Aspmuma 2009 ‘xxooxx’ - Malware Analysis Lab
Overview
Part 1: Dynamic and Preliminary Static Analysis of Script
Taking a malicious ASPX script which has been categorised as a trojan with the name ‘sharphafnium webshell’ on VirusTotal, we can explore it further.
- Source: MalShare
- Source: VirusTotal.com
First off obtain the sample with a particular SHA256 hash:
Starting Host IOC: 041719e845c185b084ed154ba5553e8074e5a857890ce7d423285748d1420fb0
This was first uploaded to VirusTotal on 2021-09-21, 6 months after Microsoft released a report on ‘HAFNIUM targeting Exchange Servers with 0-day exploits’, so although it is being detected as a web shell under various signatures which would indicate it’s a C# implant tied to the HAFNIUM actor (Generic.SharpHafnium.C.2.562B1375), it’s important to keep in mind that this is very much a generic detection and isn’t necessarily tied to activity by the entity tracked within Microsoft as HAFNIUM.
A quick glance at this in a text editor shows it is importing a number of libraries (assemblies), and the namespaces imported give us an idea of the potential functionality of this script:
- System.IO: Reading and writing to files and data streams
- System.Diagnostics: Interacting with system processes, event logs, and performance counters
- System.Data: Managing data from multiple data sources
- System.Management: Interacting with Windows Management Instrumentation infrastructure
- System.Data.OleDb: Interacting with OLE DB via .NET
- Microsoft.Win32: Handling events raised by Windows or accessing the Windows registry
- System.Net.Sockets: Making low level network requests
- System.Net: Implementing commonly used protocols over a network
- System.Runtime.InteropServices: Supports unmanaged code communicating with managed code via COM interfaces
- System.DirectoryServices: Interacting with Active Directory Domain Services
- System.ServiceProcess: Interacting with Windows services
- System.Text.RegularExpressions: Supports regular expressions
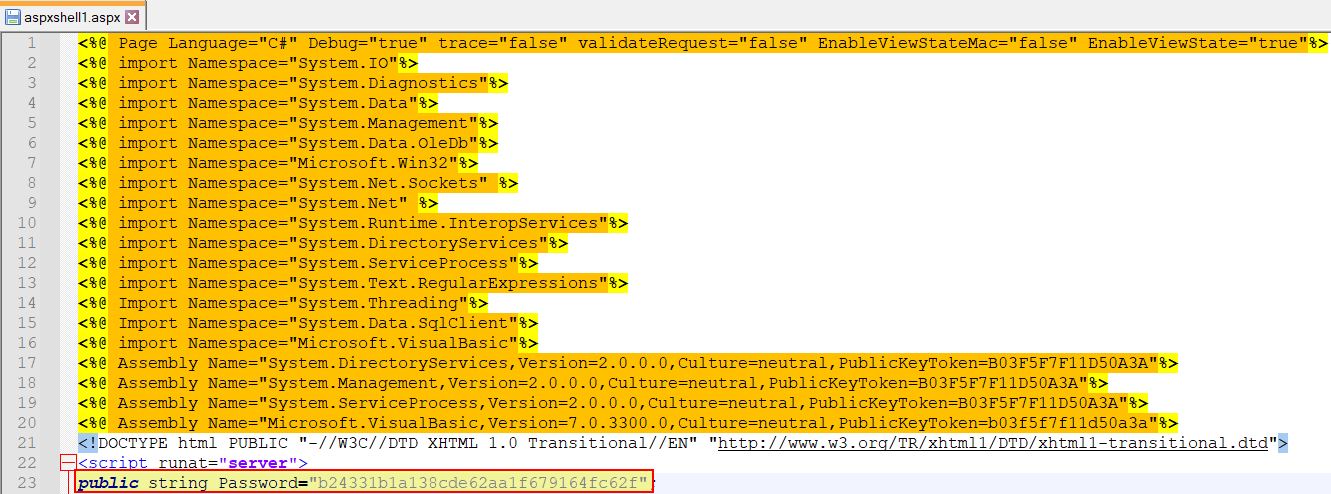
There’s also a field which contains the string ‘Password=’ which appears interesting and may be useful during analysis.
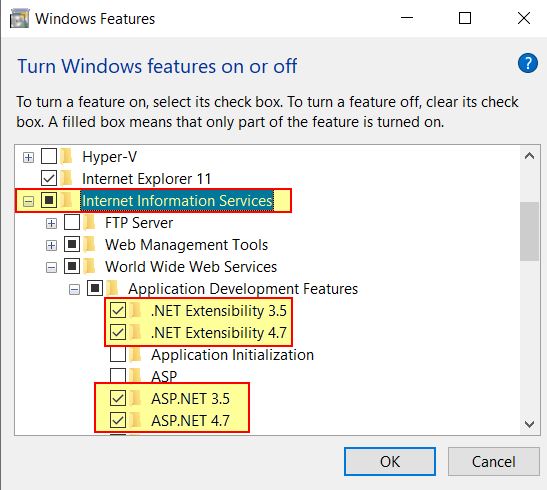
Start by enabling Internet Information Services (IIS) on a Windows system and enabling support for .NET (specifically ASP.NET, .NET Extensibility is a requirement of ASP.NET). This allows the web shell to be analysed dynamically if placed in the web root (by default - C:\inetpub\wwwroot).
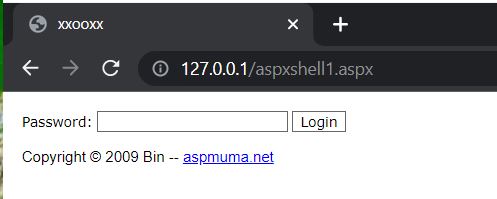
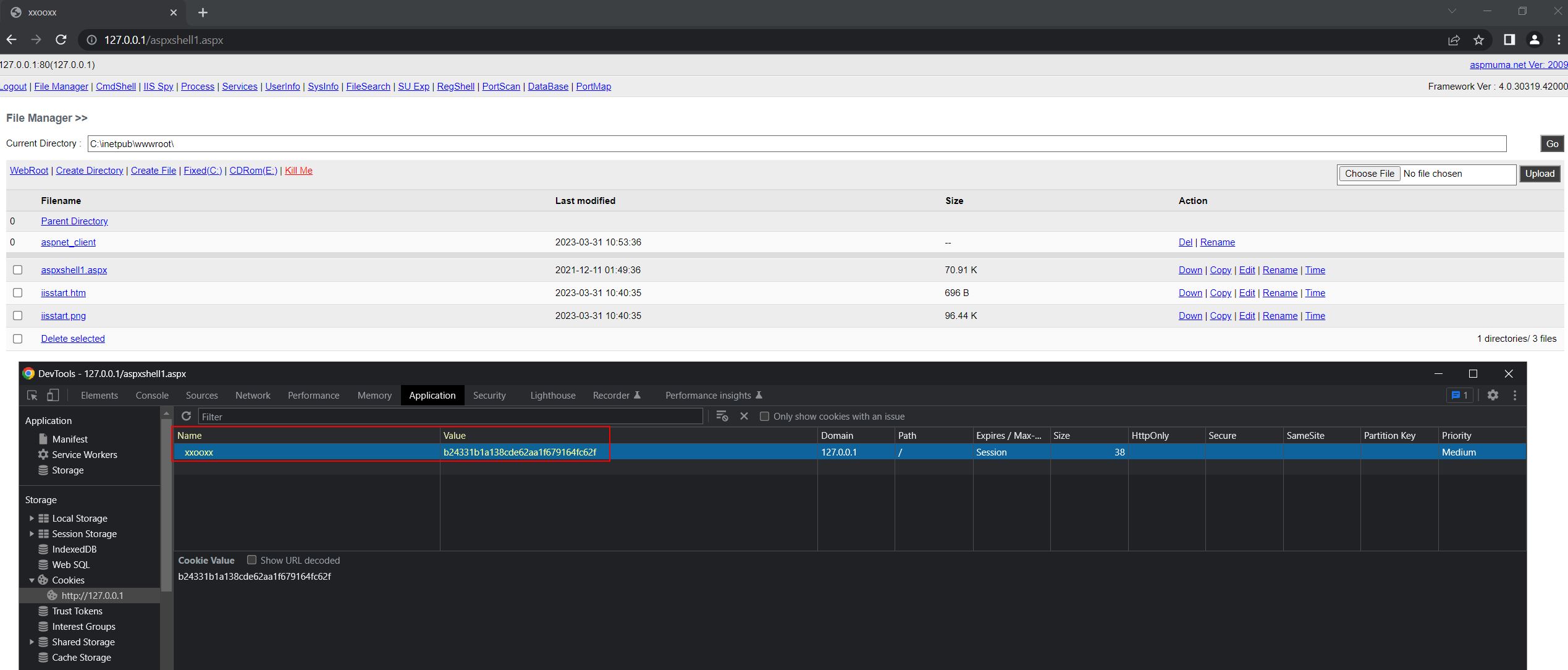
By accessing the web shell through a browser it prompts for a password to login, has a copyright message from 2009 tied to someone known as ‘Bin’, and a title of ‘xxooxx’.
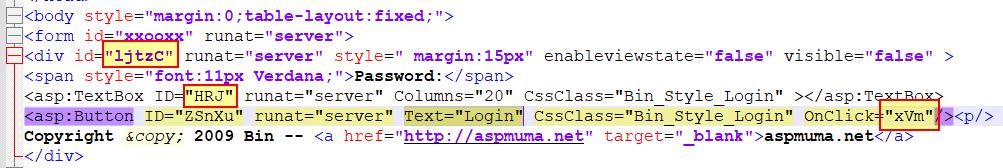
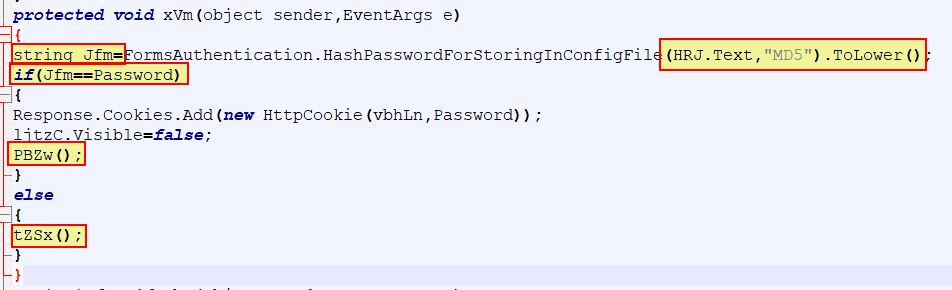
Manually examining the web shell code and searching for ‘Text=”Login”’ leads to the section accepting the logon form submission. This contains 3 elements of interest, the div tag identified as ‘ljtzC’ (as this shows or hides the logon screen), the textbox with ID ‘XRJ’ (as this holds the password submitted), and ‘xVm’ (as this is the method run when login is pressed).
Examining ‘xVm’ provides insight into how the logon form works. This is taking a MD5 hash of what is submitted and comparing it against the ‘Password’ string. If this matches it will create a new cookie with the password hash stored in a string defined as ‘vbhLn’, and then run the method ‘PBZw’ after setting the visibility of the logon screen ‘ljtzC’ to false. If it doesn’t it will run ‘tZSx’.
Running a search for the MD5 password string reveals it is ‘abc@123’, honestly a poor form password which has not only come up in breaches, but is also accessible using either rainbow tables online, or via cracking with a wordlist such as rockyou. You’d think criminals would have known better.
hashcat64.exe -m 0 b24331b1a138cde62aa1f679164fc62f rockyou.txt
Authenticating to the web shell reveals a primitive, yet easy to navigate interface. Looking at assigned cookies, a value called ‘xxooxx’ is now storing the MD5 of the password used to authenticate to ensure this session remains active. The reason this cookie is called ‘xxooxx’ is because the string ‘vbhLn’ is defined in the script as ‘xxooxx’.
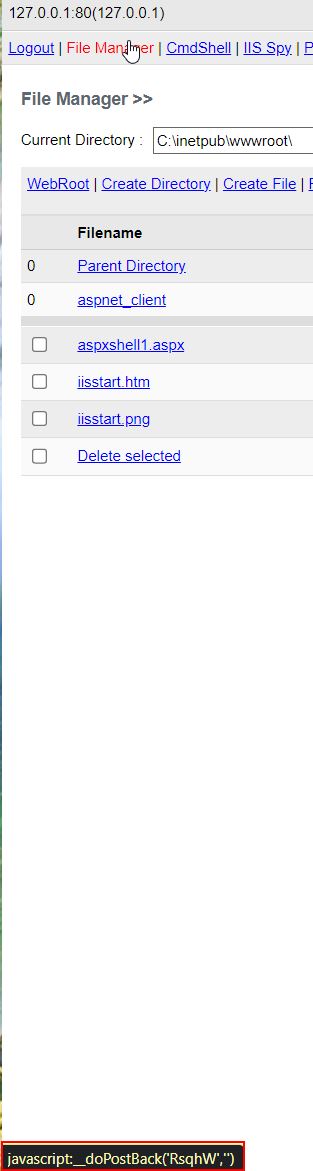
Highlighting any of the navigational links at the top reveals what will occur when they’re clicked. In this instance javascript is used which will call ‘__doPostBack’ with the target ‘RsqhW’ and no arguments.
Examining the script we gain more context that when ‘File Manager’ is clicked it will run the method ‘Ybg’.
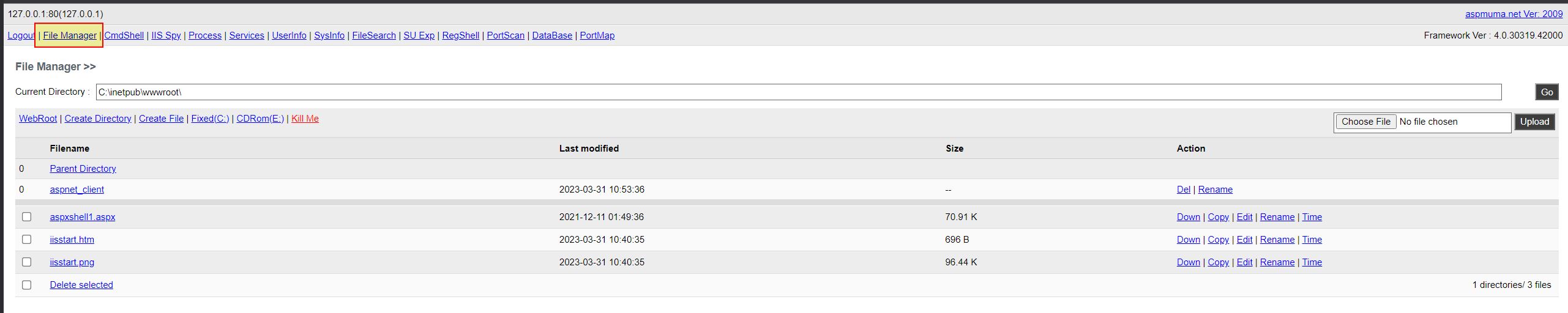
At a glance this web shell appears to have the following features which is fairly amazing for something so small:
Logout
This appears to de-authenticate the user and return to the logon screen.
File Manager
File Upload
WebRoot
This appears to navigate the user to the web directory within ‘File Manager’.
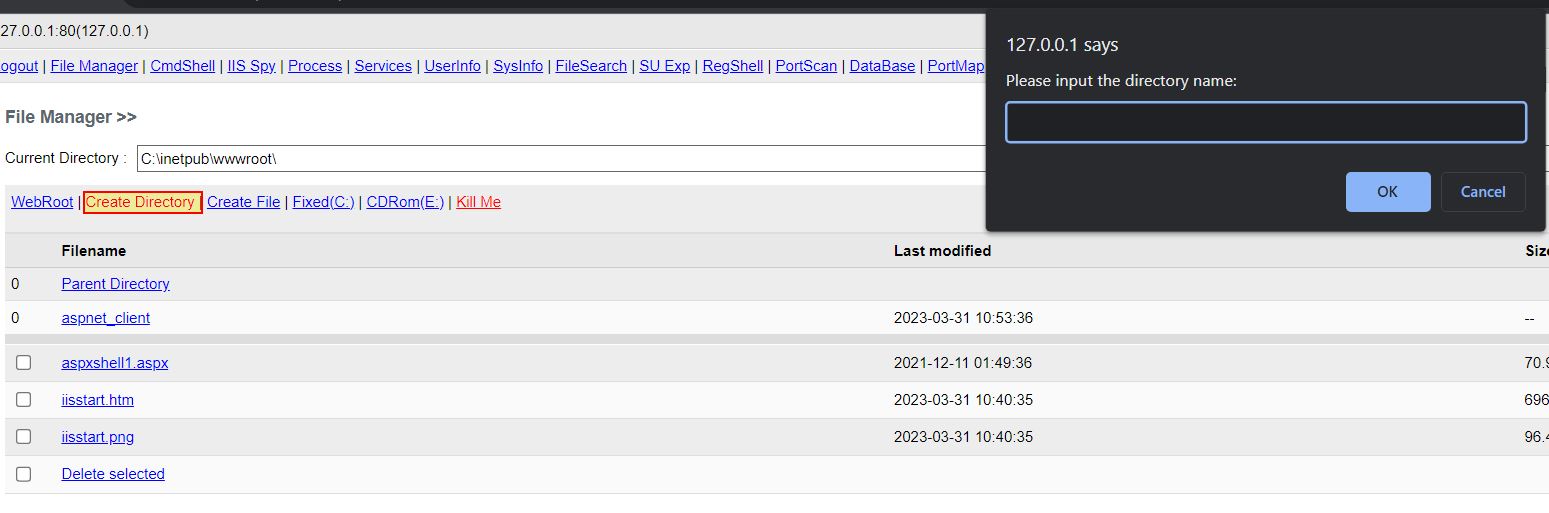
Create Directory
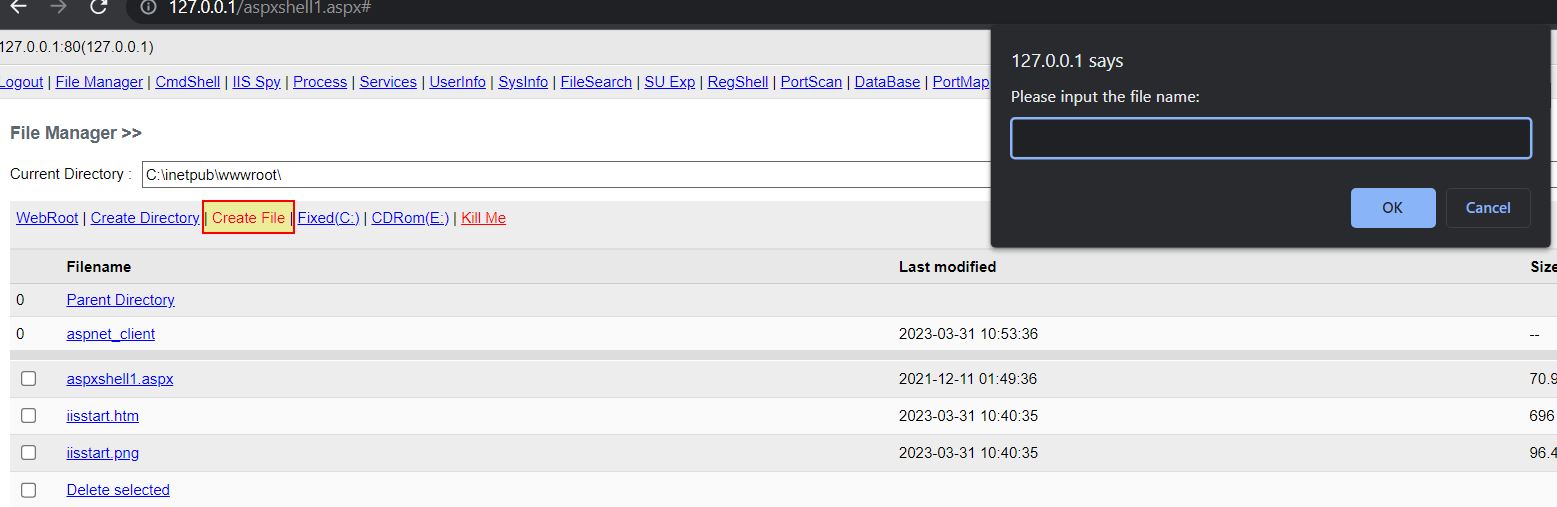
Create File
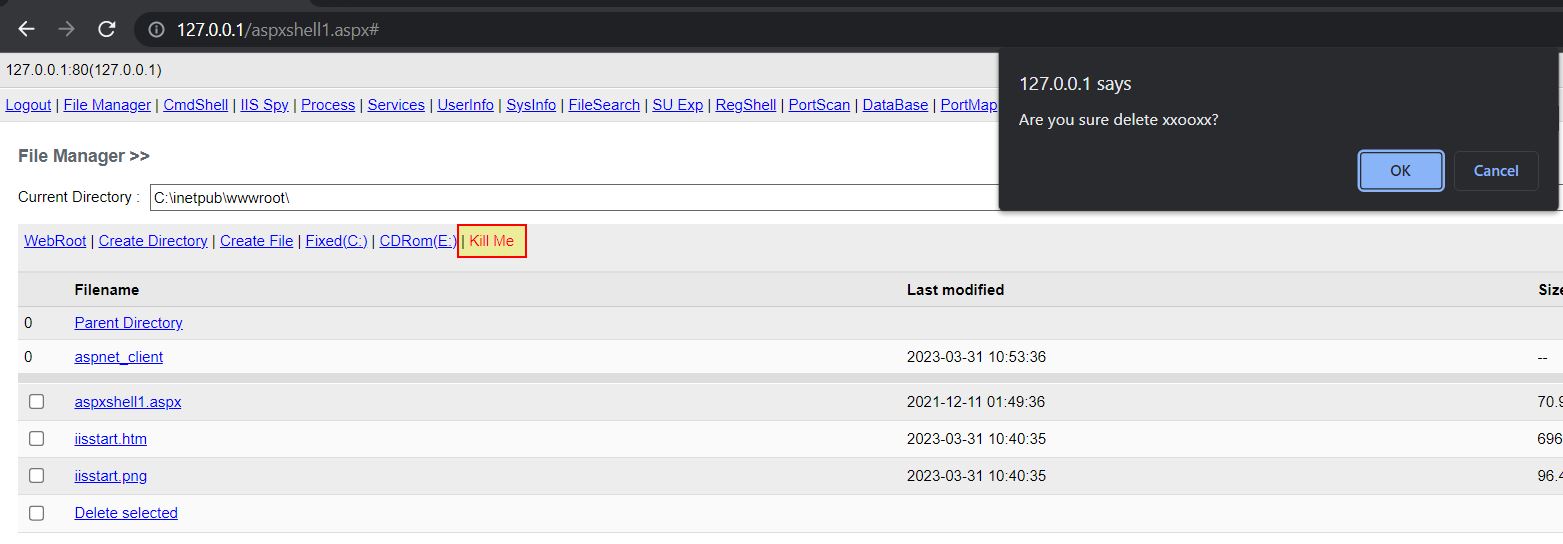
Kill Me
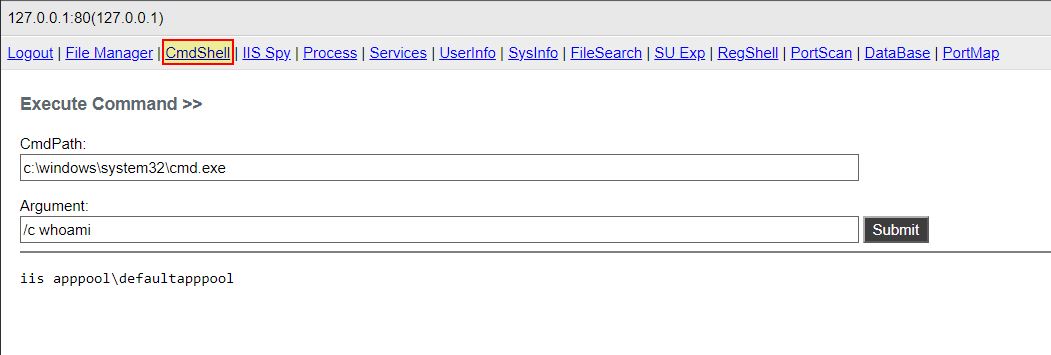
Command Shell
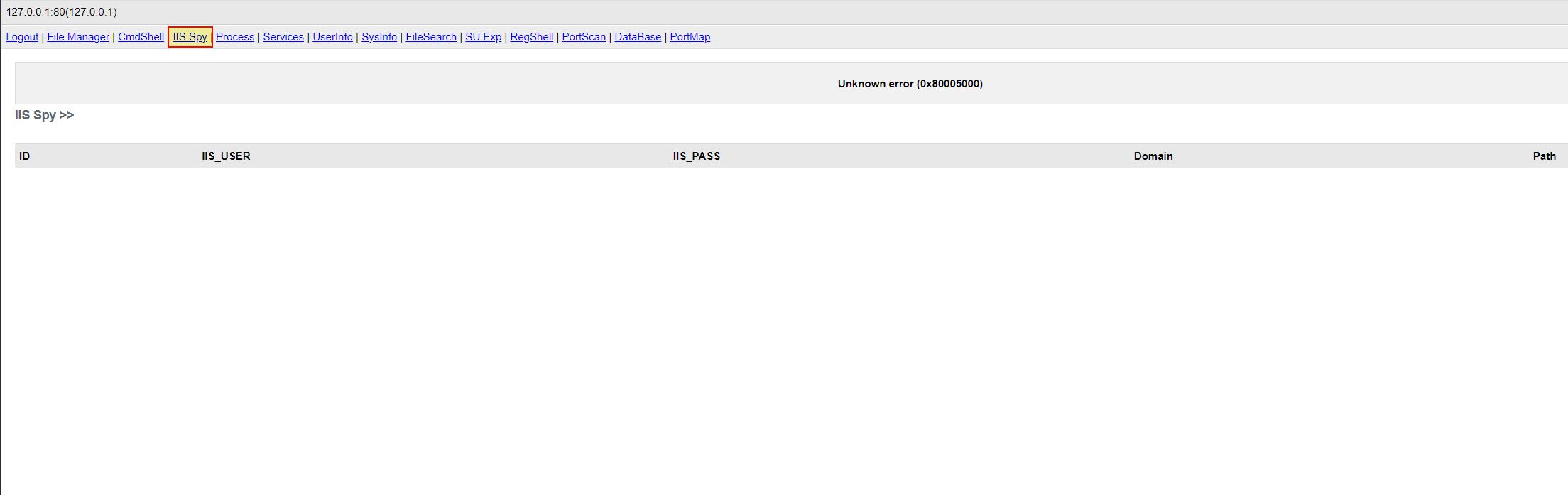
IIS Credential Harvesting
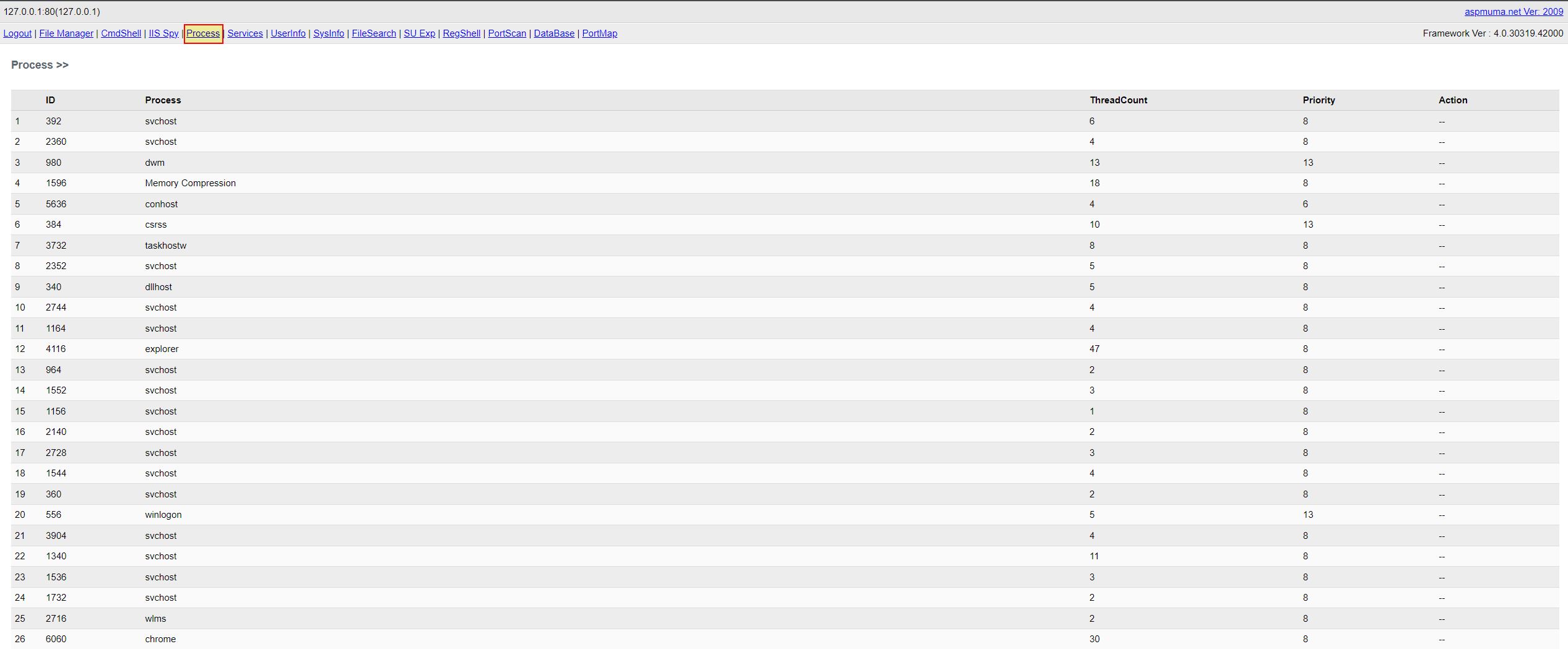
Process Discovery and Management
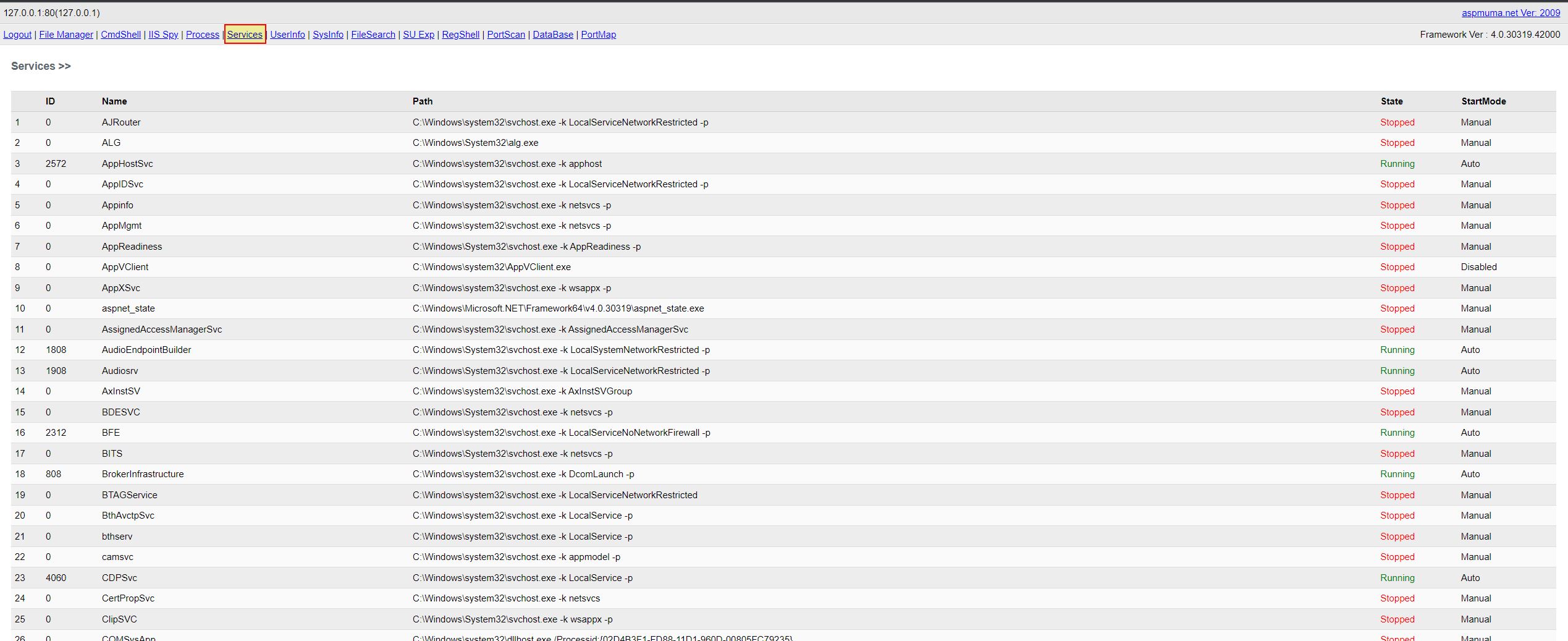
Service Discovery
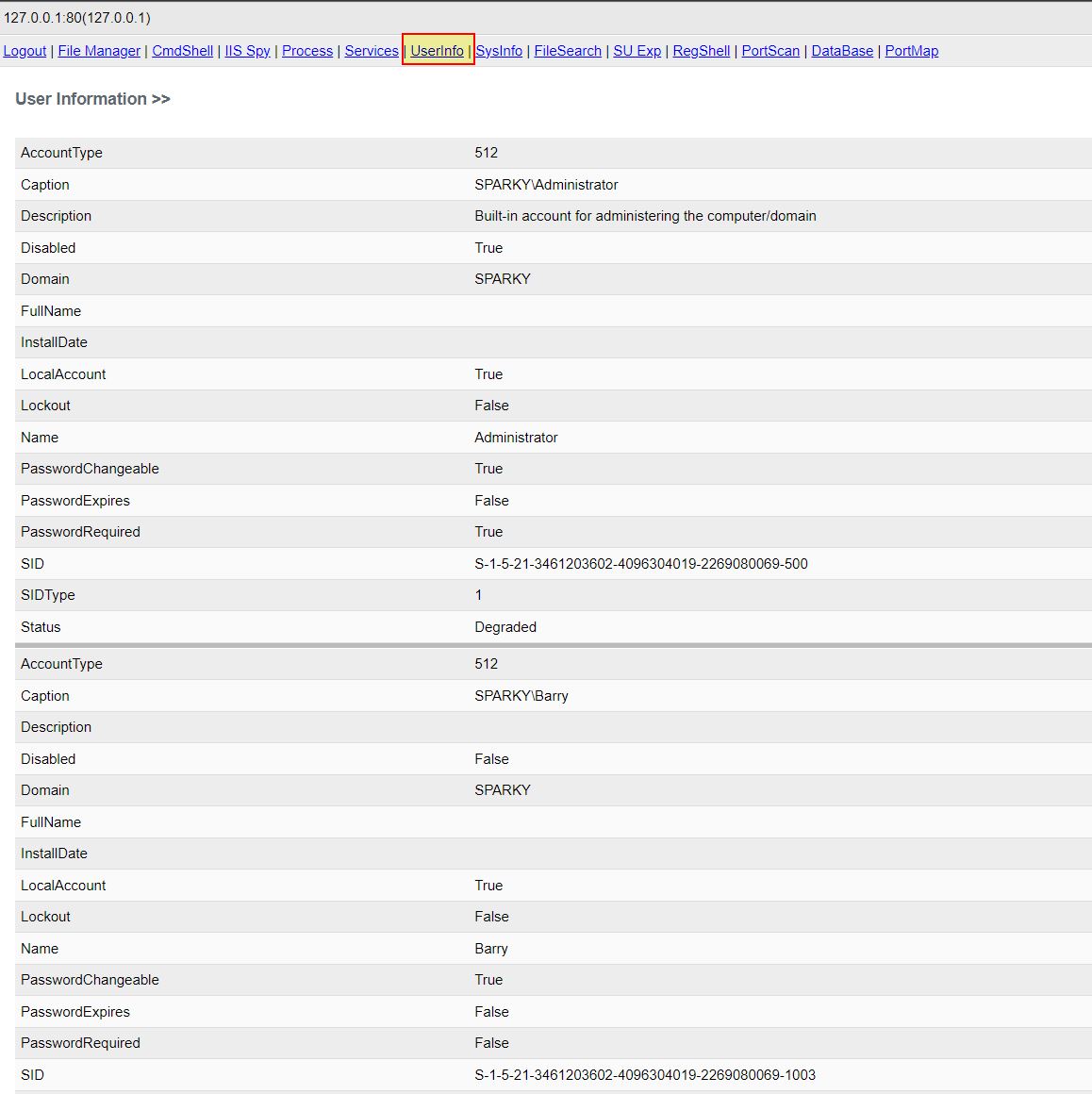
User Account and Password Expiry Discovery
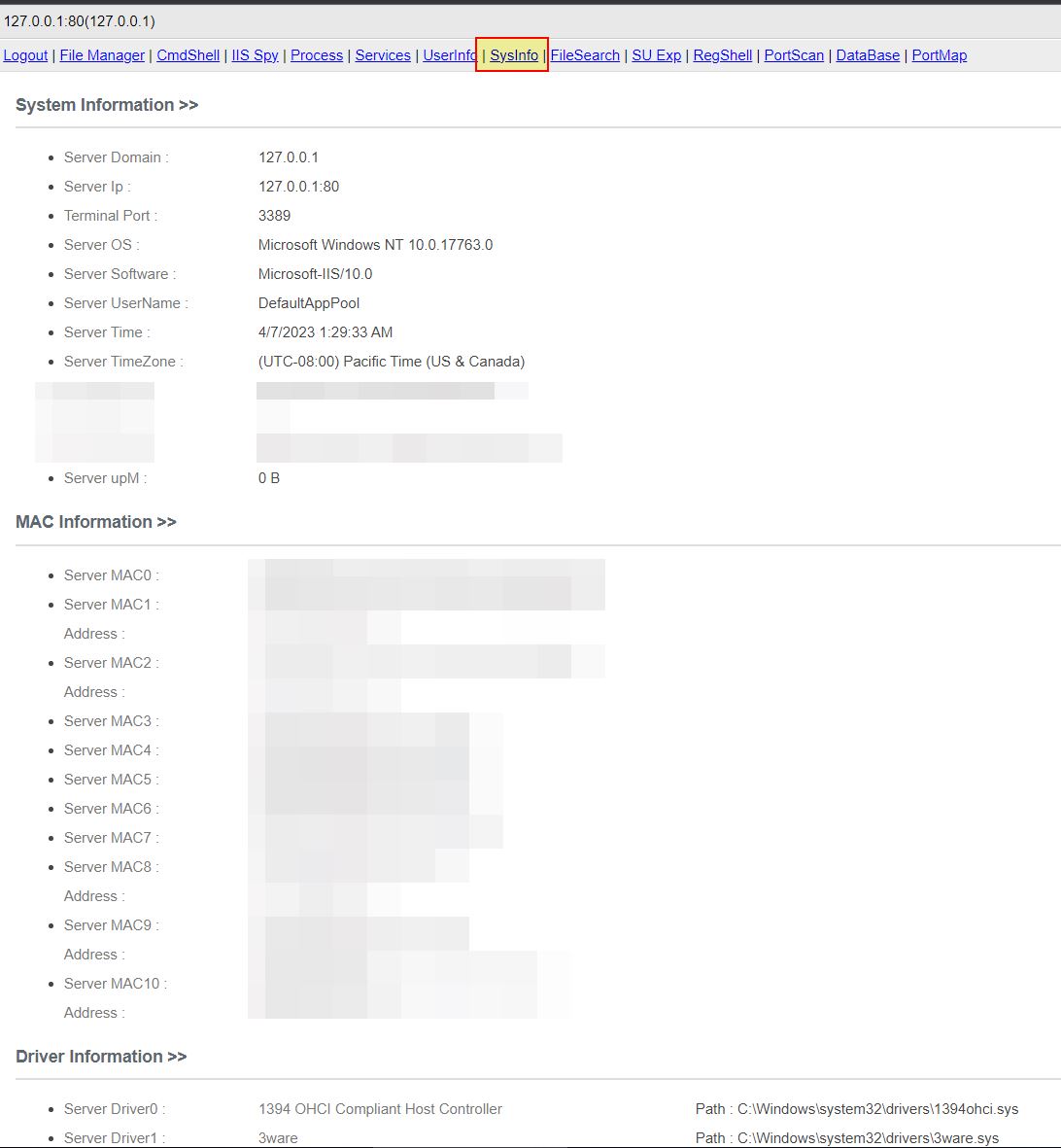
System Information and Driver Discovery
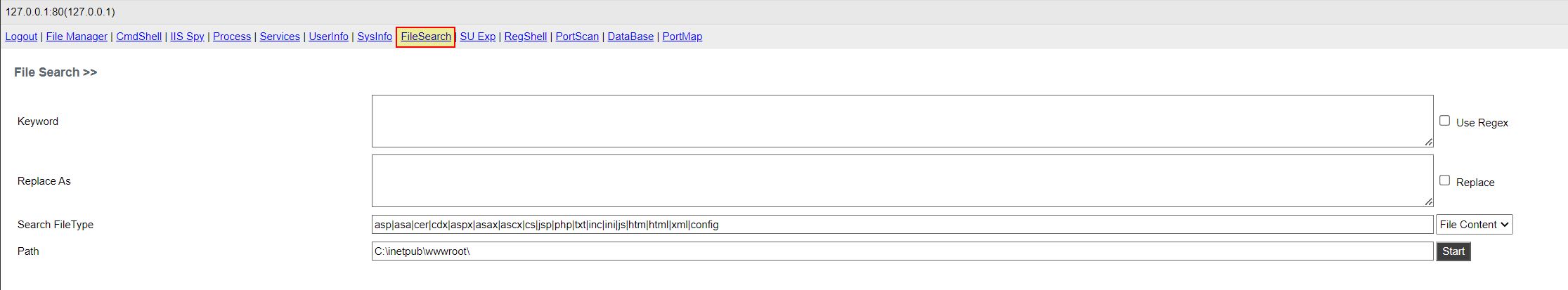
File Discovery / Search
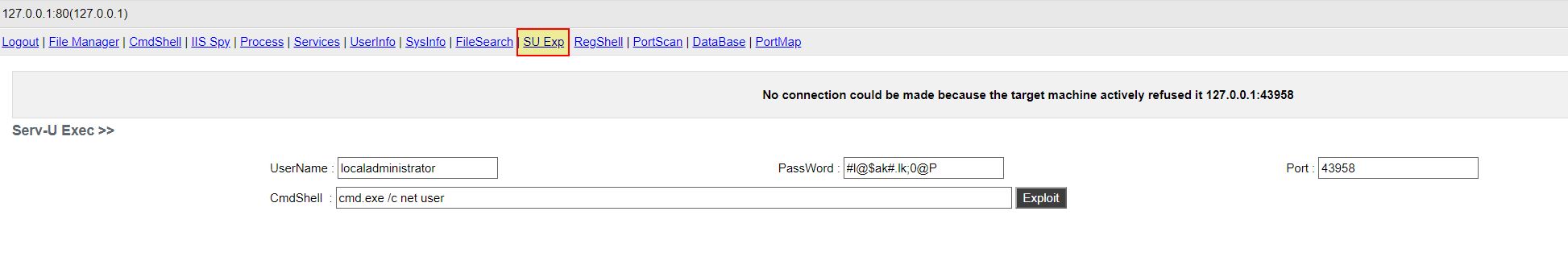
FTP Serv-U Command Execution via Possible Vulnerability Exploitation
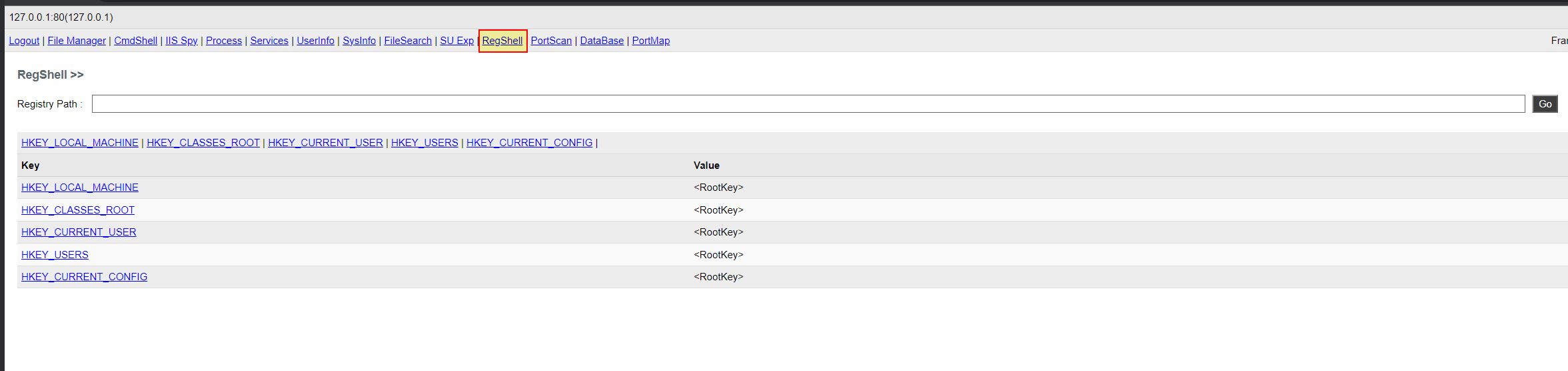
Registry Discovery / Querying
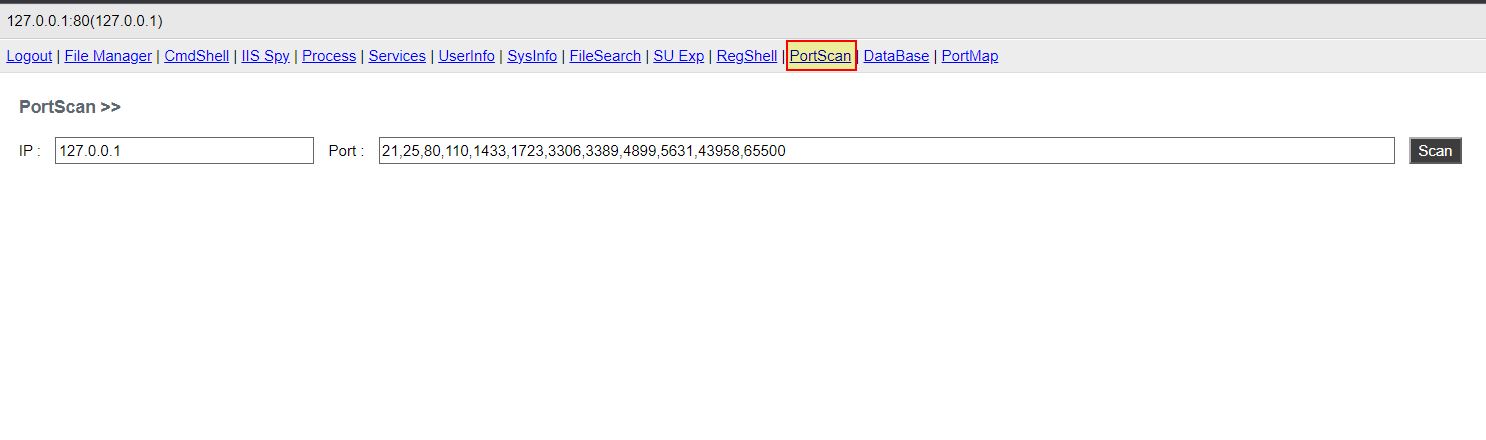
Port Scanning
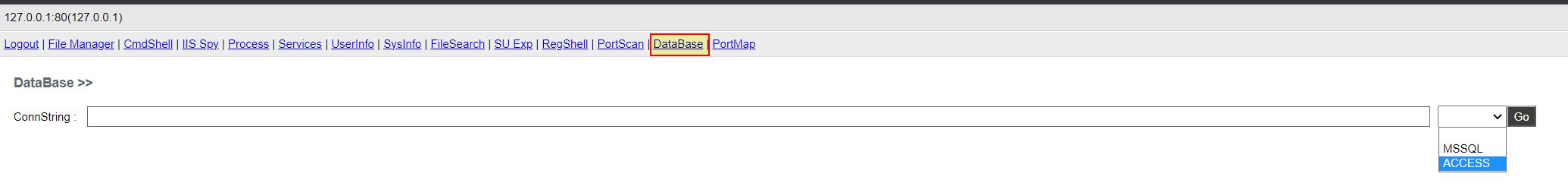
Microsoft Access / SQL Management
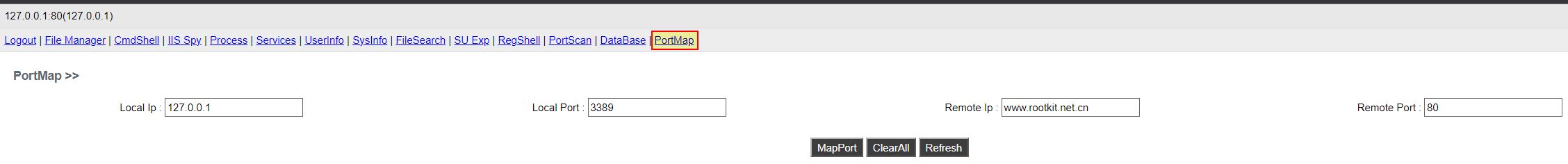
Port Forwarding / Protocol Tunneling
Part 2: Static Analysis of Script
Understanding Form ID to Method Mapping
The following are used as ‘__doPostBack’ targets with their associated methods being called upon being clicked:
- Logout: ‘UtkN’ -> Method: ‘YKpI’
- File Manager: ‘RsqhW’ -> Method: ‘Ybg’
- Command Shell: ‘xxzE’ -> Method: ‘VOxn’
- File Upload: ‘RvPp’ -> Method: ‘lbjLD’
- WebRoot: ‘OLJFp’ -> Method: ‘mcCY’
- Create Directory: ‘Bin_Button_CreateDir’ -> Method: ‘Bin_Createdir’
- Create File: ‘Bin_Button_CreateFile’ -> Method: ‘Bin_Createfile’
- Kill Me: ‘Bin_Button_KillMe’ -> Method: ‘hae’
- IIS Credential Harvesting: ‘nuc’ -> Method: ‘KjPi’
- Process Discovery and Management: ‘OREpx’ -> Method: ‘Grxk’
- Service Discovery: ‘jHN’ -> Method: ‘ilC’
- User Account and Password Expiry Discovery: ‘PHq’ -> Method: ‘Olm’
- System Information and Driver Discovery: ‘wmgnK’ -> Method: HtB
- File Discovery / Search: ‘FeV’ -> Method: ‘PPtK’
- FTP Serv-U Command Execution via Possible Vulnerability Exploitation: ‘PVQ’ -> Method: ‘jXhS’
- Registry Discovery / Querying: ‘jNDb’ -> Method: xSy
- Port Scanning: ‘HDQ’ -> Method: ‘cptS’
- Microsoft Access / SQL Management: ‘AoI’ -> Method: ‘dMx’
- Port Forwarding / Protocol Tunneling: ‘KHbEd’ -> Method: ‘fDO’
It’s worth noting that each of these specifically include ‘runat=”server”’ after the ID declaration. This is because all of the links above function as ‘HTML server controls’, which in essence is a way of extending traditional HTML page structure to allow access to elements which are being processed and parsed server-side, as opposed to being processed client-side in the browser itself. This means that the elements and their identifiers specified above are able to be accessed by underlying .NET code which is running on the server and used to populate the fields as shown in the screenshots above.
Logout
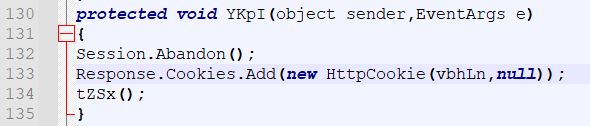
This button calls the method ‘YKpI’. This method contains 3 actions which take place:
- Session.Abandon is called to ensure the current authenticated user session is no longer valid.
- The cookie ‘xxooxx’ defined from a string stored in ‘vbhLn’ is set to ‘null’ effectively removing the correct entered password from the user browser cookie to prevent automatically logging in.
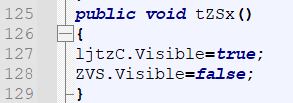
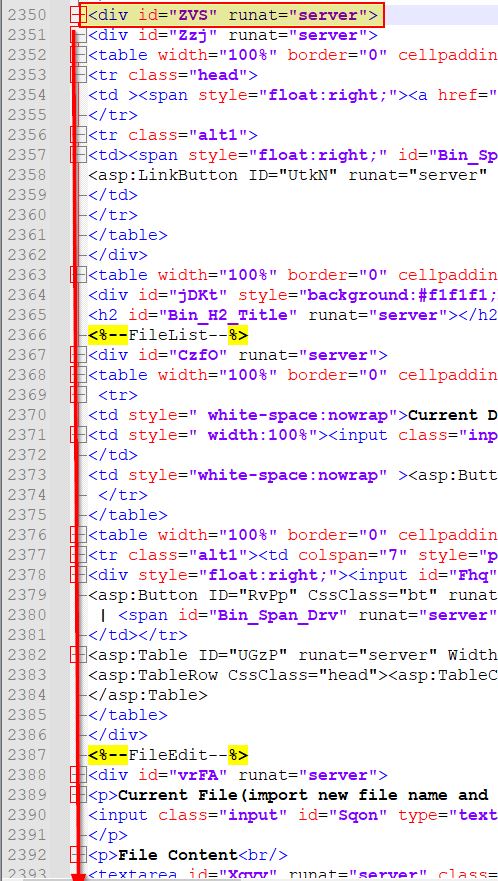
- ‘tZSx’ is called which sets ‘ljtzC’ to visible, and ‘ZVS’ to be invisible. As mentioned previously ‘ljtzC’ is the logon screen, and it’s also shown that ‘ZVS’ is the ID used to identify a div tag holding the entire web shell C2 interface.
File Manager
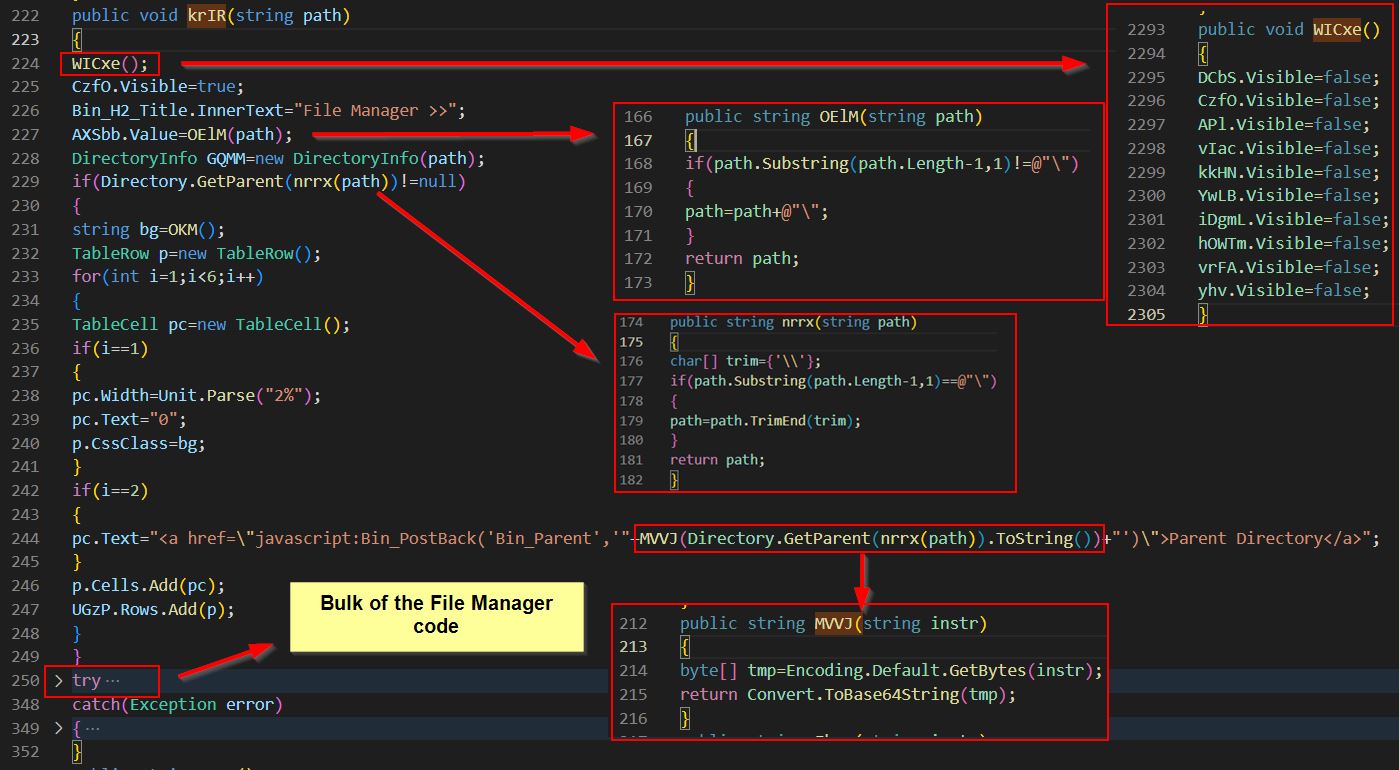
This button calls the method ‘Ybg’. This method calls another method ‘krIR’ and passes into it the output of Server.MapPath to get the current physical file path on disk where the web shell resides based on the web application’s current virtual path.
Examining the method ‘krIR’, this calls another method called ‘WICxe’ designed to reset all div tags to false before setting the one wanted to true, enabling seemless transition from a single page by hiding and showing elements as necessary. This has a number of other methods being called, most of which are creating and formatting the UI with a table to be used, before calling the bulk of the File Manager code from within a try statement, so that if if fails the user is instead presented with an appropriate error message.