapter 1 Lab Write-up
Chapter 1. Basic Static Techniques
This details analysis undertaken and answers to the lab questions in Chapter 1.
Lab 1-1
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
Question 1
Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
Answer 1
Using the Malcode Analyst Pack we are able to perform this by simply right clicking the files and selecting VirusTotal. At the time of writing both matched existing antivirus signatures:
- 35/65 detection rate
- 28/64 detection rate
Question 2
When were these files compiled?
Answer 2
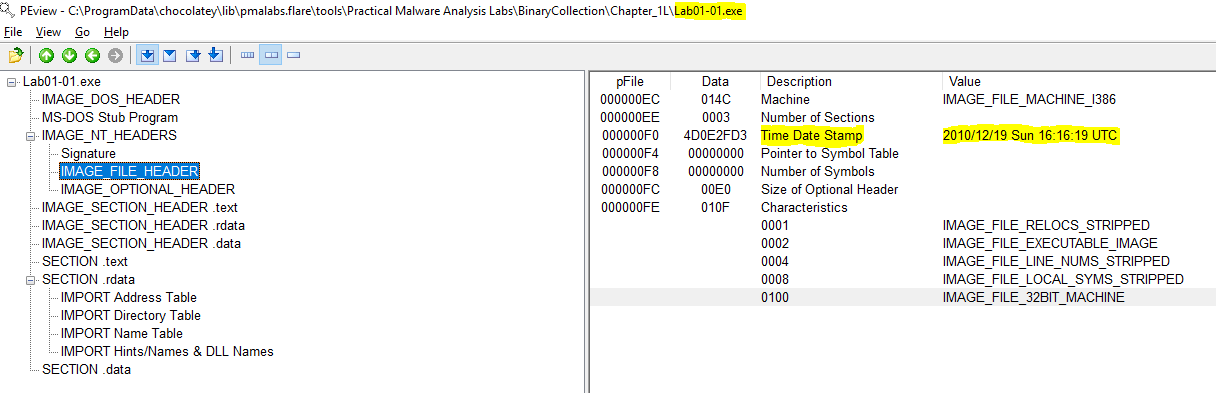
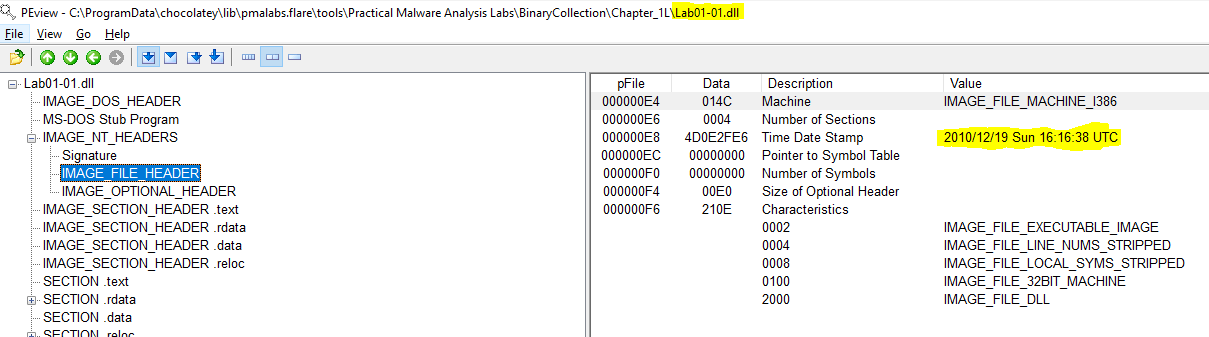
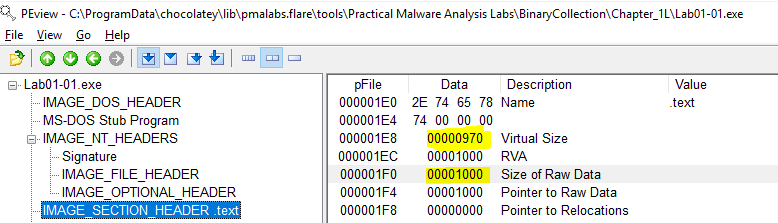
Using PEview we are able to view this information. The information is found under: IMAGE_NT_HEADERS > IMAGE_FILE_HEADER > Time Date Stamp
lab01-01.exe compile time - 2010-12-19 Sunday 16:16:19 UTC
lab01-01.dll compile time - 2010-12-19 Sunday 16:16:38 UTC
Question 3
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
Answer 3
No, there’s no indicators these files are packed or obfuscated due to the following:
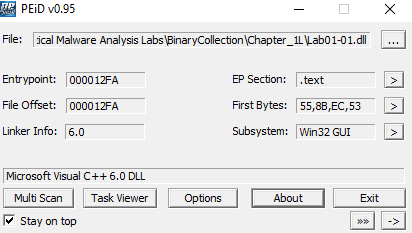
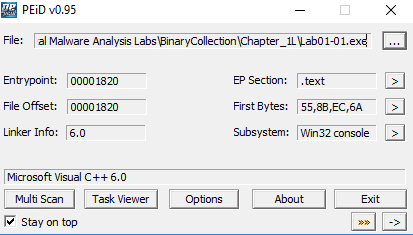
Using PEiD we can identify them as being compiled with Microsoft Visual C++ 6.0.
lab01-01.dll
lab01-01.exe
Using PEview we can see the virtual size is close to the raw size of the files.
lab01-01.exe
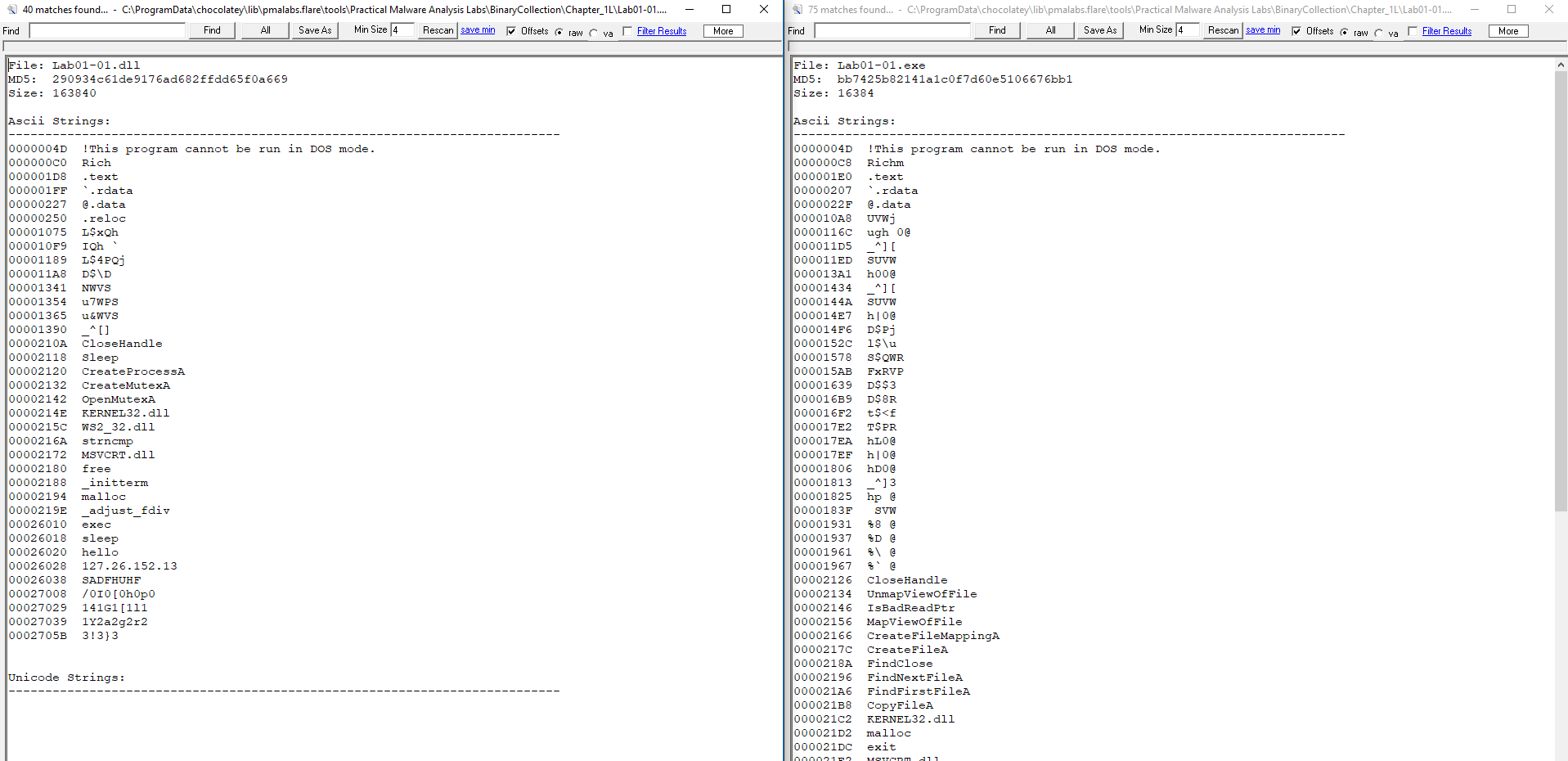
Using the Malcode Analyst Pack we can view “strings” and see there’s plenty of them.
lab01-01.dll and lab01-01.exe
Question 4
Do any imports hint at what this malware does? If so, which imports are they?
Answer 4
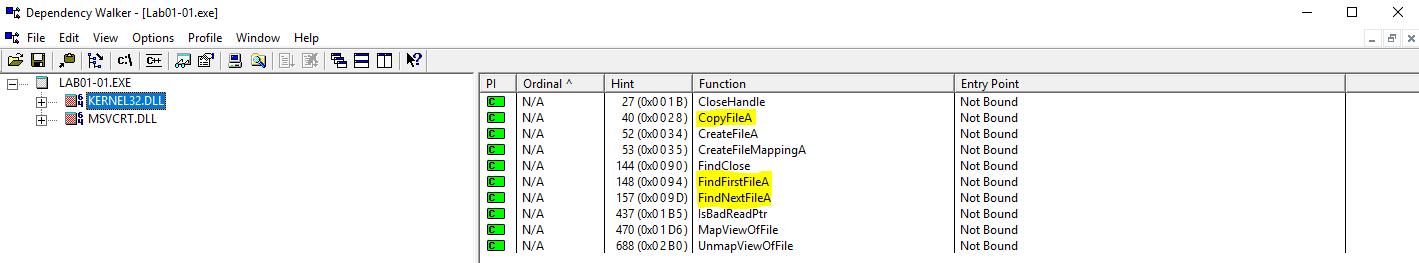
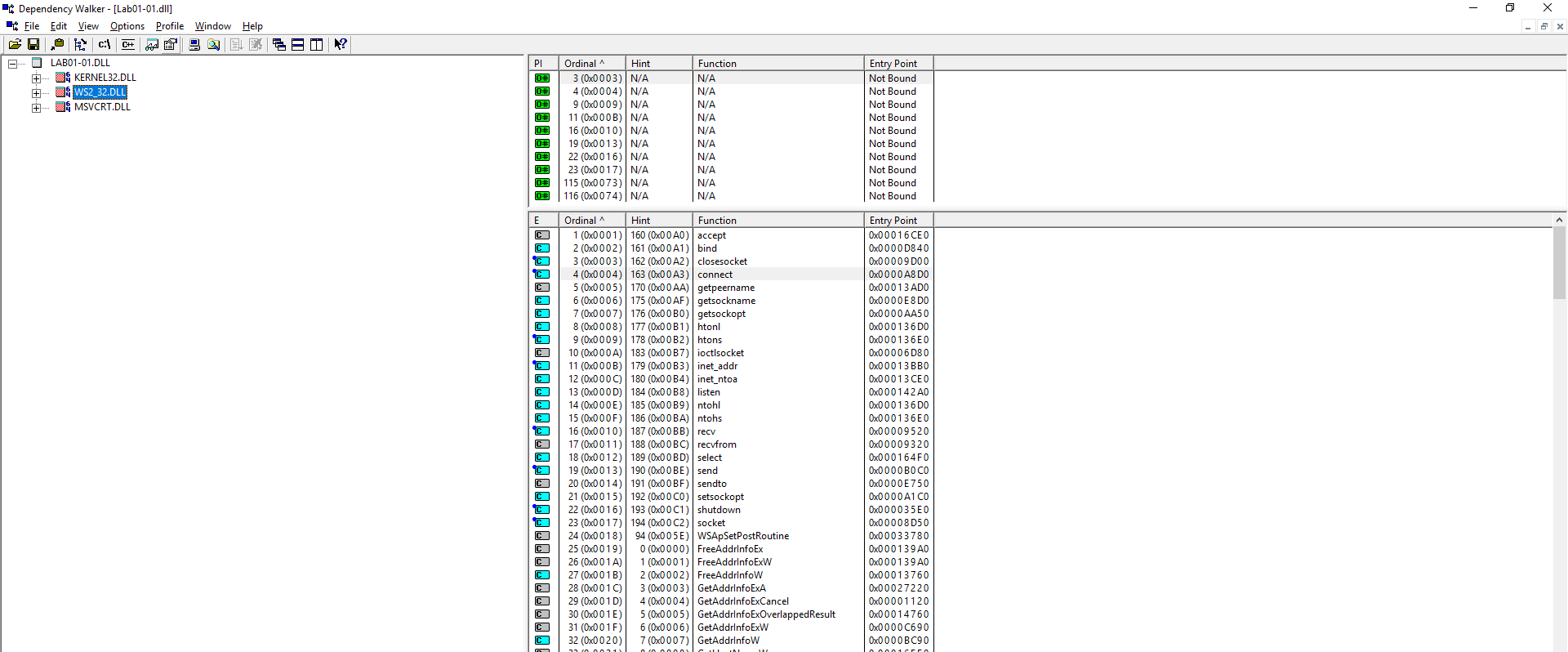
Analysing Lab01-01.exe through Dependency Walker highlighted a number of interesting functions imported from KERNEL32.DLL, these were:
- CopyFile
- FindFirstFile
- FindNextFile
Based on this we can infer that files would likely be searched for on the file system and files would be copied.
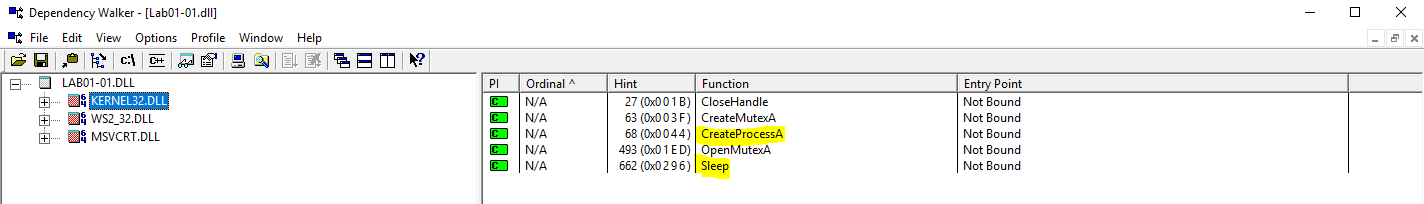
Analysing Lab01-01.dll through Dependency Walker highlighted functions imported from KERNEL32.DLL, these were:
- CreateProcess
- Sleep
Based on this we can infer that the dll would likely spawn a new process and sleep (pause execution) at some stage.
The DLL also had some interesting imports from WS2_32.DLL through the use of the ‘Ordinal Number’.
Matching the Ordinal Number to the associated name, these functions were:
- closesocket
- connect
- htons
- inet_addr
- recv
- send
- shutdown
- socket
- WSAStartup
- WSACleanup
Based on this we can infer that the program has connects to a network or IP of some kind and opens up a socket to send and receive packets.
Question 5
Are there any other files or host-based indicators that you could look for on infected systems?
Answer 5
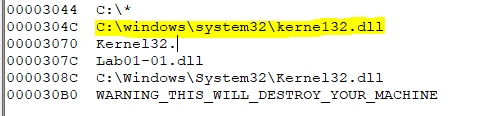
Examining the strings contained within Lab01-01.exe more closely reveals that it is referencing a file called C:\windows\system32\kerne132.dll. This is a very subtle misspelling of the legitimate Kernel32.dll file (notice the use of 1 instead of l) because of this it is likely malicious and we are able to use this to search for infected systems.
Question 6
What network-based indicators could be used to find this malware on infected machines?
Answer 6
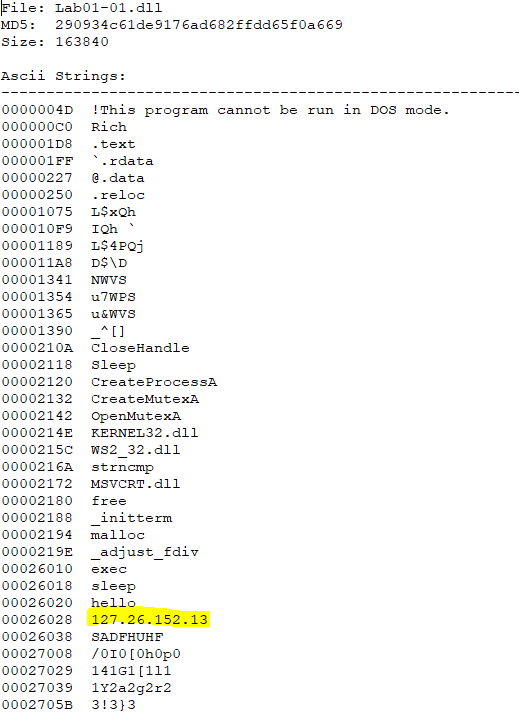
Examining the strings contained within Lab01-01.dll more closely reveals that there is what appears to be an IP address. Because of this and the network imports, it is highly likely that this DLL contacts this IP address, and as such we are able to use this to find infected systems which have contacted 127.26.152.13.
Question 7
What would you guess is the purpose of these files?
Answer 7
Based on everything we’ve enumerated above, we would guess that the executable is used to run the DLL which acts as a backdoor or remote access trojan (RAT). Based on the imports it’s possible the executable searches to see if C:\windows\system32\kerne132.dll exists, and if it doesn’t it may attempt to copy the malicious DLL to C:\windows\system32\kerne132.dll which is used for persistence. Upon executing the DLL, it likely contacts a C2 server at 127.26.152.13.
Lab 1-2
This lab uses the file Lab01-02.exe. Analyze the file Lab01-02.exe.
Question 1
Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer 1
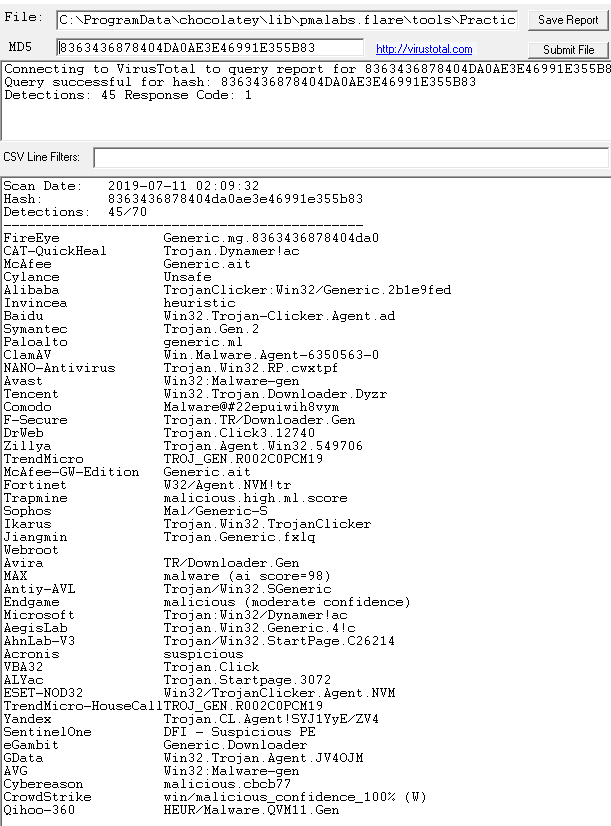
Using the Malcode Analyst Pack we are able to perform this by simply right clicking the files and selecting VirusTotal. At the time of writing the file matched existing antivirus signatures:
- 45/70 detection rate
Question 2
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Answer 2
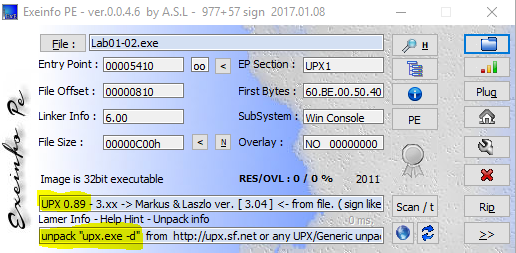
Diving in with a different tool called Exeinfo PE, we are able to determine that this file is packed using the Ultimate Packer for eXecutables (UPX). This also gives me some information on how to unpack the executable using UPX.
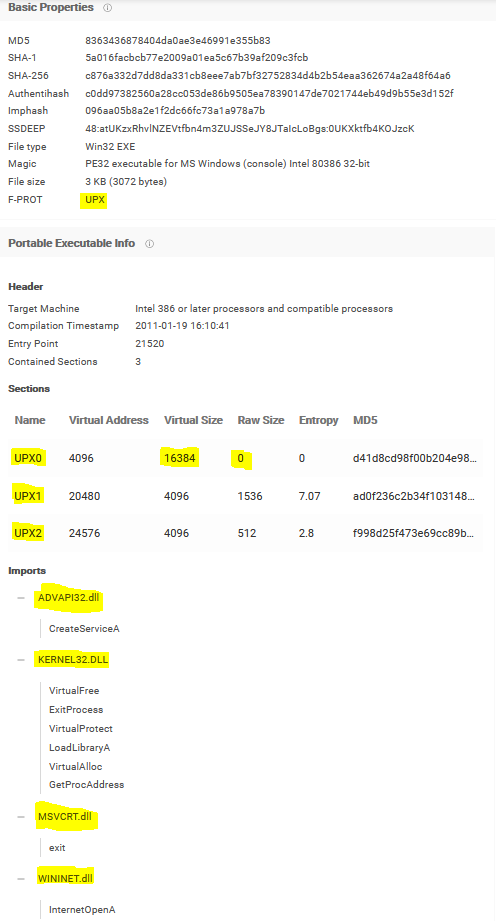
In addition, we can use VirusTotal to view Section names, properties, a small number of imports, and a section with a raw size significantly smaller than the virtual size which all indicate that this file is packed with UPX.
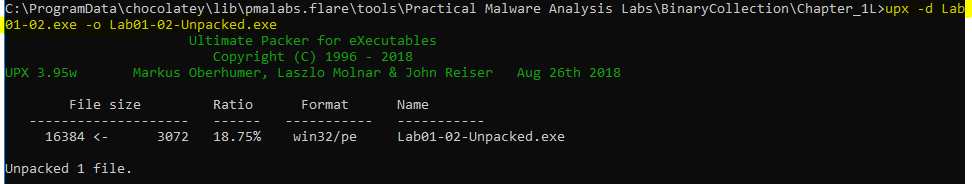
Following the unpacking guidance, we can unpack this executable giving to a new file.
upx -d Lab01-02.exe -o Lab01-02-Unpacked.exe
Question 3
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer 3
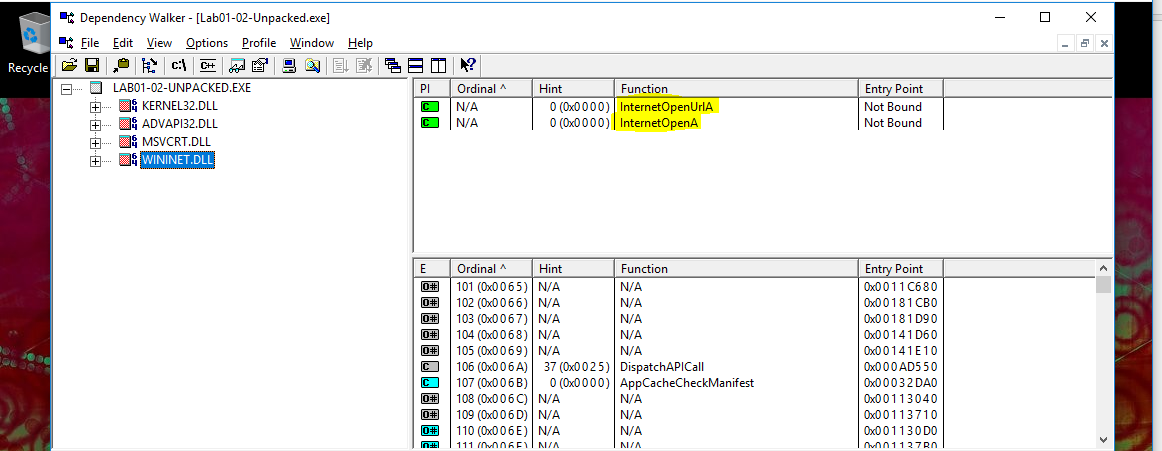
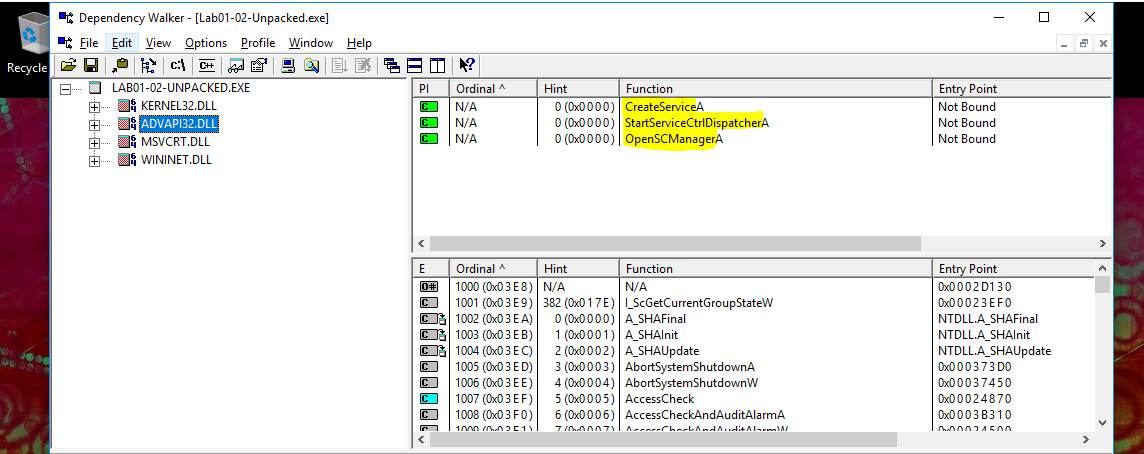
Analysing Lab01-02.exe through Dependency Walker highlighted the below interesting functions:
WININET.DLL
- InternetOpenUrl
- InternetOpen
ADVAPI32.DLL
- CreateService
- StartServiceCtrlDispatcher
- OpenSCManager
Based on this we can infer that the executable creates and triggers a service, and that it connects to the internet.
Question 4
What host- or network-based indicators could be used to identify this malware on infected machines?
Answer 4
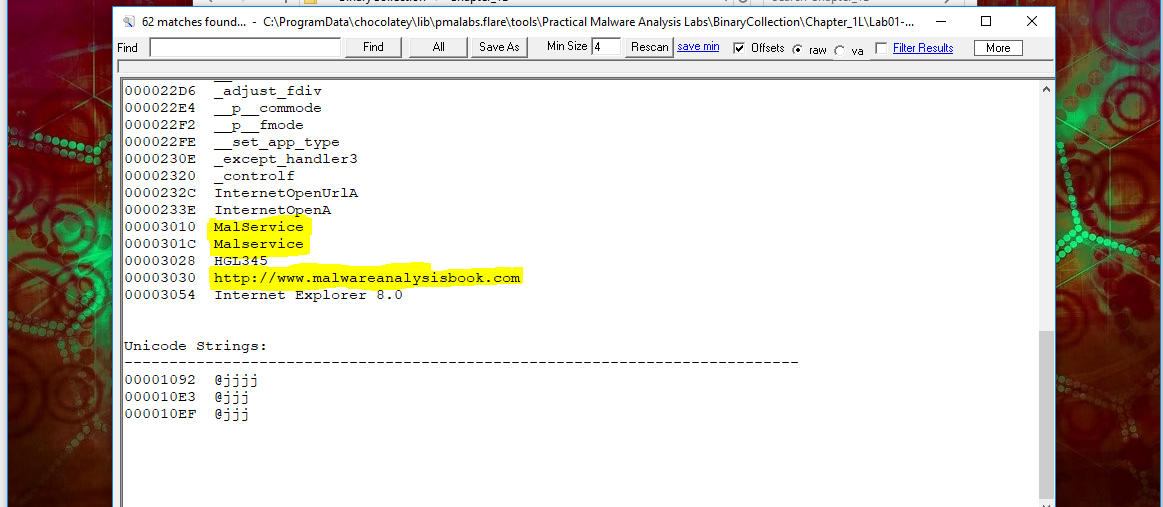
Looking at the strings of this file shows 2 interesting elements, ‘malservice’ and ‘http://www.malwareanalysisbook.com’.
Based on this we can assume that searching hosts for the scheduled service called ‘malservice’ and looking at any hosts connectiong to ‘http://www.malwareanalysisbook.com’ would serve as reliable host and network indicators.
Lab 1-3
This lab uses the file Lab01-03.exe. Analyze the file Lab01-03.exe.
Question 1
Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer 1
At the time of writing this had an overwhelming number of AV detections.
55/65 detection
Question 2
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Answer 2
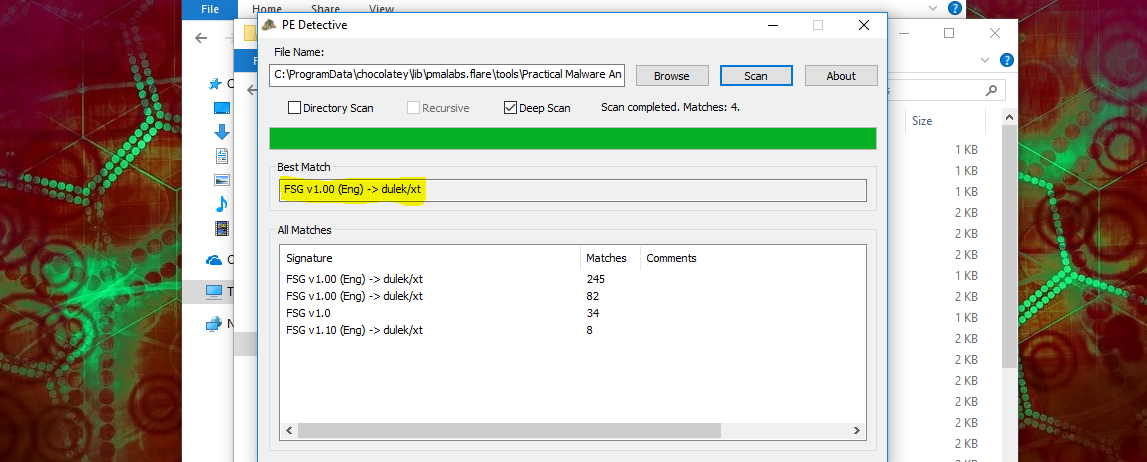
Once again, trying a different tool to keep things fresh, PE Detective revealed that this file was packed this time using FSG.
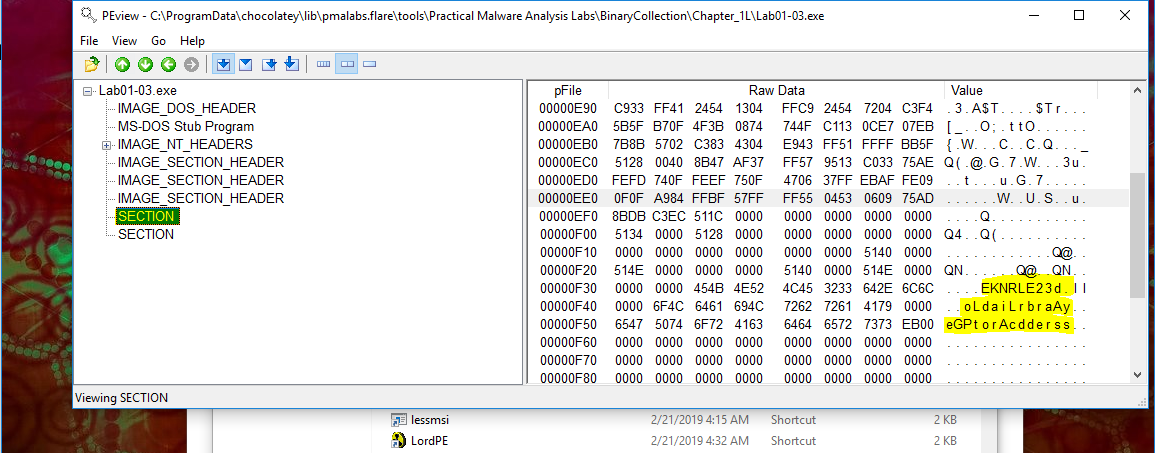
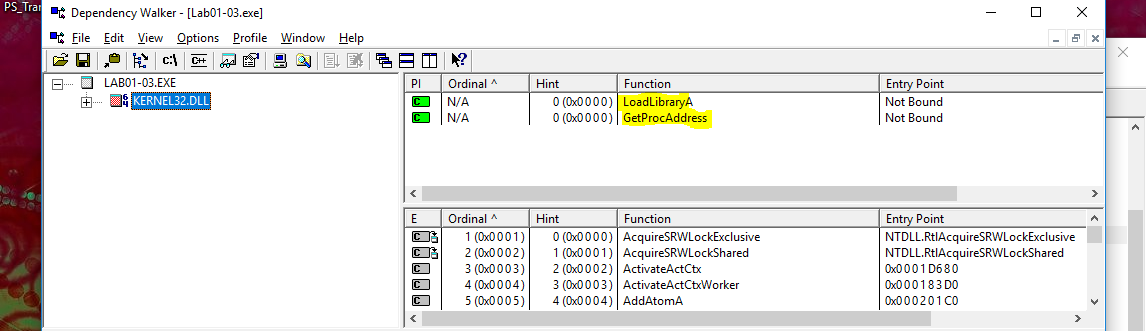
Using PEiD reveals that there are no import tables for the section like previously seen, which seems extremely strange. The raw hex almost looks like it is supposed to be importing something similar to loadlibrary and getprocaddress.
Looking at this through dependency walker revealed that these were indeed being imported. With only these libraries it is a very good indication that this binary is packed.
Question 3
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer 3
At present the file is packed with FSG, and we are unable to unpack this with the techniques learnt so far.
Question 4
What host- or network-based indicators could be used to identify this malware on infected machines?
Answer 4
At present the file is packed with FSG, and we are unable to unpack this with the techniques learnt so far.
Lab 1-4
This lab uses the file Lab01-04.exe. Analyze the file Lab01-04.exe.
Question 1
Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer 1
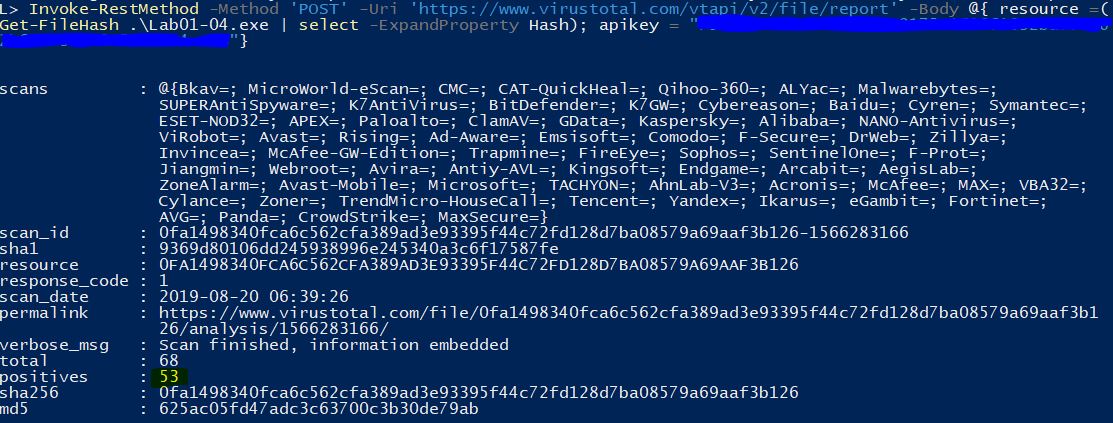
Getting creative with our VirusTotal submissions, we can check the file hash by using the VirusTotal API and some basic PowerShell. At the time of writing this had 53 detections.
Question 2
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Answer 2
There are no indications this file is packed or obfuscated, PEiD identifies it was created with Microsoft Visual C++ 6.0, PEview shows similar virtual and raw data size, and dependency walker shows a number of imports.
Question 3
When was this program compiled?
Answer 3
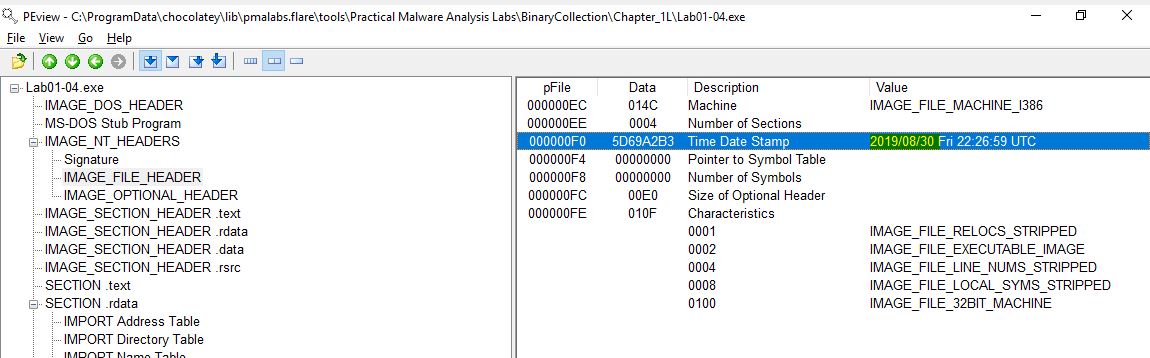
Using PEview we can see this program says it was compiled on the 30th of August 2019, and even as I type this years after the book was published that date is still a week away so this has obviously been faked or ‘timestomped’.
Question 4
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer 4
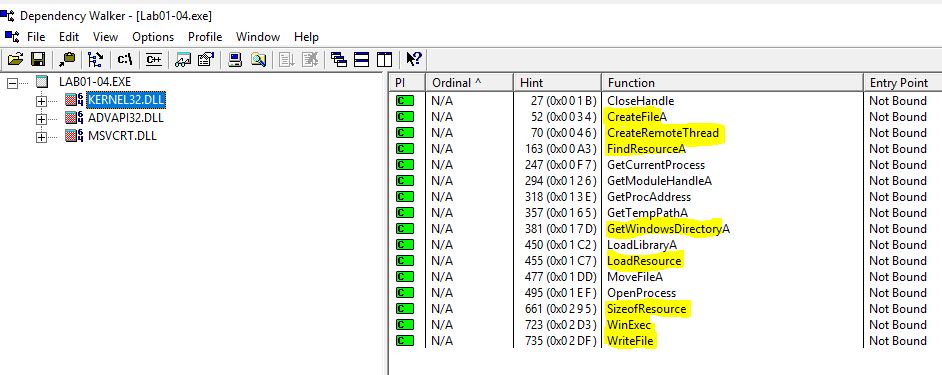
Based on the imports from Kernel32 we can see that this will load resources from the file’s resource section and write files to disk. Based on the GetWindowsDirectory function we can assume this will write files to the system directory, and will then execute them due to the WinExec function.
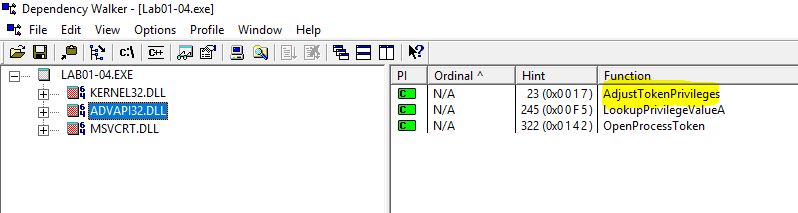
The imports from Advapi32 indicate that this is attempting to modify or change the token assigned to the execution of this process, presumably to elevate privileges or give extended access rights.
Question 5
What host-based or network-based indicators could be used to identify this malware on infected machines?
Answer 5
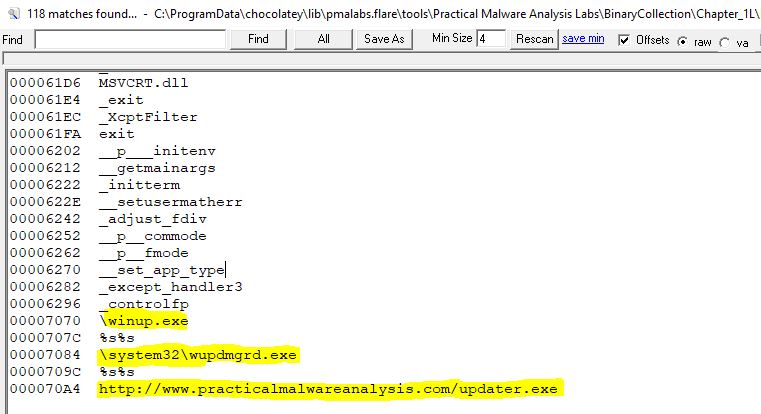
Looking into the strings of this file, we can see an entry for the following host indicators:
- winup.exe
- system32\wupdmgrd.exe
The strings also indicate the below network-based url which may be where a malware updater or second stage payload is pulled from.
- http://practicalmalwareanalysis.com/updater.exe
Question 6
This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
Answer 6
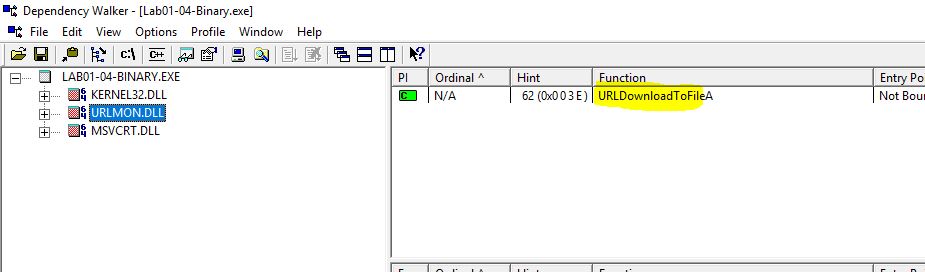
Looking at this resource through Resource Hacker, we can see that it has a header which indicates it is an embedded executable.
By saving this as a binary (executable) file, we can then open it in dependency walker and see this is the file which not only contains the winexec imported function of kernel32, but also the URLDownloadToFile function of URLMON.DLL which indicates it will likely download and execute a file.
This concludes chapter 1, proceed to the next chapter.